
In the world of cyber security, APT (Advanced Persistent Threat) groups are perhaps the most feared. This is because they are the most well-equipped and technically proficient threat actors, leading many to believe they have government-backing.
One of the most infamous, APT28 (aka Fancy Bear), was first identified in 2004 by Trend Micro. Since their discovery, they have been implicated in multiple high-profile attacks against Government entities, diplomatic missions and media organisations.
Most recently, however, researchers have implicated APT 28 in attacks against hotels in several European countries.
Recently: APT 28’s most recent attack targeted businesses in the hospitality industry over July and August this year. FireEye researchers were the first to identify the campaign in which a malicious ‘Hotel Reservation Form’ was sent to target organisations in a classic spearphishing campaign.
Once the document was opened, and macros enabled, Fancy Bear’s signature malware – GAMEFISH – was dropped on to the terminal.
After successfully gaining access, APT28 moved laterally through the network to seek machines that controlled both guest and internal Wi-Fi networks. After these were compromised, the group aimed to steal usernames and passwords which would allow further privilege escalation.
Technically: In the past week, we discovered a sample from the above attack campaign and conducted the following analysis:
Initially we spotted the following domains in the client logs:
mvtband(.)net
mvband(.)net
https://virustotal.com/#/url/fd9cf2adc77595a8977188866c03986e4f70bf2bc6d0dbe5a150aaa8c025feee/detection
https://virustotal.com/#/url/d8a03dbf5409952ea201e11d808faabef555ed96c9f37ffe9769f6694b21b6be/detection
These domains triggered an alert as our threat intelligence feed identified them as Command and Control (C&C) servers. Our LMNTRIX HUNT team then scoured the logs and, by identifying the infected host, we found the malicious document and continued our analysis:

Figure 1 Malicious Document
– C:\Documents and Settings\fancybear\Hotel_Reservation_Form.doc
(78600 bytes) – binary
• Found ZIP archive
• Packed Unpacked Perc Date/time Filename
• 431 1819 23.7 01.01.1980 [Content_Types].xml
• 239 590 40.6 01.01.1980 _rels/.rels
• 342 1601 21.4 01.01.1980 word/_rels/document.xml.rels
• 4343 63115 6.9 01.01.1980 word/document.xml
• 437 1503 29.1 01.01.1980 word/footnotes.xml
• 434 1497 29.0 01.01.1980 word/endnotes.xml
• 191 277 69.0 01.01.1980 word/_rels/vbaProject.bin.rels
• 531 531 100.0 01.01.1980 word/media/image3.gif
• 200 392 51.0 01.01.1980 word/media/image2.wmf
• 197 392 50.3 01.01.1980 word/media/image1.wmf
• 7028 15872 44.3 01.01.1980 word/vbaProject.bin
• 1571 6795 23.2 01.01.1980 word/theme/theme1.xml
• 449 1367 32.9 01.01.1980 word/vbaData.xml
• 6354 30398 21.0 01.01.1980 word/settings.xml
• 47830 95561 50.1 01.01.1980 docProps/app.xml
• 2647 22908 11.6 01.01.1980 word/styles.xml
• 416 815 51.0 01.01.1980 docProps/core.xml
• 549 1816 30.3 01.01.1980 word/fontTable.xml
• 389 928 42.0 01.01.1980 word/webSettings.xml
• 74578 248177 30.1 Total (19 files)
The above list is the document’s internal files. One particular file which perked our interest was “vbaproject.bin” which we extracted for further analysis with officemalscanner.
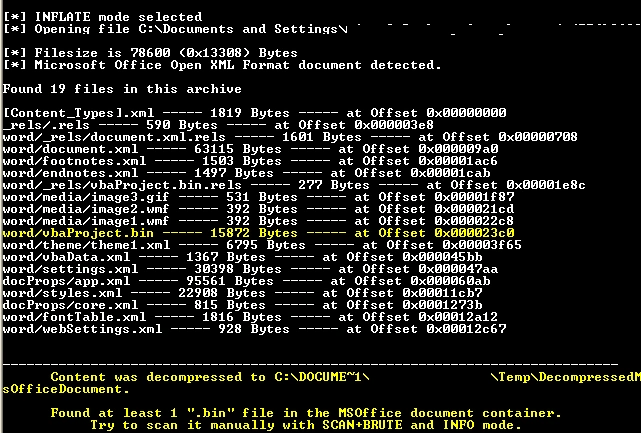
Figure 2 Extracted contents of doc file
The below analysis on the vbaproject.bin file gives us a better understanding of this sample’s behaviour:
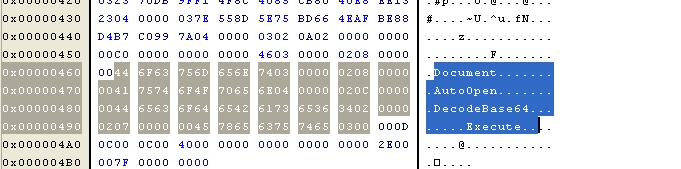
Figure 3 Interesting strings
Here we see base 64 being used for encoding and decoding – the decoded file gets saved in the AppData location:
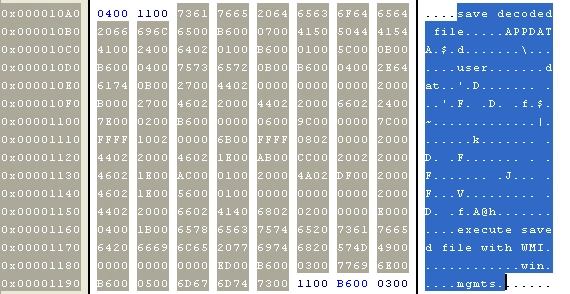
Figure 4 Decoded File Saved in AppData location
The saved file is then executed using WMI and then calls for rundll32.exe to execute supporting files, as seen below:

