Since July 2021, numerous US, European, and Australian intrusions have been attributed to the BlackByte ransomware group. Attacks have been launched against manufacturing companies, financial services, key infrastructure providers, and most recently an American football club. BlackByte is believed to be headquartered in Russia because it’s meant to avoid organisations where the system default language is Russian or another language from the Commonwealth of Independent States. LMNTRIX CDC recently observed that BlackByte attackers used Microsoft Exchange Server ProxyShell & Proxylogon vulnerabilities to gain initial access as part of the infection process.
The malware is coded in Golang which has become popular among threat actors in the last 3 years.
Targets: BlackByte ransomware has infected victims all over the world, from North America to Colombia, the Netherlands, China, Mexico and Vietnam.
Impact of Blackbyte Ransomware
Numerous users in Russia have had their accounts hacked by the Blackbyte ransomware variant. Tens of thousands of email accounts have been compromised as a result of an attack on the largest web mail service in the nation using this malware as a service. According to the FBI’s Joint Cyber Security Advisory, “BlackByte ransomware had compromised multiple US and foreign businesses, including entities in at least three US critical infrastructure sectors (government facilities, financial, and food & agriculture). BlackByte is a Ransomware as a Service (RaaS) group that encrypts files on compromised Windows host systems, including physical and virtual servers.” In order to develop a more effective protection strategy against BlackByte, it is helpful to be aware of the major steps it takes to infiltrate target networks.
Initial Access Phase
The BlackByte group’s playbook, much like Conti ransomware group, focuses on exploiting known vulnerabilities in public-facing server infrastructures such as Exchange. The fact that traffic to and from these services has been encrypted with the transport layer security makes detecting exploitation attempts difficult for most of the security controls deployed by a typical SMB organization.
Organizations should keep an eye out for and patch any vulnerabilities affecting publicly accessible infrastructure, such as Proxy Shell and Proxy Logon, which is used by BlackByte group. Security teams should be vigilant and, whenever possible, monitor encrypted communication, such as TLS 1.2 and 1.3 with full fidelity request forwarding, to make sure that attackers cannot conceal their attempts at exploitation.
Exploitation by BlackByte
Like many cyber criminals, the BlackByte gang depends on Cobalt Strike toolkit to supply the essential components for their attack, exploitation, or post-exploitation stages. After successfully breaching your perimeter defense, an attacker will concentrate and start intelligence gathering on the inside, next steps of lateral movement, and privilege escalation during the post exploitation phase will follow. Communicating later with the designated command and control server, another round of recon and/or evasion is inevitable, as these capabilities are offered by penetration testing tools like Cobalt Strike in a beautifully packaged manner even to a non-technical attacker. Ransomware groups like BlackByte are able to quickly move laterally, compromise many systems, and disable security features like EDR and remote logging by utilizing packaged tools and well-known attack vectors. Due to the lack of attention given to internal network security, in terms of detection and response, it has always been challenging to identify the lateral movement and off-the-grid approaches. Many companies are trying to encrypt all internal traffic, which exacerbates a difficult situation by widening the visibility gap and giving attackers more time.
A BlackByte ransomware affiliate recently started using “ExByte“, an info-stealer to steal data from Windows devices quickly. ExByte allows BlackByte ransomware to upload exfiltrated data to mega.co.nz for double extortion. BlackByte as well as other ransomware gain unauthorized access, steal data from victims and threaten to delete, OR leak data unless they get paid.
Cyber Defense Tactics To Slow Down BlackByte
Security Operation teams must adopt visibility and detection techniques like strategic decryption with the presumption that their network has already been infiltrated. Decryption of frequently exploited protocols, such as SMBv3, MS-RPC, NTLM, and Kerberos, is essential for limiting an attacker’s capacity to operate covertly and assisting in the discovery of harmful behavior. Speed of incident response is a real factor when it comes to responding while combating harmful attacks such as Blackbyte. It is crucial to decisively take action to limit the spread of malicious behavior, but it’s also equally crucial to make sure that the action is precise enough to reduce any unintended damage to an organization’s infrastructure.
Security tools can identify malicious behavior by detecting lateral movement, network enumeration, and efforts to some extent. However, as companies try to expand encryption to internal network traffic, many IT / Security Operation teams are losing sight of these strategies. Integrating security products like endpoint detection next-gen antivirus, network detection and response (NDR), with traditional and web application firewalls, cloud based SSO for identity and access management (IAM), machine learning, threat intelligence and a unified control such as eXtended Detection & Response (XDR) can ensure security operation teams respond swiftly to malicious activity with greater control.
BlackByte Ransomware Attack
In addition to encrypting local file systems and network file sharing, ransomware attacks also commonly steals data that is essential to business operations before encrypting it. For defenders, with little to no visibility, this offers a variety of potential detection challenges.
