
When it comes to ‘scatter-gun’ distribution methods, a ransomware strain discovered late last year is taking spray-and-pray to new heights. The latest variant of Scarab ransomware was discovered last November and was clocked using the Necurs botnet to send 12.5 million spam emails in just six hours – more than 2 million spam emails per hour!
Its primary targets were .com and .co.uk top-level domains, but domains in Australia, France, Germany and New Zealand were also targeted. Despite its discovery last year, we witnessed the strain still being used to target victims on January 18, 2018.
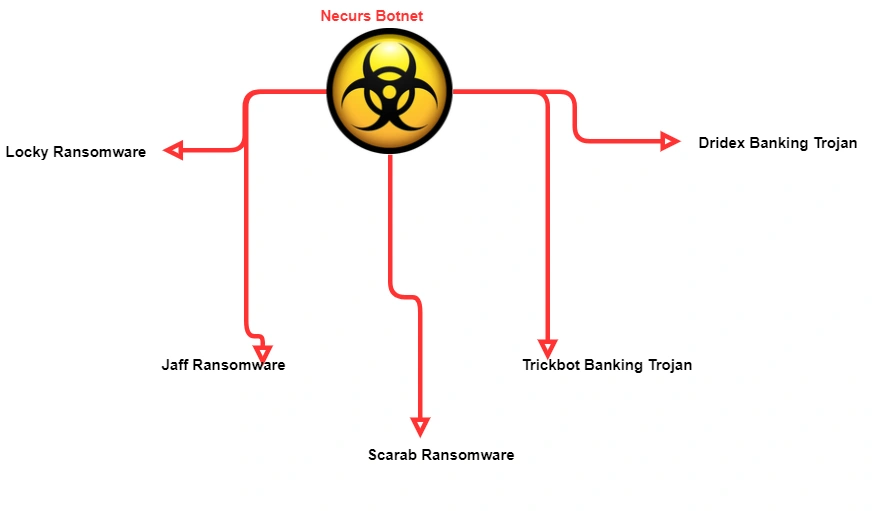
Necurs is one of the world’s largest botnets with between 5 and 6 million infected hosts online monthly. In the past, it has been used to distribute other ransomware strains, Locky being the most notable. Below is a list of malware campaigns Necurs has distributed:
Scarab’s spam email contains a malicious VBScript downloader (md5: c3d641dc9dd08d592d66f8091ef76de4), compressed with 7zip which pulls down the final payload. The ransomware then drops the file: %Application Data%\sevnz.exe
After this initial step, Scarab then proceeds to:
• Create a registry entry as an autostart mechanism in order to maintain persistence
• Scan all drives to check file extensions
• Read and encrypt all files using AES encryption with the .scarab extension
• Delete volume shadow copies, system backups and remove Windows recovery mode
Once installed and executed on the victim’s computer, Scarab connects to a website that provides the attacker with the victim’s IP address and other machine information so tabs can be kept on the victim’s machine.
Once encryption is complete, the ransomware drops a ransom note with the filename “IF YOU WANT TO GET ALL YOUR FILES BACK, PLEASE READ THIS.TXT” within each affected directory.
