
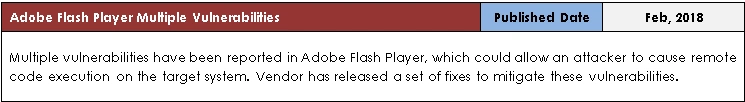
| CVSS V3 Base Score Metrics | |||
| CVE-ID | CVE-2018-4878 | CVE-2018-4877 | |
| Exploitability Metrics | Attack Vector | Network | Network |
| Attack Complexity | Low | Low | |
| Privileges Required | None | None | |
| User Interaction | Required | Required | |
| Scope | Unchanged | Unchanged | |
| Impact Metrics | Confidentiality | High | High |
| Integrity | High | High | |
| Availability | High | High | |
| Type | Use After Free/Remote Code Execution | Use After Free/Remote Code Execution | |
| Base Score | 8.8 | 8.8 |
| Affected Products |
| Adobe Flash Player Desktop Runtime version 28.0.0.137 and earlier versions for Windows, Linux and Macintosh.Google Chrome version 28.0.0.137 and earlier for Windows, Macintosh, Linux and Chrome OS.Microsoft Edge and Internet Explorer 11 version 28.0.0.137 and earlier for Windows 10 and 8.1. |
| Vulnerability Information | ||
| # | VulnerabilityID | Description |
| 1 | CVE-2018-4878 | A use-after-free vulnerability was discovered in Adobe Flash Player before 28.0.0.161. This vulnerability occurs due to a dangling pointer in the Primetime SDK related to the handling of listener objects. A successful attack can lead to arbitrary code execution. This was exploited in the wild in January and February 2018. |
| 2 | CVE-2018-4877 | A use-after-free vulnerability was discovered in Adobe Flash Player before 28.0.0.161. This vulnerability occurs due to a dangling pointer in the Primetime SDK related to quality of service functionality. A successful attack can lead to arbitrary code execution. |
| Safeguards/Recommendations |
| Software updates are given below:Adobe Flash Player Desktop Runtime Version 28.0.0.161Updates are available at Flash Player Download Center and Flash Player DistributionAdobe Flash Player for Google Chrome Version 28.0.0.161Updates are available at Google Chrome ReleasesAdobe Flash Player for Microsoft Edge and Internet Explorer 11 Version 28.0.0.161Updates are available at Microsoft Security AdvisoryAdobe Flash Player installed with Google Chrome will be automatically updated to the latest Google Chrome version, which will include Adobe Flash Player 28.0.0.161 for Windows, Macintosh, Linux and Chrome OS.Adobe Flash Player installed with Microsoft Edge and Internet Explorer 11 for Windows 10 and 8.1 will be automatically updated to the latest version, which will include Adobe Flash Player 28.0.0.161.Vendor advisory is available. |
| IOCs |
| hxxp://www.1588-2040.co[.]kr/conf/product_old.jpg hxxp://www.1588-2040.co[.]kr/conf/product.jpg hxxp://www.1588-2040.co[.]kr/design/m/images/image/image.php hxxp://www.dylboiler.co[.]kr/admincenter/files/board/4/manager.php hxxp://www.korea-tax[.]info/main/local.php hxxp://www.korea-tax[.]info/main/local.phploadswf_SWFBClass hxxp://www.dylboiler.co[.]kr/service/store.php hxxp://www.dylboiler.co[.]kr/admincenter/files/boad/4/manager.php 1f93c09eed6bb17ec46e63f00bd40ebb 4c1533cbfb693da14e54e5a92ce6faba 5f97c5ea28c0401abc093069a50aa1f8 9593d277b42947ef28217325bcc1fe50 394e52e219feb1a5c403714154048728 d2881e56e66aeaebef7efaa60a58ef9b 111d205422fe90848c2f41cc84ebd96a 3142fc8c1142f25698dabe8921996753 3f98c434d7b39de61a8b459180dd46a3 a47176bbc8aa136eb2814f3113617af7 f75a5e7ecc26c089c8d20406ea192c49 PDB path: F:\work\flash\obfuscation\loadswf\src |
| AV detection |
| McAfee : Exploit-CVE2018- 4878.b Kaspersky : Exploit.SWF.Agent.rs Sophos : Exp/20184878-A ESET-NOD32 : SWF/Exploit.CVE-2018- 4878.A |
| Mitigations |
| Administrators may also consider implementing Protected View for Office. Protected View opens a file marked as potentially unsafe in Read-only mode.It is safe to uninstall/disable Adobe Flash from all machines in your organization.Disable Flash on a browser that does not display untrusted Flash content OR enable Click to Play function.Open the Security tab from “Internet Options” in Internet Explorer and set the security level of Internet zone and local intranet zone to “High”.Be careful not to open suspicious office files coming via unknown sender.If you are running Internet Explorer on Flash Player 27 or later and Windows 7 or later you may be able to avoid running it by prompting, to play SWF content.Yara rule implementation (not tested)Snort Rule alert tcp $HOME_NET any -> $EXTERNAL_NET $HTTP_PORTS (msg:”Possible CVE-2018-4878 check-in alert”; flow:established,to_server; http_uri; content:”?id=”; http_uri; content:”&fp_vs=”; http_uri; content:”&os_vs=”; http_uri; reference: source, Vitali Kremez-Flashpoint; classtype:Trojan-activity; rev:1;) |
| Version History | |
| Version 1.0 | Initial Report with Safeguards/Recommendations and the released fixes. |


