Lorenz is a human operated ransomware group that targets global organizations. To pressurize the victim, the malware operator threatens the user to leak data online if the ransom is not paid. The Lorenz operators work hard on their target recon. They conduct research on their target’s employees, suppliers, and partners before launching the attack. The Lorenz group can even move from one already compromised victim to another in this manner. The information they have gathered at every step is used to tailor the attack to the target.
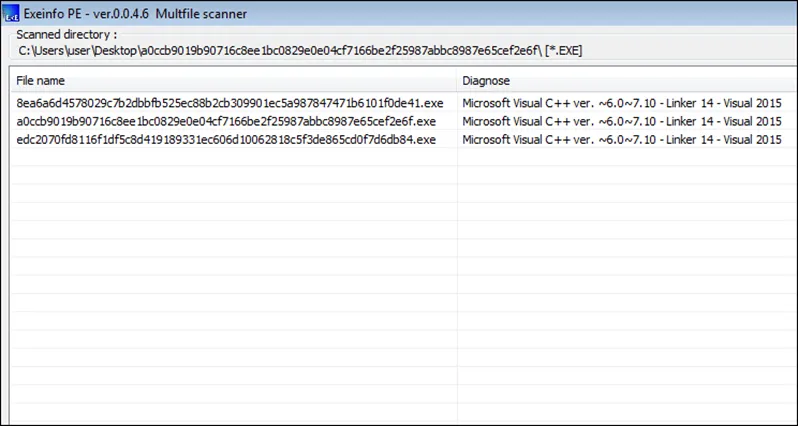
At first glance, the ransomware appears to be written in C++ using Microsoft Visual Studio 2015. An interesting finding in the two samples we examined seems to be that they are both compiled with debug info, despite the fact that they appear to be compiled in release mode. Debugging information can be useful since it makes the analysis a little easier. Lorenz like most ransomware creates a mutex during routine startup. The ‘wolf’ mutex is used to prevent the ransomware from starting twice. The connections in the samples we examined were steered to the command and control server’s IP address on port 55.
Language Used: Microsoft Visual C / C++
Target: Mitel / VoIP appliances
Vulnerability / Exploit Used: CVE-2022-29499
Brief Overview of CVE-2022-29499
A ransomware attack was launched against an unidentified target, with Mitel’s VoIP appliance serving as an entry point. Attackers are actively exploiting CVE-2022-29499 to gain remote code execution and initial access to their victim’s environment. The CVSS vulnerability scoring system assigns a severity of 9.8 to this vulnerability.
Mitel fixed the CVE-2022-29499, which affects the Mitel Service Appliance component of MiVoice Connect, in April 2022, but the fix did not work. The “bug” according to Mitel, allows attackers to execute remote code within the context of the Mitel Service Appliance.

The following Appliances / Software are impacted;
R19.2 SP3 (22.20.2300.0) and earlier R14.x and earlier
SA 100 SA400 Virtual SA MiVoice Connect Service appliances
R19.2 SP3 (22.20.2300.0) and earlier R14.x and earlier
The CVE-2022-29499 exploit which includes two HTTP GET requests is used to trigger remote code execution by fetching rogue commands from an attacker-controlled infrastructure. LMNTRIX CDC observed the attacker using the exploit to create a reverse shell and launch a web shell (“pdf import.php”) on the VoIP appliance during the investigation.
The attacker attempted to go undetected by performing anti-forensic techniques on the VoIP appliance – renaming the binary to “memdump”. The device observed by LMNTRIX was a Linux Mitel VoIP appliance deployed on the network perimeter, with EDR software. Mitel recommends that customers with affected product versions implement the proposed remediation as soon as possible, in addition to reviewing the product Security Bulletin.
Execution & Propagation of Lorenz ransomware
STEP 1: Cybercriminals are executing Lorenz Ransomware manually on the compromised systems. In this step, the attacker uses public vulnerabilities against the targeted network and exploits them. Public-facing servers and Internet exposed machines are generally found by special search engines such as SHODAN.
STEP 2: Malware breaches a network and spread laterally to other connected devices till the malware gains access to windows domain administrator credentials. Malware captures the credentials and brute force to gain access over the network.
STEP 3: While spreading throughout the network, the malware gathers unencrypted data from infected systems and sends it back to the command-control server.
