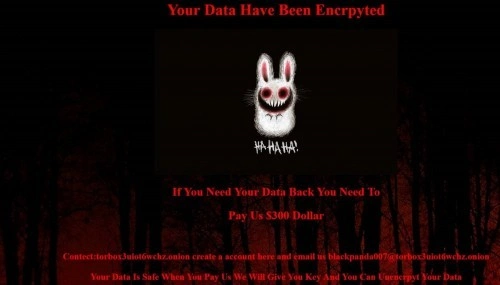
Yesterday we posted an analysis on the GandCrab Ransomware, today we have uncovered further details on how its sold on the deep and dark web.
Below is the dark web advertisement, all in Russian:
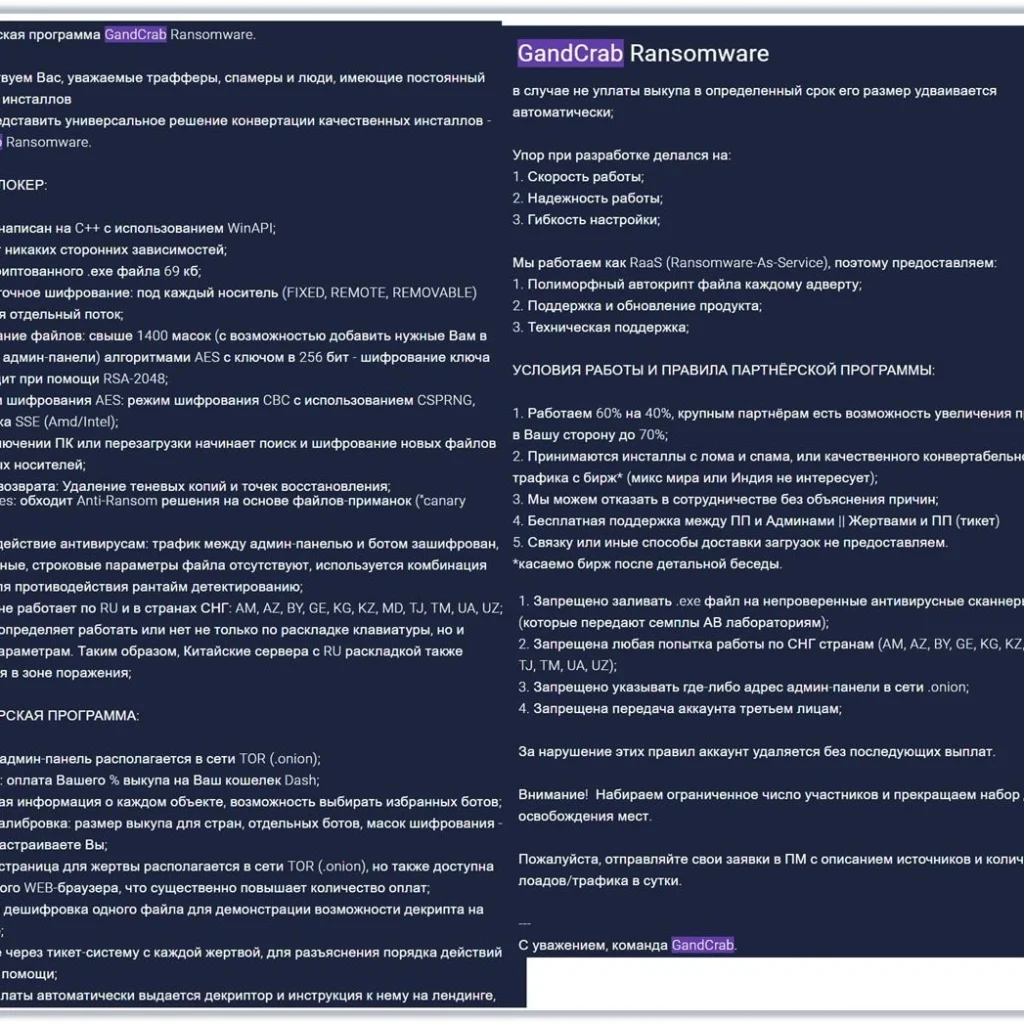
We’ve posted the full English translation further below, but some particularly interesting points from the advertisement include:
• Prospective buyers are asked to join the ‘partner program’, in which profits from the ransomware are split 60:40
• ‘Large’ partners are able to increase their percentage of proceeds to 70 per cent
• As a Ransomware-as-a-service offering, technical support and updates are offered to ‘partners’
• Partners are prohibited from targeting countries in the Commonwealth of Independent States (Azerbaijan, Armenia, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Russia, Tajikistan, Turkmenistan, Uzbekistan and Ukraine) – violating this rule results in account deletion
• Partners must apply to use the ransomware, and there is a limited amount of ‘seats’ available
• The authors have even posted an instructional video: https://www.youtube.com/watch?v=nUmisgYCeDU
Full translation is below:
“The partner program GandCrab Ransomware.
