The trojan called Bumblebee was created in C++ with the intention of attacking the Windows OS. It has the ability to collect system data, persist itself post execution, communicate with a C2 server, and receive and activate payloads like shellcode and DLLs which combines a lot of hooking and unhooking calls.
BumbleBee malware uses the DLLs to execute or inject payloads into a process from a hardcoded list after saving them to disc. Data structured as JSON and encrypted using RC4 is sent back and forth between C2 Server over HTTPS protocol. Additionally, a binary comparison of the code between Bumblebee and the Ramnit virus showed that there was a substantial degree of code commonality.
Bumblebee Trojan which is mainly distributed via phishing and spam emails, it is the replacement for Bazar-Loader malware. It delivers known attack frameworks and open-source tools such as Cobalt Strike, Shellcode, Sliver, Meterpreter, etc. Usually, ‘.EML’ contains an ‘.iso’ file – an archive file format to deliver the payload files such as [.LNK & .EXE or .DLL].
Infection Chain
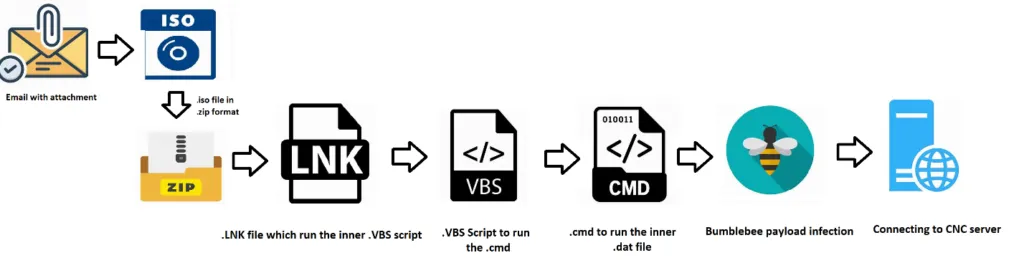
Recently, the Bumblebee campaign infected its victims by initial infection vectors of spam emails. The phishing email attachment contains the .ISO file. This image contains the payload file to infect the targeted victim machines. LMNTRIX CDC has been tracking another fresh infection chain that employs the PowerSploit framework for covert reflective injection of a DLL payload into memory; we have been tracking this sample in a fresh iteration of the Bumblebee malware loader.
As usual, the initial vectors may vary depending on their targets and we all know that the threat actors perform basic reconnaissance methodologies to decide their infection vector.
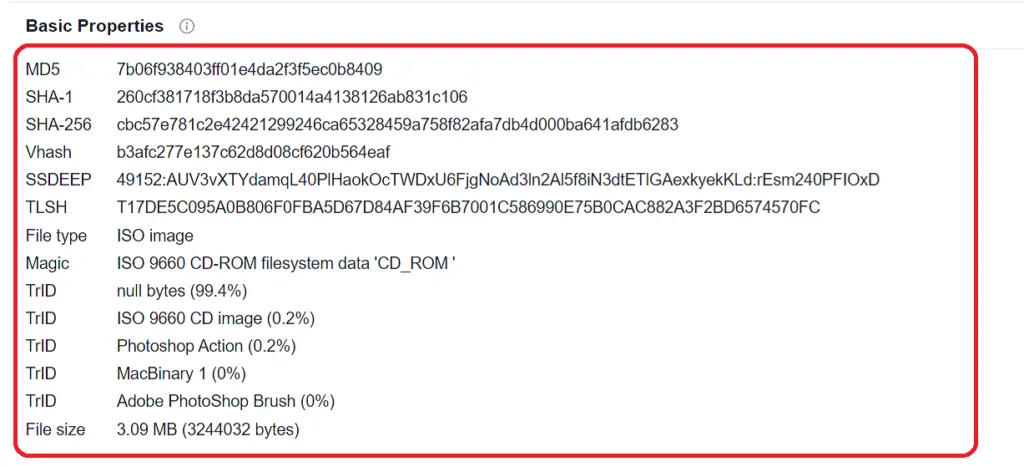
Sample Information
Technical Analysis of Bumblebee
Bumblebee’s code contains a single function that handles the initialization, deployment, response handling, and sending requests. Once the malware is launched on a compromised device, it gathers the victim’s information, then it communicates to the C2 server. Basically, this malware is used to fetch and run additional malicious payloads, such as Cobalt Strike, Sliver, and Meterpreter.
