
Despite a deep bag of tricks, cyber scammers often fall back on the tried-and-true method of spoofing legitimate emails to trick victims into executing malware. If you’ve ever heard the term ‘phishing’, that’s what we’re talking about today.
It’s not original, but it is effective.
Check your spam folder now and you’ll have dozens of emails purporting to include tracking numbers from DHL or UPS, the location of hot singles in your area or, as we’ll be looking at today, payment advice from your bank.
All a victim needs to do is click on the links or open the attachments in these emails, and they’ve already lost the battle. Their device is no longer theirs.
Given the prevalence of phishing attacks, today we’re going to unpack one such campaign. Masquerading as payment advice from HSBC, the scammers in this case are dropping the Fareit (aka Pony) Password Stealer. In addition to its ‘Stealer’ functionality, Fareit can also be used as a Downloader, allowing the attacker to remotely load any other malware on the system.
A few years ago, Fareit/Pony was used to steal more than $200,000 in bitcoins and more than 700,000 credentials. See? Effective.
Email Analysis
Before we analyse the malware, let’s take a look at what the potential victim sees – the email. The campaign’s primary email is said to have been sent from “HSBC BANK Advising Service” by spoofing Mail-id advising.service556421@hsbc.com from IP – 198.57.177.246.
So far in this campaign we’ve seen two variants of the HSBC email, one sent from ‘HSBC BANK Advising Service’ and the other from ‘HSBC Bank Service’. The Header Info for both is below:
Received: from server.hollandi.com (server.hollandi.com [198.57.177.246])
for ; Tue, 1 Aug 2017 16:50:44 +1200
Received: from [127.0.0.1] (port=37168 helo=hollandi.com)
by server.hollandi.com with esmtpa (Exim 4.87)
(envelope-from ) Tue, 01 Aug 2017 04:34:59 +0000
Content-Type: multipart/alternative;
Date: Tue, 01 Aug 2017 04:34:57 +0000
From: HSBC BANK Advising Service
To: undisclosed-recipients:;
Subject: ©HSBC Bank Plc… Payment Advice / Swift Copy
User-Agent: Roundcube Webmail/1.1.4
OR
Received: From e-marketing@hsbc.com.hk Wed Jul 26 07:56:07 2017
Wed, 26 Jul 2017 07:56:07 -0400
Received: from [198.57.177.246] (helo=server.hollandi.com)
by mail.victim.example with esmtps (Exim 4.63)
From: HSBC Bank Service
To: undisclosed-recipients:;
Subject: Fwd: Wire Transfer
Interestingly, we found the above IP address is being used in multiple simultaneous campaigns – see the table below:
| Date | Subject | IP |
| 03-08-17 | Re: Bank Details Payment, Invoice | 198.57.177.246 – server.hollandi.com |
| 03-08-17 | FedEx Shipment 784213218998: Delivery scheduled for tomorrow | |
| 01-08-17 | UPS Exception Notification, Tracking Number 1Z36X67E03938098 | |
| 01-08-17 | Re: Bank Details Payment, Invoice | |
| 25-07-17 | Fwd: Wire Transfer |
We ran the IP address through IPVoid and had the below results:
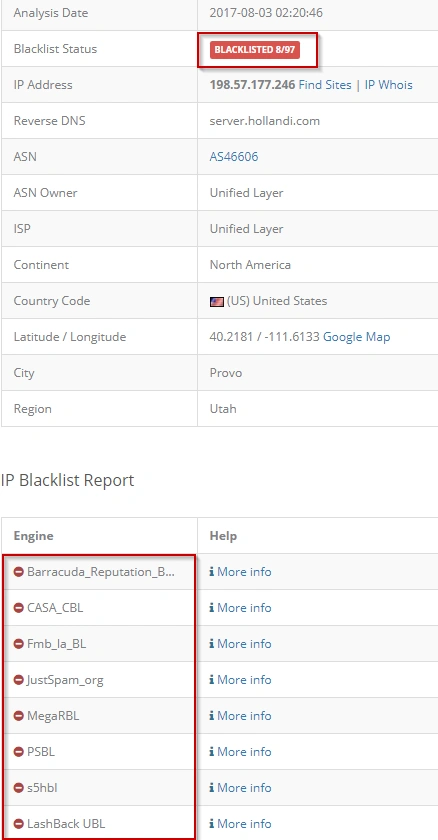
Image: IP info & Geo location (using IPvoid.com)
Below we see the first email sent to potential victms. Note how all the links lead to the same malicious domain.
