
Overview
With cryptocurrency taking the world by storm, it’s no surprise hackers have found a way to exploit the frenzy. Blouiroet, a trojan with the ability to establish remote access connections, keylog, collect system information, download/upload files, and drop further malware on the infected system, is being sold on the dark web disguised as a crypto-miner.
To be clear, a phishing URL (highlighted in the dark web advertisement below) is being sold to attackers who then craft an email purporting to offer access to cryptomining software. This is then distributed via a spam email campaign – in Blouiroet’s case, it has been used to target victims in the U.S, France and China.
The following Operating Systems are vulnerable to Blouiroet:
• Windows 2000
• Windows 95
• Windows 98
• Windows Me
• Windows NT
• Windows Server 2003
• Windows XP
• Windows Vista
• Windows 7 (x86/x64)
• Windows 8 (x86/x64)
• Windows 10 (x86/x64)
File Details
| File type | Portable Executable (PE) file |
| Md5 hash | 905a5167b248647ce31d57d241aacd63 |
Static Analysis
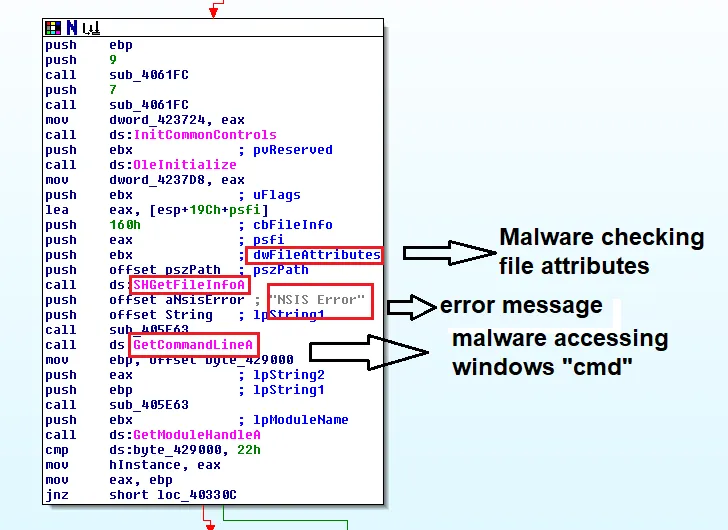
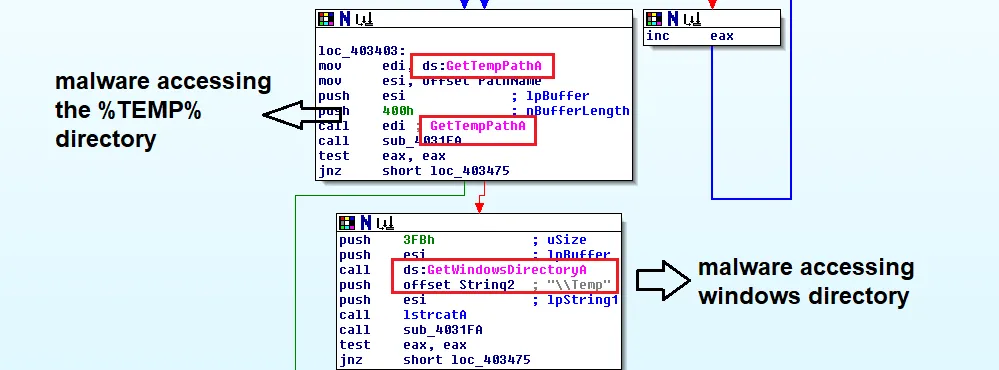
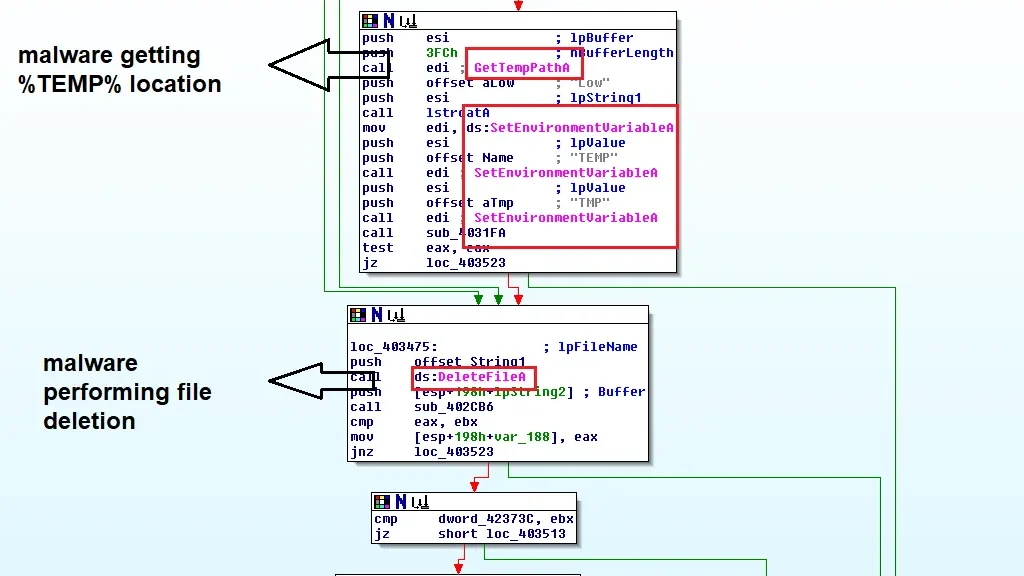
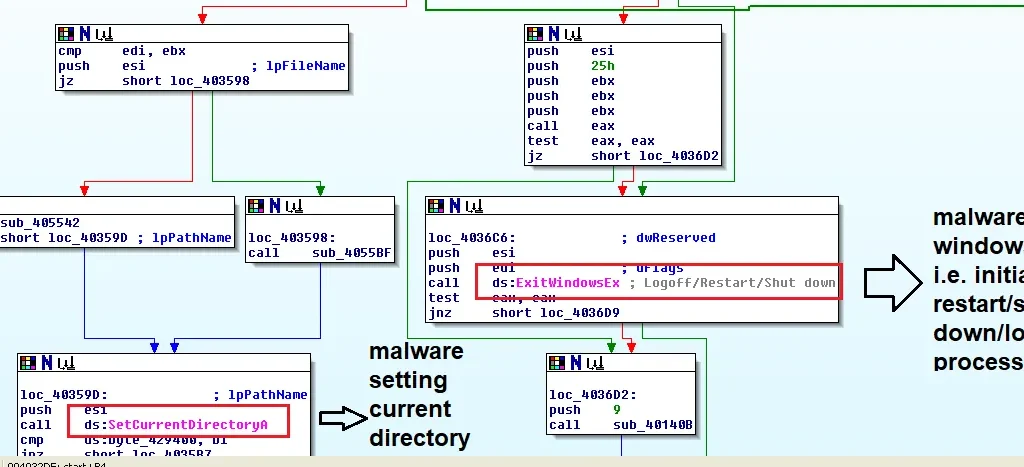
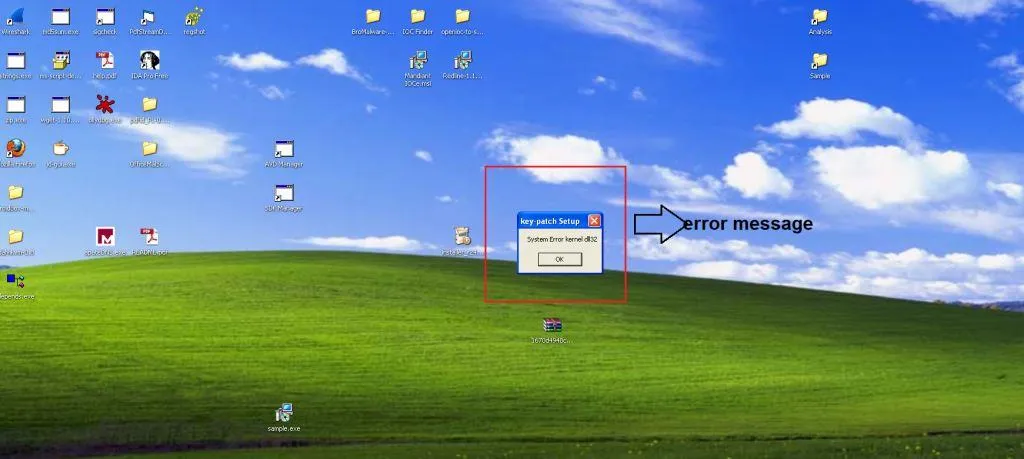
Static analysis quickly uncovered the file’s malicious behavior. Strings were discovered showing the malware searching for various files, checking path names of %TEMP% directory, setting file attributes where the malware was present, and executing command line. Once the fake cryptominer link is clicked, an installation procedure executes. The installation process is designed to fail, with the error message containing a link ‘for more information’. This link takes the victim directly to Blouiroet’s Command and Control (C&C) server [H**p: //nsis [.]Sf [.]Net/NSIS_Error].
