
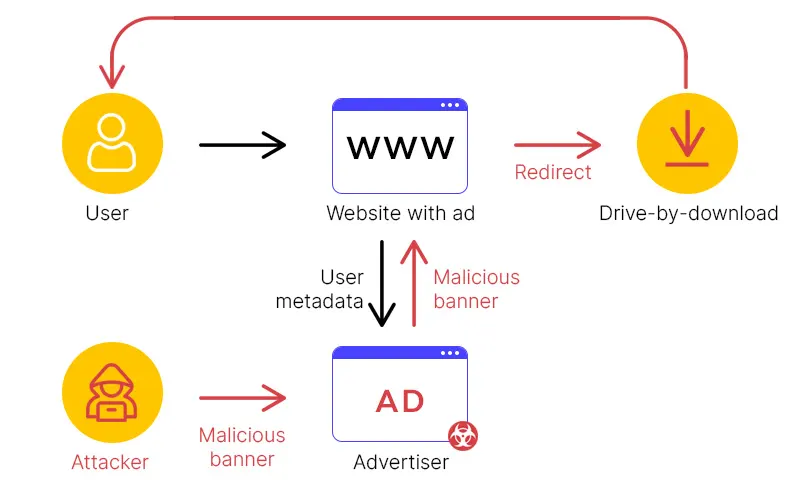
MasquerAds
MasquerAds are malware that pretends to be advertising to fool people into downloading and installing it. The threat actors behind MasquerAds create fake websites to spread malware. Malicious advertisements and previously unknown websites can be used for sending phishing emails to promote these rogue sites.
“MasquerAds” exploits the user’s trust in Google and its promoted search results. They also avoid even the most powerful EDRs by abusing renowned file-sharing platforms and software companies. Even simple actions like Google Search using a web browser necessitate more behavioral and unbiased protection in 2022/23.
A rogue site’s malware payload can be distributed through several methods. The site may utilize a mix of browser vulnerabilities and/or social engineering to automatically install malware on users’ devices. The malware payload can collect personal data, display advertising, or link users to dangerous websites.
Sample Zloader, it could serve as an example of how malicious ads get ransomware on to your system and disable security tools, as needed.
VERMUX Threat Group
Vermux is a threat actor that distributes cryptocurrency-related malware. The threat actor uses phishing emails, rogue websites, and software laced with malware are favored methods to disseminate their payloads. The malware is known to steal a variety of cryptocurrencies including Bitcoin, Monero, and Ethereum by stealing wallet information and private keys to grant access to the victim’s funds.
Vermux malware specifically targets the machine’s Graphics Processing Unit (GPU) for cryptocurrency mining by hijacking an infected PC’s processing capacity to mine cryptocurrency for the threat actor. Vermux malware can infect Windows & Linux computers via email attachments, corrupted websites, and masquerads (malicious advertisements). After installation, the malware quietly mines cryptocurrency on the victim’s machine, this type of malware is often referred to as a crypto miner.
In late December 2022, reports began to emerge that Google Ads were being abused to spread malware. Researchers discovered that multiple campaigns have been abusing Google Ads hiding malicious redirects by profiling for a one-time valid gclid value (Google identifier for promotional flow) as well as additional visitors’ information (geo-location, user-agent, and several other bits of information stored in the browser ).
This fingerprinting together with server-side forwarding makes this malicious forwarding hidden from Google as well as security sandboxes used to detect malicious activity. Using this attack method, threat actors were able to change malicious payloads daily and bundle the malware with legitimate software.
Further, to prevent detection malware payloads were bloated to 500Mb and above preventing detection from traditional anti-virus products. Other campaigns hid malware inside reputable file-sharing and code-hosting servers like Discord’s CDN, Dropbox, and GitHub. Researchers soon discovered that Vermux was seen abusing Google Ads in the above-mentioned way. Not only was Vermux deploying cryptominers but a variant of the Vidar trojan, a feature-rich info stealer.
To avoid Vermux and similar threat actors, avoid opening emails from unfamiliar sources, use anti-virus software, and keep it updated. Firewalls and network segmentation can also prevent malware from spreading. Another useful countermeasure is to use hardware wallets. Hardware wallets have proven to be much safer than software wallets for storing cryptocurrency.
