
A key plank of LMNTRIX’s Active Defense involves monitoring deep and dark web activity to give customers real-time intelligence, direct from the mouths of cyber attackers. As part of this reconnaissance, we have uncovered a criminal claiming to have access to a Windows 10 zero-day exploit based on ASLR/DEP bypass vulnerabilities.
In the thread, pictured below, the seller claims the zero day enables attacks on both 32-bit and 64-bit versions of Windows 10:
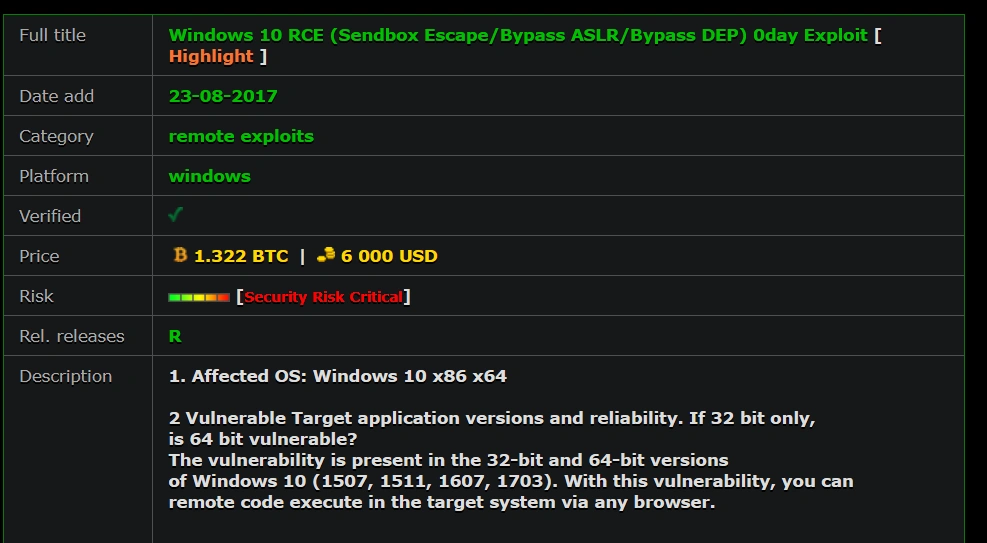
The asking price has been set at 1.322 BTC or USD$6000.
While we have as yet been unable to view the exploit code, the features it purports to target (Microsoft’s Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR)) are security mechanisms which protect against any viruses or trojans that attack Windows system memory.
The code has been verified by administrators of the site, which suggests the zero day could be legitimate:

Additionally, our research team have viewed the attacker’s previous posts which show a history of selling legitimate exploits:

For this latest exploit, the malware merchant lists the applications and browsers that the zero day has been successfully tested against:

According to the advertisement, the exploit enables an attacker to deploy Remote Code Execution and Sandbox escape, both of which can be delivered via a compromised web page.
The nature of the vulnerability the exploit attacks is the memory handling procedure of Windows 10 32 and 64-bit versions. Apparently, this could be accomplished by parameter exploitation of ASLR, DEP and EMET version 5.52. However, the seller concedes that in order to make the arbitrary payload fully functional, additional work on the attack platform is required.
These features have been targeted in earlier exploits, but as this latest version claims to be able to launch attacks from web browsers, it is significantly more potent.
Tips for mitigation:
Intelligence is the best weapon against any adversary, and knowing what the criminals have at their disposal means defenders can be prepared to nullify any attack. A zero day gives attackers the element of surprise and intel gathered by sources like LMNTRIX Recon strips cyber attackers of this advantage.
As the zero day relies on compromised webpages to drop the exploit, users should avoid visiting suspicious or unknown webpages and URLs.
Traditional antivirus will not detect the zero day, so if you have anti-exploit endpoint protection like that offered by LMNTRIX Respond, it should be enabled (this should always be the case).
Additionally, Hardware Assisted Control Flow Integrity (HACFI) can also block execution of such an exploit in the early stages of an attack, which again is only available within the LMNTRIX Respond solution.


