
Despite its cute name, ‘Pony’ is anything but. Bucking the recent ransomware trend, Pony is a form of credential stealing malware which is designed to pilfer log in credentials and is typically spread via spam email campaigns.
It has been implicated in the massive Equifax data breach, which saw the personal details of more than 145 million people stolen, and was particularly popular after its release in 2013 where it was used to steal $200,000 in bitcoin and 700,000 log in credentials.
During a recent analysis of a Pony sample, we observed a call back which we’ll unpack in today’s post.
Static properties of the sample
MD5: C13C6AB0CC0AD7E045259E16ED768683
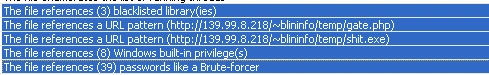
Figure 1 Malicious Indicators of the malware
After detecting the indicators and static properties of the sample, we checked for artefacts like libraries, imports and strings:
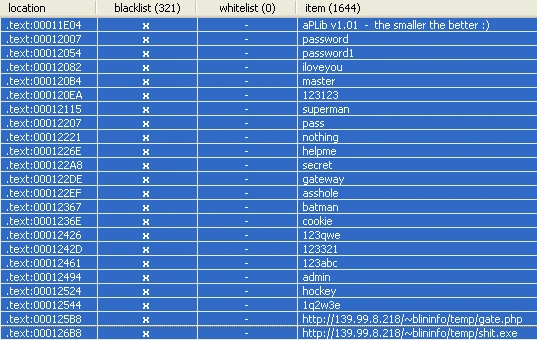
Figure 2 Interesting strings
We discovered what appears to be usernames, passwords and Pony call back URLS. Further analysis discovered even more passwords in the strings:
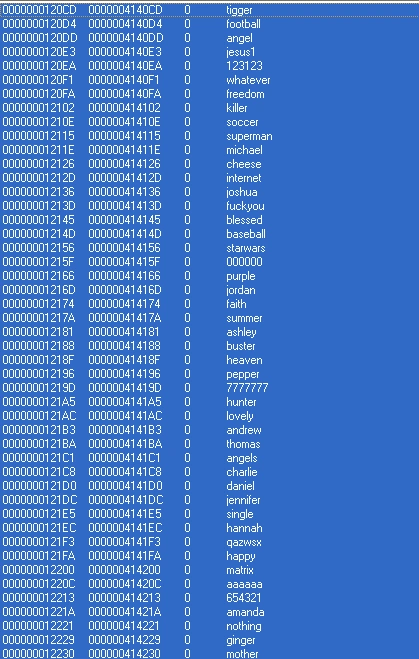
Figure 3 Strings (passwords)
We believe this password list indicates commonly used passwords which are used in brute force attacks. Subsequent analysis uncovered Pony’s password stealer ability, in which it calls a query for encrypted passwords:
| • 000000014070 000000416070 0 signons.sqlite |
• 00000001407F 00000041607F 0 signons.txt
• 00000001408B 00000041608B 0 signons2.txt
• 000000014098 000000416098 0 signons3.txt
| • 000000014070 000000416070 0 signons.sqlite |
| • 0000000140B1 0000004160B1 0 SELECT hostname, encryptedUsername, encryptedPassword FROM moz_logins |
| • 0000000140F7 0000004160F7 0 Firefox |
| • 0000000140FF 0000004160FF 0 \Mozilla\Firefox\ |
• 000000014111 000000416111 0 Software\Mozilla
• 000000014126 000000416126 0 ftp://
• 00000001412D 00000041612D 0 http://
• 000000014135 000000416135 0 https://
• 000000014143 000000416143 0 fireFTPsites.dat
• 000000014154 000000416154 0 SeaMonkey
• 00000001415E 00000041615E 0 \Mozilla\SeaMonkey\
Our sample primarily targeted passwords stored in Mozilla Firefox browsers. The query is trying to fetch the hostname, encrypted username, and encrypted password from Moz_logins table.

