
After staying dormant since February 2020, Emotet is back with full vengeance with significant surge in the variant’s malware campaign during September 2020 and first week of Oct 2020. This has led US CERT CISA to release an official warning about the Emotet Botnet’s return.
In this latest malspam campaign we analysed, the emails have a financial theme and come as a reply to a previous transaction by using fake payment remittance notices, invoice attachments or payment details. We also noticed that this time around it uses PowerShell macros in which users are tricked into opening an attached document to enable macros and trigger a PowerShell command which attempts to download Emotet from compromised sites.
Furthermore, Emotet is now targeting legitimate websites that have WordPress themes by using the arbitrary file upload vulnerability in which file mime type is not checked by the server or code while attacker uploads backdoor script and the uploaded folder on given websites is directly accessible.
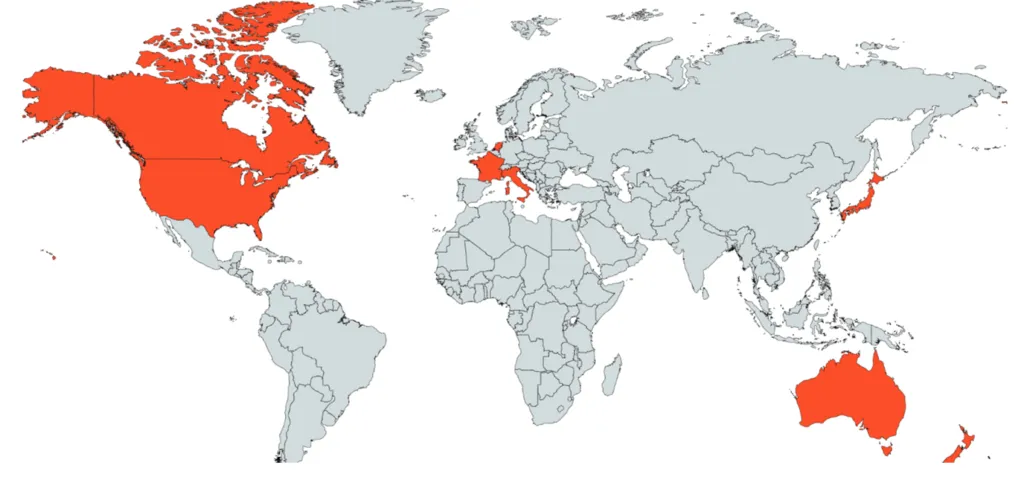
Based on LMNTRIX Threat Intelligence, following regions have been observed to be the major targets when analysing the phishing campaigns associated with Emotet.
Recently, this malware now provides Malware-as-a-Service (MaaS) to other malware groups to rent access to the Emotet-infected computers to infect them with other malware such as Trickbot Trojan and Ryuk Ransomware.
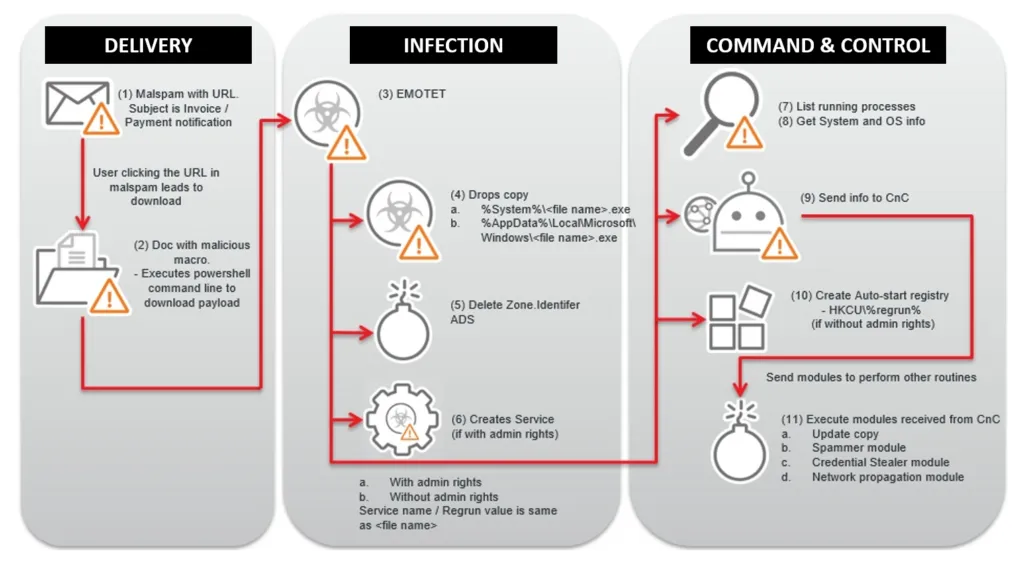
The LMNTRIX Cyber Defence Center has detected below samples across different client networks and has successfully helped them mitigate the threat using Active Defence protections. A few of these samples are explained below:
Sample- 1
Md5: 9d221f86f2f325f5e2625cd21de3d335
Filename: REP_RGMWSRXWSM4Z9TO.doc
Location:

The malicious Word file contained VB Macro code, which is executed on file open, automatically. The macro code performed multiple suspicious actions upon execution –
- Executes another obfuscated Powershell command
- Drop emotet malware to C:\Users\<username>\zwL6MUI\oVCdBxs\ folder path (MD5: 2151719197adfd4ed1e97422f5dd1c32)
- Emotet copies itself to C:\users\<username>\AppData\Local\<random> folder path
- Connects to Command and Control
- Adds Autorun key in Registry to maintain Persistence
Sample -2
