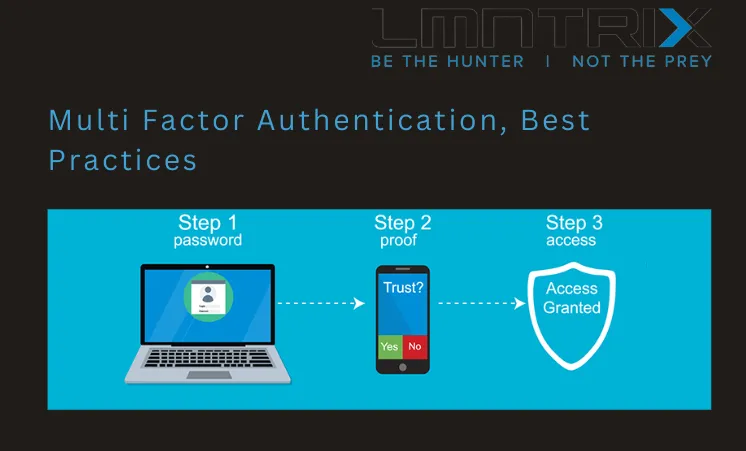
In this article, we will continue our discussion on MFA with a focus on what needs to be focused on when developing your organization’s MFA policy.
Considerations When Adopting MFA
In the previous article, we discussed what is considered MFA so we will not bore readers with the content we have already covered. Rather, we will begin with important considerations when developing your organization’s MFA policies and what hardware or software should be adopted to best realize the policies to be put in place.
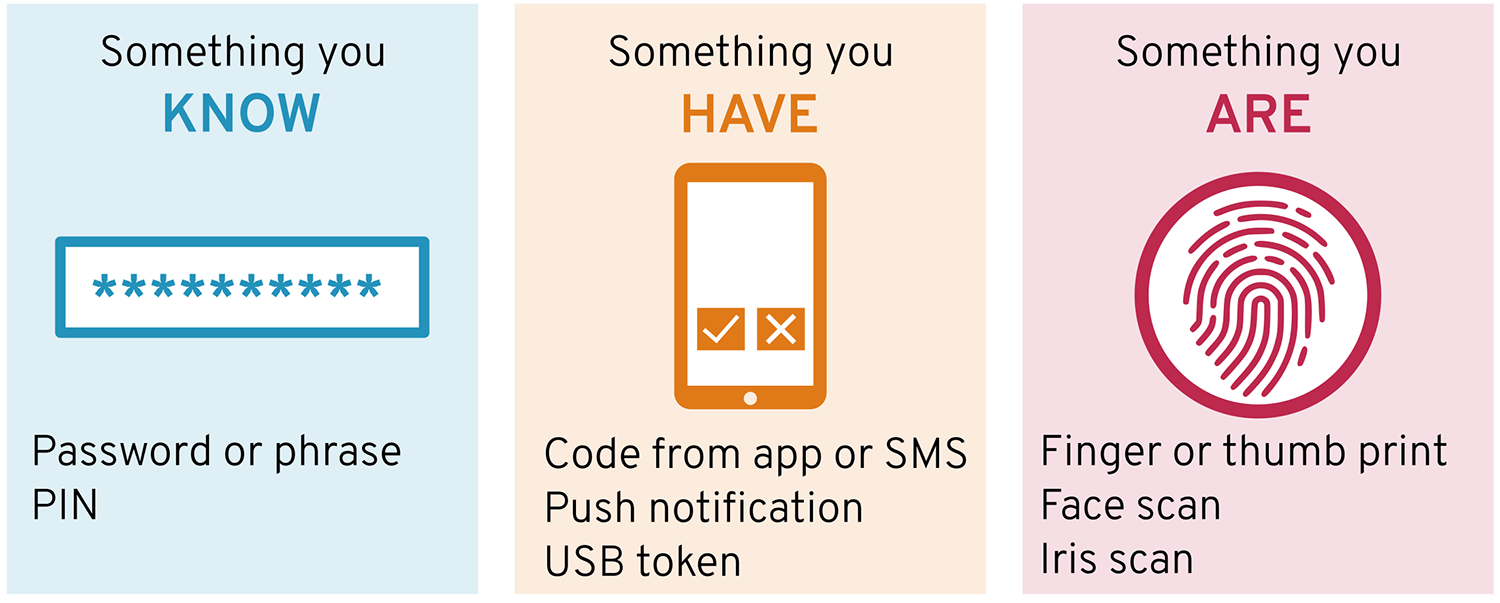
Security Considerations
Ultimately the strength of MFA resides in using one method of authentication that cannot be easily compromised. Further, when the use of MFA credentials is implemented, care must be taken to develop alerts on unusual access behavior that might indicate a compromise. Interception of MFA tokens and loss of hardware-based devices is a problem that needs to be contended with. To this extent, the US National Security Agency (NSA) noted that,
“Physical tokens and devices can always be lost, stolen, or duplicated. In some cases an adversary with physical access to the token could tamper with the token to change its behavior or use it to infect the host it interfaces with, though for many modern tokens this requires significant skill, investment, and risk. Consider using devices that include physical security mechanisms, such as tamper evidence or response.”
To that extent, the NSA advises,
“The NSA recommends using devices validated by the NIST Cryptographic Module Validation Program to the FIPS 140-2 standard. FIPS 140-2 level 1 validation is sufficient for most devices that will remain in a user’s possession and can be easily revoked and replaced if lost; devices validated to levels 3 or 4 provide tamper evidence or tamper responses (respectively) that can provide additional protection if the device is temporarily left unattended in high risk environments. Some MFA token systems depend on central authentication servers, certification authorities, and/or token issuance systems, and these servers should be very carefully protected and isolated.”
It also needs to be noted that biometric methods of authentication can be compromised. Several advanced threat actors have shown that fingerprint scanners on certain devices could be bypassed. That said, so-called “liveness tests”, designed to check that the person submitting biometric data is not spoofing, have improved considerably to the point that biometric MFA can be a vital technology in securing data.
Advancements in better security and technology have meant that attackers have looked to compromise individual MFA factors as compromising the entire system has proven beyond their current capabilities. Threat actors will look to find and gain persistence in IT infrastructure that acts as the meeting point of multiple MFA factors. The current best method to prevent a compromise with persistence as its goal is to continually educate both users and administrators as to the current threats to MFA being experienced. Not only do they need to be educated as to the possible threats but also on how to detect possible compromise.
Adaptive Access Control
When implementing MFA, organization leaders also need to look at integrating behavioral analytics. These can be used to determine high-risk behaviors. Once such behaviors have been determined, if an access request is determined to be of high risk, access can be denied. Types of data that can benefit the creation of adaptive access control are geolocation tags and as well as IP addresses associated with access requests. One of the advantages of such an approach is that access control can be bolstered by further requirements in the future to prevent future threats.

Ease of Use
Technology has enabled MFA authentication to be done in record time and with relative ease. Be it biometric protocols or an authenticator app, access to IT infrastructure can be granted securely without too much hassle on the part of the user. To that extent the NSA advises,
“Enterprises must consider the impact to users that MFA systems present and carefully coordinate the transition to gain users’ acceptance. Train administrators, help desk personnel, and users on the MFA system as well as the enrollment plan. Describe key usability improvements that MFA provides over password-only authentication. For example, the need to memorize and manage multiple complex passwords for multiple systems has always placed a burden on users; an MFA token with PIN authentication can help significantly reduce this burden. Anticipate potential issues with user access requirements and successful and failed authentication behavior. Provide a reliable and readily available issuance/re-issuance and compromise reporting infrastructure to minimize the pain associated with reporting and replacing lost or stolen tokens. Finally, train users and administrators on the benefits of and procedures for authentication factor revocation.”
Best Practice Checklist for MFA
The above considerations can prove vital when developing MFA policies that help keep the organization and its users secure. Some of the best implementations include several of the below features and we strongly suggest they be considered for your organization to supplement existing MFA factors. Without further delay, here is our MFA checklist:
- Focus on User Experience. Make implementation of MFA as easy as possible on the user base to help ensure ready adoption and improved workflows with a strong security backbone.
- Use Single Sign-On where possible. Single Sign-On (SSO) is a proven and tested authentication method that significantly improves the user experience. With SSO, users can log into multiple SaaS applications and services with just one set of credentials.
- Implement Adaptive Access Control. This was covered above but it has also been seen to improve the speed at which users can access the infrastructure they need.
- Implement MFA Across the Organisation. This can be difficult when the organization relies on older technologies not compliant with MFA. However, this is a goal that should be pursued and more technologies are being implemented to bring older technologies in line with MFA protocols.
- Awareness and Training. MFA is not a silver bullet that when implemented will stop any cyber attacks. Constant education and training of staff can prove the difference when defending an organization and its data.