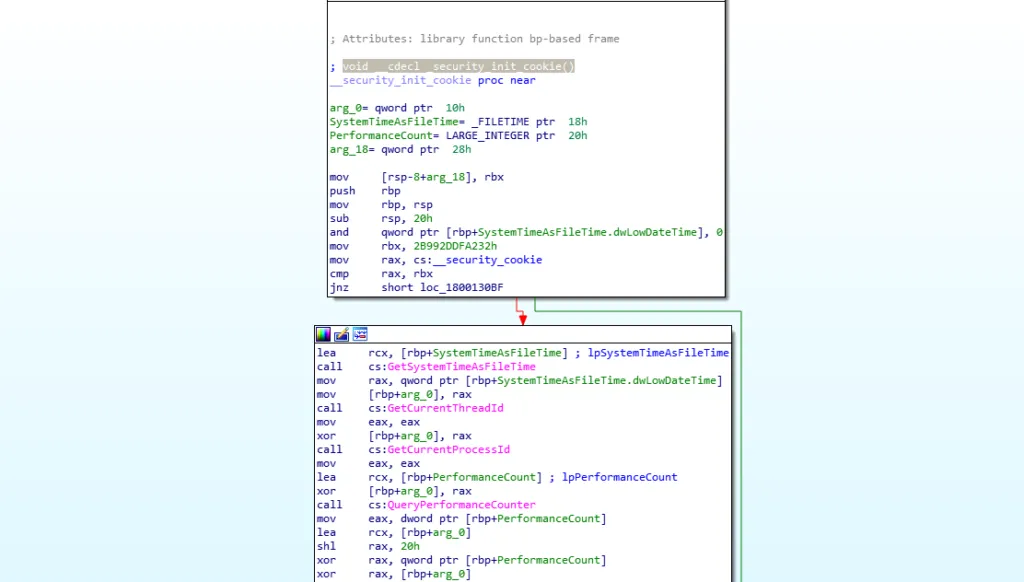
It’s compiled in Microsoft Visual C++, screenshot attached below,
Phishing Email containing the .ISO File
Why are ISO files being used?
ISO files are used to store file system copies of optical discs as a disc image format, but they essentially operate as an archive file format similar to zip, rar and cab formats. Also, malware authors know that many e-mail gateway scanners don’t scan ISO file attachments properly. This is because ISOs tend to be hundreds of megabytes in size, making them largely inefficient for the scanner to parse. It’s an effective method to evade security controls. However, ISOs can also be very small and may contain nothing more than a half megabyte malware binary. Now-a-days ISO files are very easy to open. This increases the chances of the target opening the file and infecting their victim machines.
Manual Extraction of ISO file
How does BumbleBee loader work?