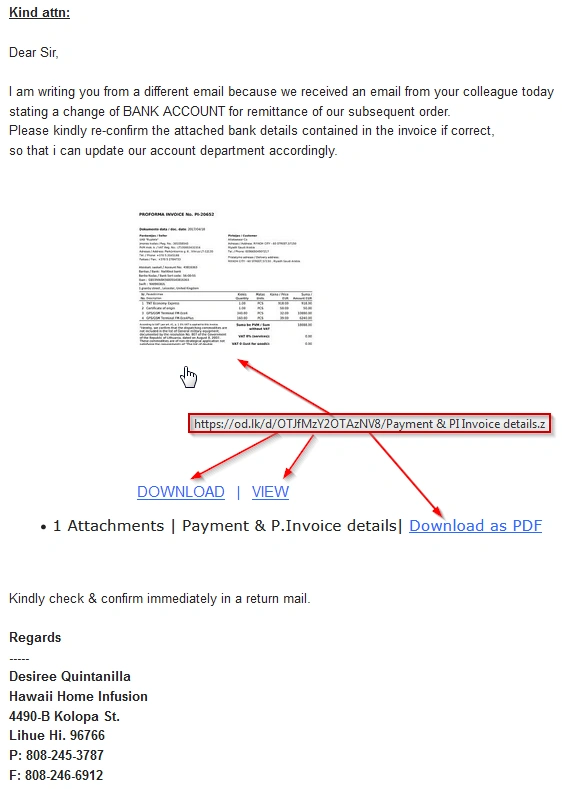
Image: Bank Account / Invoice spoofed mail
Here we have the second version of the email. Although the text is different, all links once again lead to the fall of Rome.
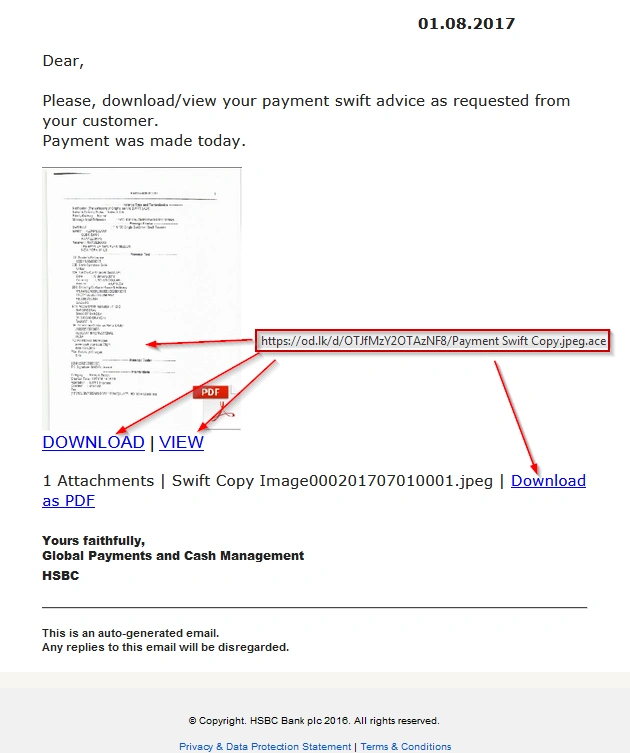
Image: Bank Account / Invoice spoofed mail
Although the links in the above two emails are slightly different, both of them redirect to: hxxps://web.opendrive.com/api/v1/download/file.json/OTJfMzY2OTAzNV8?inline=0
If successful, the following content is downloaded:
Email One: File – Payment & PI Invoice details.z
SHA256 – 6945c30a23c9fe3f58affaa35bfff40317b7eb11c2557a585d0d7f0b35cf03e9
Email Two: File – Payment Swift Copy.jpeg.ace
SHA-256 – 407e12198559a468f711cd2ea480a046fe93632816602238228503b64d44b089
Inside both files we discovered a PE file:
File Name – Payment & PI Invoice details.scr & Payment Swift Copy.jpeg.scr
SHA 256 – 83fb46296b16ba69d8fe662fa0db65284bcc4cafb32bd3cdeb08ee8ca5d31194
We then ran the files through Virus Total, with the following results:
Only two antivirus (AV) vendors detected the Zip file (SHA-256 – 407e12198559a468f711cd2ea480a046fe93632816602238228503b64d44b089) as malicious.
