
Despite the collective efforts of Europol, Intel, Kasperksy, and the Dutch cybercrime unit to eradicate the Shade ransomware, the strain has returned and its authors are now mocking the authorities who tried to bring it down.
Last year’s attempted takedown was performed under the banner of the No More Ransom initiative, whose aim is to attack ransomware control systems and publish free decryption keys.
While initially successfully, Shade has returned and added the extension “.no_more_ransom” (among others) to encrypted files – a clear swipe at last year’s venture.
LMNTRIX Labs discovered the latest sample earlier this month. This new variant has been predominately targeting users in the UK, France, Germany, Italy, Ukraine, and Russia.
Overview
Shade, aka Troldesh, belongs to a family of ransomware whose primary attack vectors are either malicious spam or exploit kits. Exploit kit attacks are particularly damaging as the victim does not necessarily have to open any file for the infection to occur – a single visit to any infected website is enough to initiate the infection process.
In its more mundane form, Shade spreads via emails containing malicious links which download a zipped JavaScript (JS) file or a Word document. When the JavaScript file is executed, it installs the ransomware.
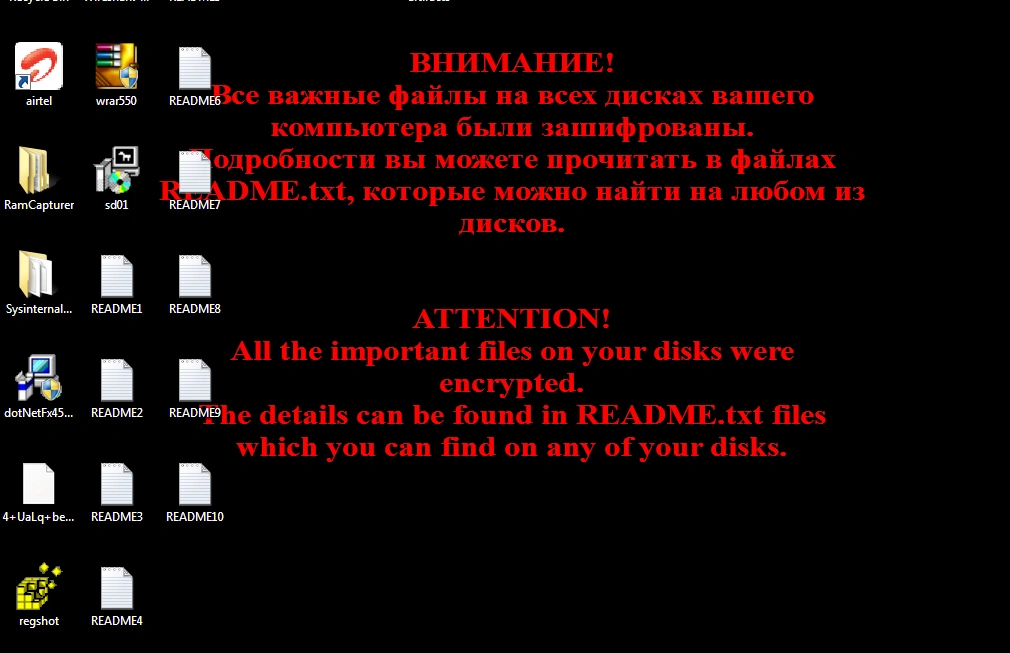
After successful infection, Shade encrypts most files stored on the infected machine, changes the desktop background and creates a .txt file which includes the ransom demand and directions on how to pay.
The latest version adds the .crypted000007, .no_more_ransom, .better_call_saul, .breaking bad, .heisenberg, .windows10, .7h9r, .xtbl, .ytbl or .da_vinci_code extensions to encrypted files.
Shade also connects with multiple Command and Control servers in order to receive configuration data and other information about the victim’s computer.