Figure 4 Signons.sqlite (moz_logins)
In addition to stored log in details, Pony also targeted FTP details…
• 00000001488B 00000041688B 0 Software\LinasFTP\Site Manager
• 000000014900 000000416900 0 Software\SimonTatham\PuTTY\Sessions
• 000000014989 000000416989 0 FTP destination server
• 0000000149A0 0000004169A0 0 FTP destination user
• 0000000149B5 0000004169B5 0 FTP destination password
• 0000000149CE 0000004169CE 0 FTP destination port
• 0000000149E3 0000004169E3 0 FTP destination catalog
• 0000000149FB 0000004169FB 0 FTP profiles
• 000000014A08 000000416A08 0 FTPShell
• 000000014A11 000000416A11 0 ftpshell.fsi
• 000000014A1E 000000416A1E 0 Software\MAS-Soft\FTPInfo\Setup
… and SMTP email details, including server details, usernames and passwords. Outlook details are also captured:
• 000000014F3C 000000416F3C 0 IMAP Password2
• 000000014F4B 000000416F4B 0 NNTP Password2
• 000000014F5A 000000416F5A 0 HTTPMail Password2
• 000000014F6D 000000416F6D 0 SMTP Password2
• 000000014F7D 000000416F7D 0 POP3 Password
• 000000014F8B 000000416F8B 0 IMAP Password
• 000000014F99 000000416F99 0 NNTP Password
• 000000014FA7 000000416FA7 0 HTTP Password
• 000000014FB5 000000416FB5 0 SMTP Password
• 000000014FC4 000000416FC4 0 Software\Microsoft\Internet Account Manager\Accounts
• 000000014FF9 000000416FF9 0 Identities
• 000000015004 000000417004 0 Software\Microsoft\Office\Outlook\OMI Account Manager\Accounts
• 000000015043 000000417043 0 Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Microsoft Outlook Internet Settings
• 0000000150B9 0000004170B9 0 Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook
• 000000015113 000000417113 0 Software\Microsoft\Internet Account Manager
• 00000001513F 00000041713F 0 Outlook
• 000000015147 000000417147 0 \Accounts
• 000000015151 000000417151 0 identification
• 000000015160 000000417160 0 identitymgr
• 00000001516C 00000041716C 0 inetcomm server passwords
• 000000015186 000000417186 0 outlook account manager passwords
The sample also contained two clsid (class identifier) numbers, neither of which were legitimate:
• {CB1F2C0F-8094-4AAC-BCF5-41A64E27F777}
• {9EA55529-E122-4757-BC79-E4825F80732C}
Further research on these two clsid links them to Pony and Vawtrak malware variants. These clsid numbers can be used as indicators of compromise for detecting either malware strain infections in host machines.
Behavioural Analysis
After executing the sample in our control environment, we observed the malware seeking out the following registry entries:
• SOFTWARE\MICROSOFT\WINDOWS LIVE MAIL
• SOFTWARE\MICROSOFT\INTERNET ACCOUNT MANAGER\ACCOUNTS
• IDENTITIES\{57AB3677-534E-4173-8F92-6566F6F82F10}\SOFTWARE\MICROSOFT\INTERNET ACCOUNT MANAGER\ACCOUNTS
• SOFTWARE\MICROSOFT\OFFICE\OUTLOOK\OMI ACCOUNT MANAGER\ACCOUNTS
• SOFTWARE\MICROSOFT\WINDOWS LIVE MAIL
Software\FlashPeak\BlazeFtp\Settings
Pony then attempts to steal the mail and FTP credentials before calling back to the following URLs:
| hxxp://139.99.8(.)218/~blininfo/temp/shit.exe |
| hxxp://139.99.8(.)218/~blininfo/temp/gate.php |
We accessed these manually and were greeted with only 404 errors. We then observed batch files get dropped in the temp location, which upon execution deleted both the parent and batch files:

Figure 5 Batch file
Prevention
Based on the threat intelligence, we’ve developed yara rules to identify Pony malware infections:

Figure 6 Pony Yara rule to test
The yara rules were tested against this malware sample and detected it without any issue:

Figure 7 Yara rule detects the pony sample
IOC Details:
Url:
hxxp://139.99.8(.)218/~blininfo/temp/shit.exe
hxxp://139.99.8(.)218/~blininfo/temp/gate.php
Conclusion
Not only is Pony a credential stealer, it also compromises the host which can lead to further malware downloads. Although the call back URLs resulted in 404 errors, they should be blocked in proxy and firewall settings. Finally, the above yara rules can detect the malware in the host, and so can be used in any compromise assessment.