The AV vendors fared slightly better (13/57) with the PE file (SHA 256 – 83fb46296b16ba69d8fe662fa0db65284bcc4cafb32bd3cdeb08ee8ca5d31194) although there was no static detection found.
We also saw that the same file has been submitted with multiple different names.
Screenshots of all three results are below:
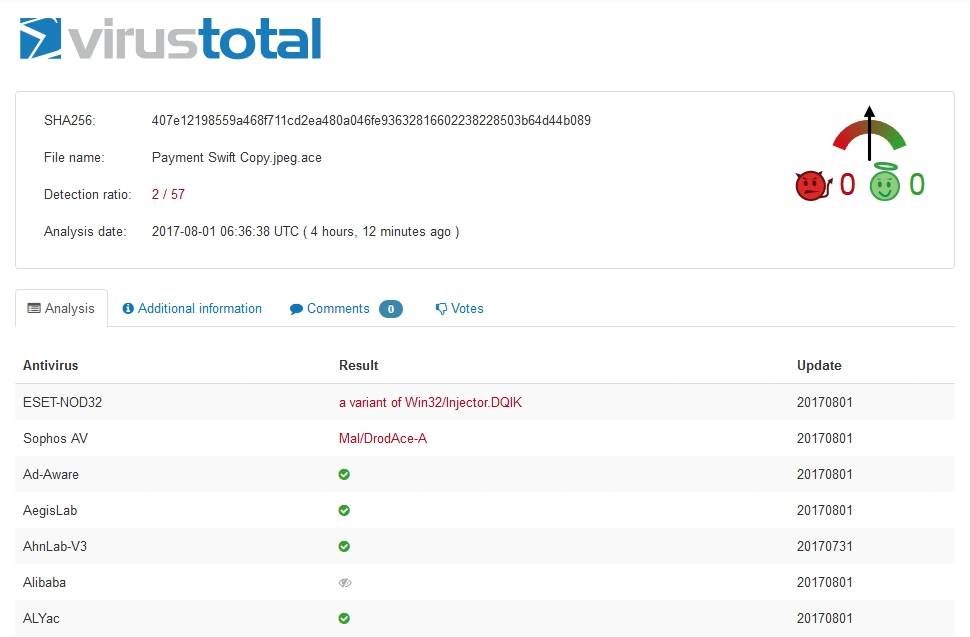