Search Engine Advertising
Threat actors can use search engine advertising to spread malware by placing deceptive adverts at the top of search results. Clicking may lead users to a bad website that installs malware or steals personal data. Google has tight regulations for ad content and landing pages, automated methods to detect and remove malicious advertisements, and a reporting system for users to report suspect or harmful ads. Despite these measures, fraudulent advertising may surface on the platform from time to time.
Malicious Advertising (Example)
Royal Ransomware is distributed by seasoned threat actors, and attacks using Royal ransomware indicate a pattern of continuous innovation by adopting the following delivery methods,
● Using Google Ads in a campaign to blend in with normal advertising traffic.
● Making malicious downloads appear authentic by hosting fake installer files on legitimate-looking download sites.
● Using contact forms located on an organization’s website to distribute phishing links.
Did You Know? Royal Ransomware is launched from the command line & developed in C/C++ language. The said behavior suggests a pen-testing team worked to breach the internal network and performed privilege escalation and lateral movement, reinforcing one of LMNTRIX’s core messages – To catch a human you need a human being.
To avoid threats such as Masquerads and similar tactics used by ransomware gangs like ROyal Ransomware, avoid clicking on ads, and use an EDR/EPP security control that can detect threats based on the signature, heuristic, and behavioral aspects of malware. Make sure you report suspicious advertising to Google within 24 hours from the moment you encounter it. This greatly helps Google’s ability to crack down on malicious advertising campaigns to prevent further infections.
Fake MSI Afterburner Targeting Windows Gamers
MSI’s Afterburner graphics card overclocking software lets users tweak settings to boost performance. The software has a simple interface and includes many clock, voltage, and fan speed choices. The app lets users monitor their GPU’s temperature, power usage, and performance indicators in real-time. Much of the app’s popularity rests in the fact that most graphics cards can use the software and it is not limited to MSI’s own offerings.
Unfortunately, threat actors looked to abuse the app’s popularity to spread malware. Afterberner.live and msi-afterburner-download.ru were fake third-party MSI Afterburner websites targeting Windows gamers. The fake installers were promoted by BlackSEO which uses common search engine optimization techniques to push malicious ads to users and score better on search engine results tricking users into clicking malicious links. BlackSEO was used to redirect to several other malicious websites including:
● msi-afterburner–download.site
● msi-afterburner-download.site
● msi-afterburner-download.tech
● msi-afterburner-download.online
● msi-afterburner-download.store
● msi-afterburner-download.ru
● msi-afterburner.download
● mslafterburners.com
● Msi-afterburnerr.com
A quick look at the address with no further analysis could fool even the wariest of gamers looking to boost the performance of their current rig. Fake software that poses like real software, but potentially contains a piece of malware. Users should only download and install software from trusted and verified sources like the MSI website (directly). To guarantee the software is trustworthy, users should follow best practices such as checking the digital signature of the installation package.
Modus Operandi of Fake MSI Afterburner malware
When MSIAfterburnerSetup.msi is launched, the real Afterburner application is installed. The installer will silently install RedLine info-stealer malware and an XMR miner on the hacked device.
A 64-bit Python program named “browser assistant.exe” gets created in the local Program Files directory; it injects a shell into the installer’s process to install the crypto miner.
This shellcode injects the XMR miner into explorer.exe memory from a GitHub source. The miner never touches the disc, greatly reducing the chances traditional security products detect the malware payload. Further, the miner can detect how many threads the CPU has to make for more efficient mining of Monero without being detected. Monero is a cryptocurrency favored by threat actors for its increased focus on anonymity. For the purpose of cryptomining, Monero is favored by specific groups as it can be mined using a CPU rather than a GPU, the latter might not be present on a victim’s machine.
Conclusion
Security to a reasonable extent is an issue of trust, hence we always advise you to choose trusted providers on the World Wide Web. However, no one is flawless, and more threat actors are likely to exploit these security gaps than we can think in the New Year. To avoid MasquerAds, update your devices and software, avoid strange links and adverts, and use a good antivirus product. Avoid accessing untrustworthy websites that ask to install software or updates.
We see it here at LMNTRIX every day — the continual rat race between the firms controlling sophisticated advertisement systems, global content delivery networks serving the content, and security infrastructure being evaded by those evasive individuals who find a way to sneak under the radar, exploiting naive users for their own gain.As a power user of the internet, you should consider using browser plugins such as AdBlock Plus, uBlock Origin, or NoScript for blocking harmful advertisements such as masquerads.


