
Hitler Ransomware was first discovered last year, and since then it has continued to target European Windows users with its destructive brand of malware.
Upon successful infection, it extracts the following files into the system’s %Temp% folder: chrst.exe, ErOne.vbs, and firefox32.exe.
“firefox32.exe” is also copied into the Windows startup folder so it can be automatically launched upon system reboot.
Upon reboot, the ransomware checks for the existence of the following processes, and, if found running, kills them: taskmgr, utilman, sethc, and cmd.
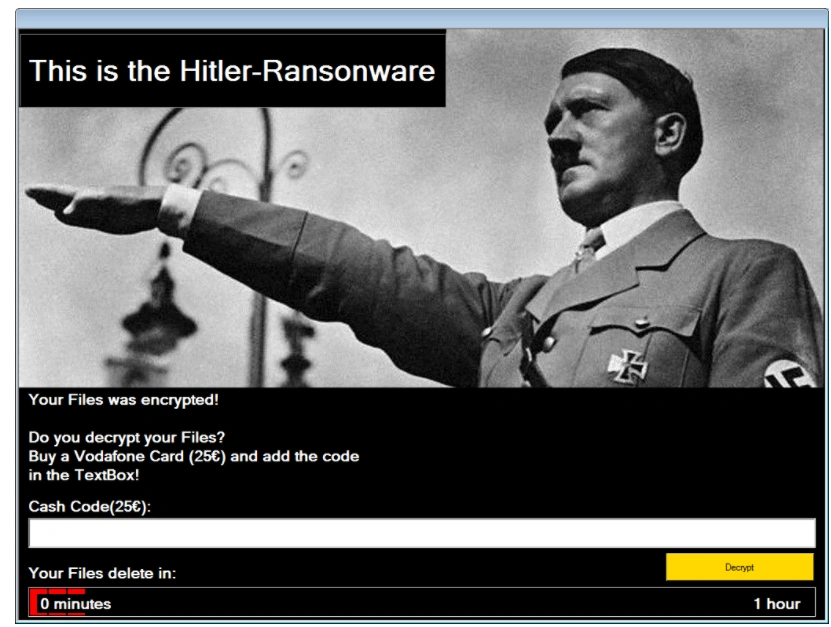
This malware removes the extensions for all files in various directories, displays a lock screen with a one-hour countdown message, and demands you enter a cash code for a 25 Euro Vodafone Card as payment before the timer runs out. Failing to enter the code within an hour leads the system to reboot, which in turn deletes most files on the victim computer.
File Details
| File Type | Portable Executable (PE) File |
| Md5 hash | e64dbe09fc1805177d9058a40807e128(packed) 57381bc089724b9ee6fa65bf7a56800a(unpacked) |
Static Analysis
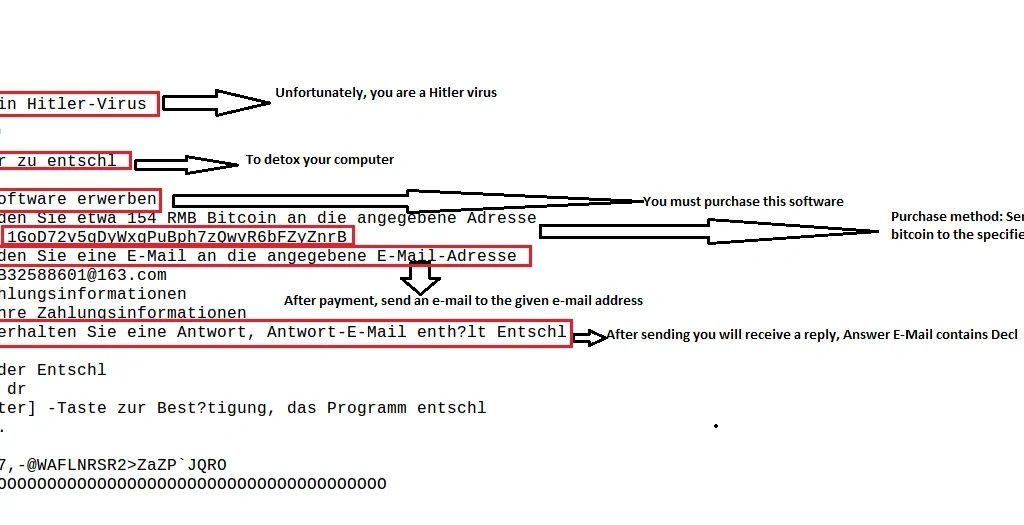
This first thing our static analysis uncovered was that Hitler ransomware is packed with a UPX packer (unpacked as shown below):

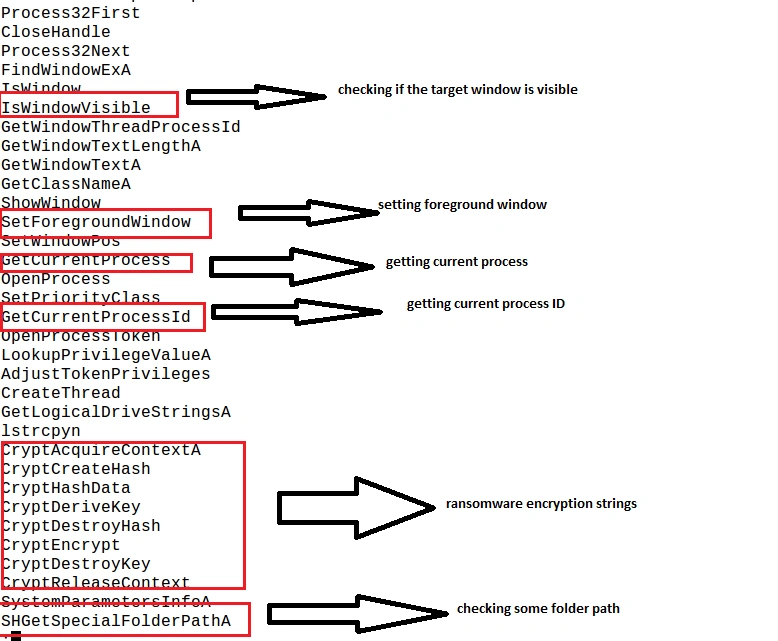
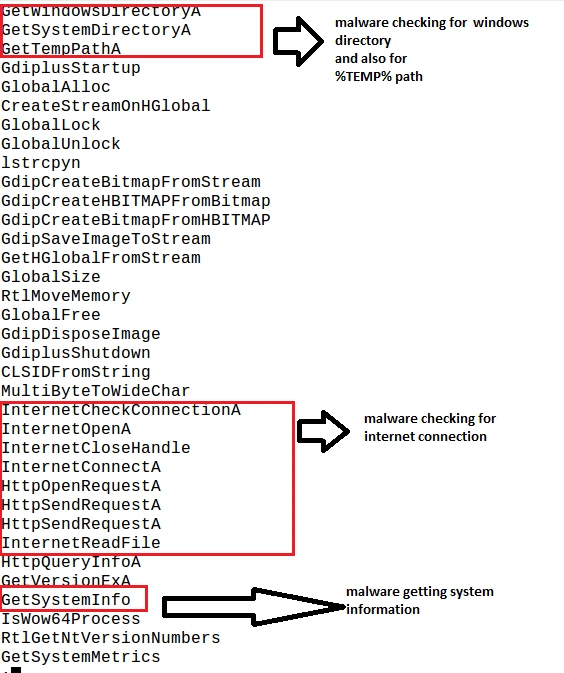