STEP 4: The attacker may leak some portion of stolen data on the following public website.
hxxp://lorenzezzket6afhfqfjagefsrjn44edsgi26kq4sfhqjal6wyneh4yd.onion
STEP 5: In this step, the malware launches an encryptor by executing the scripts. The ransomware uses an AES encryption algorithm and an embedded RSA key to encrypt the encryption key, it appends the “. Lorenz.sz40” extension to all files.
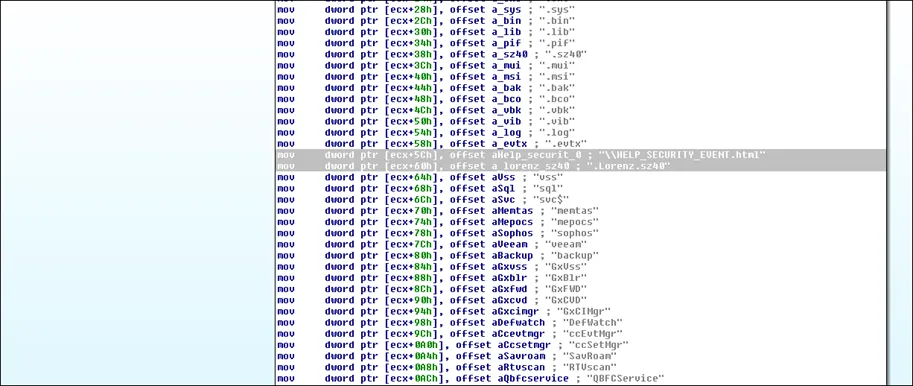
STEP 6: Later, the malware drops a ransom note in all affected folders with the name “HELP_SECURITY_EVENT.html”. It also creates a unique web link of TOR website.
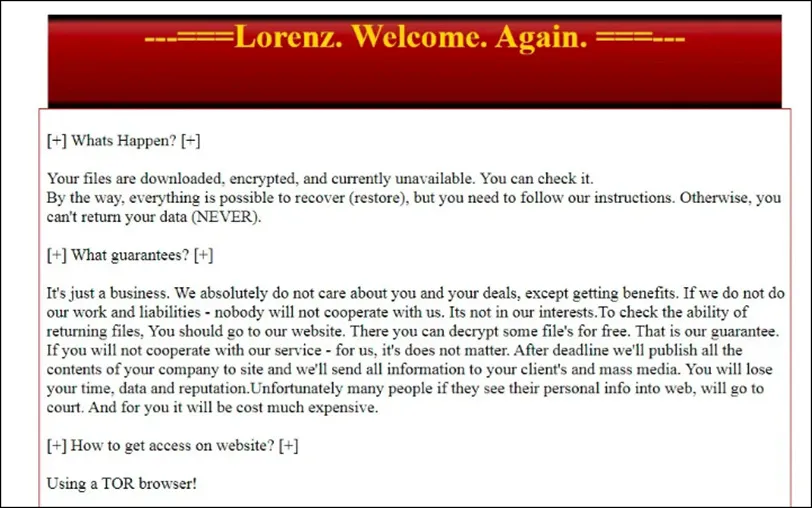
Some Interesting Observations by LMNTRIX CDC
Assigning SZ40 Extension for infected files, HELP SECURITY EVENT.html is the actual ransom note,
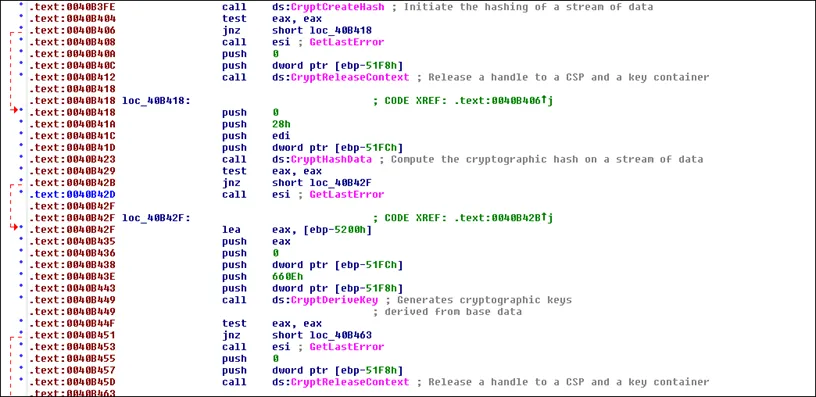
The sample we analyzed was compiled using Visual C/C++ in the year 2021. The file supports ASLR, DEP and uses Microsoft’s Enhanced Cryptographic Functions as shown below.
