
While ransomware was front of mind last year, with WannaCry and Petya making headlines around the world, banking trojans were also making the rounds though with much less fanfare.
Banking trojans are popular with hackers as they enable the attacker to steal online banking credentials. The potential windfall of a successfully executed banking trojan campaign can be particularly lucrative, so its no wonder strains like Zeus continue to be observed in the wild almost a decade after its discovery.
In November last year, researchers discovered a new Banking trojan dubbed “IcedID”. The authors of the strain targeted banks, payment card providers, mobile service providers, and e-commerce sites in the U.S, as well as major banks in the U.K.
For a quick background, IcedID performed sophisticated redirection attacks, serving up fake bank webpages designed to look incredibly similar to the legitimate version. The trojan lies in wait and when the victim enters a bank URL on the compromised machine that matches the list of URLs in IcedID’s code, it executes a designated web injection. The victim, thinking they’re interacting with their bank, then unwittingly sends their details to the attacker’s server.
Below is an example of a malicious page designed to mimic a legitimate bank log-in page:
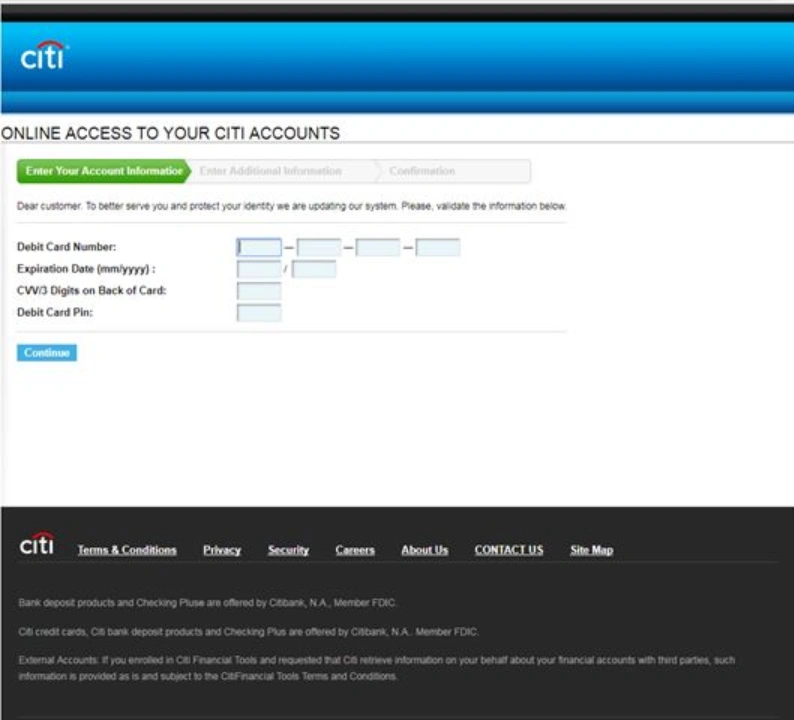
URL: https:\/\/www.financebankpay[.]com/citiCards/
A more detailed rundown on IcedID’s functionality is available here.
In monitoring deep and dark web activity for our clients, LMNTRIX researchers have uncovered how IcedID is being bought and sold in the internet underworld, shedding light on the innerworkings of malicious merchants.
Deep and Dark Web Dealing
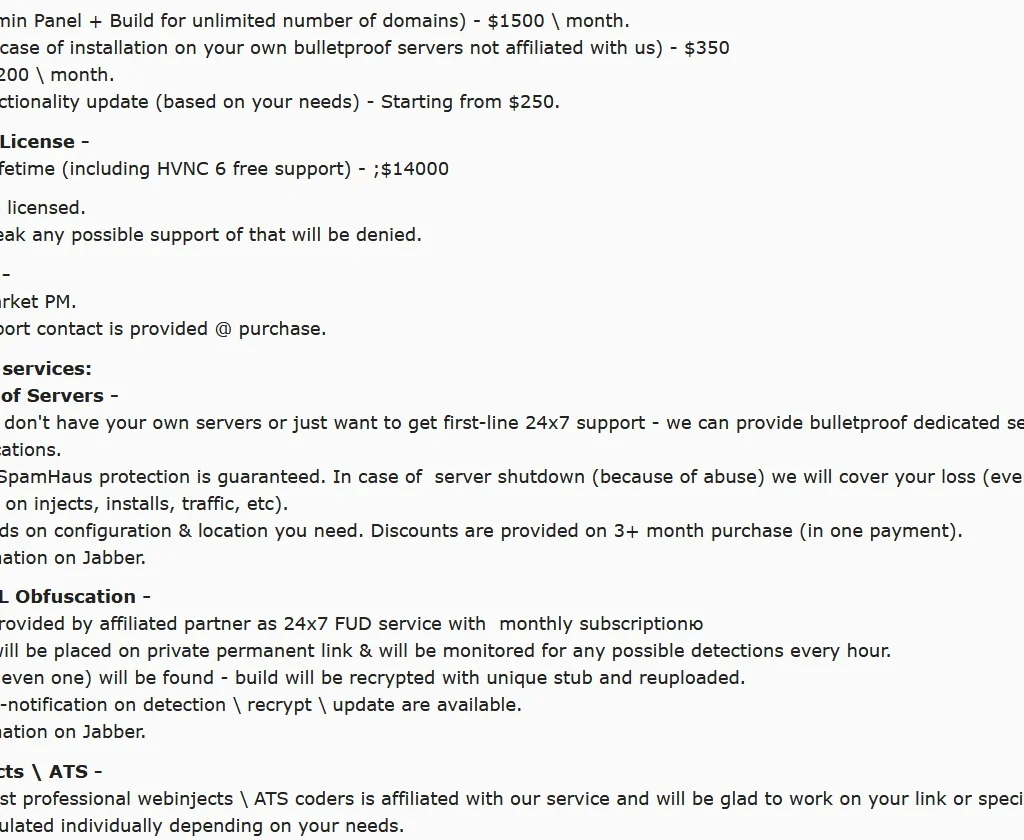
In the image below, we can see that the botnet infrastructure underpinning IcedID is being sold with different service levels. A lifetime license can be purchased for $14,000 (which includes free ongoing customer support), while an as-a-service offering is available for $1500 per month for the discerning hacker who prefers OPEX over the initial CAPEX outlay.