The below images illustrate the malicious string associated:
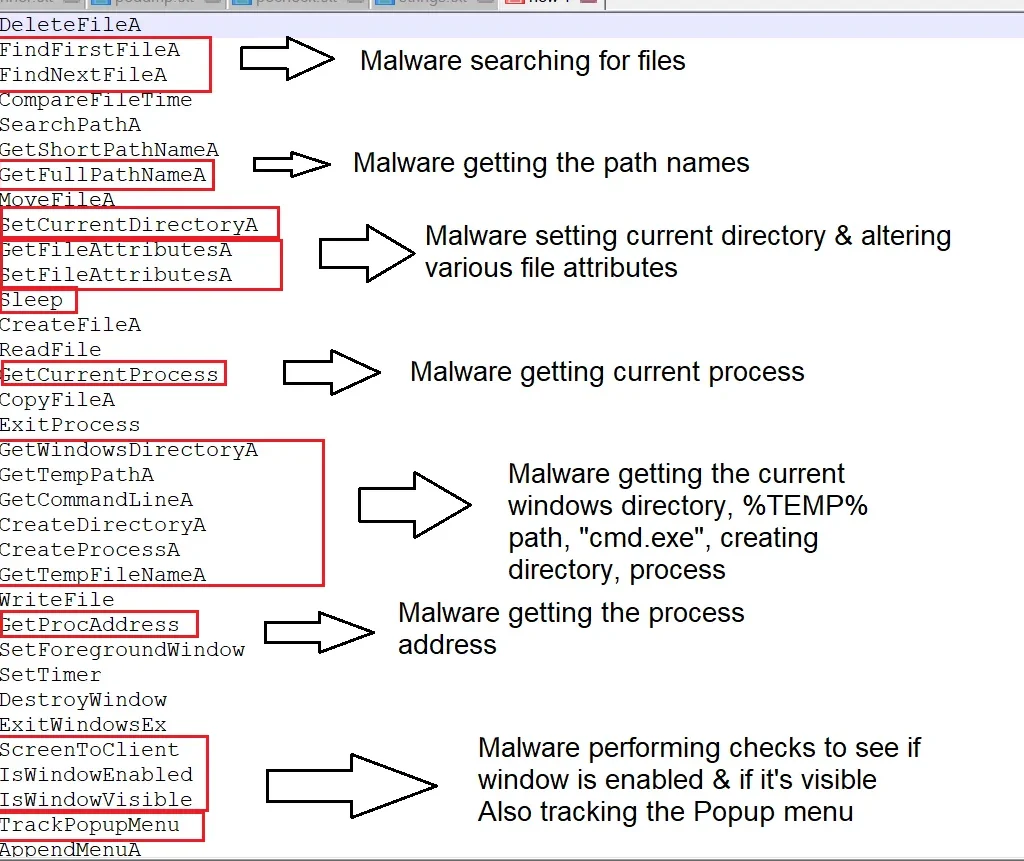
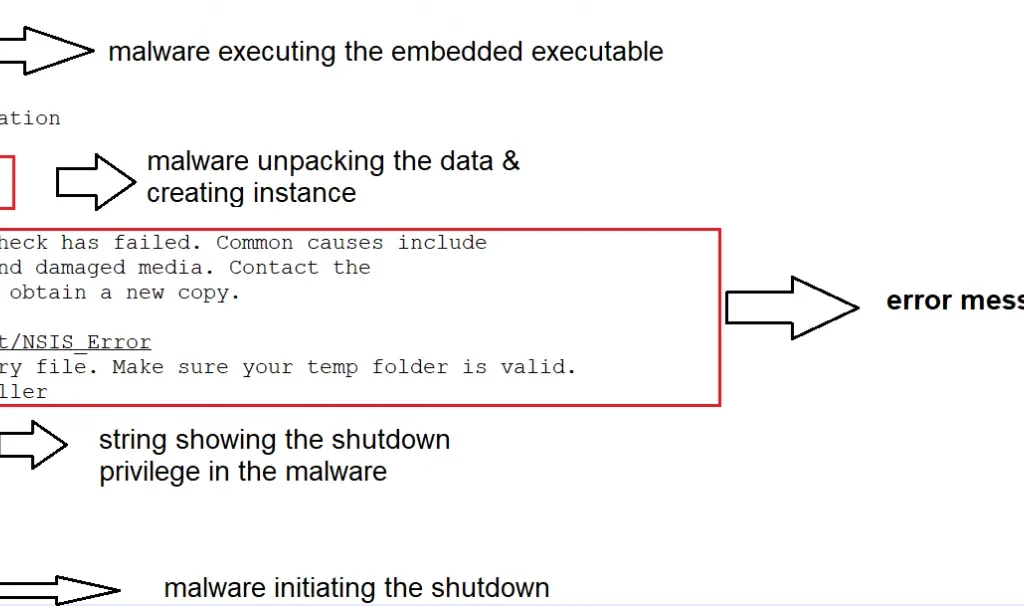
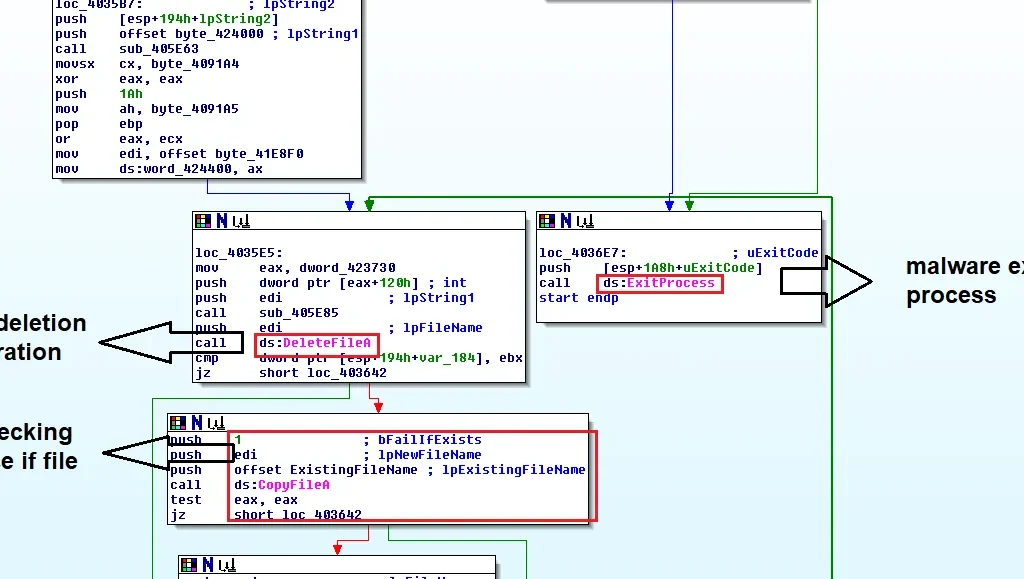
Below process describes the flow of malicious code which gathers victim system and file attributes and function calls.
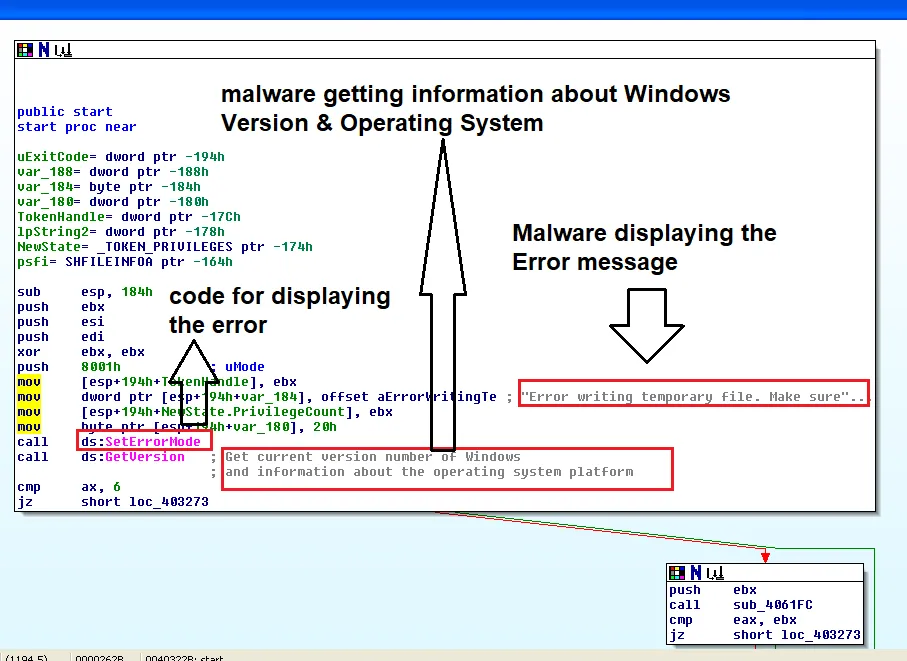
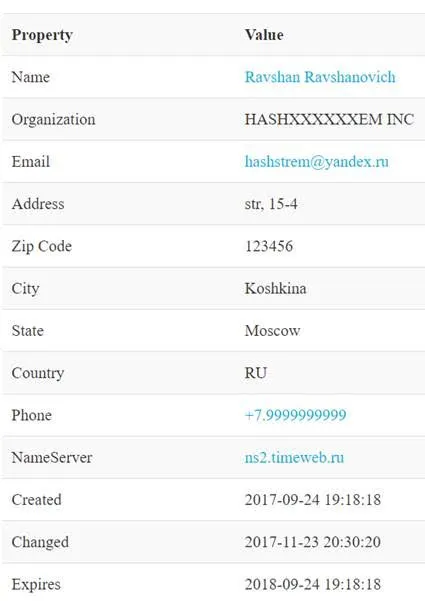
Further analysis on the C&C uncovered it was created in Russia in September last year:
Dynamic Analysis