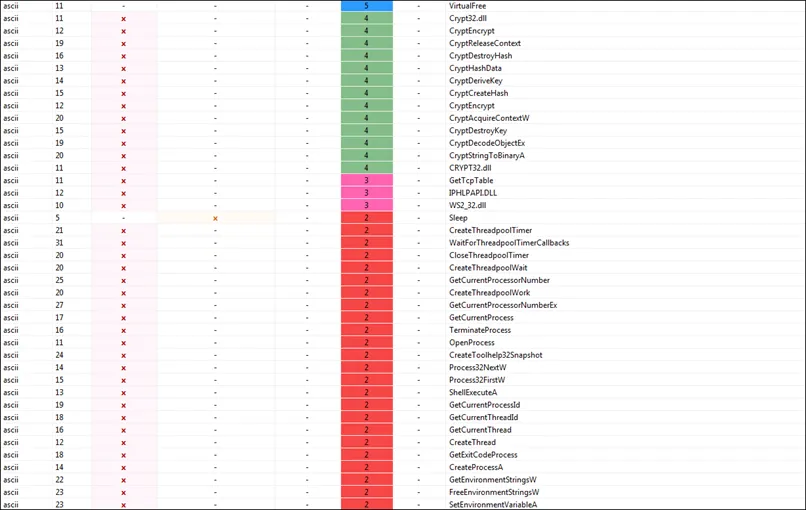
Functions Imported by the Lorenz Ransomware (Sample)
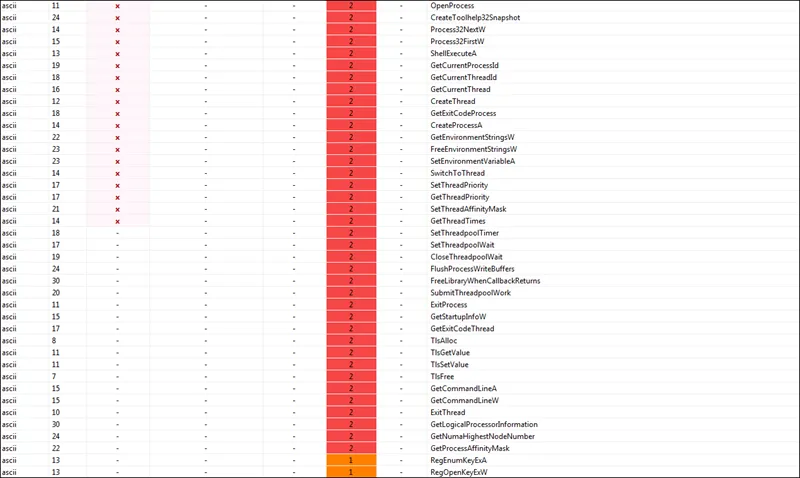
Creating Scheduled Tasks – Lorenz ransomware created a remote scheduled task that runs another ransomware binary on a computer in the same network that was infected. This behavior shows that the attackers moved laterally through the systems, gathered information, and stole passwords before sending the ransomware’s payload. The names of the scheduled tasks in the binaries are the same ones found when other scheduled tasks were made in other binaries, and they all start with “SZ40.” When the malware is run, it deletes the planned task to get rid of any remains that may alert your IT / security operations team.
Dropping 2 files / processes and deleting Volume Shadow Copy using the following commands,
C:\Windows\System32\wbem\WMIC.exe WMIC.exe shadowcopy delete /nointeractive
C:\Windows\System32\cmd.exe cmd.exe /c WMIC.exe shadowcopy delete /nointeractive & bcdedit.exe /set {default} recoveryenabled no & bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures
How Lorenz Ransomware Works
Lorenz Ransomware infiltrates a victim’s machine via phishing emails or other form of social engineering. Once on the victim’s machine, the malware will begin encrypting files with a highly sophisticated encryption algorithm. Following that, the malware will show a ransom note demanding payment in exchange for the decryption key. Lorenz group uses the double extortion model to get the ransom amount paid. In an effort to coax people in to paying the money, the data is first encrypted. Data is also stolen (exfiltrated), and leaked further get the victim’s co-operation to pay the ransom.
Estimated Ransom Amount: Lorenz ransom demands can range from $500,000 to $700,000 USD.