A late-stage sign of many ransomware attacks, including BlackByte, is the exfiltration of data to anonymous file-sharing websites. BlackByte is infamous for uploading substantial amounts of customer data to file-sharing websites which they later exploit to demand further payments from their victims. It would be noteworthy to mention, that a good XDR solution can spot every step of the attack from initial access to data exfiltration.
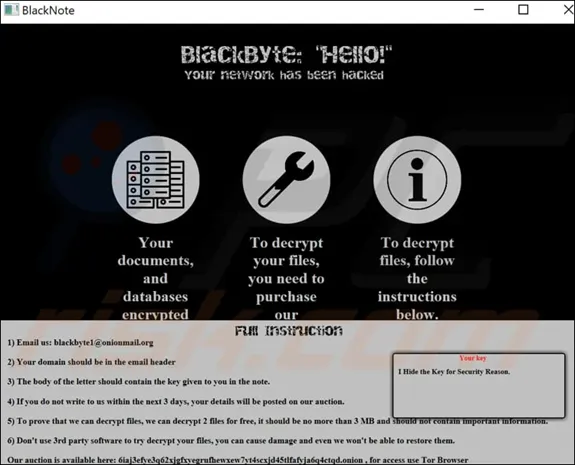
Encryption of network file shares, like data exfiltration, generates distinct traffic patterns that good security products can use to detect “active” ransomware activity. In the case of BlackByte, the ransomware creates ransom notes with instructions on how to contact the attackers, pay the ransom, and decrypt the user’s files.
Following are examples of anonymizer websites used by BlackByte,
- Anonymfiles[.]com
- file[.]io.
We have outlined a few simple Indicators of Compromise, for BlackByte that anybody can use;
- BlackByte_restoremyfiles.hta – the ransomware note
- Encrypted files with the extension “*.blackbyte”
Mitigation Strategy for BlackByte
Conventional prevention strategies often lack the capability required to stop a ransomware infection. LMNTRIX recommends the company to use better access controls, segment the network and training users to identify phishing attempts on a regular basis. That being said, the complexity of implementing and managing a security program and, the limited gains associated with user training as a partially effective strategy can’t be ruled out.
LMNTRIX believes that businesses must understand that a layered approach to cyber security is still required to defend against advanced attackers, such as BlackByte. Instead of adopting a post-compromise security mindset, organisations should develop a process and leverage tooling to detect attackers at every stage of the kill chain (think XDR). This includes endpoint detection and response, NGAV, threat intelligence, machine learning, underground intelligence, and network detection and response (or network visibility tools), which are required to detect cyber intrusions and lateral movement, allowing Security and Operations teams to slow down an attack before a full-scale breach can occur. No single security product is capable of addressing the breadth of the modern threat landscape. As part of your security program, your company must constantly evaluate the IT organization’s security posture, and adapt as conditions evolve.
General mitigation steps, for Ransomware, according to LMNTRIX playbook are as follows:
- Implement regular backups of all data to be stored as password protected copies offline.
- Ensure these copies are not accessible for modification or deletion, from any system where the original data resides.
- Implement network segmentation such as VLAN, a control that ensures all machines on your network are not accessible from every other machine.
- Install and regularly update antivirus and EDR software on all hosts, enable real time detection and take action when you see an alert. Triage the alert, validate and close the incident ticket with proper containment and remediation steps.
- Install security updates & patch your operating systems, software, and firmware as soon as updates/patches are released by the vendors.
- Audit all user accounts with administrative privileges and configure access controls with the principle of least privilege in mind. Do NOT give administrative privilege to all users.
- Disable unused remote access/Remote Desktop Protocol (RDP) ports and monitor remote access/RDP logs for any unusual activity.
- Disable HTML email, and remove any/all hyperlinks in received emails.
- Use double authentication, or a MFA control, when logging into accounts or services.
- Ensure that routine security auditing is conducted for all accounts.
- Ensure all the identified IOCs are fed into the network firewall, web app firewall, EDR, IDS/IPS, SIEM for continuous monitoring, and stay vigilant when an alert pops up. Use your incident response process to validate alerts, prioritize alerts and remediate security threats.
Conclusion
BlackByte is considered as one of the “big game” ransomware groups, they target large and high-profile organizations by not only exfiltrating their data, but also threatening to publicly leak it on dark-web websites, if the unsuspecting mark doesn’t pay the demanded ransom amount.
We would like to conclude, with a sober note, a ransomware group has needs that must be met in order to be successful. In order to compromise your systems, network and data, the attacker needs to obtain unauthorized access to the “target” systems, storing critical / confidential data. The attackers must then establish command and control, identify weak points within your network, and move laterally.