Bumblebee contains a small malicious program whose goal is to download and execute additional payloads on compromised machines without detection. To achieve this, they use various techniques to inject or attach these payloads to existing legitimate processes. They also collect system information about the compromised computer that can later be used to uniquely identify the victim machine in the attackers’ command-and-control panel.
Script Files
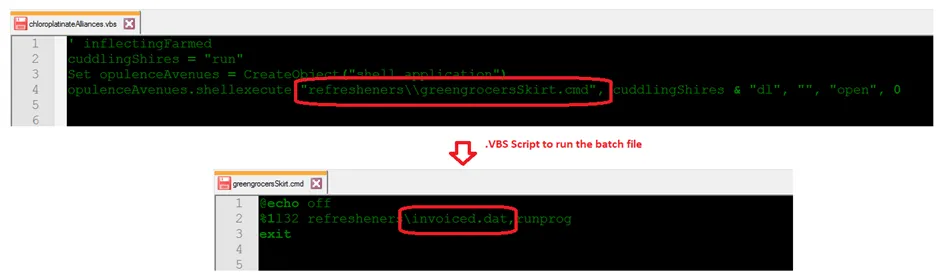
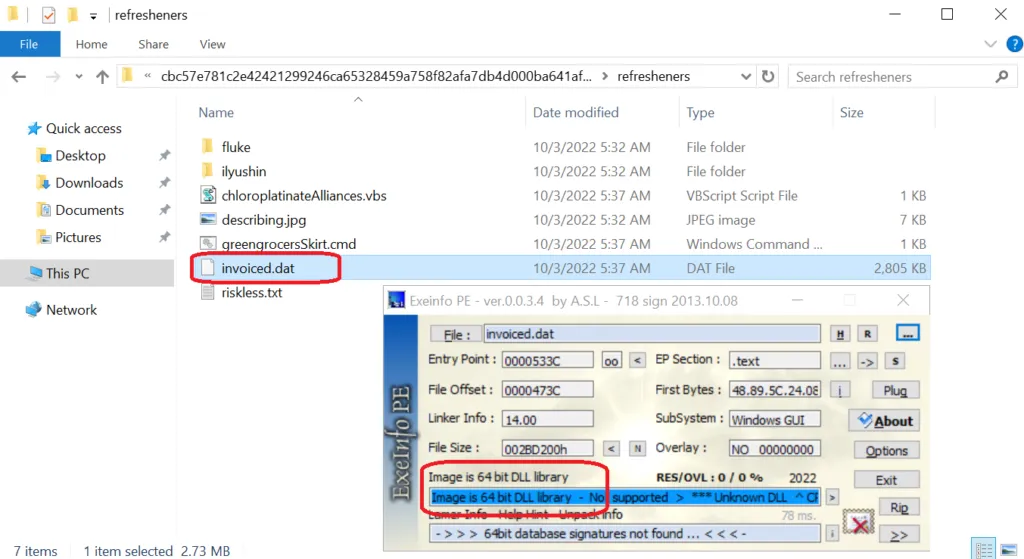
From the above-mentioned snap, the infection flow is very simple. Initially, the .LNK shortcut file triggers the .VBS script. Using a shell command, the .VBS script file executes the .CMD file, then it will call the {XXXXX.DAT} file. It’s the final payload file in .DLL format.
Analysis of .DLL payload file:
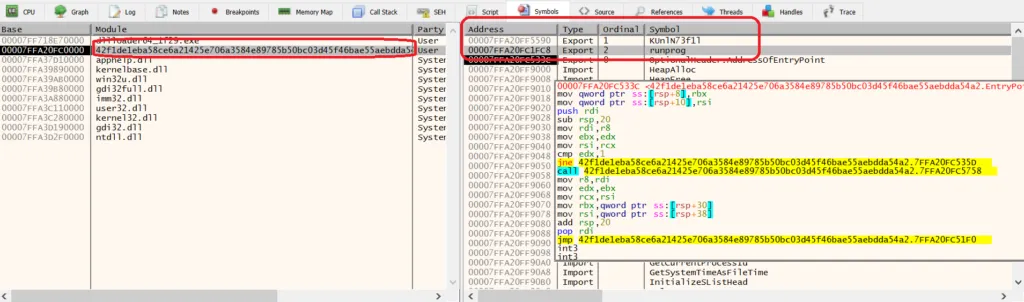
Imports & Export functions
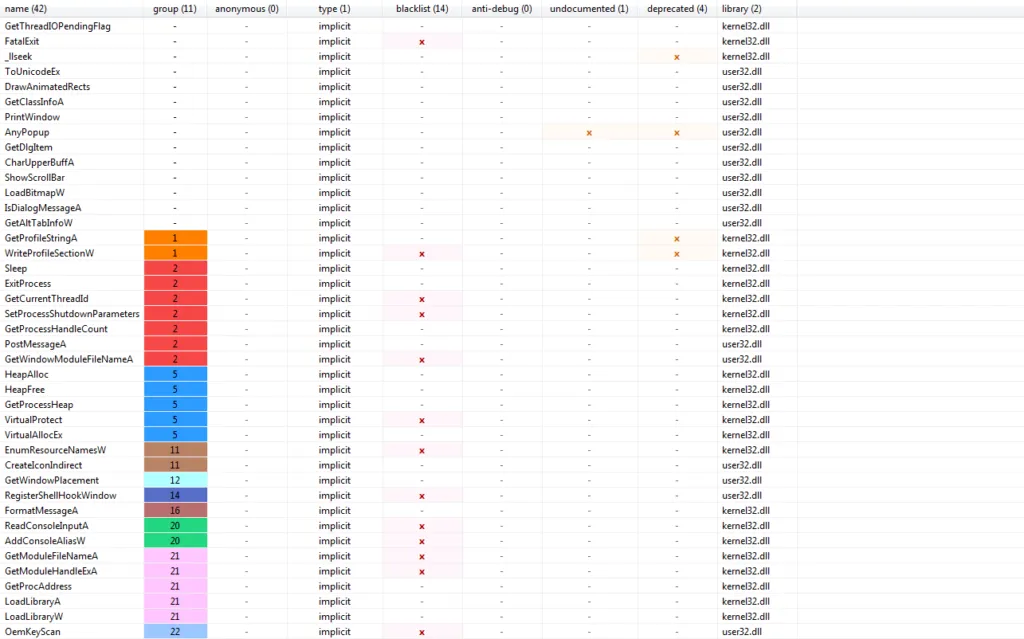
Calls to ExitProcess, IsDebuggerPresent, RegisterShellHookWindow represent anti-debugging and anti-VM checks in bumblebee’s malicious code.