File details
| File type | Portable executable (.exe) file |
| Md5 hash | 9a02862ac95345359dfc3dcc93e3c10e |
Static Analysis
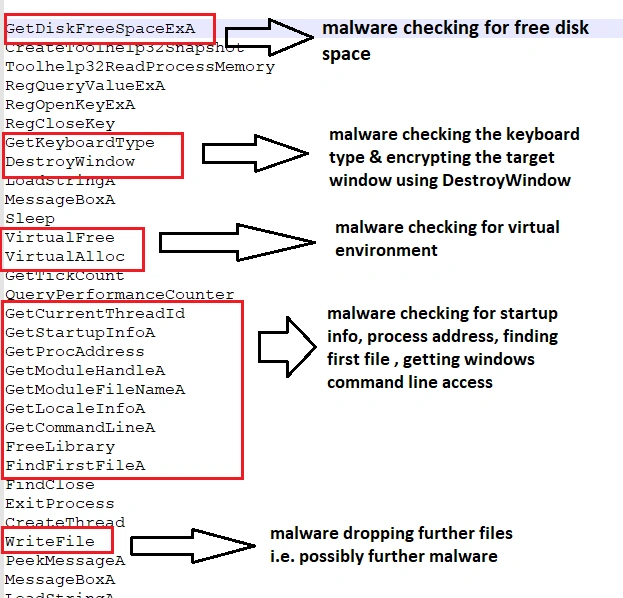
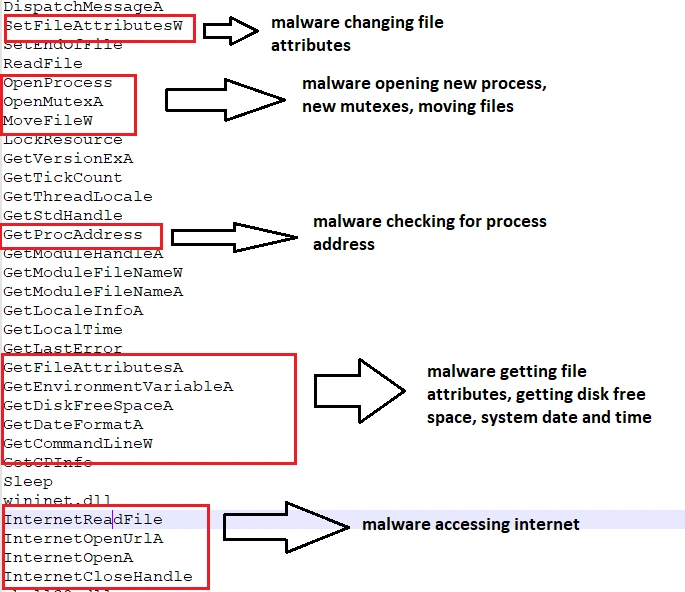
Static analysis uncovered a number of attributes that give away the sample’s malicious nature, including checks for free disk space, virtual environment detection, startup process checks, windows command line access, and attempting to connect to the internet:
Dynamic analysis
After executing the sample in a dedicated virtual environment, we were able to follow Scarab’s infection process step-by-step. The chain outlined below gives a high-level description of the processes initiated during infection:
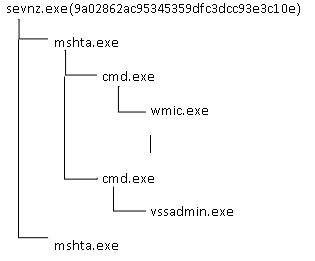
When we executed the sample “sevnz.exe”, it initiates “mshta.exe” which copies the file “sevnz.exe” to the location “%Application Data%\sevnz.exe”.
Next, “cmd.exe” is initiated which launches “wmic.exe” – the latter of which deletes system backups.
A second instance of “cmd.exe” also starts up with the child process “vssadmin.exe” – this is used to delete the system’s volume shadow copies.

After all these processes have been executed, sevnz.exe and mshta.exe continue running and remain persistent.
