
The geopolitical scenario of United States and Iran has often spilled over into the realm of Cyberspace between the countries and 2020 was no exception. On 6th January 2020 the US department of Homeland Security published a Cyber Alert which is to be considered as an anticipated warning for Iran in response to a Baghdad strike by US forces.
The Cyber Alert published by US CERT focuses on the country’s Critical Infrastructures which are the possible targets for a cyber-attack by Iranian threat actors. The industrial sector and critical infrastructure consist of a wide range of industries like transport, manufacturing, electricity supply and Energy, mining, water utilities and supply, nuclear facilities, automobile manufacturing, maritime manufacturing and shipping, etc. Now each of these industries are a possible target of state sponsored cyber terrorism which threatens the vulnerable OT (Operational technology) systems. These include the hardware and software systems that monitor and control physical devices in the field. It goes without saying that securing these targets is a huge and a mammoth task that lies at each country’s doorstep that possess any critical infrastructure. In this analysis, LMNTRIX focuses on the growing number of different and distinct cyber threats which we have seen over the past year targeting nuclear facilities backed by various state-sponsored threat actors.
In order to understand the effective functions of the nuclear plant, the devices, functions, and its attributes need to be segregated using Purdue model: –
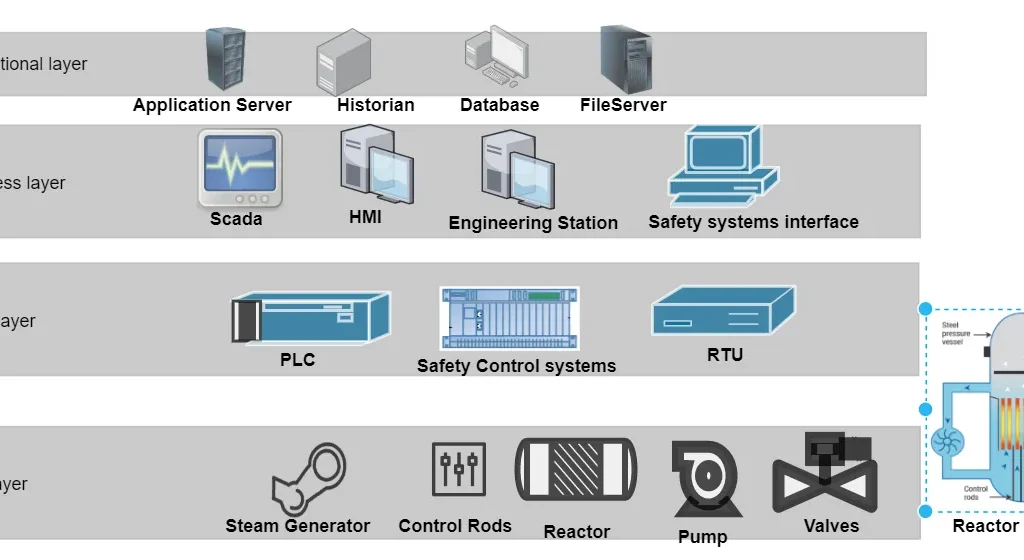
Figure 1: Purdue Model of Nuclear Power Plant
The cyber threats observed on nuclear power plants mostly target the components associated with Level 1 & 2 of the Purdue model. We will refer to the Level 3 as the IT network (even though this is different from the enterprise network and ideally it is placed behind a DMZ) and Level 2 as the OT network from here on. Adversaries targeting Industrial Control systems (ICS) require more resources than any other type of adversary, as each ICS based organization is different in terms of systems used. These systems have varying operational processes that define acceptable and unacceptable outcomes for the PLC devices, valves, pumps, actuators, etc. The ICS Cyber Kill Chain breaks down the steps taken by an adversary into two stages. Identifying each part of these stages and considering them into threat modelling process will lead to a layered defence against ICS attackers.
The Stage 1 of ICS Cyber Kill Chain is similar to the traditional Cyber Kill Chain as the objectives and goals are similar, namely, of gaining access to information; defeating existing defensive measures; gain access to protected network segments; exfiltrate data; and maintain undetectable access to infected systems.
