
Determining the size and scope of a cybersecurity budget is a puzzling endeavor for many organizations, especially small- and medium-sized enterprises. Such a trend is alarming as close to 70 percent of all cyberattacks are targeting SMBs since the mid-2010s.
One of the main challenges when drafting a cybersecurity budget for your organization is that cybersecurity is a broad field, so defining specific goals, improvements and particular measures requires in-depth knowledge of the IT security domain.
Further, you need to evaluate factors such as:
- Industry and company size
- Compliance and regulations within your industry
- What sensitive data you collect, use and share
- What specific security measures your stakeholders and customers require.
Evidently, planning for cybersecurity spending closely reflects your wider view on IT security. Nonetheless, it is of utmost importance to plan with the broader picture in sight and not implement an ad hoc strategy that results in reactive security procedures, which are of little use in today’s fast-paced world of rapidly evolving cyber threats.
How Much Should You Spend on Cybersecurity
The amount that your organization spends on security is closely tied to your overall IT budget. Recent studies find that organizations spend between 5.6% and up to 20% of their total IT budget on cybersecurity.
How Much Organizations Spend on Cybersecurity
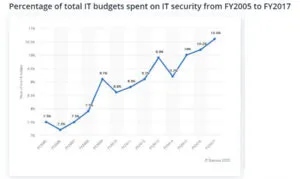
The actual figures often depend on an organization’s approach to cybersecurity, which varies from the counterproductive “nice to have” to the more wise “must have”. Even within these approaches on cybersecurity budgeting, you can see different categories of spending:
- Security as a differentiator: These organizations spend heavily on cybersecurity, realizing that security will make their product or service stand out from the crowd while protecting their digital assets.
- Risk based: These are organizations that make large investments in cybersecurity but in the same time try to balance risks and IT spending.
- Regulatory compliance: Some organizations invest in their cybersecurity in accordance with the applicable regulatory and industry requirements, which is cheaper but gives them less security.
- Ad hoc spending: These organizations does not have a specific cybersecurity budget and view funding for security measures as part of their overall IT budget, minimizing costs but having a fragmented cybersecurity.
Obviously, opting for the latest option is not a viable choice unless you are running a very small business and even then you may end up suffering substantial losses due to a data breach, ransomware or data theft.
Decide What Drives Your Cybersecurity Investments
You cannot have a feasible cybersecurity budget before you determine a specific approach toward security and whether you are to invest in one-size-fits-all solution or will gear toward a custom and proactive IT security strategy. That said, you need to define the major factors that drive your security spending.
A survey by the SANS Institute shows what the five leading factors for cybersecurity spending in 2020 are:
- Regulatory compliance with 69% of responses
- Decreasing the number incidents and breaches (59%)
- Keeping up with new threats (57%)
- Maintaining company reputation (43%)
- Incident response and investigation (40%)
Other major factors to consider include securing organizations’ assets in the cloud and protections for networking infrastructure, both on-premises and in the cloud.
If you are to adopt an effective cybersecurity budget that deals with risks and threats specific to your industry and core business activities, you should address three topics related to cross-functional budgeting:
- What risks we are ready to take? What is our risk appetite?
- In what to invest for maximum impact?
- How do we maximize value from existing investments?
Only after addressing these security topics, your organization will be able to draft and adopt a budget that reflects both your current and evolving needs based on an approach that maximizes the effect from existing and future investments alike.
Define Your Long-Term IT Security Spending Strategy
A classical approach is to stick to the principle of securing funds to have the minimum required tools and measures in place, which enables you to focus on growth. This is an approach usually in use by growing organizations where the budget stays about the same in the course of several growth cycles, providing the bare minimum for adoption of cybersecurity measures.
Under that development strategy, an organization does not implement a strategic IT strategy but instead spends its budget on immediate needs such as launch of a new product or opening of a new office. It might work well for some organizations but the spending may become overwhelming over time, as the organization must respond to a growing number of unexpected issues and security needs for which it had not planned beforehand.
A more seasoned approach is when an organization bets on assessing business-critical risks in advance and all cybersecurity investments are made with the idea to mitigate and eliminate those risks. This strategy will save you a whole lot of funds in the long-run while equipping your organizations with the right tools that are not filling the current security gaps but provide long-term security solutions.
In any case, you should define what outcomes do you expect and what is the timeframe for these results to become visible. Such an approach will help you avoid panic spending and will enable you to focus on a few fundamental topics when you draft your cybersecurity budget.
How Much to Spend on IT Security, Really
Now we come to the point when you need to determine your actual budget for cybersecurity. There is no universal formula how much should you spend on security since organizations’ needs differ even within one and the same industry vertical and size of business.
Nonetheless, there are three fundamental cybersecurity areas to address when planning your spending:
- Thoroughly assess the threats and associate risks that are more relevant to your industry and operations as well as your current and eventual scope of business operations. Use as many threat intelligence reports as you can to determine, which are the major risks and cyber threats in your business domain.
- Carefully evaluate risks and potential value of each and every cybersecurity solution by taking of all the in-house and external expertise you have access to. Outsourcing risk assessment and solutions evaluation is a viable approach, especially for small- and medium-sized organizations that lack in-house cybersecurity expertise.
- You can use industry benchmarks to determine the broader scope of your IT security budget but take advantage of all the available research tools to delve deep into the numbers concerning threats, measures and specific cost of implementing one or another solution.
Once you address all these subjects, you can move on to adopt a cybersecurity budget that is tailored to your actual needs and requirements. You should plan for the future but always look back to find what was working fine in the past and what did not produce the desired outcomes.


