
Introduction
The Internet was originally built around the late 1960s. Nobody at the time would have predicted the proliferation of internet-based attacks like memory corruption, XSS, SQLi, RFI/LFI, and account takeovers to become the norm.
Since then it has become important for security vendors to embrace a reactive mindset to prepare for unforeseen evolutions on the threat landscape. With signature and behavioral-based detection methods that rely on a perceived hooded hacker attacking their network and systems, the traditional response is to block it (assuming they already have an accurate signature and behavior-based detection protocol for that specific attack). This is then followed by the industry building solutions in response.
Security vendors are constantly on the back foot, since attackers and their tools, tactics, and procedures are constantly evolving at a rapid pace. The security vendor mistakenly assumes attackers will use the same approach time and again. This constant innovation leaves security vendors scratching their heads implying it is time to evolve in threat detection and response, shining a light on any and ALL active threats that lurk within your organisation’s network.
There is a clear winner and loser in an asymmetric game where one player keeps evolving. This all but begs the question, as defenders why are we not taking the lead?
There may be a silver lining on the horizon. Due to the world coming to a standstill with COVID19 pandemic, we found ourselves at home with not much to do. There is only so much Fortnite someone can play before they decide to do something more productive. Many people decided transitioning into cyber security was a positive way for them to survive in a world defined by remote work. Cyber security consists of a set of skills that is in high demand, across all economic vertices; it is incredibly likely that some of these individuals may combine previous knowledge and skill bases to help revolutionise the industry.
Red vs. Blue Dilemma
Whether it is books, videos, magazines, or newsletters, all the media publications and mass communication we receive glamorizes the hacker and as a result the white hat counterparts, penetration tester and red teamer receive a buff. If you want to get into red teaming or pen testing and need free or low-cost training, there’s a sea of quality offerings now. If you want to be able to train with hands-on tools, there is a plethora of free, but high-quality, open source tools available to you.
However, if you want to be on the blue team, the defender’s side, sorry folks, you are going to have to pay up thousands of dollars for training. Most SMB/Medium Sized companies do not have the budget to field a group of people in the IT department or their Security Operations team for costly security training. You are not going to have access to any of these platforms. You can NOT become proficient with them unless you work for a company that has ALREADY bought them. For example, Fortinet has their Firewall engineer 1-3 levels open and free, and others occasionally open up for certain demographics or giveaways. This is sadly not going to be enough for a tidal wave of enthusiasts trying to get a break in the field of blue teaming.
So what we have is imbalance regarding red team vs. blue team hires. This means that companies can readily test infrastructure, finding all the vulnerabilities, and showing how to bypass all these expensive products invested in. Conversely, there is almost no pipeline to practice and evolve for the infrastructure’s defenders, the blue team. It’s hard to find people today who are saying with pride, they want to be a “firewall engineer”, a “SOC analyst” or an “IAM specialist”. It’s just not happening because there is no path, no means, no way which is easily accessible.
If you want all the talent to be focused on red teaming, namely showing the flaws and vulnerabilities in a product, software, or hardware, stay in the current direction for training. Simply put this path is great.
For those wanting to be a defender, the path is unnecessarily more difficult. At some point, the security vendors in the defense space have to OPEN UP these paywalls and give defensive training away. Give all people, from all economic backgrounds and geographic regions a fair shot in becoming a blue teamer. Otherwise, there is going to be no one there to operate and tune your products. Further, the drastic skills shortage in the sector is bound to widen, hurting the product providers in the long run.
We don’t need a couple of people with CCIE level knowledge in Cisco on contract, we need all the training we can get, we need more people with defensive skills to be a part of the cyber security domain.
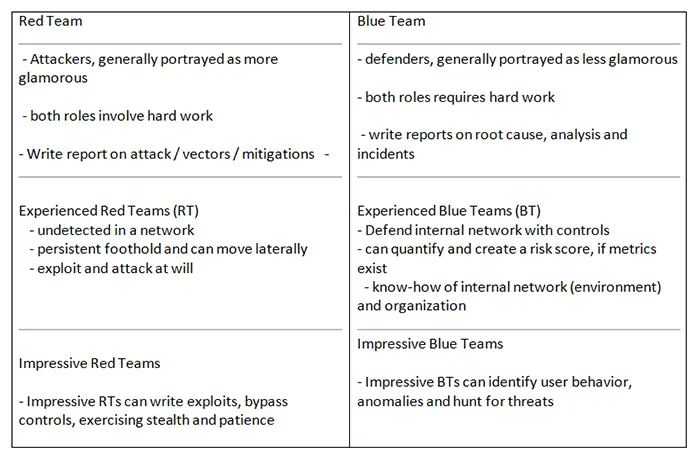
Required Skillsets
Skill sets for Red teams and Blue teams
Conclusion
As Albert Einstein said, “Insanity is doing the same thing over and over while expecting different results.” I could be paraphrasing here, but, IF that saying holds true, why do we continue with the same approach to security that continues to fail us? It is no secret that the cybersecurity sector is suffering from a massive skills shortage. With one side of the coin, red teams, being so favoured, the skills shortage has become even more lopsided. The sector needs to address how to train and hire infrastructure defenders and without the steep financial hurdle prospective hires might encounter.



[…] As we mentioned in another blog post, a skilled security team would be able to stop an attacker at the beginning of the kill chain, but […]