Process Tree
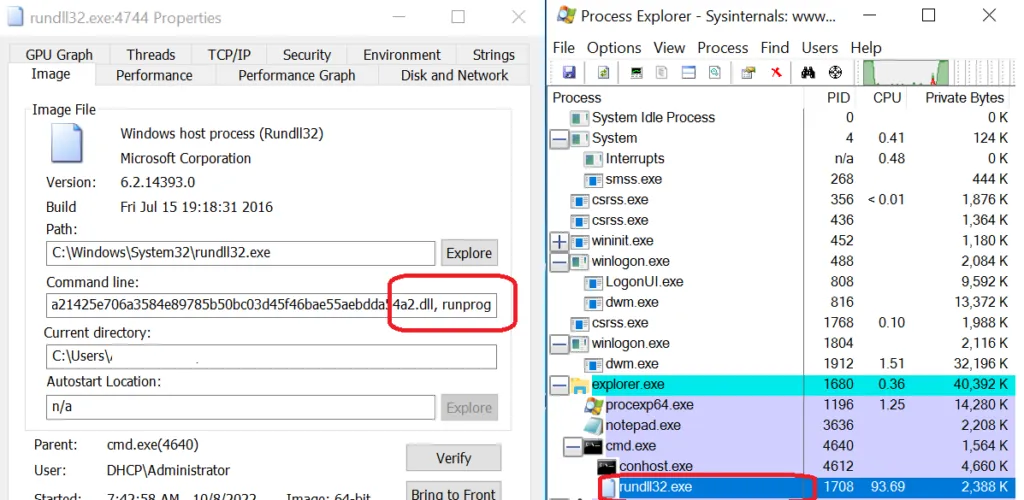
Here, we can see by using the runprXX export function to run the payload file, Once executed successfully then the infection starts. Every malware used to identify the virtual environment, likewise Bumblebee performs the following actions:
- Queries registry keys related to Virtual Machine-related software.
- Executes WMI queries to identify them.
- Identifies emulator by reading the respective registry keys.
- Identify the window name of the running process.
Indicators of Compromise for BumbleBee malware
BumbleBee Files
container.vhd (SHA256) 91d29cfe549d8c7ade35f681ea60ce73a48e00c2f6d55a608f86b6f17f494d0d
Quote.lnk (SHA256) 940182dd2eaf42327457d249f781274b07e7978b62dca0ae4077b438a8e13937
quotefile.ps1 (SHA256) d6cc3ac995484b99ed790b6f8ceb145492794eb5d01ec4a71123b9975e9bfd20
stage2.ps1 (SHA256) 5d000af554dcd96efa066301b234265892b8bf37bf134f21184096bdc3d7230b
payload.dll (SHA256) 0b0a5f3592df7b538b8d8db4ba621b03896f27c9f112b88d56761972b03e6e58
Bumblebee ISO samples
9eacade8174f008c48ea57d43068dbce3d91093603db0511467c18252f60de32
6214e19836c0c3c4bc94e23d6391c45ad87fdd890f6cbd3ab078650455c31dc8
201c4d0070552d9dc06b76ee55479fc0a9dfacb6dbec6bbec5265e04644eebc9
1fd5326034792c0f0fb00be77629a10ac9162b2f473f96072397a5d639da45dd
01cc151149b5bf974449b00de08ce7dbf5eca77f55edd00982a959e48d017225
Bumblebee Samples Analyzed
c70413851599bbcd9df3ce34cc356b66d10a5cbb2da97b488c1b68894c60ea69
c78290da99475f965ce54f737e0927a9855e03c9a27f2ee7a797562533779305
14f04302df7fa49d138c876705303d6991083fd84c59e8a618d6933d50905c61
76e4742d9e7f4fd3a74a98c006dfdce23c2f9434e48809d62772acff169c3549
024f8b16ee749c7bb0d76500ab22aa1418cd8256fb12dcbf18ab248acf45947e
2691858396d4993749fec76ac34cf3cc3658ee3d4eaf9c748e2782cfc994849d
6bc2ab410376c1587717b2293f2f3ce47cb341f4c527a729da28ce00adaaa8db
083a4678c635f5d14ac5b6d15675d2b39f947bb9253be34d0ab0db18d3140f96
21df56d1d4b0a6a54bae3aba7fe15d307bac0e3391625cef9b05dd749cf78c0c
31005979dc726ed1ebfe05558f00c841912ca950dccdcdf73fd2ffbae1f2b97f
2d67a6e6e7f95d3649d4740419f596981a149b500503cbc3fcbeb11684e55218
f98898df74fb2b2fad3a2ea2907086397b36ae496ef3f4454bf6b7125fc103b8
3c0f67f71e427b24dc77b3dee60b08bfb19012634465115e1a2e7ee5bef16015
