
LMNTRIX Cyber Defence Center has been tracking a Russian group of malware mongers, selling their software from Deep and Dark Web forums. This group is known as “Predator The Thief”.
The group first appeared in early March 2019, developing and propagating a multiple malware strains since then – the most recent coming last week with an update to their data stealer malware PredatorThief v3.2.1. Given how frequent the updates are, we believe these are being made as soon as previous versions are detected.
The threat actors host multiple secret groups and forums on the Deep and Dark Web to sell their malware, and most members of the group appear to be Russian as the posts and advertisements are primarily in Russian Cyrillic.
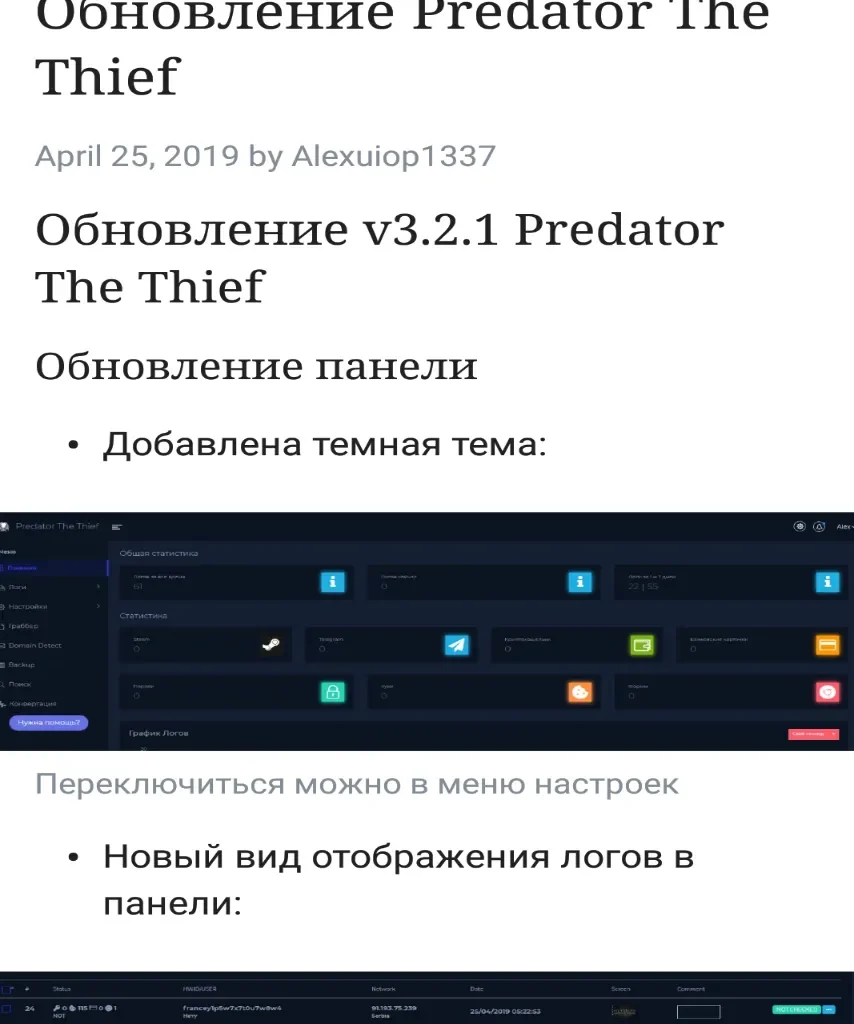
With each updated version, the threat actors work to increase functionality and usability of their malware. The most recent version, released on April 25 2019, includes a fully fledged UI for their customers to manage the malware from a single panel.
