Today I’m going to take a look at a member of the Click-Fraud malware family – ZeroAccess Trojan. Now, because it’s function isn’t as apparent as that of ‘ransomware’ or ‘credential stealing’, I’ve included diagrams and additional information on how this scheme works at the end of the post. As a quick definition though, click fraud involves the malware highjacking the user’s search engine results, pushing advertisements from a chosen Ad Server. The cyber criminals profit here as they’re generally hired as middlemen/third parties of an agency with advertisements on that server.
In previous iterations, the malware was also known to mine bitcoin. This makes a lot of sense – if you have access to one of the world’s largest botnets, why not send it to work? Its authors, however, released a patch sometime in 2013 which removed the mining functionality from the Trojan, most likely due to its futility in the face of bitcoin’s rapidly increasing hash rate.
Recently: There’s some interesting history to this strain. Not only is it the first to commercialize the Click Fraud scheme – and run on the power of one of the world’s largest botnets – but it also still exists despite a concerted effort in 2013 from Microsoft, Europol and the FBI to erase it from existence.
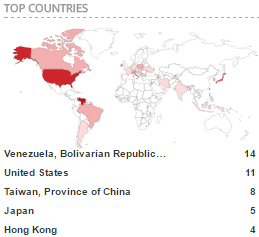
According to Shodan’s Malware Hunter tool, ZeroAccess Trojan’s botnet is currently operating on computers across 70 countries, with Venezuela and the United States being the most heavily infected.
Below are Malware Hunter’s infections stats for ZeroAccess Trojan as of May 29, 2017:
Propagation: The Trojan’s primary propagation method is ‘ExploitKit’, which involves the Botnet infecting an Ad Server, thereby spreading the malware throughout the server’s network of web-sites. This propagation method proves to be an extremely efficient channel through which to spread malware.
Another method of propagation used by the Trojan’s authors is to develop highly-targeted spear phishing emails, attempting to lure victims to click on a malicious link embedded into the email.
Functionality:
The Trojan’s M.O is to create a backdoor on the infected machine, thus adding it to the botnet, after which point it will be shortly sent to work generating revenue.
Below, we’ll analyze a recent sample::
MD5: 41b0aac4362135e3643a6b603b9744d1
Filename: SourceEnclosure.exe; MultimediaAlaska.exe; Necipemujuga hesopo ji
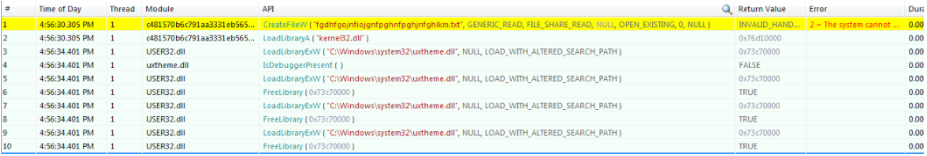
To better understand the Trojan’s functionality, we debugged the malicious payload. The first function observed is the creation of a randomly-named text file, executed by the function “CreateFileW”.
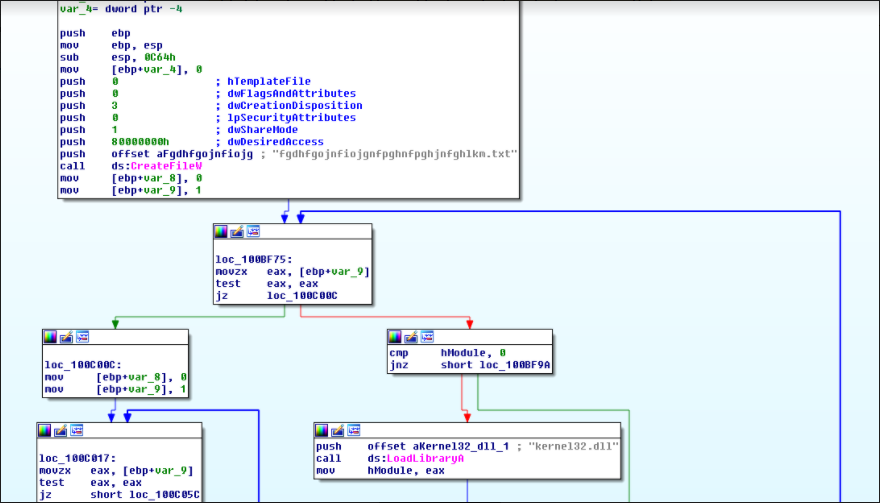
Once the random file has been created, a “LoadLibraryA” function is called upon the stack for using “Kernel32.dll” file in the specified memory location. The dll file can be broken down into multiple modules, each used for specific functions in different locations, as highlighted in the image below:
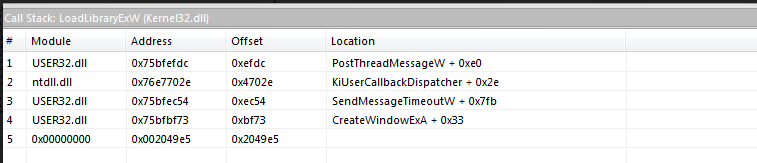
The above modules illustrate the stealth of ZeroAccess Trojan once executed on the infected machine. One particular behavior we can observe is the exploitation of the CVE-2015-1701 local privilege vulnerability.
CVE-2015-1701 is a Windows zero day that was discovered in April 2015 by FireEye researchers. The exploit executes a callback using the flaw to pull data from the System process before executing code through escalated privileges. After running code through the kernel, stolen system tokens are then modified to mirror System process privileges.
