
Overview
While most of the malware campaigns we’ve covered rely on ‘spray-and-pray’ phishing campaigns to exploit known vulnerabilities, some attackers prefer the human touch – social engineering. At a high level, this involves manipulating a victim’s behaivour so they take a certain course of action or divulge a particular piece of information.
One such campaign involves the SpyBanker downloader. This is a banking trojan which steals personal data like computer name, OS installed, antivirus, and banking details then aims to download further malware on the victim’s device.
Delivery
In past SpyBanker campaigns, such as a particularly successful 2015 foray into Brazil, the downloader spread through social media platforms, offering people coupons or other free products if they clicked on a bit[.]ly URL. It should come as no surprise that instead of free stuff, the other side of these URLs offered only the SpyBanker payload. This reliance on exploiting human behaivour means the attackers didn’t need to rely on specific system vulnerabilities – once SpyBanker Downloader is on a victim’s computer, the hackers can just about do as they please.
File Details
| File Name | doc_boleto_9876245138.exe |
| File Type | PE (Portable Executable) file |
| MD5 hash | ac33bb9b18a9980e8e7a5e275a98ba42 |
Static Analysis
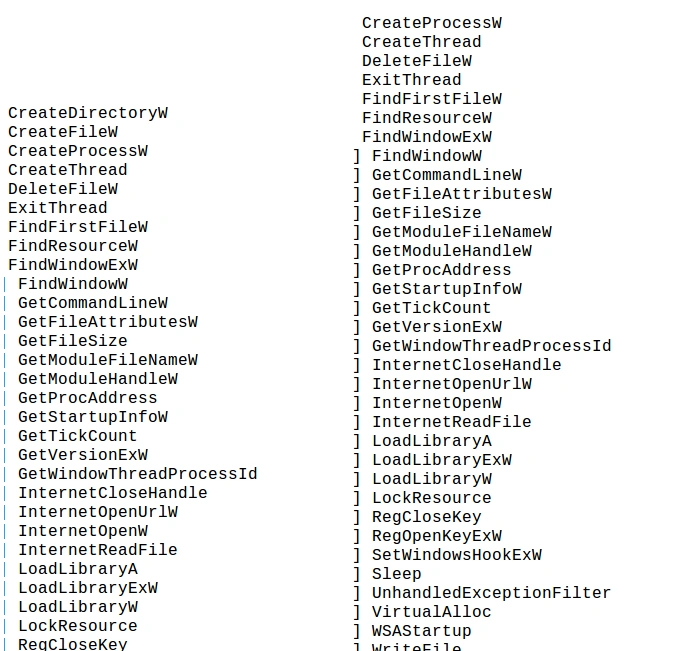
SpyBanker has the ability to get command line access using “GetCommandLineW”, check all file attributes
(permissions surrounding read, write, and execute) using “GetFilesAttributesW”, check file size using “GetFileSize”, and obtain startup information using “GetStartupInfoW”.
Static analysis also uncovered the malware’s ability to access the internet using “InternetOpenUrlW”, “InternetOpenW”, and “InternetReadFile”, its file dropping properties using “WriteFile”, and its ability to scan the target system for virtual machines using “virtualAlloc”.
ts full attributes are shown below:

Dynamic Analysis
Upon execution, SpyBanker Downloader establishes a connection with the IP address “138.197.179.85:80” – as shown below:
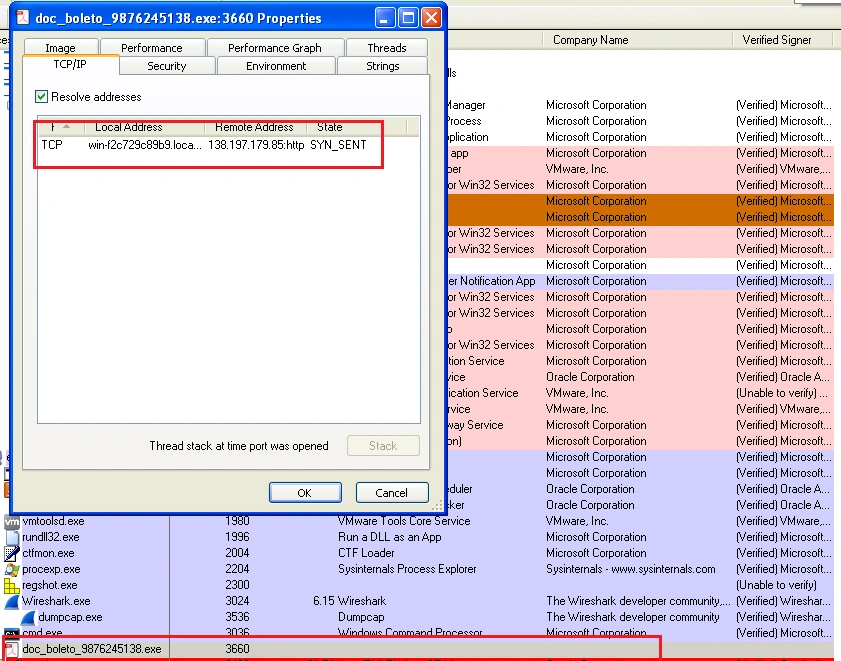
This IP is known to host malware content:

When the above IP is contacted, another file (“01.zip”) is dropped onto the system. In this instance, the malware is a variant of the Zusy banking trojan.
