
Overview
As ransomware variants continue to send users into meltdown, it’s fitting that the latest variant to shake victims to their core has been dubbed ‘Nuclear’. This latest strain belongs to the BTCware ransomware family (which is itself an adaption of the cryptxxx family) and demands a bitcoin payment before user files are restored. Other BTCware variants include .aleta, .gryphon, .xfile and .master.
Delivery
One interesting feature of the BTCware family is its delivery method. Its authors favour hacking into networks via remote desktop services that employ weak passwords before dropping the ransomware. As the description suggests, there is no great level of skill involved in hacking these remote desktop services – the attackers literally guess the credentials, using the most common username and password combinations… Admin/admin anyone?
Infection
Static Analysis:
SHA 256: 63ab37b3051369013734341941fdf548ac17ec886d8402a5b749b374aea29af5
File type and size: PE32 executable and around 752 KB in size.
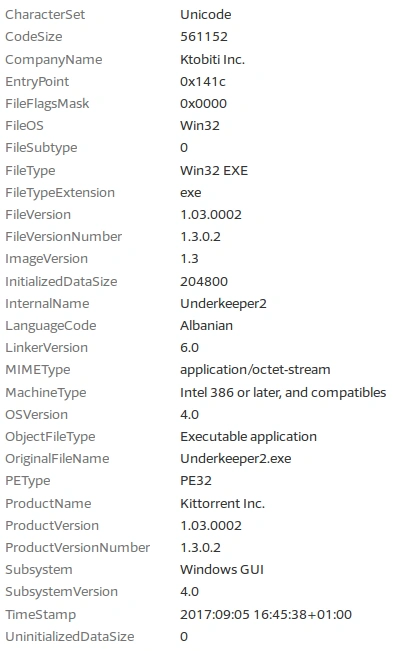
Figure 1 File metadata
The above snapshot shows the malware’s metadata, including the file type and creation timestamp. Nuclear’s original file name was ‘Underkeeper2.exe’ and its original product name was ‘kittorrent inc’. The timestamp shows us the file was created on September 5, 2017 and the language code suggests the ransomware is of Albanian origin.
The below details indicate the file was compiled using visual basic:

Figure 2 Compiler details of the sample

Figure 3 Visual Basic signature
Version details:
• VALUE “CompanyName”, “Ktobiti Inc.”
• VALUE “ProductName”, “Kittorrent Inc.”
• VALUE “FileVersion”, “1.03.0002”
• VALUE “ProductVersion”, “1.03.0002”
• VALUE “InternalName”, “Underkeeper2”
• VALUE “OriginalFilename”, “Underkeeper2.exe”
We ran the original file name (Underkeeper2.exe) and company name (Ktobiti Inc.) through the ‘isthisfile safe’ service and both were flagged as malicious:

Figure 4 Underkeeper2 as the search value for file name

Figure 5 kitobiti Inc as search value for company name
Based on the search results, we know all the files with the same version information have bad reputations.
File debugging:
Analysing malware compiled in Visual Basic is always a little more complicated than other samples. In this case, we used the OllyVB plugin:
Figure 6 OllyVB name windows
Using Ollyvb allowed us to uncover the dll function call details. Armed with this information, we can put breakpoints on all the dll function calls and proceed for full run:
Figure 7 Breakpoints on the dll function calls
Behaviour analysis:
When we executed the sample in our controlled environment, we observed the sample accessing volume shadow copy. Shadow copy is a Windows service which takes periodic backup snapshots. Generally, one method of circumventing ransomware infections is to revert to earlier shadow copies. In this case, the malware author is one step ahead as the Nuclear variant deletes volume snapshots:
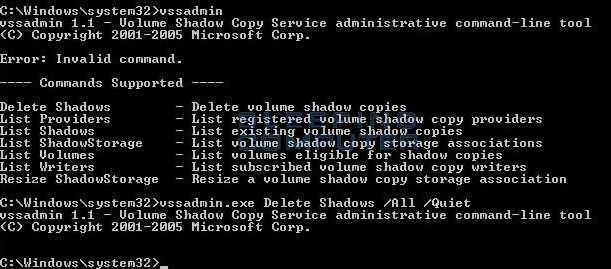
Figure 8 volume snapshot delete
The “vssadmin.exe Delete Shadows /All /Quiet” command is used by the ransomware to delete the shadow volume. Nuclear doesn’t stop here, it also disables the Windows error recovery on start up by using the boot configuration data edit tool (BCDEdit).

Figure 9 recoveryenabled Yes (Bcdedit)
The above snapshot shows the recovery enabled status as “Yes” but Nuclear runs the following command: “bcdedit.exe /set {default} recoveryenabled No”. This disables the error recovery on start up. After this change has been made, the following commands are run:
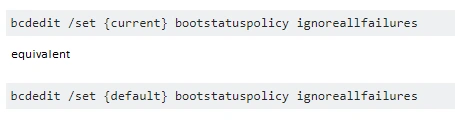
Figure 10 bootstatuspolicyignoreallfailures
We found two interesting strings in the memory:
• “%APPDATA%\HELP.hta”
• DECRYPTINFO
Changes we observed in run entry relate to the above memory strings – Help.hta is the physical location of file path and decryptinfo is the value in the run entry:
| HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN” “DECRYPTINFO” “%APPDATA%\HELP.hta” |
This helps the malware keep persistence.
The hta file is the ransom note, which is displayed after files are encrypted with the .nuclear extension, along with the email id.
Ransom note:

Figure 11 Nuclear Ransomware Note
Interestingly, the ransom note does not specify an amount to be paid – this amount is given to the victim after they contact the attackers. Payment can only be made in bitcoin and the attackers offer to decrypt three files (up to 1 MB) for free, as a good will gesture.
Threat Indicators
IOC details:
Email:
assistance@firemail.cc
2ndsupport@protonmail.com
File Extension added:
.[assistance@firemail.cc].nuclear
Mutex:
\Sessions\1\BaseNamedObjects\NUCLEAR
Conclusion
The criminals behind Nuclear exploit weak username and password combinations of remote desktop services. This modus operandi simply wouldn’t work if people didn’t keep these credentials set as the default – or generally weak – combinations.
Strong passwords – on everything requiring a password – are a crucial plank in a strong defensive posture.
Finally, keeping frequent backups will enable you to restore your files to a recent version in the event you do fall victim to ransomware.