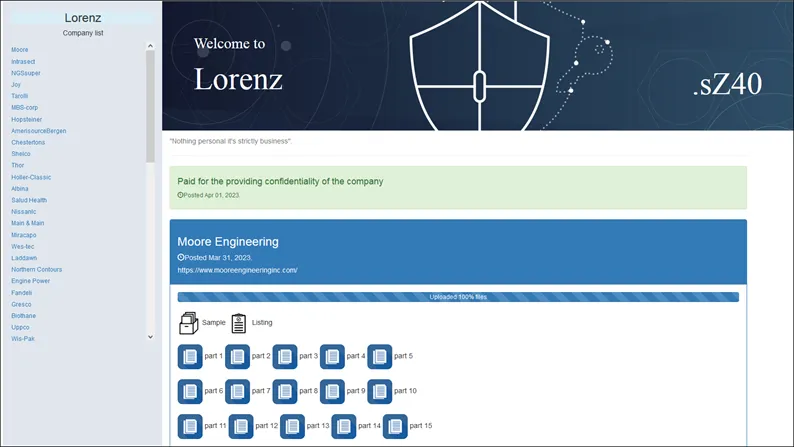
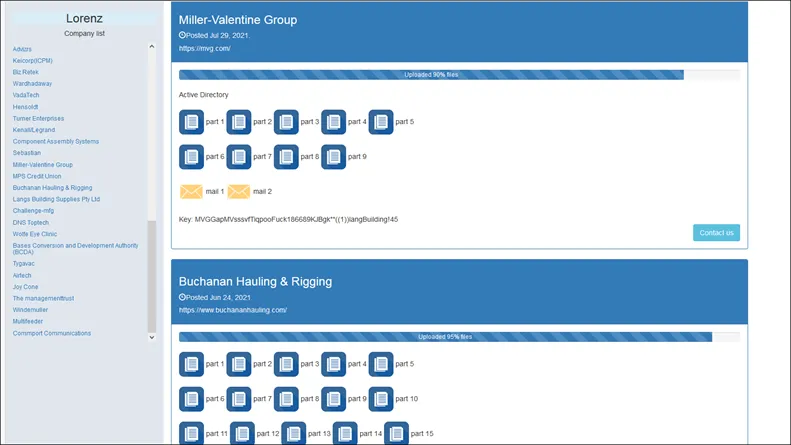
The impact of Lorenz Ransomware on business and individuals
Lorenz Ransomware had a major global effect on both companies and consumers alike. It specifically targeted big organisations such as hospitals, universities, and government agencies. These organisations frequently have valuable data that is essential to their business operations, and threat of data loss could be potentially disastrous. The impact of Lorenz Ransomware is not limited to the loss of data. It can also cause significant financial harm to businesses and individuals. The ransom demands made by the malware can be substantial, with some victims being asked to pay hundreds of thousands or even millions of dollars in exchange for the ransomware decryption key.
Prevention and Mitigation for Lorenz Ransomware
There are several measures that businesses and individuals can take to prevent and mitigate the effects of Lorenz Ransomware. One of the most important is to ensure that all software and systems are up to date and that security patches are applied as soon as they become available. This will help to prevent vulnerabilities that can be exploited by malware like Lorenz Ransomware.
It is also important to back up all critical data, and test these backup copies regularly with a restoration exercise. Testing backups will help ensure that data can be restored, and business can continue operations with a slight blip in the event of an unexpected ransomware infection.
An important, but oft-neglected measure is employee education/security awareness for employees about the dangers of phishing emails, spam mails, ransomware (modus operandi) and other forms of social engineering. Employees should be trained to recognize suspicious emails and to report them to IT security and/or security operations personnel.
How LMNTRIX would address the Lorenz infection,
LMNTRIX researchers have said repeatedly, that updating software to the latest version at the right time is still an important step in defending the network against Lorenz like attacks, but in the case of critical vulnerabilities, companies should also check their environment for exploit attempts and possible intrusions, most companies lack the skillset to inventory their assets, scan them for vulnerabilities both internal and external and patch devices such as switches, routers and VoIP/SIP phones and network printers.
Scanning for vulnerabilities and patching them before a malware infection occurs is the best case scenario,
LMNTRIX XDR can help you ‘after an infection’ with EDR, Next Gen Antivirus, Network Detection & Response (NDR), Contextual threat intelligence and Machine Learning to facilitate detection across all phases of the Lorenz attack.
Enable your device logs and, LMNTRIX CDC will review the logs periodically, it gives you a slight edge to stay proactive, while you can leave the containment and remediation with our team.
Looking for signs of unauthorized access or behavior on your network with continuous threat hunting service,
And LMNTRIX CDC will be constantly peeking in to your network monitoring tool for “strange” (anomalous) traffic could reveal an intrusion that would get past a missed security update.