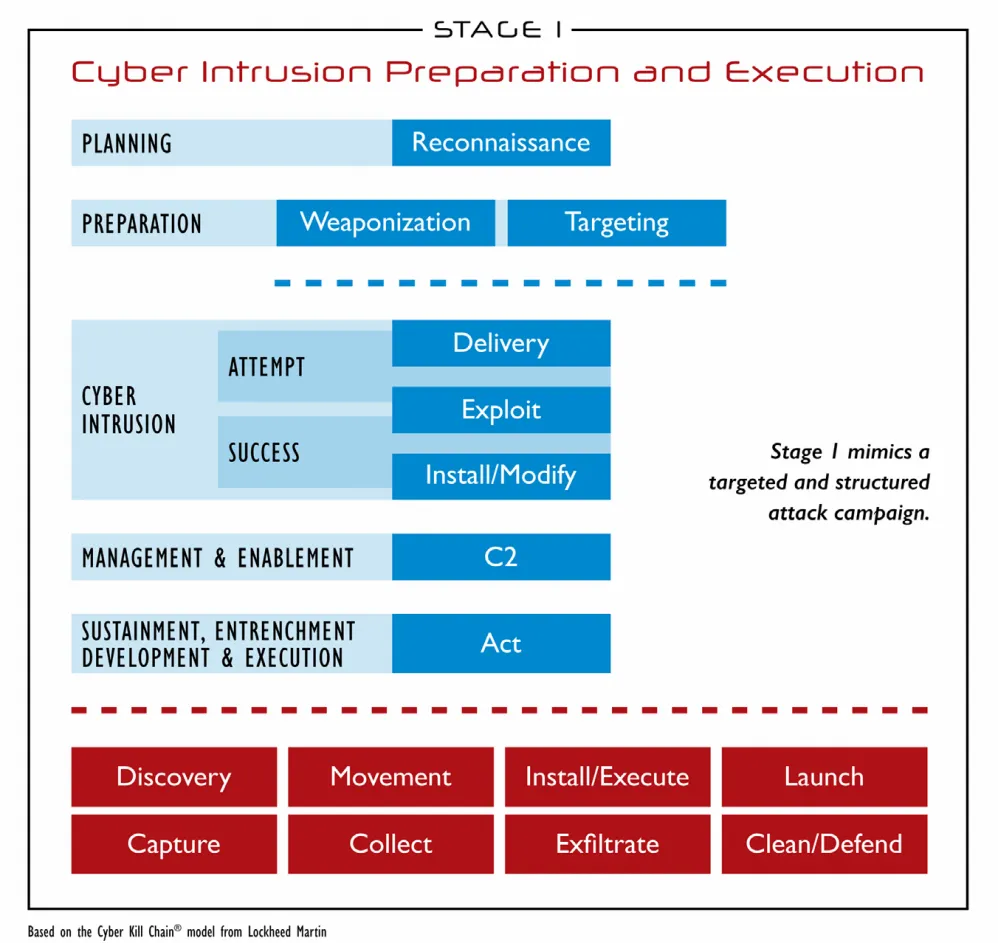
Figure 2: ICS Cyber Kill Chain, Stage 1, SANS (SANS, 2015)
In Stage 2, the attacker uses information gained from Stage 1 to develop, test, and execute the attack. Often an adversary fails in Stage 1 due to the sensitive nature of the equipment connected to the network causing unintended outcomes for an attacker. State-sponsored attackers are capable of successfully reaching Stage 2, because they might often get to either a test network in their home country or exfiltrate system specific information to successfully develop working malware.