Unpacking the malware revealed the below strings and functionality:

Dynamic Analysis
Our researchers executed the ransomware in a virtual environment to see how it behaves in the real world.
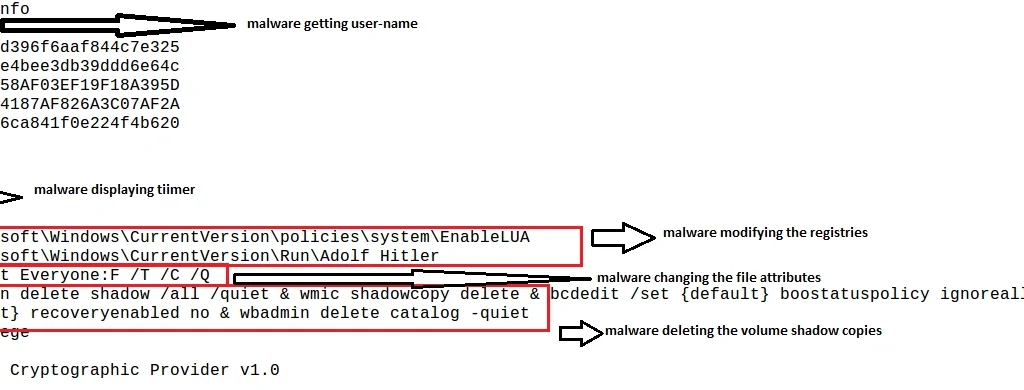
The first thing we noticed was the sample scanning the computer for particular file attributes, using the following command:
“icacls.exe icacls . /grant Everyone:F /T /C /Q”
It then accesses Windows command line utility (cmd.exe), and uses vssadmin.exe to delete volume shadow copies of the system (as shown below):
cmd.exe cmd /c vssadmin delete shadow /all /quiet & wmic shadowcopy delete & bcdedit /set {default} boostatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no & wbadmin delete catalog –quiet
Now the ‘encryption’ phase begins, with the following pop-up displayed onto the victim’s PC
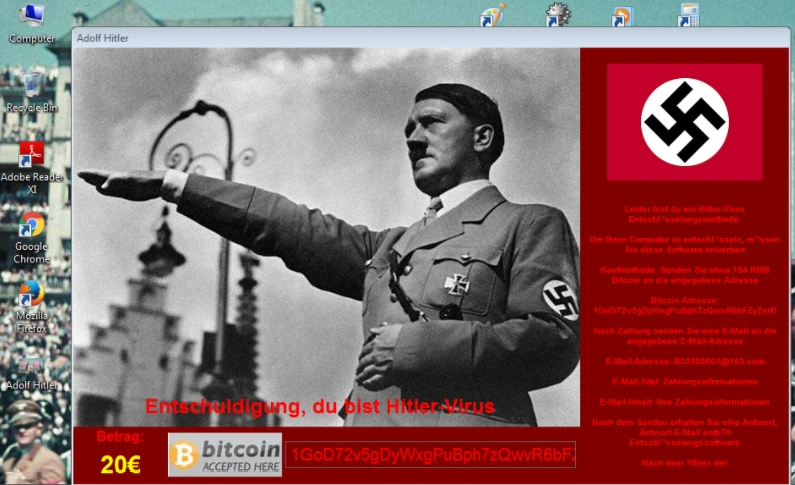
Next, all the victim’s files have their extensions replaced with .AdolfHitler:

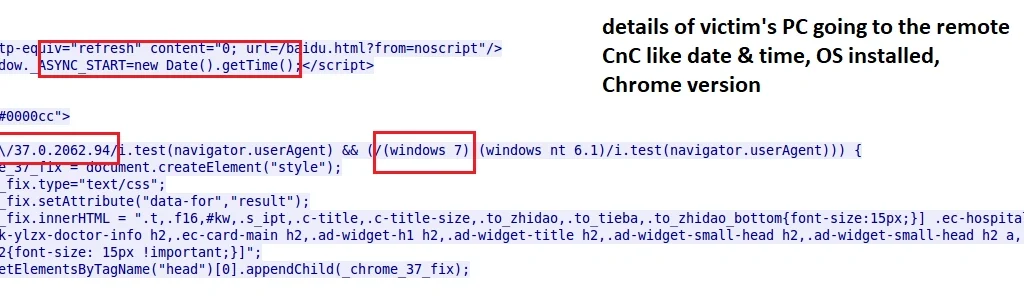
Below are the network activity observations:



The ransomware also adds the following registries to ensure persistence:
• HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Adolf Hitler: “C:\Users\<user-name>\Desktop\sample.exe”
• HKU\S-1-5-21-1265348393-3129211107-4082868339-1000\Software\Classes\VirtualStore\MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Adolf Hitler: “C:\Users\<user-name>\test\Desktop\sample.exe”