File Details
| File Type | Portable Executable (PE) File |
| Md5 hash | 15ebea98889b4d50c8db1c3b9d09b716 |
Static Analysis
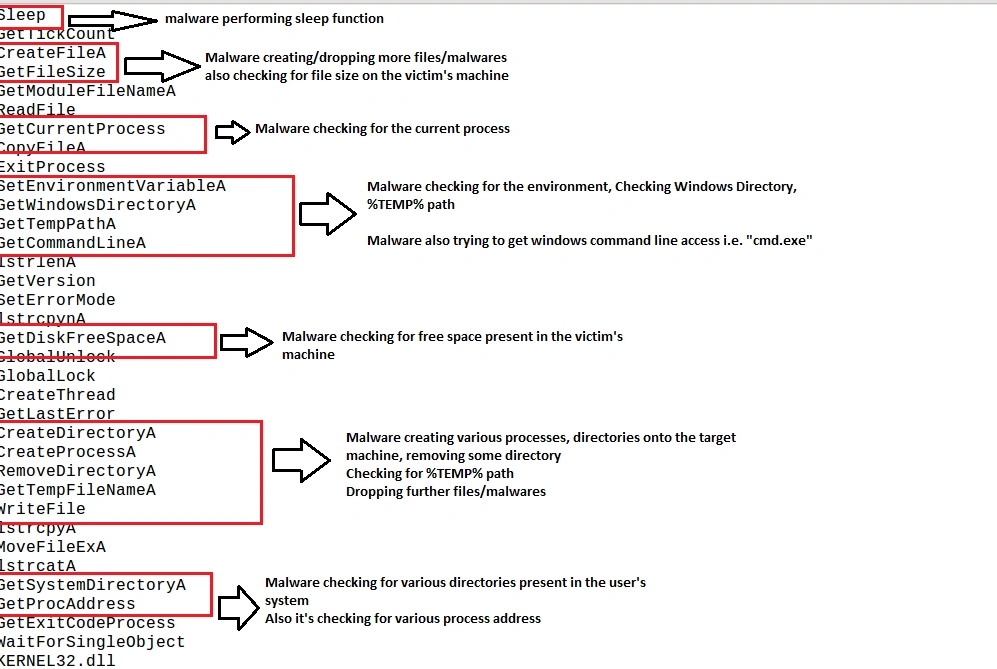
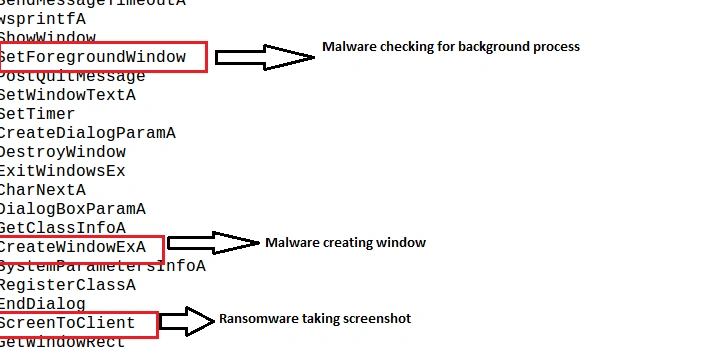
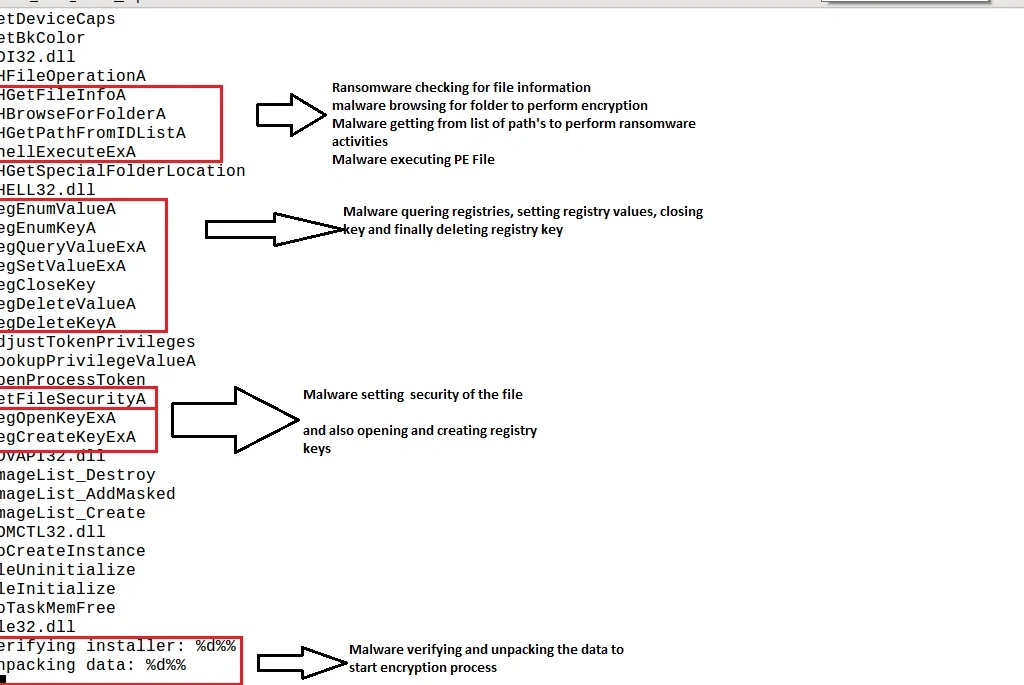
Once executed, Shade’s functionality includes:
• Creating registries
• Deleting files
• Dropping further malware
• Gaining command line (cmd.exe) access
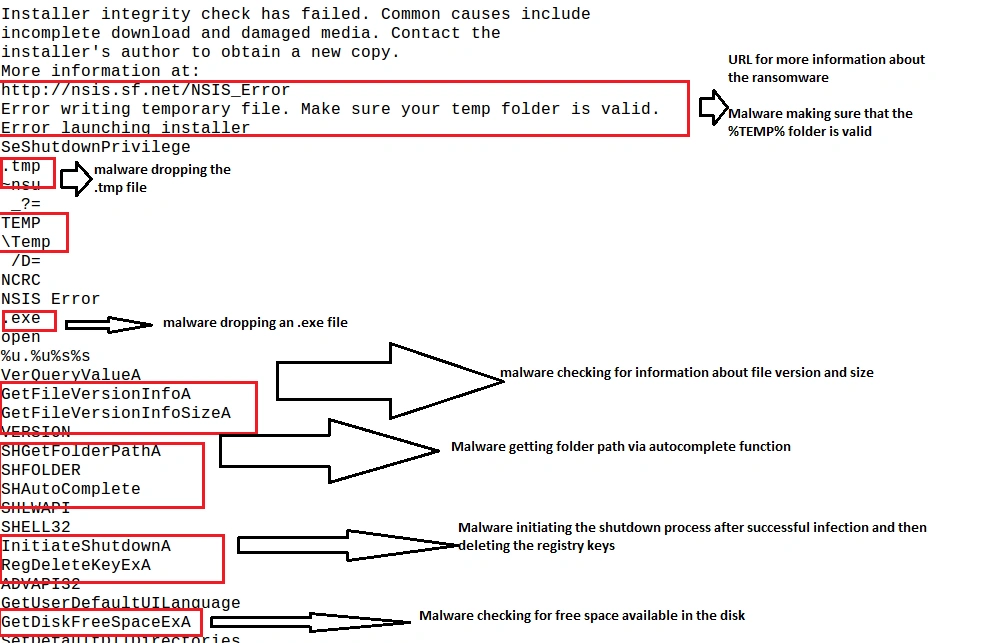
• Confirming file version and size before encrypting
• Shutting down the computer after successful infection
Full functionality is illustrated below:


