Go / Golang is a statically typed language whose syntax is like C/C++ at a very basic level. It includes desirable features from other popular languages such as JAVA (garbage collection, cross-platform support), Rust (reliability), and Python (wide collection of libraries, linting). Etc. As the Go source code is compiled, an executable is given as output depending on the host OS or the GOOS environment variable. Running machine code is always faster than running interpreted language (like Python / Ruby scripts). Thus, Go offers faster execution.
The same codebase can be compiled for any of the supported OS without any requirement of a virtual machine (such as JVM) or dependency (such as Python). It supports built-in concurrency natively as the goal for developing Go was to use it for web applications.
It has a great variety of functions in the standard library itself. Additionally, it is very easy to import 3rd party libraries, such as, including a library just by specifying the GitHub URL of the library. Given all these benefits, it is one of the desired languages for developers who want to get things done.
Golang Malware
Speaking of getting things done – hackers and adversaries are a prime example of developers who prefer productivity over aesthetics. This is eventually lead to the adoption of Golang by malware developers. Golang malware has been around for at least 4 years but only recently there has been a sharp rise in the spread. Last year, a security researcher found over 10k+ Golang based malware in the wild. This observation has led us to wonder why this is the case and most importantly how can we detect these threats?
It seems that the ease of writing code without going through the hassle of Windows C++ coding syntax is a driving factor for malware developers to choose Go. Looking at how threat actors are now targeting containers (Docker and Kubernetes) and Linux with Golang malware also leads us to conclude that the cross-platform compilation is another prime reason behind choosing Go.
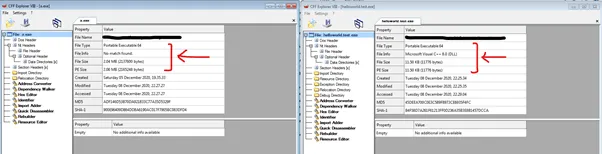
Since Go includes its standard library and garbage collection routines within each Go compiled binary, a simple Hello World program translates to a 2MB portable executable in Windows. Given how heavy Go binaries are, the size of a RAT binary written in Go will range somewhere around 4-6 MB in size. This heavy file size would mean that most simple and traditional AV programs would simply not scan it entirely. Also, since RATs or any other generic malware other than Adware or Bundled Trojan, are usually smaller in size, such as under 2MB – the Go malware is least likely to ever come under anomalous PE file size detection.
The majority of Golang malware families belong to penetration testing frameworks, RATs, and payload generators. The most common malware campaigns/families seen in the wild to date are as follows –
- Veil – Veil Framework is a tool that generates Metasploit payloads. It contains Golang based reverse shell for TCP / HTTP / HTTPS which has been observed mostly in the wild. (https://github.com/Veil-Framework/Veil )
- GoBot2 – This is a Go-based botnet with a lot of features for the Command and Control as well as the Bots. This project shows how matured malware development can be accomplished from Go. (https://github.com/SaturnsVoid/GoBot2/ )
- HERCULES – This is a payload generator for reverse shell over TCP / HTTP / HTTPS that claims to bypass AV software. The entire framework as well as the payloads are written in Go. (https://github.com/EgeBalci/HERCULES )
- CHAOS – This is another payload generator which also features RAT-like abilities. The entire framework and payloads are written in Go. (https://github.com/tiagorlampert/CHAOS )
- GoBotKR – A backdoor malware masquerading as torrent data for South Korean movies and TV shows to bait users and evade detection. The malware was observed to hide with deceptive filenames and extensions.
- StealthWorker – Trojan malware written in Golang targeting eCommerce websites with brute force attacks.
- JCry – Israeli websites were targeted by JCry ransomware which was written in Golang.
- CVE-2018-7600 Exploit – Golang based malware-infected webservers by exploiting Drupal vulnerability to mine Monero coin. It also exploits many other vulnerabilities in other applications to propagate.
- FancyBear – A discovery was made in 2019 that the threat group had added new modules as a part of its new campaign, which included a backdoor written in Golang.
- GoRansom – This is a simple Go-based ransomware. It allows the developers to understand how easy it is to write Go ransomware and subsequently build more enhanced and complex variants from this. (https://github.com/andpalmier/goransom)
Case Study: Blackrota
A malicious backdoor program written in Golang that exploits an unauthorized access vulnerability in Docker Remote API. The backdoor is an ELF binary compiled in a CobaltStrike Beacon implemented in Golang. As it interacts with CobaltStrike, many common CobaltStrike functions are available. However, the source code is obfuscated using gobfuscate before compiling. Gobfuscate substitutes package names, global variable names, function names, type names, and method names with random characters. Strings are replaced with XOR encoding and a decoding function dynamically decodes strings during program execution.
Blackrota uses Gobfuscate to obfuscate Runtime Symbol Information and Runtime Type Information, which is important to analyze assembly code during disassembly. This makes it even more difficult to reverse engineer the malware sample.
This malware exploits Docker Remote API and then downloads the backdoor specific to the target architecture. Not much is known till now about the specifics of the sample as the reverse engineering task has been extremely difficult given the extreme obfuscation and unavailability of the sample in the public domain for free.
Case Study: TA416’s Golang PlugX Malware Loader
TA416 has been known to deliver PlugX malware via multiple campaigns. In the most recent campaign, it was observed that a Golang based loader was used to eventually load and execute the PlugX malware. The initial stages of infection are not known however from previous research reports it is speculated as a malicious download from Google Drive or Dropbox link sent via Phishing activity.
The initial malware is a self-extracting archive (SFX file) that extracts two legitimate Adobe executables and a DLL written in Golang. SFX then executes one of the legitimate Adobe executables which loads the DLL file. DLL side-loading leads to the execution of the malicious DLL file which is the Golang based malware loader. The DLL file has a PE export function which decrypts and dumps the final PlugX malware onto the filesystem and initiates the execution.
The continued analysis and research into methods and attacks of TA416 shows that the threat group is constantly evolving its toolset. The operational changes are minimum and sometimes none but the updates to its obfuscation and encryption are enough to confuse researchers for some time at least. In this instance, a Golang based malware loaded was observed as the first instance of using Golang in the attack lifecycle.
Challenges and Detection
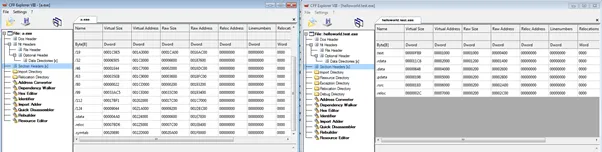
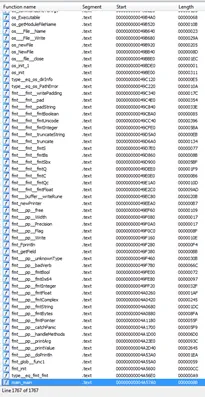
While Golang provides a lot of benefits, it also means increased overhead to malware analysts while dissecting and understanding what is going on with an executable. The assembly code looks very different under a disassembler as compared to PE coded in C, C++, or C#. The first major difference we observe is weird section names. Due to the bulky nature of the Golang PE, most of the functions are related to the standard libraries which makes finding declared functions a bit of a hassle.
Detection via traditional AV is still catching up as signatures need to be pushed by vendors after successful triage. This leads to the old problem of not being able to detect the unknown. LMNTRIX Active Defense has been successful in detecting these new Golang based malware due to the behavioral detection engine aligned to MITRE ATT&CK and the ML-based malware detection within our endpoint agent.