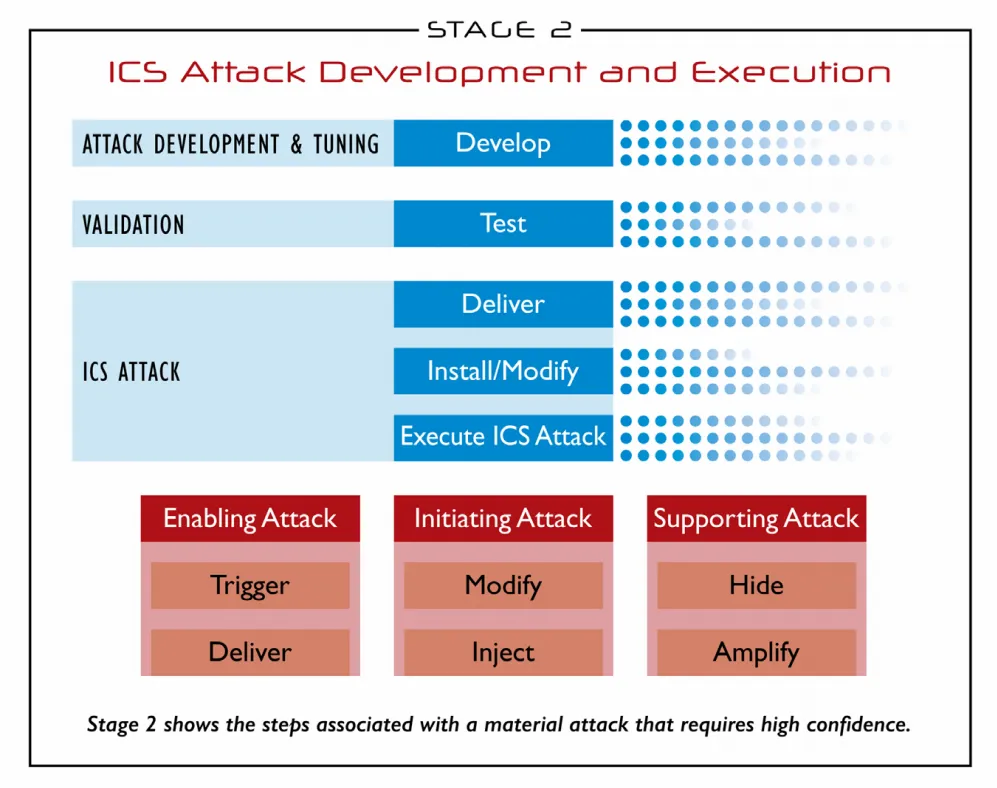
Figure 3: ICS Cyber Kill Chain, Stage 2, SANS (SANS, 2015)
Before we move further, it is important to establish what is considered as an ICS attack. Although attacks on ICS organizations may involve theft of operational data or the infection of systems. The functional impact of such an attack on daily operations or degradation in safety involving harm to system devices, plant workers, or field personnel of an ICS organization is defined as an ICS Attack (SANS, 2015). This can be further broken down into three categories:
- LOSS
- Loss of view – unable to view systems data on console by operators
- Loss of control – unable to control systems from console by operators.
- DENIAL
- Denial of view – no access to systems data
- Denial of control – no control over systems
- Denial of safety – malfunctioning of safety instrument systems.
- MANIPULATION
- Manipulation of view – loss of data integrity
- Manipulation of control – changing of underlying instructions of a PLC device
- Manipulation of sensors and instruments – execution of instructions injected by attackers into systems controlling sensors, instruments, actuators
- Manipulation of safety – changing of values and conditions to render safety instrument system into an unknown state.
We will now look at the malware trends having an impact on the stages and steps in the ICS Cyber Kill Chain. This data is compiled from existing community research and known malware targeting ICS organizations. The data points show the number of malware strains that could make it to the shown below stages in the Kill chain. Even though a lot of strains were able to infect organizations in the IT network, only a few of them were able to or had the motivation of extracting sensitive data and to maintain undetected persistent access. The number of stage 2 ICS attacks were a bit higher due to either denial of control, denial of safety (DRAGOS, 2017), or manipulation of sensors and instruments (Symantec, 2011). This sheds some light on the fact that impacting business with attacks causing loss or denial of data and control with wormable ransomware is comparatively easier to achieve than attacks on actual OT equipment causing modification of control (Ex. Stuxnet) or denial of safety (Ex. TRISIS).
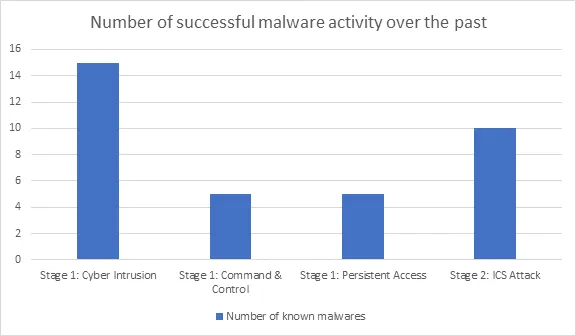
Figure 4: Historical Analysis of ICS malwares (MITRE, 2020)
Looking deeper into these malwares samples, understanding their operation in stage 2 of the ICS Kill Chain along with the Tools, Techniques and Procedures (TTP) used by the adversaries is vital. The following are a list of techniques commonly used by ICS malware that has the greatest impact.