The authors also offer customisation starting from $250, and the inclusion of a hidden virtual network computing (HVNC) module for $1200 a month.
Bulletproof Servers can also be supplied, and if the server is shutdown, the authors even offer to cover the loss. Server packages are discounted when purchased for three months and paid upfront.
This shows how sophisticated the online marketplace for hacking tools has become. We were surprised a free set of steak knives wasn’t on offer to the first 50 customers…
Below we see some of the specific functionality of the “IcedID Banking Bot”. Features include keylogging, anti-virus detection, sandbox detection and DNS spoofing on Chrome, FireFox and Internet Explorer:
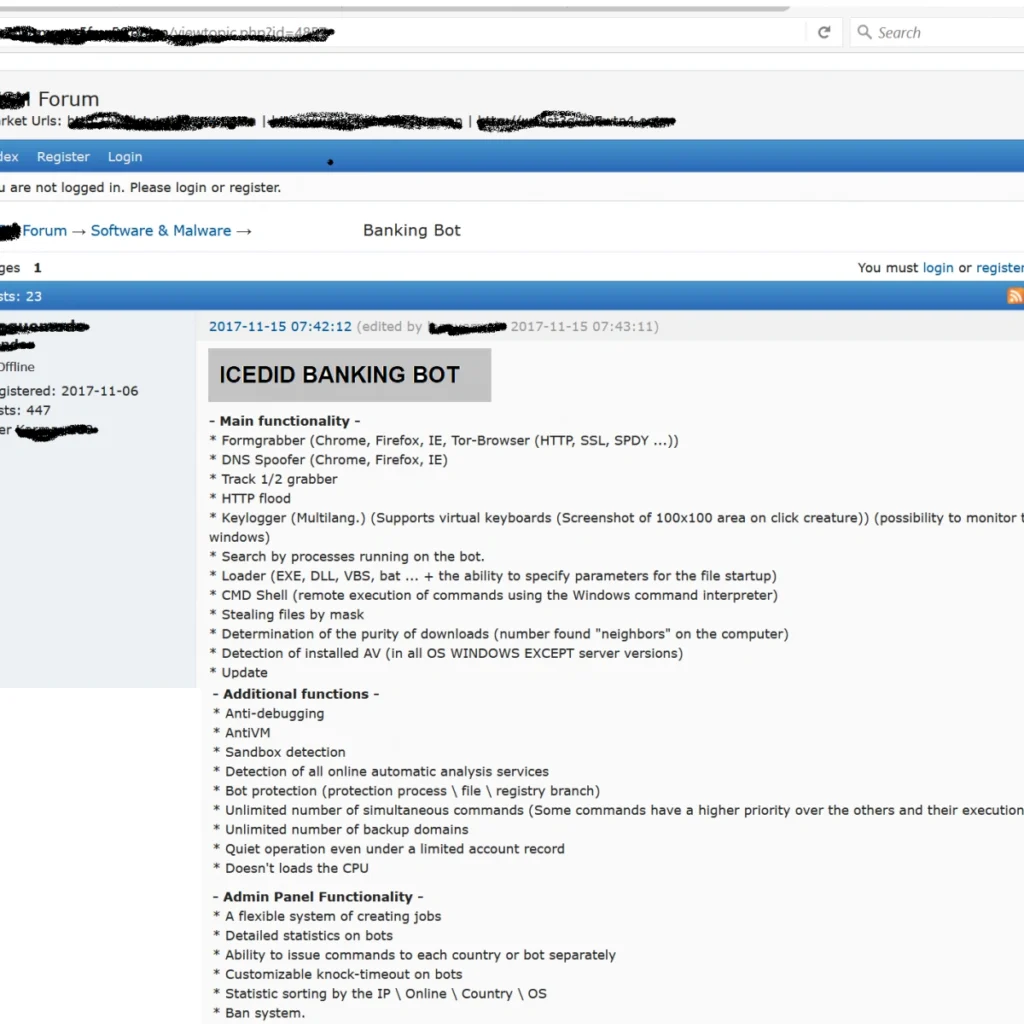
While the above images are targeted to English-speaking culprits, below we see Russian-speaking attackers are also being catered to:

Its clear to see that industrious hackers are increasingly lowering the bar for entry into the world of cyber-criminality. No longer do people need to develop their own exploits, they can just buy a prepared package and even contact customer support when something goes wrong.