• HKU\S-1-5-21-1265348393-3129211107-4082868339-1000\Software\Microsoft\Internet Explorer\LowRegistry\Audio\PolicyConfig\PropertyStore\8bd7da89_0\: “{0.0.0.00000000}.{90a75006-e5fb-494e-8926-42d3ba714ca7}|\Device\HarddiskVolume2\Users\<user-name>\\Desktop\sample.exe%b{00000000-0000-0000-0000-000000000000}”
Indicators of Compromise
Command and Control:
• 103.235.46.40
• baidu[.]com
• 163[.]com
• 123.125.93.50
• 183.238.101.233
• 2017[.]ip138[.]com
MD5 file hashes
• e64dbe09fc1805177d9058a40807e128
• 57381bc089724b9ee6fa65bf7a56800a
Mitigation
Unfortunately, the Hitler ransomware’s distribution method is currently unknown.
However, some specific tips for what to do after you’ve been infected (and before the countdown timer runs out) include:
As the malware relies on the system being rebooted, you should boot your system in “Safe Mode with Networking”, then find and delete the following entry:
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup\firefox32.exe;
Then, delete the following entries, which are stored in the %Temp% folder:
• chrst.exe
• firefox32.exe
• ErOne.vbs
Although this strain’s specific distribution method is unknown, general cyber hygiene (such as keeping antivirus updated with the latest virus definitions and including the IOCs in endpoint devices) will help reduce the risk of infection.