- Data Historian Compromise (T810) – Attackers compromise or gain control of data historian in order to gain access to the control system environment. Database information could be exposed to attackers who can leverage this to perform reconnaissance and discover systems on the network.
- Block Command Message (T803) – Attackers modify the firmware to limit infected systems from receiving a command message rendering the system unresponsive to operators’ control. This can directly lead to an attack by denial of control.
- Block Serial COM (T805) – Attackers may open and hold a TCP session with an ethernet connected COM port, which would prevent legitimate access to the COM device. This can directly lead to an attack by loss of control.
- Control Device Identification (T808) – Attackers may use management software from infected operator systems to identify specifications of devices connected to the network. This allows attackers to find known vulnerabilities and use them to launch attacks.
- Activate Firmware Update Mode (T800) – Attackers may activate firmware update mode on devices to render it inactive or possibly install malicious firmware.
- Unauthorized Command Message (T855) – Attackers can send crafted command message to a control system to perform actions that are either outside its expected functionality or to cause damage to operations process.
- Service Stop (T881) – Attackers can stop or disable system services to impair process operations and cause significant damage to environment. This can also allow attackers to modify ICS configurations before restarting the services.
- Block Reporting Message (T804) – Attackers can hide their actions from an operator by blocking or preventing reporting message from reaching its intended target, as reporting messages usually contains event log data, I/O values of associated device. etc.
- Exploitation for Evasion (T820) – Attackers with some prior knowledge of a control device can exploit a software vulnerability in program, service, operating system, kernel, or firmware to inject malicious code into the system while evading detection or disabling security features altogether.
- Modify Control Logic (T833) – Attackers may inject malicious code in a system causing it to malfunction by modifying the underlying control logic that operates the actuators dependent on sensor readings.
Case Study: Malware attack at Kundankulam Nuclear Power Plant, India
In a recent cyberattack to Indian cyberspace, APT group Lazarus has targeted country’s largest nuclear power plant (KKNPP) which is responsible for producing 2000 MW of energy for the entire southern power grid. The DTrack malware used in this campaign to gather sensitive data and network architecture information from infected systems from the internal network, was initially used as a remote access Trojan that was originally developed to target ATMs of Indian Banks. From publicly available information, it has been determined that the malware ATMDtrack was operating in the wild during 2018 and parts of the code was reused to created DTrack which was later discovered in September 2019.
It is still not known how the initial infection took place at KKNPP but from public reports, the malware seems to have gained access to the internal KKNPP network after an infected user connected their laptop to the network.
The objectives of the malware seem to be limited to gathering the following information:
- Gathering browser history to %TEMP%\temp\browser.his
- Gathering host IP addresses to %TEMP%\temp\res.ip
- Gathering active connections to %TEMP%\temp\netstat.res
- Gathering all running processes to %TEMP%\temp\task.list
- Gathering network configuration data to %TEMP%\temp\netsh.res
- Get information of registered owner, organization, and OS install date from HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion
The malware contained strings of highly specific commands (image below) which suggests that this variant of DTrack malware was prepared after gathering enough information and credentials to exfiltrate data and system information.
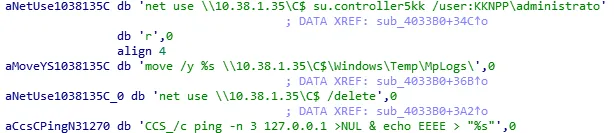
Figure 5: Highly specific commands as string constants in malware
To date, neither the security research community nor the NPCIL (Nuclear Power Corporation of India Limited) has reported on any evidence of any additional actions related to this campaign. This leads us to believe that this was a generally successful Stage 1 ICS Attack. Also to date, there has been no documented evidence on Stage 2 activity. A representation of the ICS Cyber Kill Chain for KKNPP attack is displayed below.
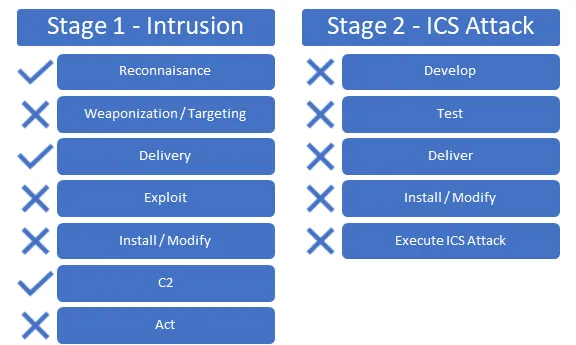
Figure 6: KKNPP Attack mapped to ICS Cyber Kill Chain
Remediation
The ICS Cyber Kill Chain provides a strong foundation for understanding the various stages of an attack on an ICS organization. Taking these into consideration during threat modelling in an organization will significantly highlight shortcomings in the security coverage.