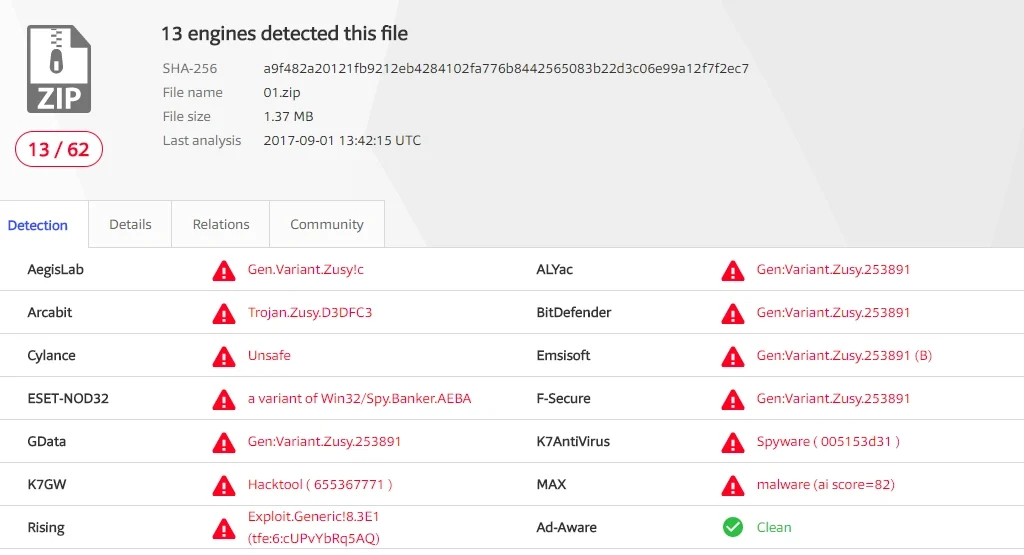
The zip file is installed in the following location: C:\Documents and Settings\Administrator\Application Data\rAmyK16tYN\01.zip
This sample made the following registry entries:
HKU\S-1-5-21-1614895754-1767777339-1801674531-500\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU\f: “%appdata%\1”
HKU\S-1-5-21-1614895754-1767777339-1801674531-500\Software\Microsoft\Windows\ShellNoRoam\MUICache\C:\Documents and Settings\Administrator\Desktop\doc_boleto_9876245138.exe: “doc_boleto_9876245138”
HKU\S-1-5-21-1614895754-1767777339-1801674531-500\Software\Microsoft\Windows\ShellNoRoam\MUICache\@shell32.dll,-21765: “Application Data”
Indicators of Compromise (IOCs)
In this SpyBanker sample, the IP address “138.197.179.85:80” was responsible for downloading the actual spyware, indicating the location of its Command and Control server.
Other indicators include:
| File Name | 01.zip |
| MD5 hash | 7f59a29694ab2e718fe2b65cf6ce9ada |
Conclusion
Inboxes aren’t the only avenue through which attackers will try to infect you. SpyBanker downloader most frequently spreads via social media posts offering either free stuff or vouchers. Once the downloader is installed on the device, the attacker is free to do as they please. Because this relies on the victim installing it on their computer, even if you’re completely patched you’ve just handed over total access to your computer.


