I thought we’d take a little break from discussing serious, fix-this-now security risks and talk instead about an innovative attack developed by researchers at Zhejiang University. This attack is interesting because it emonstrates the lateral thinking both sides of security use every day. These researchers have developed a similar attack in the past, but this iteration, dubbed DolphinAttack, is a perfection of a neat method for an attacker to send commands to your phone.
First of all, DolphinAttack requires specific hardware: an ultrasonic transducer, an amplifier, a battery, and an android phone to control the lot. The tl;dr of this method is that attackers convert a regular voice command into ultrasound, then use sound harmonics to deliver the ultrasonic message directly to the target phone’s mic at a frequency it can interpret.
Now let’s do the long explanation.
I thought we’d take a little break from discussing serious, fix-this-now security risks and talk instead about an innovative attack developed by researchers at Zhejiang University. This attack is interesting because it demonstrates the lateral thinking both sides of security use every day. These researchers have developed a similar attack in the past, but this iteration, dubbed DolphinAttack, is a perfection of a neat method for an attacker to send commands to your phone.
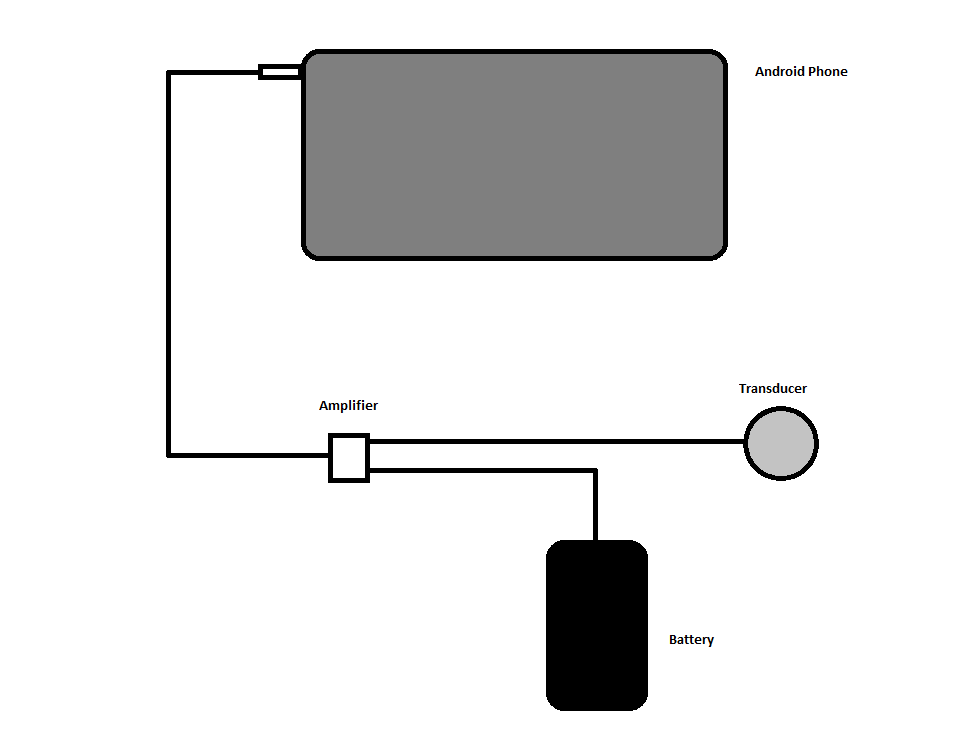
First of all, DolphinAttack requires specific hardware: an ultrasonic transducer, an amplifier, a battery, and an android phone to control the lot. The tl;dr of this method is that attackers convert a regular voice command into ultrasound, then use sound harmonics to deliver the ultrasonic message directly to the target phone’s mic at a frequency it can interpret.
Now let’s do the long explanation.
First, an attacker prerecords voice commands that will be executed on the target’s phone. As this attack targets phone assistants (Siri, Google Now, Cortana, etc.), these commands are limited to actions your phone assistant is permitted to perform through a locked device. This command will be converted into an electrical signal by the attacking phone, and output through the headphone jack.
The signal is picked up by an amplifier, which ensures the phone’s electrical signal can be properly interpreted by the transducer. A battery is also connected to the amplifier, powering both the amplifier and transducer.
Finally, the signal is sent through to the transducer, where it is converted into ultrasonic sound. The details of this process are a little complicated, but suffice to say it involves crystals which deform and oscillate under an alternating current. This ultrasonic sound is directed at the victim’s phone, and the microphone registers it as it would any other noise.
Phone mics, however, aren’t designed to listen to ultrasonic tones, which leads to the really clever bit: the tone is precisely created to produce harmonics in the 85-255 Hz range (the range of typical adult speech, and thus the range your phone mic is designed to detect).
Sound is a pressure wave, which propagates through a medium (like air, water, wood, or any physical thing). A microphone is able to convert sound (pressure) waves into electrical signals by vibrating a membrane in a magnetic field, which induces an electric current corresponding to the sound wave. Voice assistants don’t know anything about sound waves, they’re programmed to interpret patterns of electric currents.
One more important fact: a sound wave isn’t just one frequency as it also carries harmonics. Harmonics are a by-product of physical wave interactions, and they happen at regular intervals along a wavelength.
DolphinAttack takes advantage of the power of harmonics, and sends coded messages through strong harmonics in the range of the human voice. The ultrasonic transducer blasts out ultrasonic sound waves whose harmonics are powerful enough to register on a phone mic. The phone’s mic vibrates under this ultrasonic blast, but only registers the strong, lower-frequency harmonic. The phone assistant recognizes the electrical pattern, and responds as if it’s been spoken to.
Voila, DolphinAttack has executed a command on your phone, without you having any knowledge of it.
Chances are you’re not going to get attacked in this way. Even if you are, you’ll likely suffer nothing worse than sending an accidental text message or making a phone call because complicated commands often failed during the experiments.
Also, because harmonics are so weak, the range on this attack is relatively short and the entire attack method can be nullified by turning off your phone assistant’s passive-listening capabilities.
Overall, DolphinAttack isn’t very dangerous but it is an extremely clever attack and highlights the ingenuity taking place at the forefront of security research.



