
Overview
The LMNTRIX Threat Intelligence Platform has recently found a new variant of Tron, a ransomware that targets non-Russians, under the microscope. This sample underwent analysis:
File Hash (SHA-256): fb45f10c886974e29a57673769c0bc4e53fcaf063e172e38d92eea85bf570aff
File Size: 87.5 KB
File creation- TimeDateStamp: (Thu Apr 12 16:54:17 2018)
Infection
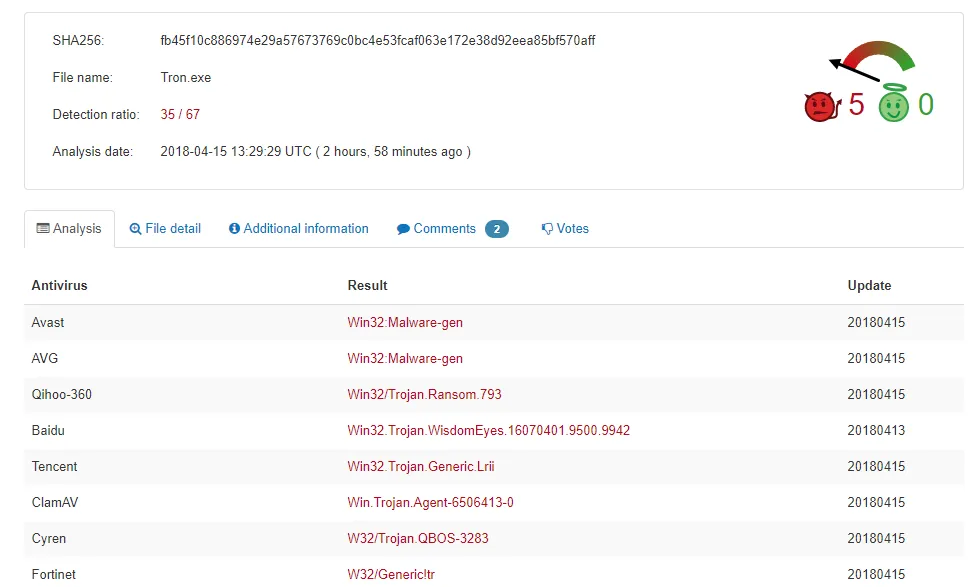
Figure 1 VT result for Tron Ransomware
Analysis of the Ransomware sample
Our researcher team checked the file’s PE details it found to be compiled using .Net.
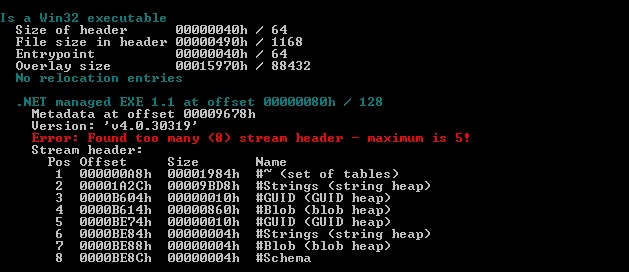
Figure 2 Compiled using .Net
We listed the following malicious indicator in the sample as shown in the screenshot:
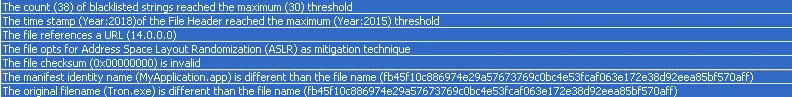
Figure 3 Malicious Indicator
Blacklisted strings count is 38 and the original file name is Tron.exe. Our researcher dissected the sample and analyse the code.
Threat Indicators
When we dissected the codes, we found the file locations in the victim’s system that would be targeted by the ransomware.
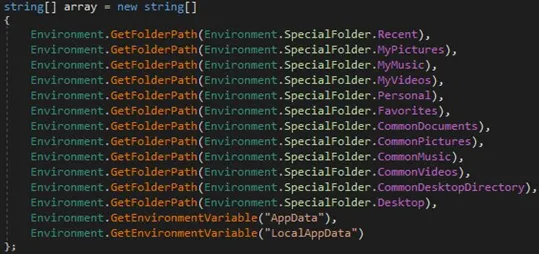
Figure 4 Targeted folders
When we executed the file, it encrypted the files in all those folders listed above. And it added the file extension as ‘Tron’ after encryption:

Figure 5 Tron Extension added after encryption
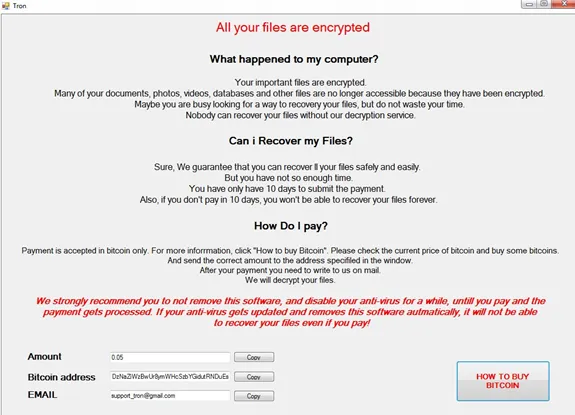
Figure 6 Ransom notes and Payment methods
Not Russia Then Exit
In this code, we found that this ransomware sense the geo location and if it detects the location as Russia then it exits.
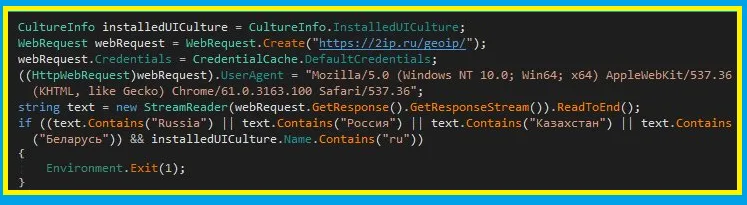
Figure 7 If Russia then exit
Threat Indicators
IOC details:
File Hashes:
SHA 256: fb45f10c886974e29a57673769c0bc4e53fcaf063e172e38d92eea85bf570aff
SHA 256: 41b9d94f13dd2b2d9d3b01df692f1837731a932e2ae938cccf34905064f6f30f
File extension added by this variant of ransomware:
‘.tron’
Conclusion
We suspect that we will continue to see the rise of geo-targeted ransomware, which in part, has the advantage for threat actors of presumably limiting local law enforcement concerns about their activities since there targets are outside of their own geographic jurisdictions.