Welcome, respected traffickers, spammers and people who have a permanent source of installation
We are glad to present a universal solution for converting quality installations – GandCrab Ransomware.
The product is written in C ++ using WinAPI;
Has no third-party dependencies;
The weight of thenon–crypted .ehe file is 69 kb;
Multithreaded encryption: for each media (FIXED, REMOTE, REMOVABLE), a separate thread is created;
Encryption of files: over 1400 masks (with the ability to add the ones you need manually into the admin panel) with AES algorithms with a key of 256 bits – encryption of the key occurs with the help of RSA-2048;
AES encryption algorithm: CBC encryption mode using CSPRNG, SSE support (Amd / Intel);
When turning off the PC or restarting, it starts searching and encryption of new files and removable media;
Point of no return: Deleting shadow copies and recovery points;
Canary files: bypasses Anti-Ransom solutions based on bait files (“canary files”);
Counteraction to antiviruses: traffic between the admin panel and the bot is encrypted, meta-data, string file parameters are missing, a combination of techniques is used to counteract the detection of runtimes;
The product does not work in RU and in CIS countries: AM, AZ, BY, GE, KG, KZ, MD, TJ, TM, UA, UZ;
The product determines whether to work or not only on the keyboardlayout, but also other parameters. Thus, Chinese servers with RU layout are also in the affected area;
A convenient admin panel is located in the network TOR (.onion);
Payouts: paying your% redemption to your Dash wallet;
Detailed information about each object, the ability to select selected bots;
Manual calibration: the size of the ransom for countries, individual bots, encryption masks – all this you configure;
The page for the victim is located in the network TOR (.onion), but is also accessible from a regular WEB-browser, which significantly increases the number of payments;
Test decryption of one file to demonstrate the possibility of a decryption on a landing;
The page for the victim is located in the network TOR (.onion), but is also accessible from a normal WEB browser, which significantly increases the number of payments;
Test decryption of one file to demonstrate the possibility of a decryption on a landing;
Communicate through the ticket system with each victim, to explain the order of actions and other assistance;
After payment, the decryptor and instructions to it are automatically issued in the Landing, in case of not paying the repayment at a certain time, its size doubles automatically;
The focus during development was on:
1. The speed of work;
2. Reliability of work;
3. Flexible customization;
We work as RaaS (Ransomware-As-Service), therefore we provide:
1. Polymorphic file autotype for each advert;
2. Support and update the product;
3. Technical support;
WORKING CONDITIONS AND RULES OF THE PARTNER PROGRAM:
1. We work 60% on 40%, large partners have the opportunity to increase the interest in your side up to 70%;
2. Installations are accepted with scrap and spam, or quality convertible traffic from stock exchanges * (a mix of the world or India is not interested);
3. We can refuse cooperation without explaining the reasons;
4. Free support between PP and Admins || Victims and PP (Ticket)
5. We do not provide links or other methods of delivery.
* regarding exchanges after a detailed conversation
1. It is forbidden to flood the .exe file with unchecked anti-virus scanners (which transmit samples to AV laboratories);
2. Any attempt to work in the CIS countries (AM, AZ, BY, GE, KG, KZ, MD, RU, TJ, TM, UA, UZ) is prohibited;
3. It is forbidden to specify anywhere the address of the admin panel in the .onion network;
4. It is forbidden to transfer the account to third parties;
For violation of these rules, the account is deleted without subsequent payments.
Attention! We recruit a limited number of participants and stop the set until the seats are vacated.
Please send your applications to the PM with a description of the sources and number of traffic / traffic per day.
—
Sincerely, TheGandCrab Team.”