Image: Virustotal source for Zip detection
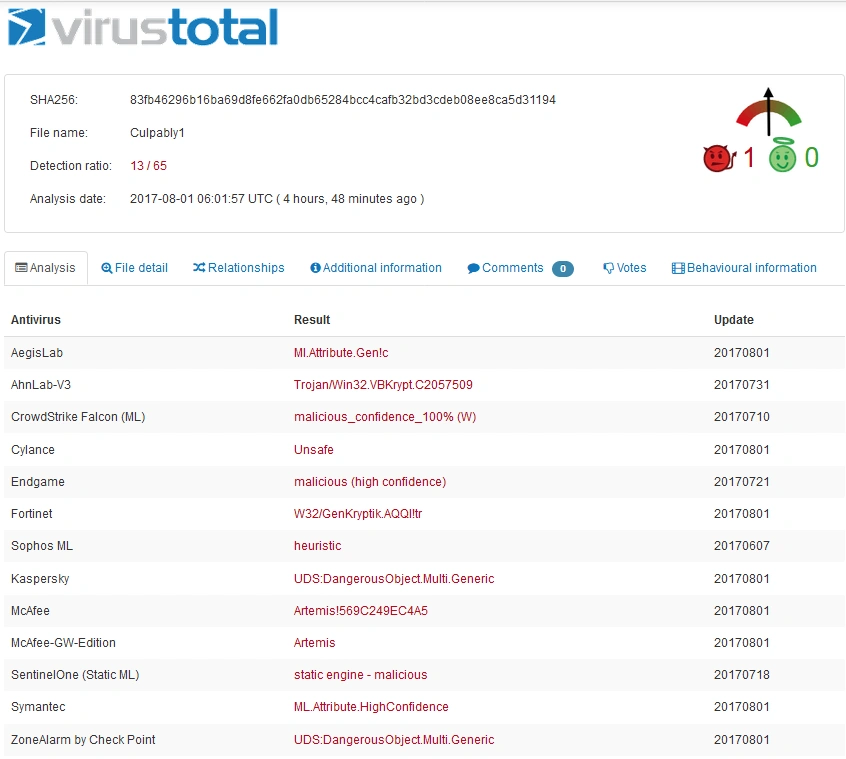
Image: Virustotal source for PE detection
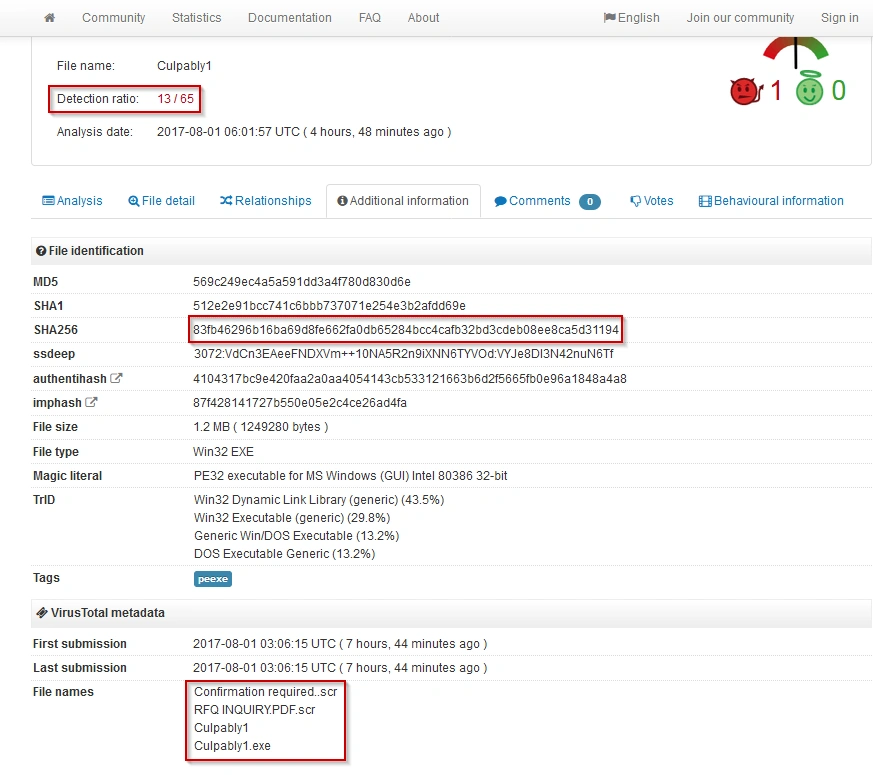
Image: Virustotal source for PE detection + Internal Info
Malware Analysis
As shown below, the malicious file comes with an LNK shortcut ICON, whose original name is “Culpably1.exe”. It is a Microsoft Visual Basic file.