LMNTRIX strongly believes, with a steady stream of BlackByte attacks identified globally in early 2022, the human operators behind the Ransomware as a Service are likely to continue to attack and extort organizations increasingly in the near future. A security control such as XDR, operated by a skilled human team, will have an opportunity to counter the ransomware operators at every step to detect, contain, respond & remediate emerging threats before they can cause significantly costly breaches.
Appendix A
Vulnerabilities exploited by the Blackbyte Group;
| CVE Number | CVSS Score | Vulnerability |
| CVE-2021-34473 | 9.8 (Critical) | Microsoft Exchange Server Remote Code Execution Vulnerability |
| CVE-2021-34523 | 9.8 (Critical) | Microsoft Exchange Server Elevation of Privilege Vulnerability |
| CVE-2021-31207 | 7.2 (High) | Microsoft Exchange Server Security Feature Bypass Vulnerability |
Appendix B
Anti Analysis Checks performed by BlackByte Ransomware;
BlackByte can detect standard analysis tools and intends to evade them, using the standard API checks, the malware calls the IsDebuggerPresent and CheckRemoteDebuggerPresent API. This development makes BlackByte and its affiliates more dangerous, especially since the Exbyte program checks to make sure it is not in an analysis environment before stopping, making it hard to detect/debug.
ImmunityDBG
OllyDBG
MegaDumper
Import Reconstructor
WinDBG
IDA Pro
It also performs checks for the following traditional antivirus software,
avghooka.dll
avghookx.dll
sxin.dll
sf2.dll
sbiedll.dll
snxhk.dll
cmdvrt32.dll
cmdvrt64.dll
wpespy.dll
vmcheck.dll
pstorec.dll
dir_watch.dll
api_log.dll
dbghelp.dll
The BlackByte sample we examined also calls NetSetInformationThreadW with undocumented value ThreadHideFromDebugger to hide the main thread from debuggers. Threat actors behind Blackbyte and similar ransomware groups want to make it more difficult for security researchers to analyze the malware sample, and hence the anti-analysis checks.
Appendix C
Indicators of Compromise for Detecting BlackByte Ransomware
Registry Keys Added
reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v LocalAccountTokenFilterPolicy /t REG_DWORD /d 1 /f
reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLinkedConnections /t REG_DWORD /d 1 /f
reg add HKLM\SYSTEM\CurrentControlSet\Control\FileSystem /v LongPathsEnabled /t REG_DWORD /d 1 /f
IP Address
185.93.6.31
45.9.148.114
MD5 Hashes
4d2da36174633565f3dd5ed6dc5033c4
cd7034692d8f29f9146deb3641de7986
d63a7756bfdcd2be6c755bf288a92c8b
eed7357ab8d2fe31ea3dbcf3f9b7ec74
695e343b81a7b0208cbae33e11f7044c
296c51eb03e70808304b5f0e050f4f94
0c7b8da133799dd72d0dbe3ea012031e
a77899602387665cddb6a0f021184a2b
1473c91e9c0588f92928bed0ebf5e0f4
28b791746c97c0c04dcbfe0954e7173b
52b8ae74406e2f52fd81c8458647acd8
1785f4058c78ae3dd030808212ae3b04
b8e24e6436f6bed17757d011780e87b9
8dfa48e56fc3a6a2272771e708cdb4d2
4ce0bdd2d4303bf77611b8b34c7d2883
c010d1326689b95a3d8106f75003427c
ae6fbc60ba9c0f3a0fef72aeffcd3dc7
405cb8b1e55bb2a50f2ef3e7c2b28496
11e35160fc4efabd0a3bd7a7c6afc91b
659b77f88288b4874b5abe41ed36380d
151c6f04aeff0e00c54929f25328f6f7
959a7df5c465fcd963a641d87c18a565
5f40e1859053b70df9c0753d327f2cee
df7befc8cdc3c5434ef27cc669fb1e4b
51f2cf541f004d3c1fa8b0f94c89914a
d9e94f076d175ace80f211ea298fa46e
8320d9ec2eab7f5ff49186b2e630a15f
cea6be26d81a8ff3db0d9da666cd0f8f
31f818372fa07d1fd158c91510b6a077
d9e94f076d175ace80f211ea298fa46e
a9cf6dce244ad9afd8ca92820b9c11b9
7139415fecd716bec6d38d2004176f5d
c13bf39e2f8bf49c9754de7fb1396a33
ad29212716d0b074d976ad7e33b8f35f
d4aa276a7fbe8dcd858174eeacbb26ce
58e8043876f2f302fbc98d00c270778b
d2a15e76a4bfa7eb007a07fc8738edfb
e46bfbdf1031ea5a383040d0aa598d45
This lab article is a living blog post… We will update this blog post, as appropriate.