In this sample, there are two mechanics which exploit this vulnerability – Exception Handling and the setting of a hardware breakpoint. From the call stack function above, we can see that the hardware breakpoint has been set to “kiUserCallbackDispatcher”.
Importantly, the API function call loads “Uxtheme.dll” via LoadLibraryA to check for the API “IsDebuggerPresent()”. This allows the Trojan to determine whether or not it is being debugged, so that it can modify its behavior if necessary.
Indicators of Compromise:
Apart from code analysis, there are certain Registry Values which ZeroAccess Trojan also manipulates:
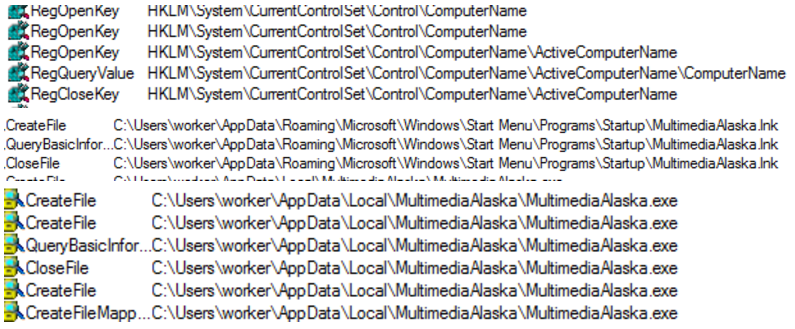
The Trojan uses the file path, C:\Users\Worker\AppData\Local\MultimediaAlaska\MultimediaAlaska.exe, to execute the Remote Access Trojan. The IP addresses the Trojan uses as Command and Control Servers to download further instructions are listed below:
- Connection: 103.219.22.63:443
- Connection: 50.116.5.69:443
- Connection: 81.88.24.211:443
Further Technical Information and Diagrams:
As mentioned at the start of this post, the mechanics behind Click-Fraud malware aren’t as easily explained as those of other malware families. Below, you’ll find additional technical information and diagrams on how this Trojan operates, makes money and impacts its victim.
First, to dispel any confusion, ‘compromised Ad Servers’ doesn’t mean the servers are acting as a malware repository. It means that through URL redirection techniques, and the injection of malicious JavaScripts and iframe modules, legitimate traffic is being redirected to compromised Ad Servers.
Below is a diagram of what a normal user interaction with an uncompromised Ad Server looks like:
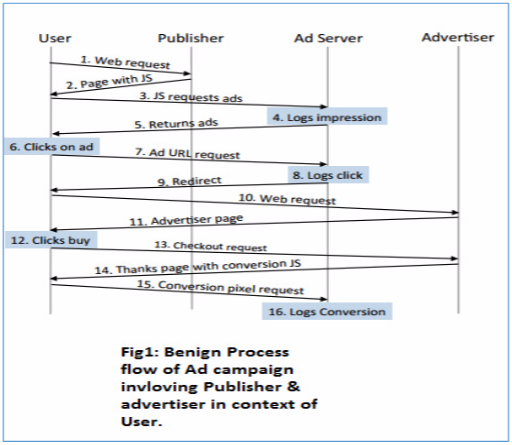
While the above image depicts what a normal user interaction would look like, when a user is infected with ZeroAccess, the Command and Control server issues a number of commands, one of which is ‘Traffic Redirection’.
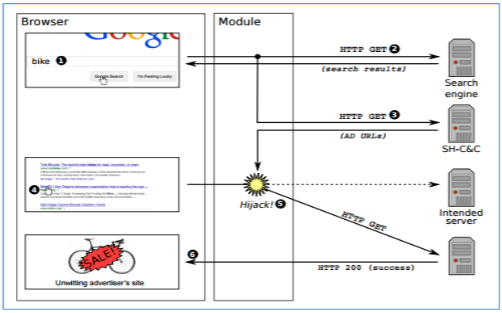
The ZeroAccess Trojan module then controls URL redirection and thus acts as an interface. The below diagram illustrates this process, as well as showing how iframe module injection fits into the functionality:
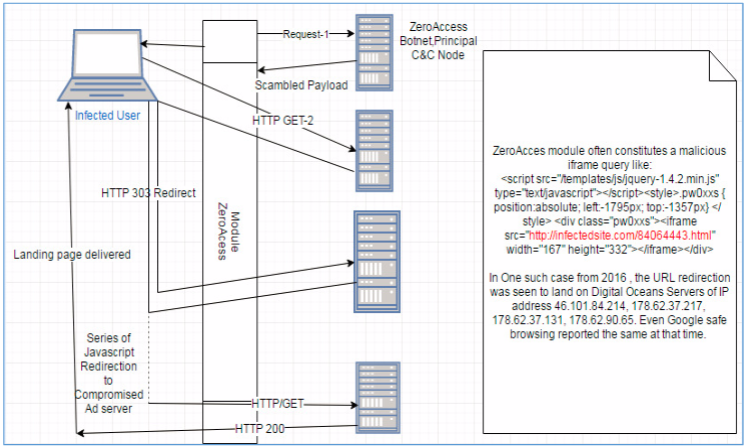
Finally, the below diagram shows the ‘Search Engine Hijacking’ or ‘Click Fraud’ functionality of ZeroAccess – the primary process through which the Trojan’s authors generate revenue: