
In April this year, the clandestine hacking group, Shadow Brokers, released a series of exploits developed by the NSA. One of these exploits – dubbed EternalSynergy – has recently been modified by Thai analyst Worawit Wang (aka sleepya) in order to prove it can work against newer versions of the Windows Operating System – a full list of these is further below.
The original version of the exploit was known to be unstable and would often ‘crash a target’, the modified version stablises the exploit and, according to Wang, now has a “nearly 0%” chance of doing so.
Microsoft has registered the vulnerability as CVE-2017-0143.
Vulnerability Description
The vulnerability involves part of the SMB header information transaction where certain parameters like UID, PID, TID and otherInfo are part of the transaction. The parameter values store the Transaction ID in the MID field and some additional fields store the same ID in the FID field.
What this means is that any foreign SMB transaction parameters with a FID value that matches the original MID, are considered a legitimate transaction. This authentication flaw in the SMB transaction is the root of the EternalSynergy vulnerability.
Exploiting the vulnerability
In a practical scenario, the vulnerability can be leveraged by packet confusion of the address pointer for the SMB_COM_WRITE_ANDX and SMB_COM_TRANSACTION_SECONDARY transactions. This means the rouge SMB_COM_TRANSACTION_SECONDARY transaction – if it’s FID value matches SMB_COM_WRITE_ANDX MIB – can overflow the original transaction.
At this point, the start of the buffer will point to the rouge transaction memory location. The potential risk in this is that any sequence of malicious code can now be executed from that location.
It is this hijacking of the execution flow from the legitimate SMB transaction to the rouge transaction that enables the exploit to target more recent Windows versions.
To further understand the real-time exploitation, we performed a code analysis on the vulnerability as listed on Exploit-DB:-
https://www.exploit-db.com/exploits/42315
The first thing we noticed was that an authentication attack is the means by which system access is gained:
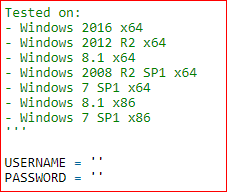
The username and password fields can be used when launching the attack from the Meterpeter Shell. The above graphic also shows the newer versions of Windows which the modified exploit can successfully target.
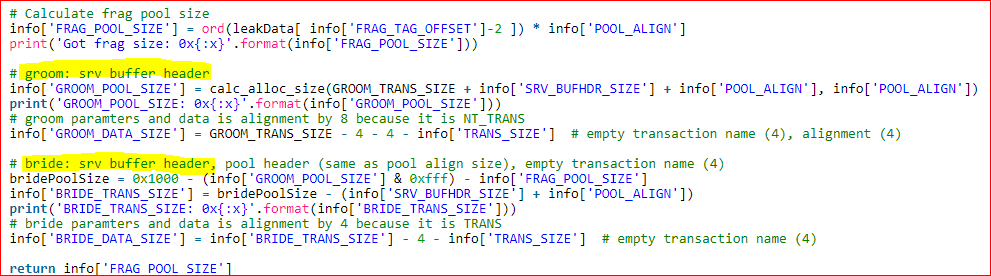
The original transaction and the leaked (rouge) transaction are defined by the ‘Groom Buffer’ and ‘Bride Buffer’ headers. Post Pool Size calculation, the Bride Buffer is considered as a leaked transaction and the location will point to the leaked transaction’s memory address.
Looking at the exploit definition, we see the ‘bug’ leveraged to access the named Pipes that is available along with target systems IP address.
The if/else function targets the Windows version based on the Operating system and exits if no suitable version is identified.
The successful attack exploitation on the target system is identified from the pawned file in the C:\ directory of the target system:
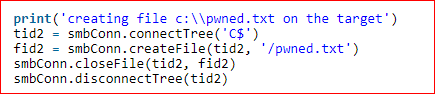
In this case, a text file “pwned.txt” is created.
The above steps are from the maturity standpoint of the exploit and a successful launch of the same from the MSF console with proper Pipe name, IP address and subsequent .dll file will do the cause for any attacker.
Conclusion
This updated version of the EternalSynergy exploit proves that it can be easily modified to target newer Windows versions – not just those that are out of support. As always, we recommend applying all updates and patches as soon as possible in order to close the vulnerabilities that enable this exploit to work.