Since first seeing the group on March 1 2019, LMNTRIX Threat Intelligence has so far detected seven different variants of the malware – these are categorised under the malware family Trojan.PredatorThief.The MD5 hashes for each variant is listed in the image below:
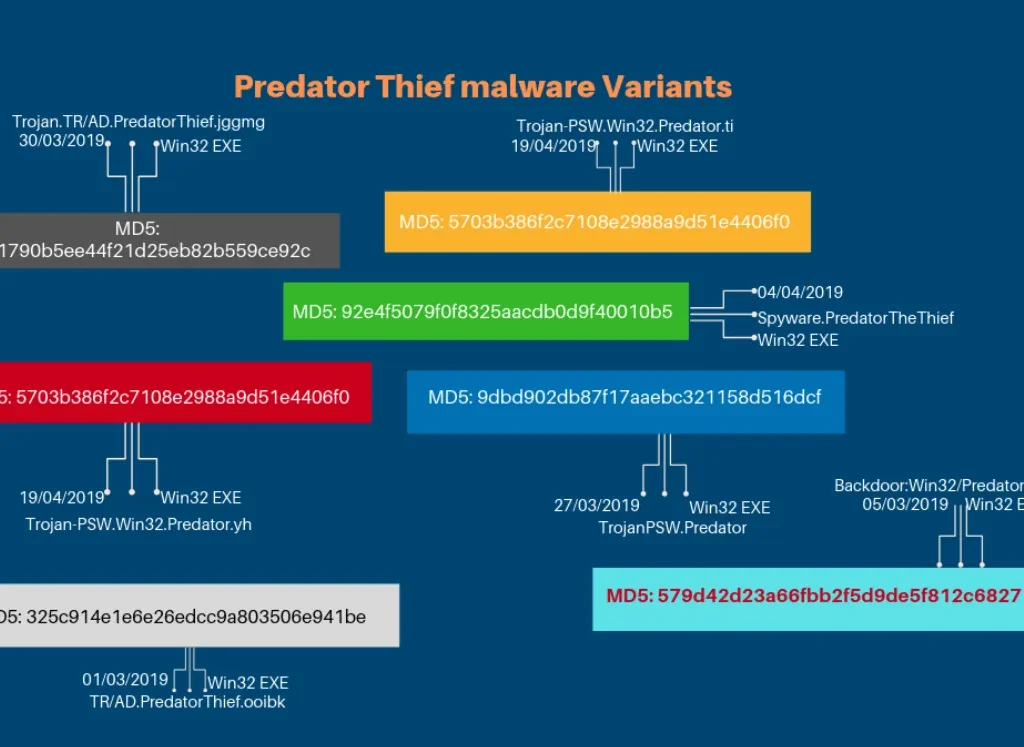
The samples shown above highlight the timeline of malware detection over the past two months. This shows how rapidly new variants are being released after detection – for example, after a version was discovered on March 1 a new variant was already in the wild within days and discovered on March 5.
Malware Analysis:
The File version properties, Resource Icon, and Dialog Boxes of the malware show some common characteristics, with each variant signed with verified signatures and signer status shows as “Valid”.
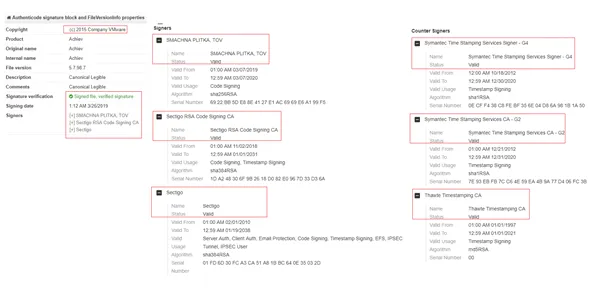
The version information shows Copyright as “LegalCopyright”, “(c) 2015 Company VMware”. This shows how the malware authors are using spoofed certificate details to evade detection.
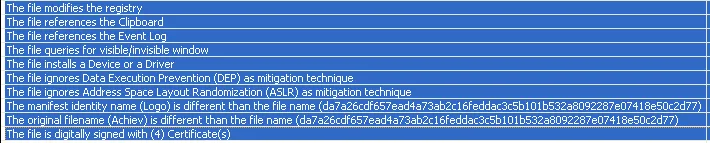
Looking into the code, it has references to clipboard, event log, installs device/driver and queries for visible/invisible windows. The malware can also modify the registry keys to gain persistence in the execution process. The below list shows the reference of fake certificates.
The malware includes multiple techniques to detect debuggers, process monitoring tools and virtual machines in order to evade detection. The PredatorThief trojan PE32 exe file modifies the executable and performs an unauthorised process injection to recently created process. The spawned process performs web query for DNS and HTTP POST request contacting the command and control server. The below process diagram shows the sequence of events performed by the malware.