Dynamic Analysis
LMNTRIX researchers executed Shade in a dedicated virtual environment in order to analyse its behavior in terms of processes being created, files dropped/deleted, registry values added/deleted, and network communications (Command and Control servers involved), etc.
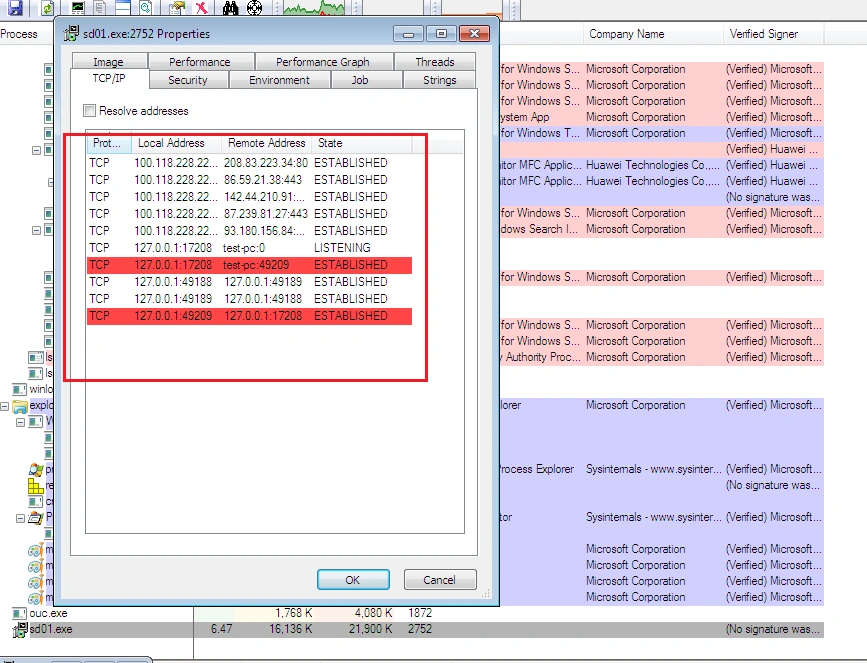
After execution, Shade (or sd01.exe) starts another child process with the same name, which disappears after some time:
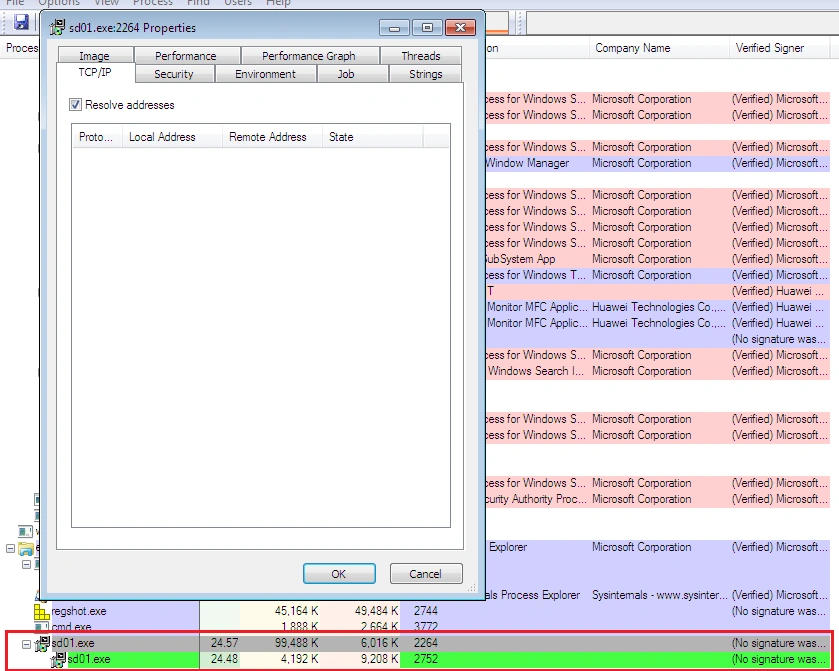
The initial process then contacts the following IP addresses:
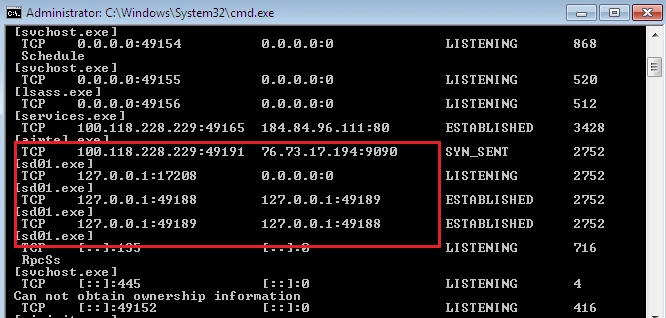