ca9da17b4b24bb5b24cc4274cc7040525092dffdaa5922f4a381e5e21ebf33aa
82aab01a3776e83695437f63dacda88a7e382af65af4af1306b5dbddbf34f9eb
a5bcb48c0d29fbe956236107b074e66ffc61900bc5abfb127087bb1f4928615c
07f277c527d707c6138aae2742939e8edc9f700e68c4f50fd3d17fe799641ea8
68ac44d1a9d77c25a97d2c443435459d757136f0d447bfe79027f7ef23a89fce
13c573cad2740d61e676440657b09033a5bec1e96aa1f404eed62ba819858d78
7024ec02c9670d02462764dcf99b9a66b29907eae5462edb7ae974fe2efeebad
ee27cceac88199bf3546e8b187d77509519d6782a0e114fc9cfc11faa2d33cd1
b2c28cdc4468f65e6fe2f5ef3691fa682057ed51c4347ad6b9672a9e19b5565e
BumbleBee Domains
al-ghurair[.]us
amevida[.]us
awsblopharma[.]com
avrobio[.]co
brightlnsight[.]co
belcolnd[.]com
craneveyor[.]us
conlfex[.]com
elemblo[.]com
faustel[.]us
kvnational[.]us
lagauge[.]us
lsoplexis[.]com
modernmeadow[.]co
missionbio[.]us
opontia[.]us
prmflltration[.]com
phxmfg[.]co
richllndmetals[.]com
revergy[.]us
Here are some common C2 Server IP addresses we have been tracking,
104[.]168[.]201[.]219 142[.]11[.]234[.]230 145[.]239[.]30[.]26
145[.]239[.]135[.]155 145[.]239[.]28[.]110 146[.]19[.]173[.]202
146[.]70[.]125[.]122 152[.]89[.]247[.]79 185[.]17[.]40[.]189
185[.]62[.]58[.]175 205[.]185[.]122[.]143 205[.]185[.]123[.]137
209[.]141[.]46[.]50 209[.]141[.]58[.]141 51[.]210[.]158[.]156
51[.]68[.]144[.]94 51[.]68[.]145[.]54 51[.]68[.]146[.]186
51[.]68[.]147[.]233 51[.]75[.]62[.]99 51[.]83[.]250[.]240
51[.]83[.]251[.]245 51[.]83[.]253[.]131 51[.]83[.]253[.]244
54[.]37[.]130[.]166 54[.]37[.]131[.]14 54[.]38[.]136[.]111
54[.]38[.]136[.]187 54[.]38[.]138[.]94 54[.]38[.]139[.]20
Note: The number of BumbleBee C2 servers in the wild, continue to increase by the day.
MITRE ATT&CK Tools & Techniques Used By BumbleBee
| ID | Tactic | Technique |
| T1566 T1190 | Initial Access | Phishing Exploit Public-Facing Application. |
| T1059 | Execution | Command and Scripting Interpreter |
| T1497 | Defense Evasion | Virtualization/Sandbox Evasion Check |
| T1053 | Persistence | Scheduled Task |
| T1012 T1082 | Discovery | Query Registry System Information Discovery |
| T1552 | Credential Access | Unsecured Credentials |
| T1021 | Lateral Movement | Remote Services |
| T1496 | Impact | Resource Hijacking |