Md5: f1ea1131ad723a81dbf1bf00eea07504
Filename: FILE_YQ4375503148YM.doc
Location:

The malicious Word file contained VB Macro code, which is executed on file open, automatically. The macro code performed multiple suspicious actions upon execution –
Executes another obfuscated Powershell command
Drop emotet malware to C:\Users\<username>\Xb1rqmo\Cj2z2jp\ folder path (MD5: a21f579180ab87e5e4bcffec3d5394ce)
Emotet copies itself to C:\users\<username>\AppData\Local\<random> folder path
Connects to Command and Control
Adds Autorun key in Registry to maintain Persistence
MITRE ATT&CK MAPPING for Emotet (ID: S0367)
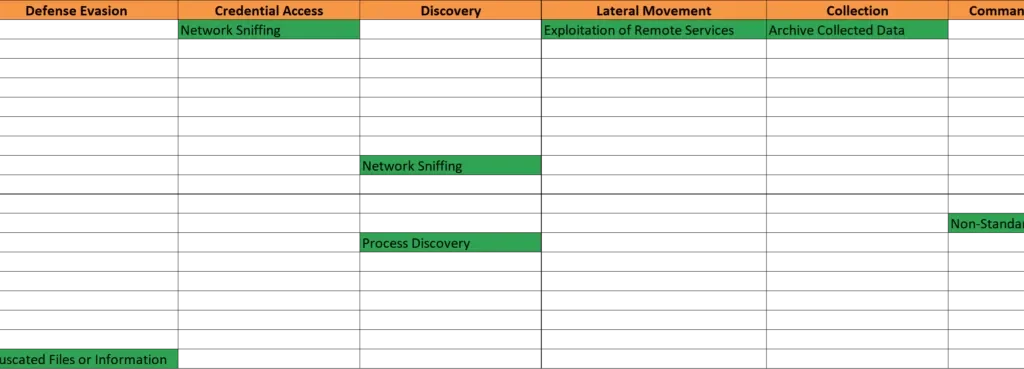
CAPABILITES
- Information Theft: Yes
- Rootkit Capability: Yes
- File Infection: Yes
- Propagation: Yes
- Download Routine: Yes
IMPACT
- Compromise system security – with backdoor capabilities that can execute malicious commands.
- Violation of user privacy – gathers and steals user credentials of various applications.
DETECTION RULES
MS-ISAC developed the following Snort signature for use in detecting network activity associated with Emotet activity.
alert tcp $HOME_NET any -> $EXTERNAL_NET 443 (msg:”[CIS] Emotet C2 Traffic Using Form Data to Send Passwords”; content:”POST”; http_method; content:”Content-Type|3a 20|multipart/form-data|3b 20|boundary=”; http_header; fast_pattern; content:”Content-Disposition|3a 20|form-data|3b 20|name=|22|”; http_client_body; content:!”——WebKitFormBoundary”; http_client_body; content:!”Cookie|3a|”; pcre:”/:?(chrome|firefox|safari|opera|ie|edge) passwords/i”; reference:url,cofense.com/flash-bulletin-emotet-epoch-1-changes-c2-communication/; sid:1; rev:2;)
In conclusion, campaigns like Emotet have always been used by leading threat actor networks to distribute everything from banking Trojans to Ransomware samples into the victims machine and network. And the rise of such campaigns through a well-known delivery partner such as Emotet does provide us a grim picture of the malware trends we expect to see for the rest of 2020. Our recommendation is to ensure you always use the latest pattern available from your security vendors to detect the old and new variants of Emotet Malware and advise your users to be extra careful while clicking and downloading any unknown links and documents as part of your user awareness training.