Conclusion
Lorenz Ransomware is a highly sophisticated kind of ransomware that can cause significant damage to companies and consumers. Organizations must take measures to prevent and mitigate the effects of this ransomware, such as updating software, educating employees about the dangers of phishing, and regularly backing up essential data. By implementing these safeguards in conjunction with an assumed breach mindset and proactive threat hunting exercises, businesses can reduce their vulnerability to Lorenz Ransomware and other kinds of malware all year round.
Indicators of Compromise for Lorenz Ransomware
| Indicator | Description |
| 71cdbbc62e10983db183ca60ab964c1a3dab0d279c5326b2e920522480780956 | Lorenz ransomware |
| 4b1170f7774acfdc5517fbe1c911f2bd9f1af498f3c3d25078f05c95701cc999 | Lorenz ransomware |
| 157[.]90[.]147[.]28 | C2 |
| 172[.]86[.]75[.]63 | C2 |
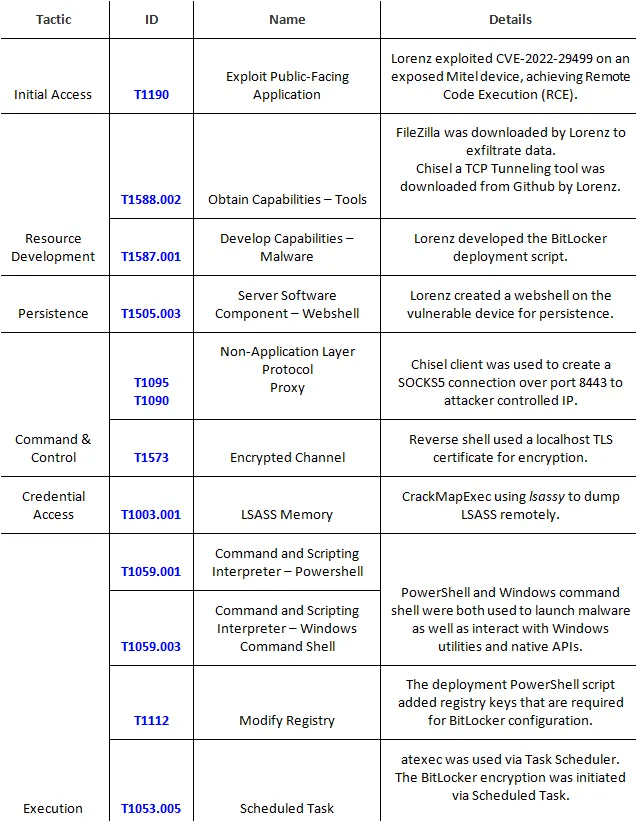
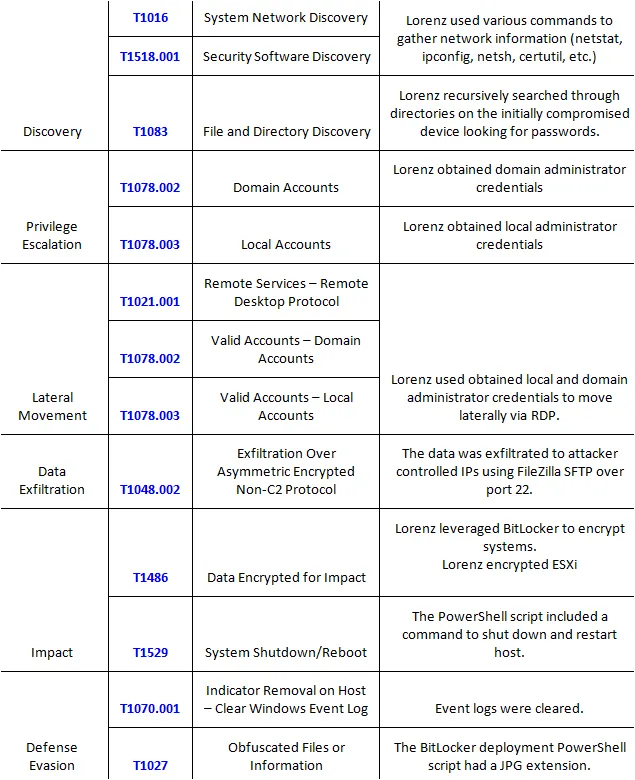
MITRE ATT&CK Matrix for Lorenz Ransomware