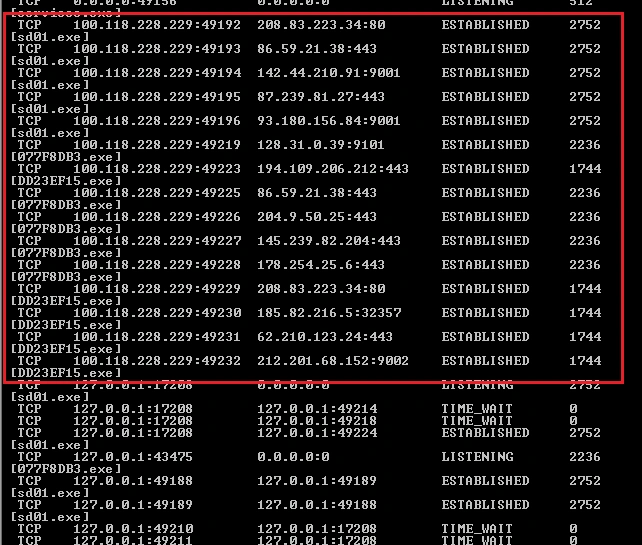
As the infection continues, the number of CnC servers contacted quickly increases. The multiple CnC callbacks and malware downloads indicates the infected machine is also conscripted to act as part of Shade’s botnet network. This could also be seen as a further slight at the authorities behind last year’s take down effort, as the latest variant’s expansive CnC infrastructure would be much harder to eradicate:
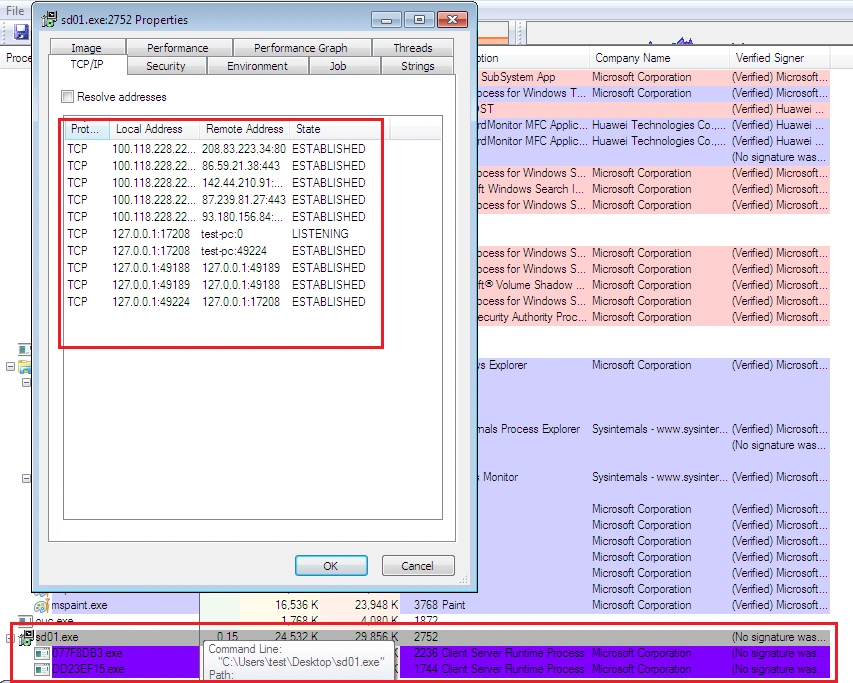
Next, more executable processes were initiated…
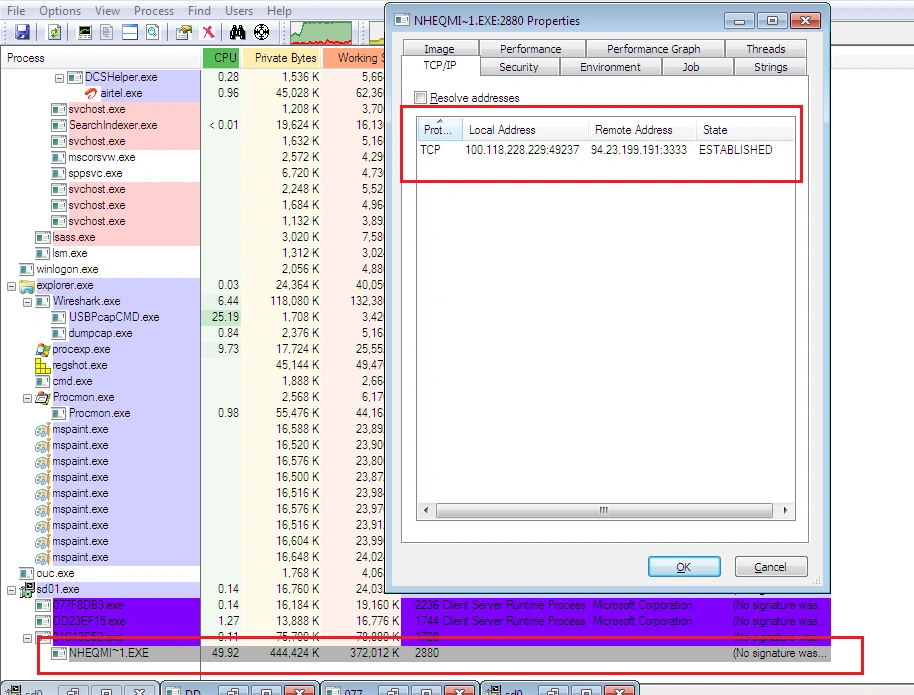