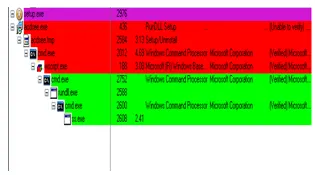
Upon executing the sample in a dedicated malware analysis environment, we saw a chain of processes being initiated as shown below, namely acdsee.exe, cmd.exe, wscript.exe, cmd.exe rundll.exe, cmd.exe, and ss.exe:
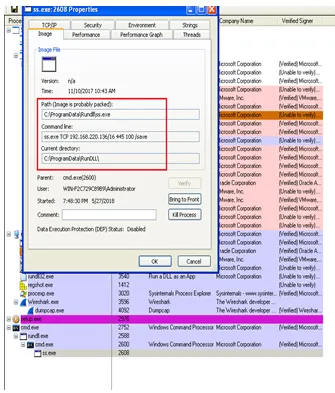
“ss.exe”, which has been dropped under “C:\ProgramData\Rundll”, establishes persistent communication with “TCP 192.168.220.136/16 445 100 /save”:
Next, “cmd.exe” (which is running as a non-existent process) starts and communicates with “192.168.220.136”:
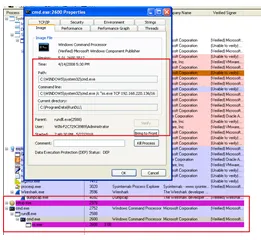
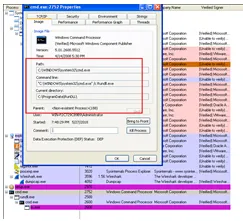
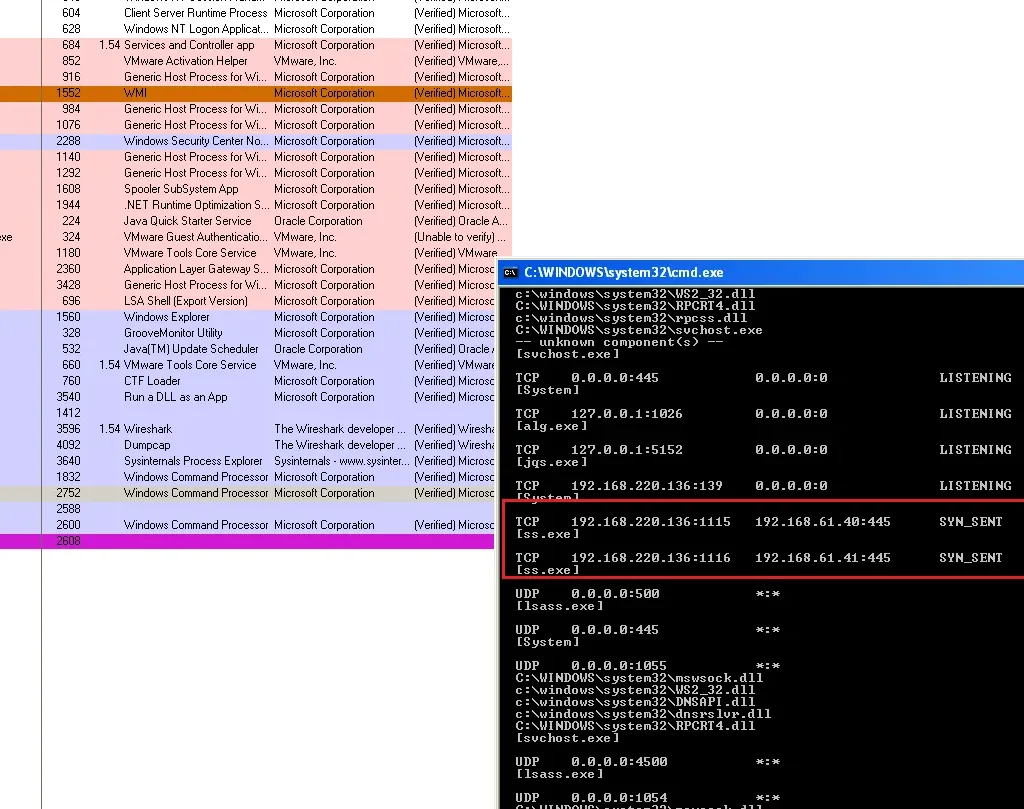
Ultimately, “cmd.exe”, “rundll.exe”, “cmd.exe”, and “ss.exe” are left running with communications towards the IP addresses “192.168.61.40” and “192.168.61.41”:
After some time, an error message (as mentioned in the static analysis) appears, pointing to the C&C, “h**p: //nsis [.]Sf [.]Net/NSIS_Error”:
