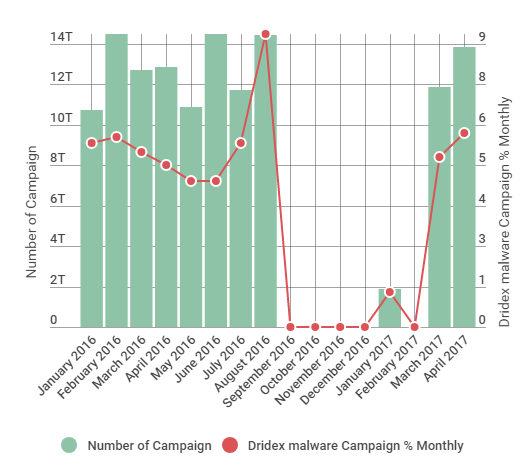
The credential-stealing Dridex malware family has typically been used to steal banking credentials and target Financial Institutions – with a particular focus on the Windows platform. It first surfaced in 2012 and, until recently at least, its exploit of choice was malicious macro-mache documents delivered as spam. Dridex distribution disappeared for seven months from August 2016 before recently resurfacing.
Recently: In January 2022, the actors behind Dridex quickly adapted to exploit a newly discovered flaw. They were rapidly able to weaponize a Microsoft zero-day which they used to target millions of recipients, primarily in Australia. Email attachments were still the favored delivery method, however the attachment was now an RTF file purporting to be a scanned document. Once the user opened the file and agreed to ‘Enable Editing’, the exploit executed.
Microsoft patched the zero-day Vulnerability (CVE-2017-0199) in its April Patch Tuesday release.
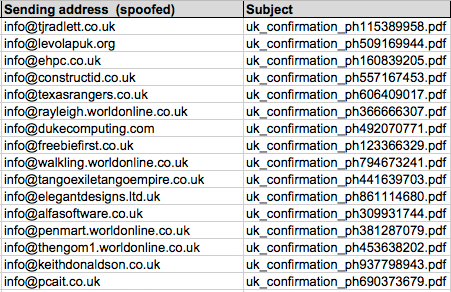
Technically: In this year’s return, the campaign continued to use email and malicious attachments as the preferred deliver method. A collection of spoofed sender addresses are included below:
In the days leading up to April’s zero-day campaign, Dridex’s authors were carrying out one of their more traditional campaigns. A lot has been written about the zero day campaign, so rather than parrot what others have written, I suggest you read Proofpoint’s analysis. Instead, we’re going to take a closer look at the initial campaign because this is more likely to mirror their next attack.
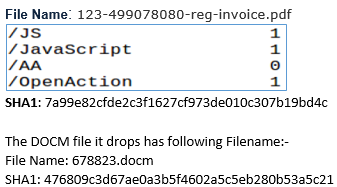
The first campaign included .pdf attachments with two JavaScripts which dropped one or more document (.docm) files into the infected host at the “TEMP” folder.
The malicious PDF also contained code to understand the targeted environment’s proxy settings and Windows installation date.
The dropped (.docm) file doesn’t contain any readable content but rather contains malicious VBA script where the URL to download the actual payload has been coded:

The payload from the above malware repositories contains the following file attributes:
Filename: 117da8ef79cb0d96c1c803709bd4827f.exe
Description: Windows PE32 executable
SHA: 6739c782d114307deaac42120a7061f51f9e74a86f1e60664997a269784143f2
Analyzing the downloaded PE32 windows file further shows us the “.rdata” section has the highest entropy value. The code randomness in this section means it might be responsible for accessing both the executable code and malicious memory.

Let’s take a closer look at the emails the attackers were sending. A number of spoofed addresses from UK retailer 123-reg were used in the campaign:
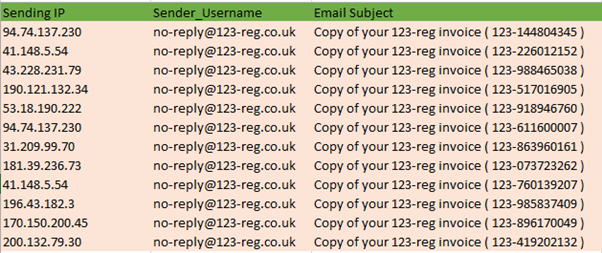
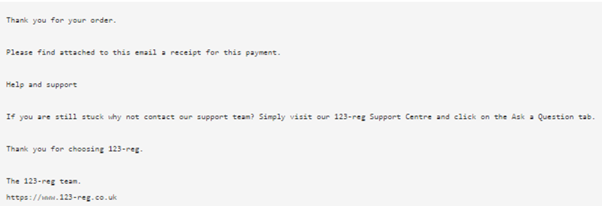
These addresses were used to send a phishing email posing as 123-reg’s customer service team. Each email contained the malicious PDF file. The body of the email is below:
The PDF attachment was basically TrojanDownloader:O97M/Donoff, which contains two JavaScripts and one embedded DOC file with macro-enabled code. This is a classic Dridex play that we expect to see again in the future. The DOCM file drops itself on multiple locations once executed by the User (opening the PDF file).
The dropped file downloads the actual payload from the hardcoded URL’s specified on the macro code of the DOCM file. However, one particular divergence we see in this campaign is that the URL mentioned to download the Dridex payload in the dropped DOCM file is unique and varies from sample to sample. This is believed to allow DRIDEX to maximize its download share while evading URL reputation services.
Prevalence: While Dridex was largely dormant for more than half a year, its sudden resurgence in two full-strength consecutive campaigns has forced the security community to rethink the malware distribution channels and their capabilities. Particularly when used to bring about the successful comeback of a retired malware.
Mitigation: In terms of the zero-day mentioned earlier in the piece, Microsoft patched this flaw in April – if you haven’t updated, you should probably stop reading this and go do that now.
While, technically, there are some things security practitioners can do to mitigate against these attacks, Dridex has always included a phishing element. Everyone should exercise caution with emails from unknown senders and – as a rule – never open attachments from unknown senders (Are you reading this mum?)
Targets: Although Dridex’s most recent campaign focused on Australian banks, it has also been used to target Financial Institutions across the globe including the UK, US, Scotland and Switzerland.
Attribution: Attribution is always difficult and with Dridex it is no different. We can, however, say that the organization behind Dridex is extremely professional – even going so far as to maintain a Monday to Friday work week.