
Overview
Since its creation six years ago, Kryptik malware has been used in various campaigns – the most of recent of which was in October last year where 300,000 detections were recorded in the U.S alone. Interestingly, 94 per cent of these cases were in West Virginia, which coincided with elections for the state governor.
We recently spotted a sample of the latest Kryptik variant which we’ll dissect today. Most AV vendors detect this version as “MSIL-Kryptik malware”.
File details:
• MD5: 245468fca16ae49742f45a95ce4d5a8a
• File Size: 869 KB
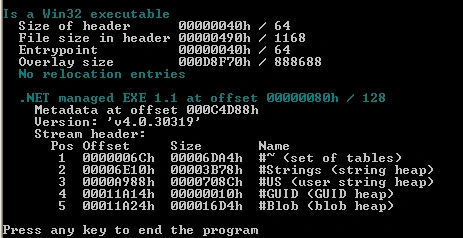
Figure 1 compiled in .net
Static analysis
This variant is compiled in .net and one of the first things we noticed was a large list of resources named ‘Membership_system’:
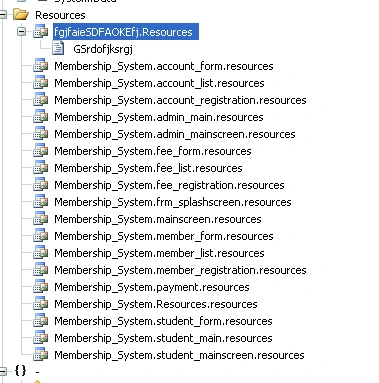
Figure 2 File resources
The resources include files named ‘account form’, ‘account list’, ‘account registration’, and ‘student form’.
After investigating further, our researchers spotted the same list of resources in the code’s functions and classes:
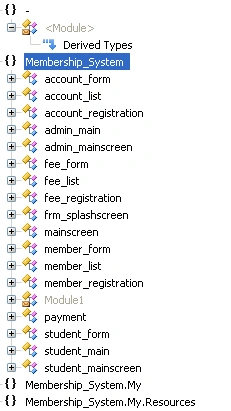
Figure 3 ‘Member_System’ Functions and Classes
Account_form and account_list contains boxes like ‘username’, ‘password’, ‘first name’ and ‘last name’. We also discovered buttons like btn_toggle (toggle), btn_update (update), btn_back (back), and btn_delete (delete). We checked the admin, payment, and student forms, and found each has details you’d expect to see in a University form such as fee payment for the year, semester and class details.
Dynamic analysis
We executed the sample in a controlled environment and discovered more artefacts such as the creation of folders and files in suspicious locations (%appdata%).
| Folders Created: 2 c:\Documents and Settings\User Name\Application Data\Microsoft\Windows c:\Documents and Settings\User Name\Application Data\Microsoft\Windows\DwiDesk |
File dropping tricks:
In general, a piece of malware will drop a file in the %appdata% location to maintain persistence with the help of run entry. In this case, we observed a trick where duplicate PE files are dropped in the following location:
“c:\Documents and Settings\User Name\Application Data\Microsoft\Windows\DwiDesk\ WinReg32.exe”.
A link file of the WinReg.exe is then copied into the %appdata% location “c:\Documents and Settings\User Name\Application Data\WinReg.lnk”.
This link file is pointing to the PE file inside the “%appdata%\Microsoft\Windows\DwiDesk\WinReg.exe” location. This link file maintains persistence with the help of the following run entry:
Registry entry added:
• Key: “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce”
• Value as “Load”
Physical location as “c:\Documents and Settings\User Name\Application Data\WinReg32.lnk”
IOC:
Files and Folder:
• MD5: 245468fca16ae49742f45a95ce4d5a8a
• “c:\Documents and Settings\User Name\Application Data\WinReg.lnk”
• “c:\Documents and Settings\User Name\Application Data\Microsoft\Windows\DwiDesk\WinReg.exe”
• “c:\Documents and Settings\User Name\Application Data%\Microsoft\Windows\DwiDesk”
Malicious Domain:
• crackstar.ddns(.)net
Registry entries:
• “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce” “Load”
• “c:\Documents and Settings\User Name\Application Data\WinReg32.lnk”
Conclusion
It is clear this variant is used to target University students. Our analysis indicates of the code shows a fake application has been developed to collect student payment details.
Students would be targeted with an email crafted to look as though it came from their education institution. The email would include a link leading the student to a website hosting the Kryptik malware. Thinking they’re interacting with a legitimate website, students would be duped into handing their personal and payment details over to attackers.