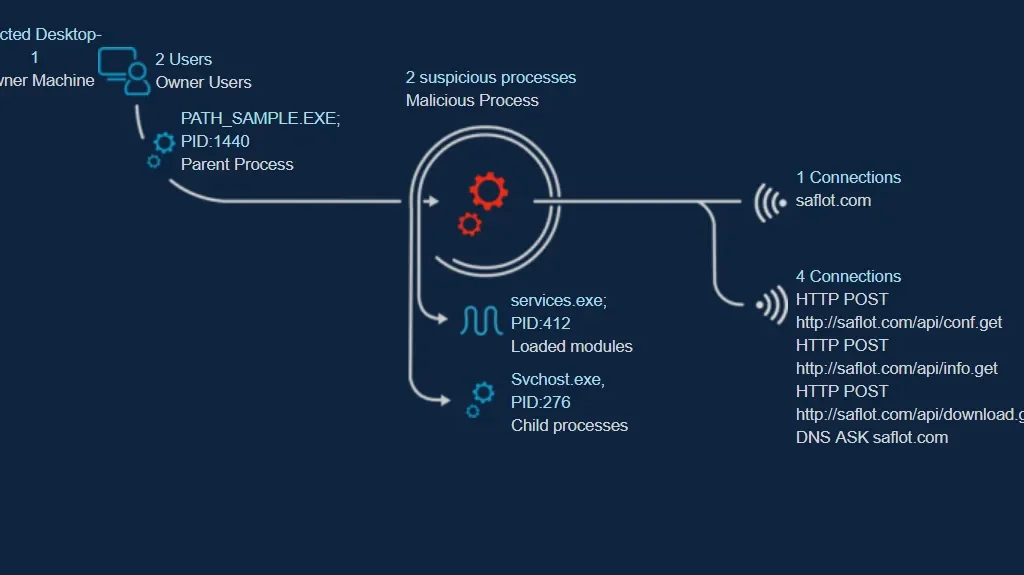
Further analysis shows the malware opens the clipboard and collects the clipboard data. If the GetClipboardData function succeeds, the return value is the handle to a clipboard object in the indicated format. The clipboard data is vital information for the attackers as they use it to achieve several malicious objectives. Additionally, the code has lstrlenA and TextOutA, which are used to determine the length of the specified characters and writes the characters at the specified location.

This malware has also inducted HTTP Connections to transfer the different credentials to the attacker’s server from the victims machine. Functions like WinHttpSetCredentials are being used to send authorisation credentials.
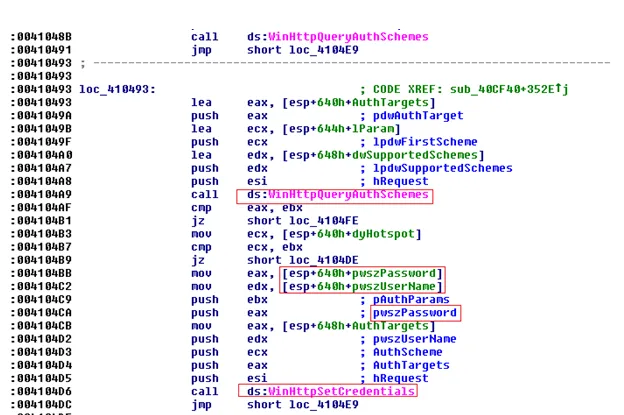
While performing HTTP requests, the malware has already spotted login URL and the authentication parameters like username, password in the function call – WinHttpSetCredentials.
Protection:
The “MITRE ATT&CK” matrix lists the different Tools, Tactics and Procedures (TTP) which the attackers use to achieve their objectives. Analyzing the TTP of the PredatorTheft malware variant, it follows the below attributes of the Attack matrix:
1. T1055: Process Injection: involves writing malicious code directly into the process (without a file on disk) then invoking execution with either additional code or by creating a remote thread.
2. T1115: Clipboard Data: Adversaries collect data stored in the Windows clipboard from users copying information within or between applications.
3. T1003: Credential Dumping: Credential dumping is the process of obtaining account login and password information, normally in the form of a hash or a clear text password, from the operating system and software. Credentials can then be used to perform Lateral Movement and access restricted information.
Alternatively, LMNTRIX’s Adaptative Threat Response platform provides complete endpoint security with detection techniques mapped to the “MITRE ATT&CK” framework. With advanced analytics, LMNTRIX platform brings light to threats that otherwise go undetected, along with detailed analysis to provide attack attribution. The LMNTRIX platform includes an inbuilt offline capability which uses machine learning models to classify malicious files and quickly isolates the location and determines the extent of the executable.
Indicators of compromise:
| Info | Value |
| Md5 | 5703b386f2c7108e2988a9d51e4406f0 |
| Md5 | 6421790b5ee44f21d25eb82b559ce92c |
| Md5 | 92e4f5079f0f8325aacdb0d9f40010b5 |
| Md5 | 5703b386f2c7108e2988a9d51e4406f0 |
| Md5 | 9dbd902db87f17aaebc321158d516dcf |
| Md5 | 325c914e1e6e26edcc9a803506e941be |
| Md5 | 579d42d23a66fbb2f5d9de5f812c6827 |
| URL | www[.]Saflot[.]com |
On 2019-04-30


