
Just over a week ago, the team behind Samba – a piece of software introduced in 1991 which enables Unix and Linux machines to interoperate with a variety of Windows networking features – released a patch for a newly discovered critical code execution flaw.
Before we go any further, if you’re currently running Samba and have file- and printer-sharing port 445 available on the Internet, shared files configured with write privileges, and your server paths for those files are either known or easily guessed, then you should visit the Samba site and download the patch for CVE-2017-7494 now.
If the three above conditions are present, the flaw (introduced in the 2010 release of Samba 3.5.0 and present in all versions since) allows attackers to upload code to the server and execute it.
Basically, malicious code targeting this vulnerability can replicate itself, spreading through a network like the chills running down the spine of anyone reading this post whose network met those conditions. In cyber parlance, we say it’s a ‘wormable’ vulnerability.
Current estimates suggest there are 477,000 Samba-enabled computers exposing port 445 to the world. Researchers at Rapid 7, said they found that 110,000 of these were running vulnerable versions of Samba.
Given those relatively small numbers, you might be wondering why this flaw is generating so much noise. The answer to your question is because, functionality-wise, it is very similar to the SMB vulnerability exploited in the recent WannaCry campaign.
Now, let’s take a closer look at the exploit code so we can better understand how it works. We ran a deep-dive analysis on the code as listed in the vulnerability database exploit-db.
The entire sequence of the code execution exploit, “is_known_pipename()”, can be seen below:
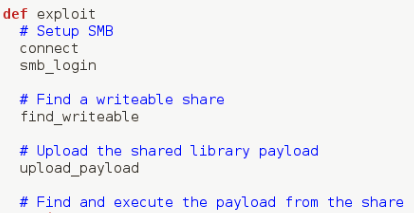
As you can see, the first step is effectively an authentication process. The first thing we saw in our analysis was that the code targets the SMB module, in order to find the directory to use within the writeable SMB share.
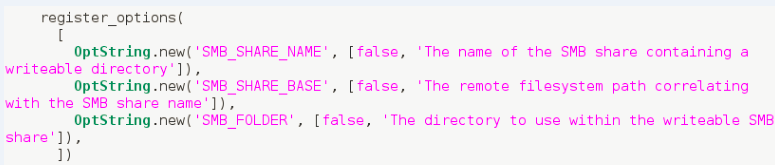
The above module also targets SMB_SHARE_BASE and SMB_SHARE_NAME, exploiting the remote file system path correlating with the SMB share name of the writeable directory.
In the second phase of the exploit, it defines a function to verify the writeable directory.
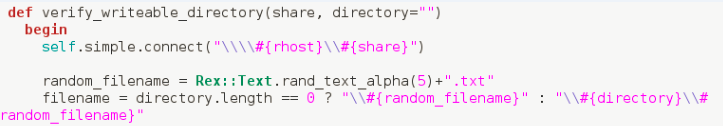
Once it finds the writable share directory, it loads the shared library payload onto the server and executes it, compromising every vulnerable machine connected to it.
And that’s all folks. Elegantly – and potentially catastrophically – simple.
Even after downloading the patch, we recommend you keep an eye on port 445 for the next few days, just in case there’s any unusual traffic.