Figure 5 Saved file execution and registering supporting files
The following files are then created in the AppData location: mvtband.dat, mrset.bat and user.dat. This mvtband.dat file is the dll file which is registered using rundll32.exe. The file is used as a C&C for APT28. The user.dat file writes the mvtband.dll file and asks the batch file to execute it.
Prevalence: APT 28 has been implicated in multiple attacks, all of which have targeted high-profile victims or institutions – typically these are seen as espionage exercises designed to gather high-value diplomatic intelligence. For example, it is widely thought the ultimate targets of the recent campaign against the hospitality industry was guests staying at the hotels, rather than the hotels themselves.
As business travellers typically rely on the Wi-Fi networks of the hotels at which they stay, it is easy to see why commandeering the hotel’s Wi-Fi would be an incredibly effective way to target guests.
The group is known for using multiple attack techniques, rarely relying on the same methods. For example, in 2015 six zero-day exploits were attributed to APT28:

Figure 6 Zero Day exploits attributed to APT28 in 2015
Mitigation: For businesses in the hospitality industry, once an alert is received it is best to unplug the machine from the network. Simple yara rules can scan for the existence of the malicious files in the host and removal scripts will easily search in the specified locations and delete them. We recommend businesses block mvtband(.)net and mvband(.)net in the proxy and firewall.
For users, always exercise caution when dealing with attachments from unknown users. Travellers – particularly business travellers – should limit their reliance on public Wi-Fi networks.
Targets: APT28 has been linked to multiple attacks against high-profile targets. Past campaigns include the April 2015 attack on the French television network TV5Monde, the March 2016 breach of the U.S. Democratic National Committee, the December 2014 cyber-attack on the German Parliament, the August 2016 breach of the World Anti-Doping Agency, and a campaign in February 2015 to target members of the Dutch Safety Board who were investigating the downing of Malaysian Airlines Flight 17 over Ukraine.
Attribution: As always, it is incredibly difficult to attribute an attack with 100 per cent certainty. That said, the widely held belief is that APT28 is sponsored by the Russian Government.