A number of files were then dropped on to the system, some of which we’ll explore in further detail below:
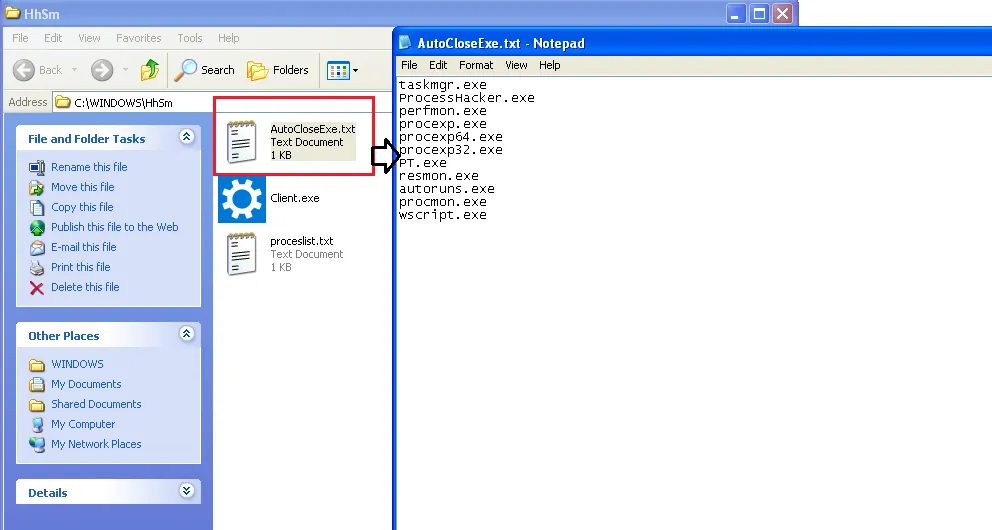
“AutoCloseExe.txt” was found present under “C:\Windows\HhSm”.
This file had all the details on which processes were executed in the victim’s machine:
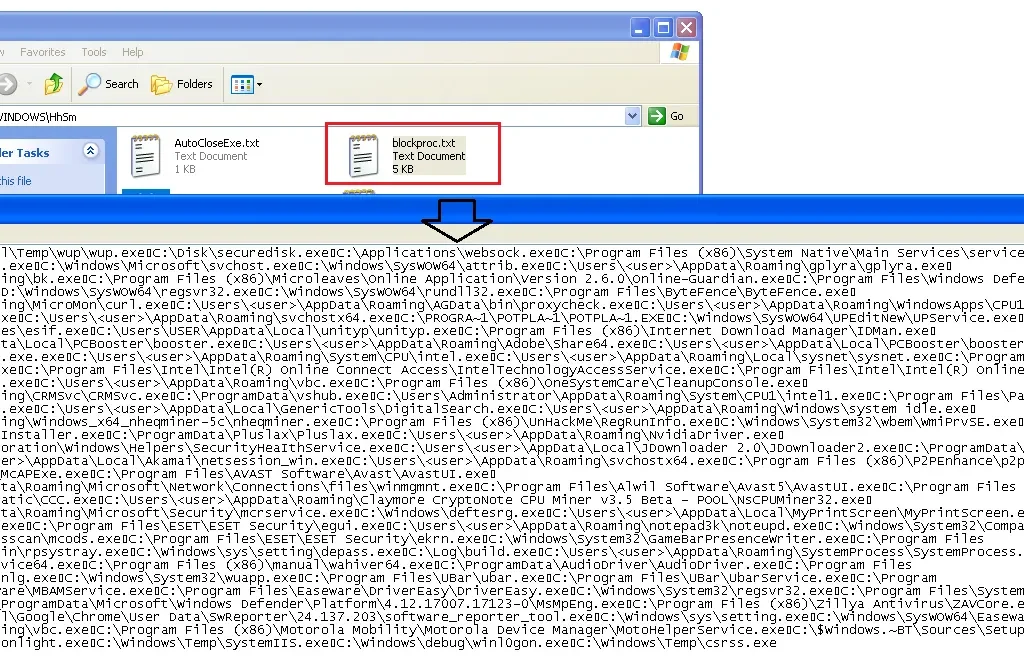
“Blocproc.txt” included details on all the software installed on the machine:
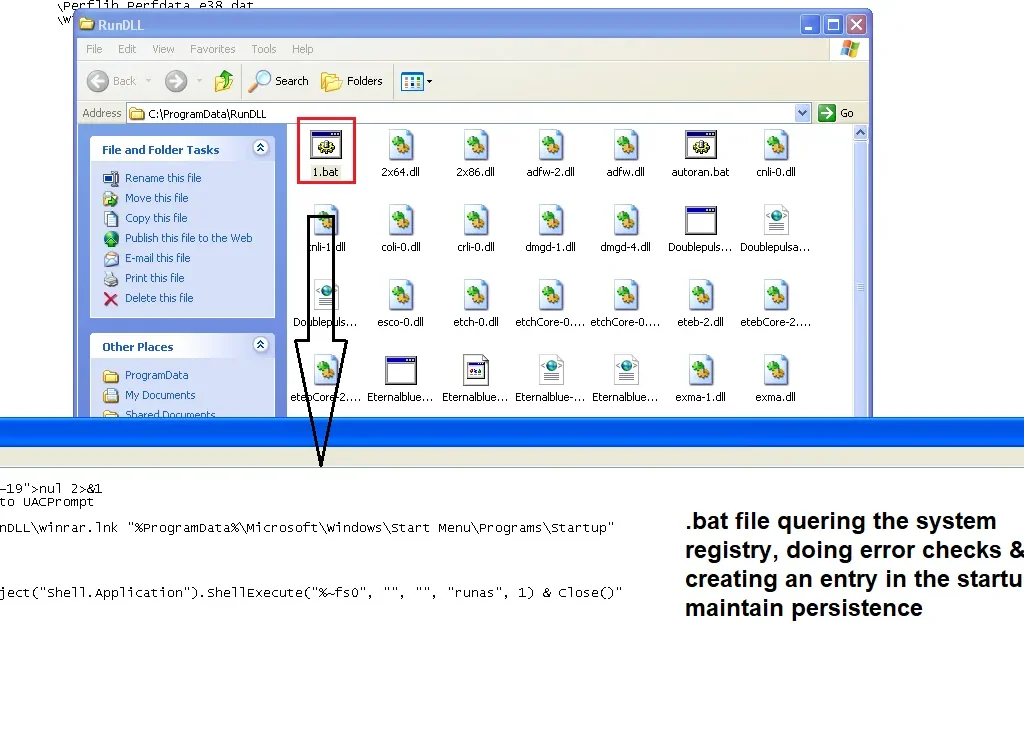
“1.bat” was present which we found querying the system registry, performing condition for error checks, and then creating a Startup entry to maintain persistence:
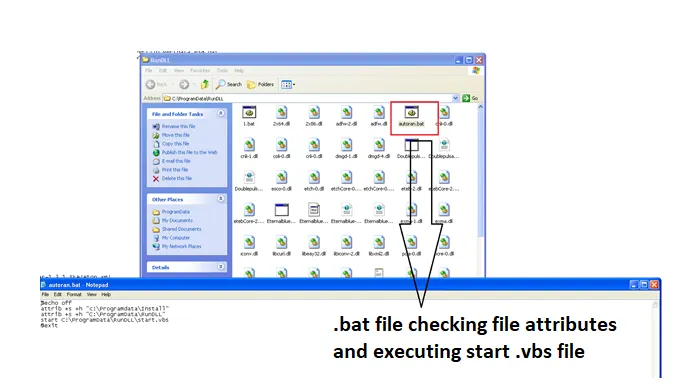
Another .bat file, “autoran.bat”, was responsible for checking file attributes and executing a “start.vbs” file:
Additionally, “C:\WINDOWS\HhSm\Client.exe” – a registry-value created file – establishes a connection with Russian Federation BOT IP address “92.53.96.179” with the domain name: hs-fileserver.info.