Separate the safety systems behind a firewall and limit access to it via the network. Remove ICS components from direct Internet access. Place the OT network and IT network in separate compartments separated further by a DMZ firewall in between.
It is also important to regularly stay updated with vendor provided security updates and patches.
Moreover, an important takeaway should be to apply a layered defence strategy to both the IT and OT networks to prevent common malware attacks or attacker techniques from successful execution.
As from the past trends of ICS malware attacks, most adversaries fail in Stage 1 itself. Therefore, having a secured environment in both the enterprise and operations network is one of the key points to successfully preventing an ICS attack.
LMNTRIX has been successfully defending our ICS customers from the recent number of growing threats in view of increased geopolitical tensions across the continents. We have reviewed CISA Alert AA20-006A (CISA, 2020) to ensure that we have an up-to-date understanding of previously observed Iranian Tactics, Techniques, and Procedures (TTPs) and taken an aggressive stance on the following MITRE ATT&CK Techniques to identify possible future Iranian activity:
AT COMMAND LATERAL MOVEMENT
CERTUTIL FILE DOWNLOAD
COMMAND LINE OBFUSCATION
COMPRESSION OF SENSITIVE FILES
CREATION OF SETTINGCONTENT-MS FILES
CREDENTIAL ACQUISITION VIA REGISTRY HIVE DUMPING
DOWNLOADED URL FILES
ENCRYPTING FILES WITH 7ZIP
EXECUTION OF FILE WRITTEN OR MODIFIED BY MICROSOFT OFFICE
EXECUTION OF FILE WRITTEN OR MODIFIED BY PDF READER
EXECUTION OF PERSISTENT SCRIPTS
MODIFICATION OF WDIGEST SECURITY PROVIDER
ENCRYPTING FILES WITH WINRAR
NETWORK CONNECTION FROM UNUSUAL DIRECTORY
PERSISTENCE OF SCRIPTS VIA REGISTRY
PERSISTENT SCRIPTS IN THE STARTUP DIRECTORY
POWERSHELL REMOTING
POWERSHELL WITH UNUSUAL ARGUMENTS
SCHEDULED TASK COMMAND LATERAL MOVEMENT
SERVICE COMMAND LATERAL MOVEMENT
STEALTHY POWERSHELL LOADING
SUSPICIOUS DOCUMENT CREATED BY PDF READER
SUSPICIOUS JAR CHILD PROCESS
SUSPICIOUS JAR DESCENDANT PROCESS
SUSPICIOUS MS OFFICE CHILD PROCESS
SUSPICIOUS MS OFFICE DESCENDANT PROCESS (Mac)
SUSPICIOUS MS OFFICE DESCENDANT PROCESS (Windows)
SUSPICIOUS MS OUTLOOK CHILD PROCESS
SUSPICIOUS PDF READER CHILD PROCESS
SUSPICIOUS PDF READER DESCENDANT PROCESS
SUSPICIOUS POWERSHELL DOWNLOADS
SUSPICIOUS SCRIPT OBJECT EXECUTION
USERS CREATING SYSTEM TASKS
WEBSHELL DETECTION (Linux)
WEBSHELL DETECTION (Windows)
WINDOWS SCRIPT EXECUTING POWERSHELL
WPAD SERVICE EXPLOIT
Contact LMNTRIX for more information.
Works Cited
(2011, February). Retrieved from Symantec: https://www.symantec.com/content/en/us/enterprise/media/security_response/whitepapers/w32_stuxnet_dossier.pdf
(2015, October). Retrieved from SANS: https://www.sans.org/reading-room/whitepapers/ICS/industrial-control-system-cyber-kill-chain-36297
(2017, December). Retrieved from DRAGOS: https://dragos.com/wp-content/uploads/TRISIS-01.pdf
(2020, January). Retrieved from MITRE: https://collaborate.mitre.org/attackics/index.php/Software
(2020, January). Retrieved from CISA: https://www.us-cert.gov/ncas/alerts/aa20-006a
On 2020-05-08


