
Crysis is a type of ransomware that has been around since early 2016. Essentially, once the payload has been opened, Crysis encrypts all your files and data and directs you to make a payment with bitcoin in order to recover your files.
Recently: Earlier this year,in the wake of numerous sanctions placed upon Russia placed by Western governments in response to the annexation of Crimea, Crysis was used in attacks with a political flavour – attacks which included a satirical political cartoon on the ‘ransom letter’ page.
An image of this ransom letter page is below:

Victims are forced to pay a six bitcoin ($6,500 USD) ransom in order to have their files decrypted. The ransom note gives those infected five days to purchase the decryption tool and warns that files will be permanently deleted if third party tools are used to try and recover data.
Technically: Now, let’s take a look at some of the coding under Crysis’ hood.
One of the ransomware’s particularly interesting features is the encryption technique it uses. A combination of RSA and AES algorithms encrypt the files and the network share drive of the infected machine. Also, it is able to infect both the Windows and MAC platforms as well as virtual platforms connected to the victim machine.
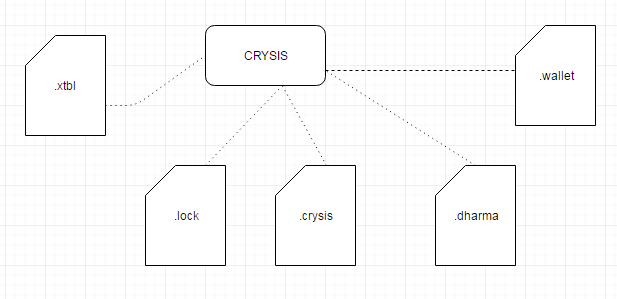
Keeping with the encryption theme, another distinct characteristic is the encrypted file type extensions. Once on the victim’s machine, file type extensions are changed to unique names in order to help mark the ransomware. Some of the file type extensions Crysis uses are below:
We found a number of ransomware samples this year, so let’s look at the code from one such sample below:
MD5: 5a8f288a70d4f3eef99af34bb3d10217fc7fd6d6bb6a13c1c8db5aee7bef40b4
Filename: Dakini.exe
The file at the time of installation copies itself to locations like:-
%localappdata%\%dakini%.exe
%windir%\system32\%dakini.exe
The following Registry value changes were also observed by the Malicious executable to run on system startup:-
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
Once the file is encrypted it drops a ‘How-To-Decrypt’ “readme.txt”/ “how_to _decrypt.html” on the /User/Desktop. In some cases, the Desktop Background is also changed to show ransom demands.
The variants identified in February 2017 were seen to exploit the Remote Desktop Protocol connections through brute-force attacks.
This variant – dubbed ‘Sanctions 2017’ – is a variant of the Crysis/Dharma family and uses the “.wallet” file extension on encrypted files. The malware falls under the category of “Advanced Malware” for the capabilities it shows such as information stealing and the ability to control voice recording features on infected machines.
The exploitation phase of the threat cycle shows a few additional features like:
- Using Malicious Scripts to spread the infection
- Deploying Exploit Tool kit to connect to the Command and Control server
- High degree of obfuscation on the malicious code to hide the attack platforms
Prevalence: According to New Jersey Cybersecurity (ROIC),variants of the Crysis ransomware made up about 64 per cent of all ransomware attacks last year.
Mitigation: During the first few months of 2017, a number of companies released free decryption tools designed to help Crysis victims recover their files and data. However, as with all pieces of malware, the development cycle means that each new variant nullifies the old decryption tool, meaning that keeping pace with attackers is a difficult task. With the latest “Sanctions 2017” variant, some steps on how to remove the ransomware are available here.
Targets: Crysis was used to target large health sector organizations, financial institutions and smaller scale business – particularly those in North America and Europe.
Attribution: We don’t know a lot about the attackers behind the latest Crysis campaign. While the political cartoon leads us to believe the attackers are either Russian or sympathetic to Russian interests, we do know that the actor behind this campaign uses an @india.com email domain address as the primary contact to demand ransom. Additionally, we have seen reports on security forums stating that victims have not received the decryption tool despite paying the ransom demands.
It further proves that warning from the security researchers to not pay those criminals are true and waiting patiently for the decryption tool is the best approach. Also this shows the impact of ransomware on the business operations and organizations are finding hard to run without requisite data.


