
Kill Switch Found?
Our research team has identified a potential “Kill Switch” for GoldenEye/Petya. That Kill Switch information follows.
GoldenEye/Petya uses Eternal Blue as an attack vector (CVE-2017-0143) spreading via SMB post-exploitation. It clears the windows event log using Wevtutil. The ransomware simply encrypts the Master Boot Record (MBR) of the machines. And by encrypting the MBR it doesn’t allow the Operating system to load. Running the peta sample , we can see that there might be logical Kill switch as well, where the Sample runs “rundl32.exe” process which further creates a file “perfc.dll” as shown below. And a manual file creation actually stops the sample from execution.
The malicious DLL gets stored into the memory:-


Writes a file “perfc” in C:\Windows directory, which is a copy of the DLL file
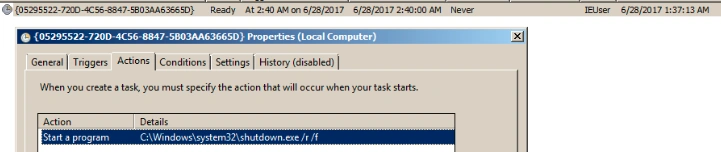
• Creates a schedule task for force restart
some malware file in SPAM emails(.xls,.rtf) has a PowerShell code to download and execute Petya payload,
– 84.200.16.242/myguy.xls

Further from the recent sample, Petya 2017 only wipes the first sectors of the disk and not actually encrypting each and every file.
Once Malware reboots (Using schedule task) victims computers and encrypts the hard drive’s master file table (MFT) and renders the master boot record (MBR) inoperable, restricting access to the full system by seizing information about file names, sizes, and location on the physical disk.
Indicator of Compromise
Domain Blocklist:-
hxxp://mischapuk6hyrn72[.]onion/
hxxp://petya3jxfp2f7g3i[.]onion/
hxxp://petya3sen7dyko2n[.]onion/
hxxp://mischa5xyix2mrhd[.]onion/MZ2MMJ
hxxp://mischapuk6hyrn72[.]onion/MZ2MMJ
hxxp://petya3jxfp2f7g3i[.]onion/MZ2MMJ
hxxp://petya3sen7dyko2n[.]onion/MZ2MMJ
hxxp://benkow[.]cc/71b6a493388e7d0b40c83ce903bc6b04.bin
COFFEINOFFICE[.]XYZ
hxxp://french-cooking[.]com/
IP address Blocklist:-
95.141.115.108
185.165.29.78
84.200.16.242
111.90.139.247
Dropped Files path :-
– %WINDIR%\dllhost[.]dat
– “%WINDIR%\system32\shutdown.exe /r /f” /ST 07:45″” [Scheduled task will be processed at specific time Interval]
– schtasks %ws/Create /SC once /TN “” /TR “%ws” /ST %02d:%02d
The ransomware attempts to encrypt files that corresponds to the following file extensions:
[.]3ds,[.]7z,[.]accdb,[.]ai,[.]asp,[.]aspx,[.]avhd,[.]back,[.]bak,[.]c,[.]cfg,[.]conf,[.]cpp,[.]cs,[.]ctl,[.]dbf,[.]disk,[.]djvu,[.]doc,[.]docx,[.]dwg,[.]eml,[.]fdb,[.]gz,[.]h,[.]hdd,[.]kdbx,[.]mail,[.]mdb,[.]msg,[.]nrg,[.]ora,[.]ost,[.]ova,[.]ovf,[.]pdf,[.]php,[.]pmf,[.]ppt,[.]pptx,[.]pst,[.]pvi,[.]py,[.]pyc,[.]rar,[.]rtf,[.]sln,[.]sql,[.]tar,[.]vbox,[.]vbs,[.]vcb,[.]vdi,[.]vfd,[.]vmc,[.]vmdk,[.]vmsd,[.]vmx,[.]vsdx,[.]vsv,[.]work,[.]xls,[.]xlsx,[.]xvd,[.]zip,[.]
SHA256 hashes
– 8143d7d370015ccebcdaafce3f399156ffdf045ac8bedcc67bdffb1507be0b58
– 027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745
– f8dbabdfa03068130c277ce49c60e35c029ff29d9e3c74c362521f3fb02670d5
– 41cb22109da26a6ff5464d6915db81c1c60f9e0808d8dbd63df1550b86372165
– 0a3706fd283a5c87340215ce05e0bdbc958d20d9ca415f6c08ec176f824fb3c0
– eccd88bfc2be71e0ee7926fa4bed4e72a2db864328f2351d301f67bfe19e26bc
Prevention Yara Rule for the Perimeter Protection
rule NotPetya_Ransomware_Jun17 {
meta:
description = “Detects new NotPetya Ransomware variant from June 2017”
date = “2017-06-27”
hash1 = “027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745”
strings:
$x1 = “Ooops, your important files are encrypted.” fullword wide
$x2 = “process call create \”C:\\Windows\\System32\\rundll32.exe \\\”C:\\Windows\\%s\\\” #1 ” fullword wide
$x3 = “-d C:\\Windows\\System32\\rundll32.exe \”C:\\Windows\\%s\”,#1 ” fullword wide
$x4 = “Send your Bitcoin wallet ID and personal installation key to e-mail ” fullword wide
$x5 = “fsutil usn deletejournal /D %c:” fullword wide
$x6 = “wevtutil cl Setup & wevtutil cl System” ascii
$s1 = “%s /node:\”%ws\” /user:\”%ws\” /password:\”%ws\” ” fullword wide
$s4 = “\\\\.\\pipe\\%ws” fullword wide
$s5 = “schtasks %ws/Create /SC once /TN \”\” /TR \”%ws\” /ST %02d:%02d” fullword wide
$s6 = “u%s \\\\%s -accepteula -s ” fullword wide
$s7 = “dllhost.dat” fullword wide
condition:
uint16(0) == 0x5a4d and filesize < 1000KB and ( 1 of ($x*) or 3 of them )
}
rule NotPetya_Rel_Malware {
meta:
description = “Detects NotPetya related malware – karo.exe”
hash1 = “e5c643f1d8ecc0fd739d0bbe4a1c6c7de2601d86ab0fff74fd89c40908654be5”
hash2 = “7f081859ae2b9b59f014669233473921f1cac755f6c6bbd5dcdd3fafbe710000”
hash3 = “3e896599851231d11c06ee3f5f9677436850d3e7d745530f0a46f712e37ce082”
strings:
$s1 = “PublicKeyToken=3e56350693f7355e” fullword wide
$s2 = “karo.exe” fullword wide
$s3 = “IWshShell3” fullword ascii
condition:
( uint16(0) == 0x5a4d and filesize < 2000KB and all of them )
}
rule NotPetya_Rel_Malware_3 {
meta:
description = “Detects NotPetya related malware – iosi.exe”
date = “2017-06-27”
hash1 = “2ddf8df2ee880dae54a7f52e4bf56f896bb3f873fb6b8fdb60cae4a3de16ff49”
strings:
$s1 = “PublicKeyToken=3e56350693f7355e” fullword wide
$s2 = “iosi.exe” fullword wide
$s3 = “WshExecStatus” fullword ascii
$s4 = “IsX64Process” fullword ascii
condition:
( uint16(0) == 0x5a4d and filesize < 2000KB and all of them )
CVE-2017-0147 https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2017-0147
Patch: MS17-010 https://technet.microsoft.com/en-us/library/security/MS17-010
………………………..XXXXXXXXXXXXXXXXXX…………………………………………………………………….