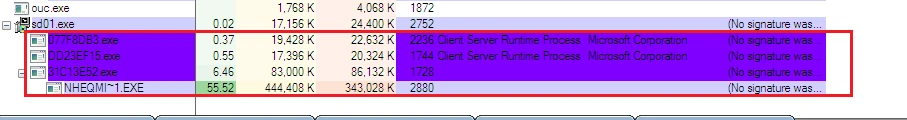
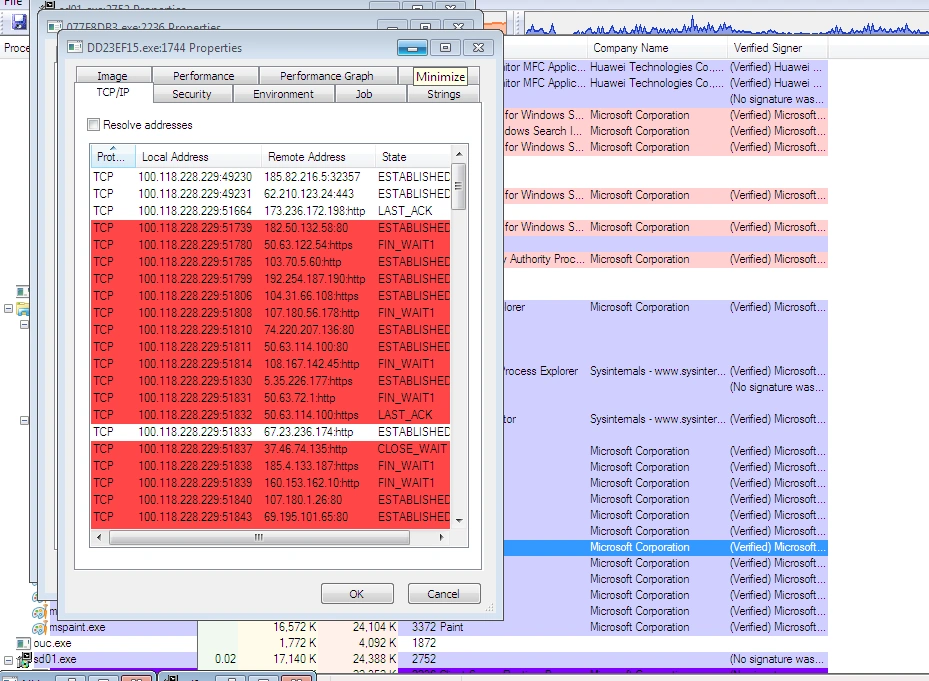
… which lead to even more CnC callbacks:
Finally, the user’s files are encrypted and the victim’s desktop is changed to display the ransom note:
Memory Analysis
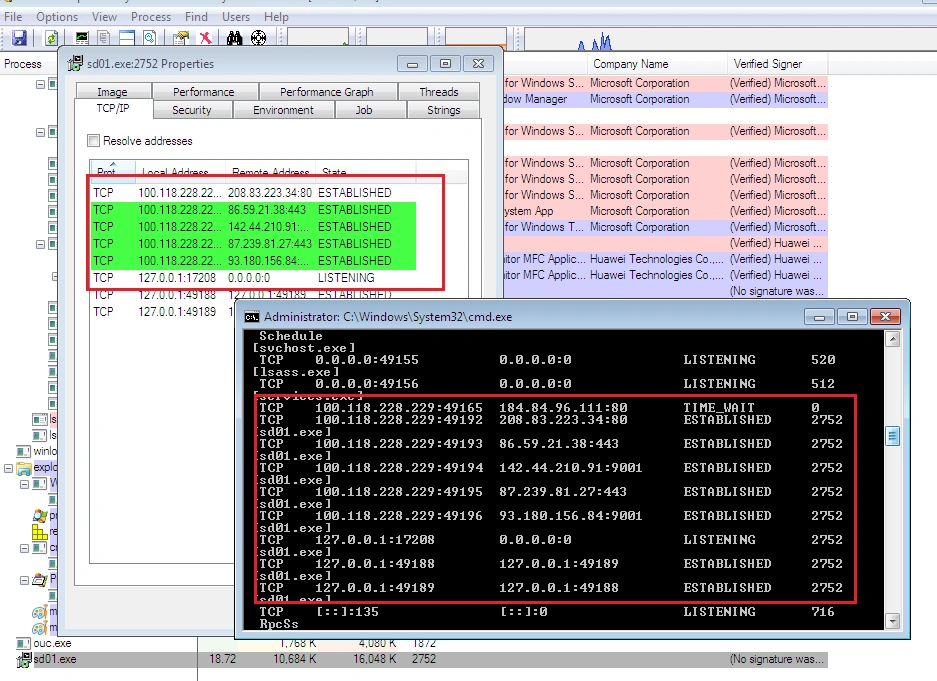
Next, we took an image of the RAM for further investigation and found the main executable process remained persistent, along with multiple child processes which kicked in after the initial executable was launched:

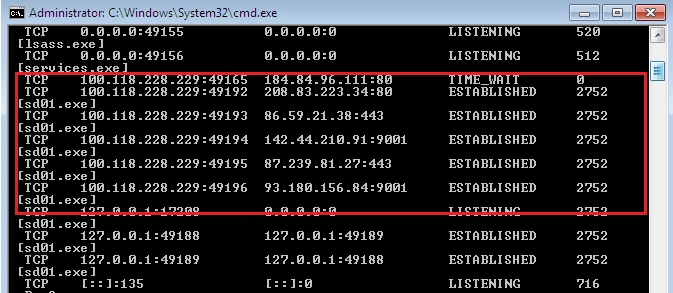