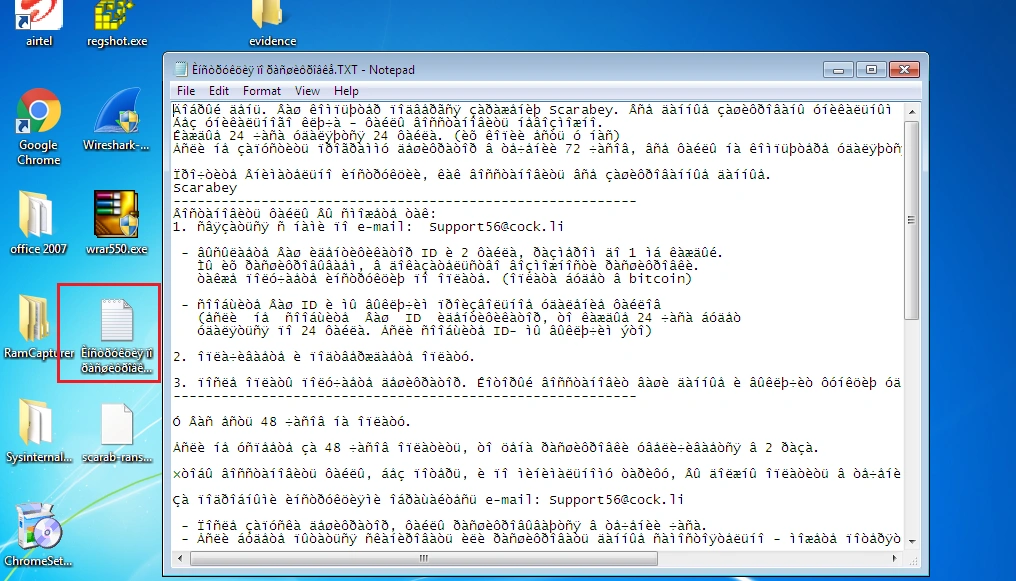
Ultimately, all data present in the victim machine is encrypted with the .scarab extension. Below is the ransom note as seen by the victim (the version we uncovered appears to be in an unsupported Cyrillic script):
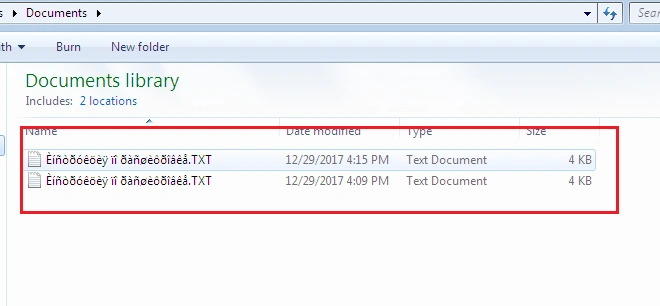
The text file containing the ransom message is also dropped in various other locations:
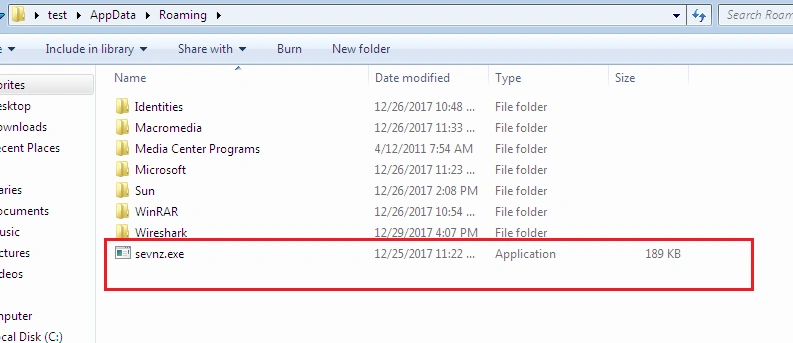
Sevnz.exe is also replicated into the following location which ensures it remains running across system reboots, encrypting data continuously. This feature means we weren’t able to capture malware artifacts such as pcap, further files/malware dropped, etc.
Below is the registry entry created at autostart:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnceuSjBVNE = “%Application Data%\sevnz.exe
Indicators of compromise
VBScript Downloader: c3d641dc9dd08d592d66f8091ef76de4
Malware sample analyzed: 9a02862ac95345359dfc3dcc93e3c10e
Mitigation
As with most ransomware strains, Scarab relies on the victim opening a weaponized attachment. Exercise caution when receiving any emails from unknown senders and do not open attachments or follow links without first verifying the email’s source.
It is also important to routinely back up important files to external storage devices to ensure you’re able to restore your files from a saved version in the event you fall victim to ransomware.