Command and Control
• H**p: //nsis [.]Sf [.]Net/NSIS_Error
• Mine[.]zarabotaibitok[.]ru
• IP Address: 92.53.96.179
Indicators of Compromise
MD5 Hash values of the dropped files:
• 6fa7482b165dc6689350d22c555de51f
• 63af4ca31a0d3f4729a6968564b232ea
• 293f75563f7fa64d1de6945aee4299f0
• 31d696f93ec84e635c4560034340e171
• 770d0caa24d964ea7c04ff5daf290f08
• 25313a0ad4154972b5770260ad594ed0
• ee2d6e1d976a3a92fb1c2524278922ae
• a539d27f33ef16e52430d3d2e92e9d5c
• 3c2fe2dbdf09cfa869344fdb53307cb2
• f82fa69bfe0522163eb0cf8365497da2
• 1ca9e6eb86036daea4dfa3297f70d542
• a05c7011ab464e6c353a057973f5a06e
• c24315b0585b852110977dacafe6c8c1
• a4e439ad454a379db68ab5b2c44a82aa
• a4e439ad454a379db68ab5b2c44a82aa
• d9b5b26f0423230e99768092f17919a3
• 3e5d06dc6e7890e1800cf24c9f599856
• 4ff94c163565a38a27cf997ad07b3d69
• 1f0669f13dc0545917e8397063f806db
• 47106682e18b0c53881252061ffcaa2d
• 24aa99837d14bee5da2e2339b07f9d4c
• 89b7dac7d9ce5b75b08f5d037edd3869
• 8c80dd97c37525927c1e549cb59bcbf3
• 756b6353239874d64291e399584ac9e5
• a6c04fca267b7b6a75dc59d6f50bd968
• a6c04fca267b7b6a75dc59d6f50bd968
• ba629216db6cf7c0c720054b0c9a13f3
• 649b368c52de83e52474a20ce4f83425
• 4803a7863da607333378b773b6a17f4c
• 43aac72a9602ef53c5769f04e1be7386
• f01f09fe90d0f810c44dce4e94785227
• 5adcbe8bbba0f6e733550ce8a9762fa0
• 9a5cec05e9c158cbc51cdc972693363d
• 6fe4544d00b77e0295e779e82d8f0fe5
• 00dd6b018c3c2d347df43f779715bca5
• 09836461312a3781af6e1298c6b2c249
• 30017e300c6d92e126bf92017c195c37
• 2f0a52ce4f445c6e656ecebbcaceade5
• b777086fd83d0bc1dccdc7c126b207d0
• 8969668746ae64ca002cc7289cd1c5da
• e53f9e6f1916103aab8703160ad130c0
• 9b80804a00bb6fa7f298d15c0947b2af
• c5fe643c7b2fb4a5e8f23411c561bb77
• c097fd043d3cbabcada0878505c7afa5
• 5e8ecdc3e70e2ecb0893cbda2c18906f
• 15191883753d0b230c4e89158261d4ac
• 0647dcd31c77d1ee6f8fac285104771a
• f0881d5a7f75389deba3eff3f4df09ac
• f61e81eaf4a9ac9cd52010da3954c2a9
• 8b0a4ce79f5ecdb17ad168e35db0d0f9
• 838ceb02081ac27de43da56bec20fc76
• 01d5adbfee39c5807ee46f7990f5fda7
• 46f7b320b13a4b618946042360215179
• 3e89c56056e5525bf4d9e52b28fbbca7
• d1aae806243cc0bedb83a22919a3a660
• 83076104ae977d850d1e015704e5730a
• 1fa609bc0d252ca0915d6aed2df7ccc2
• 6b7276e4aa7a1e50735d2f6923b40de4
• e4a7755973b32e44e4ec60beeb7809fe
• d8d6f3a3e75da9887c165781d5b31e31
• 66e0ee9a617f88f1a173ea2f0c585368
• 5b72ccfa122e403919a613785779af49
• 9744f0000284c2807de0651c7e0d980a
• e4ad4df4e41240587b4fe8bbcb32db15
Domains
• H**p: //nsis [.]Sf [.]Net/NSIS_Error
• Mine[.]zarabotaibitok[.]ru
Registry Value Created
HKLM\SYSTEM\CurrentControlSet\Services\AdobeFlashPlayerHash\ImagePath: “C:\WINDOWS\HhSm\Client.exe”
Mitigation and Countermeasures
While there are no specific countermeasures for Blouiroet, beyond using the IOCs listed above, below are the best practice steps one should take to minimise their exposure to such malware:
• Update antivirus to the latest signatures
• Exercise caution while clicking on email attachments
• Use strong passwords for data protection
• Make sure that systems are patched/updated with the latest softwar
On 2018-07-11