We were also able to see all the active connections Shade called out to, as well as the number of instances of the executable file:
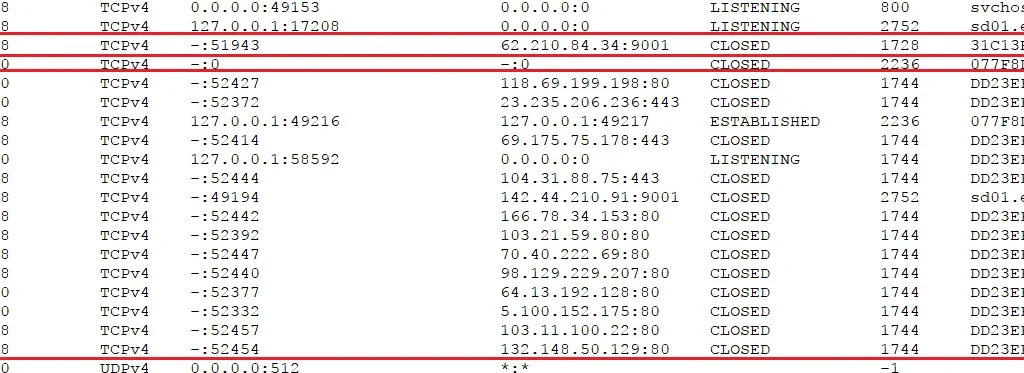
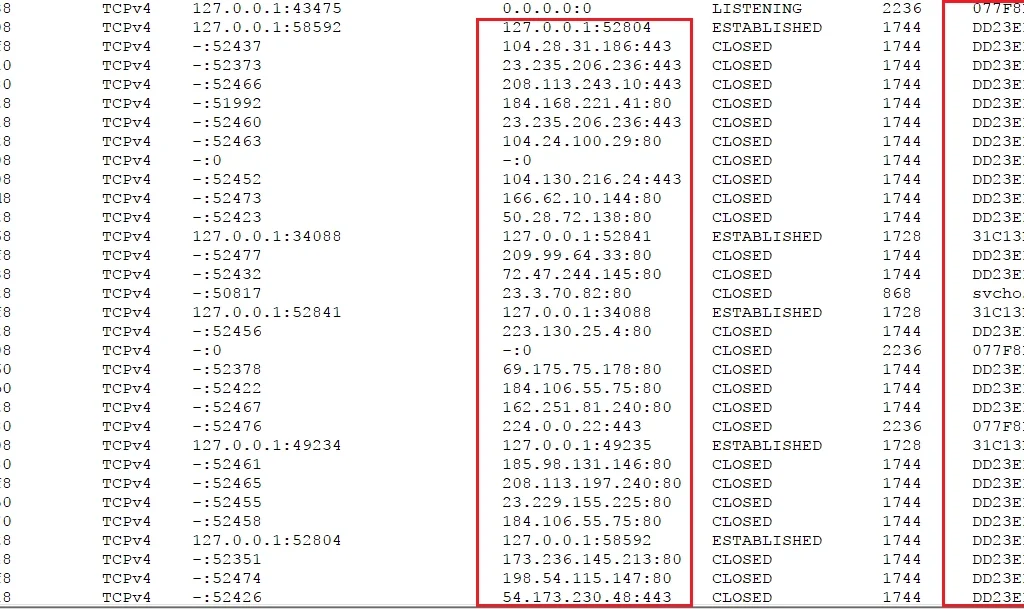
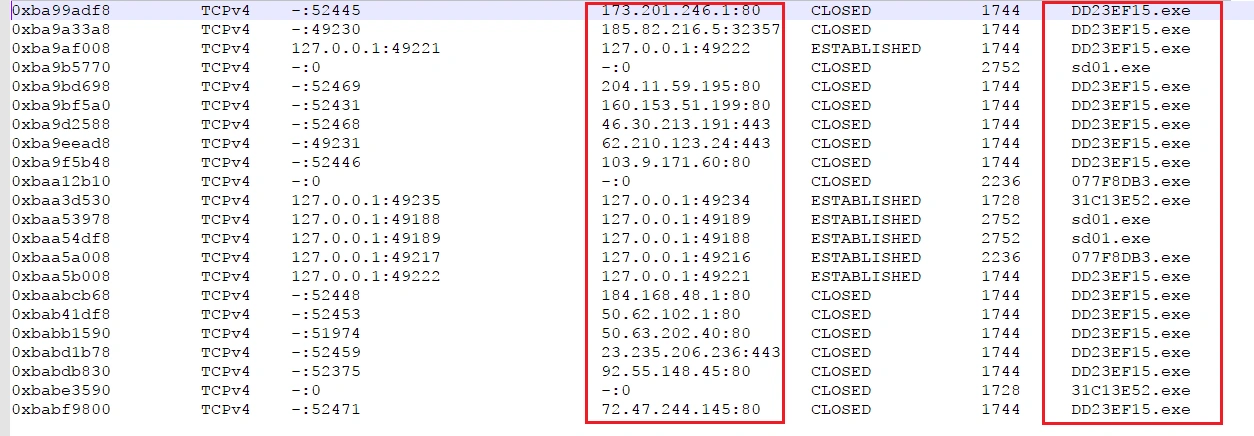
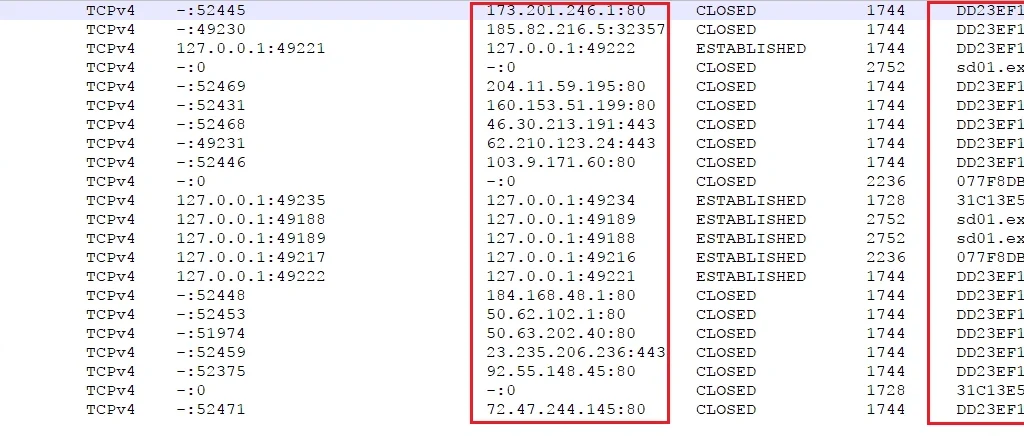
Command and Control
Below are the IP addresses involved during Shade’s infection cycle – there were 19 in total:
208.83.223.34
86.59.21.38
142.44.210.91
87.239.81.27
93.180.156.84
128.31.0.39
194.109.206.212
86.59.21.38
204.9.50.25
145.239.82.204
178.254.25.6
185.82.216.5
62.210.123.24
212.201.68.152
94.23.199.191
198.12.145.239
209.99.40.223
67.23.244.66
208.91.198.231
MD5 hash of the file analyzed: 15ebea98889b4d50c8db1c3b9d09b716
Dropped files
• C:\Users\test\AppData\Local\<user-name>\077F8DB3.exe
o md5: c1182260e1ba1f930e591a98e75552d9
• C:\Users\test\AppData\Local\<user-name>\31C13E52.exe
o md5: d668221d749214aac4e04d3daae07f7f
• C:\Users\test\AppData\Local\<user-name>\DD23EF15.exe
o md5: 8fbe9a961300fb62df587ed708160655
• C:\Users\test\AppData\Local\<user-name>\FE87884C.exe
o md5: 85d881193d41b4fcb0a27b6e2243a0dc
Protection Measures
Given the additional extensions added to encrypted files, last year’s nomoreransom.org decryption key may no longer decrypt files scrambled by Shade. Below are general cyber hygiene tips to minimize the chances of any infection, or enable a quick recovery in the event you do fall victim to ransomware:
• Keep frequent file back-ups on an external memory device or cloud-based storage.
• Keep security programs updated.
• Avoid visiting websites considered unsafe, particularly those with pirated or illegal content.
• Use a reliable anti-spam filter to block spam emails with malicious file attachments from ever entering your inbox.