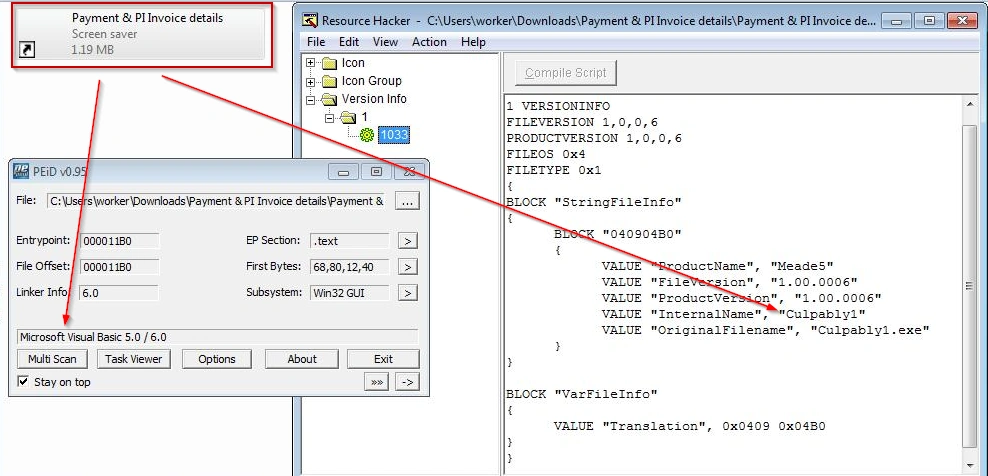
Image: PE file Internal info
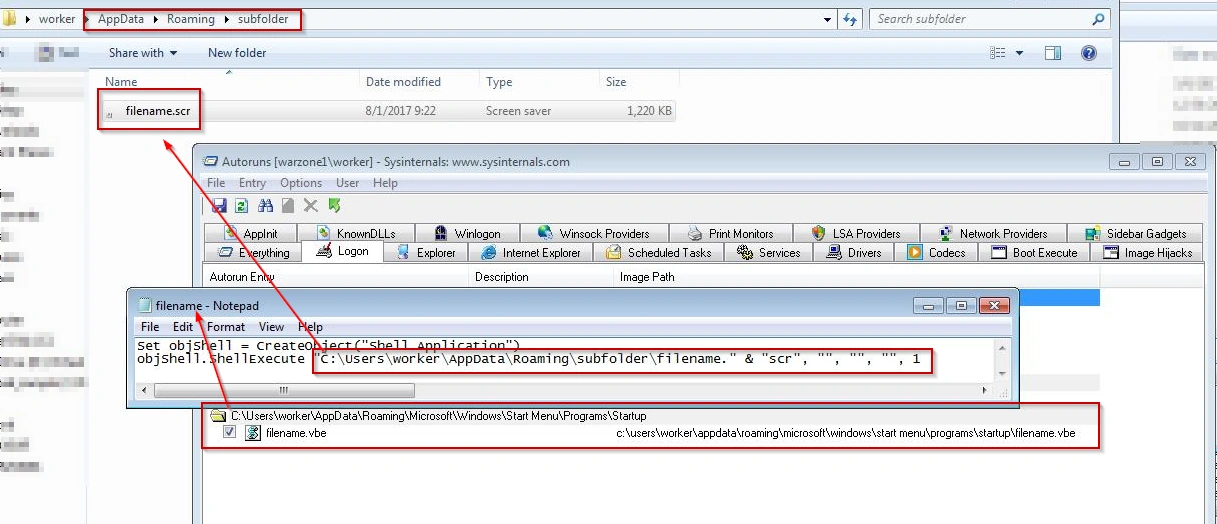
The malicious file gets copied to the C:\Users\\AppData\Roaming\subfolder as “filename.scr” and the original copy is deleted. Also, the 14439072.bat file is dropped in %temp%.
Additionally, “filename.vbe” is created in startup, so that the malware executes whenever the system starts up. The command which executes this file is:
objShell.ShellExecute “C:\Users\worker\AppData\Roaming\subfolder\filename.” & “scr”
Next, we ran the malware through cuckoo – an automated analysis engine:
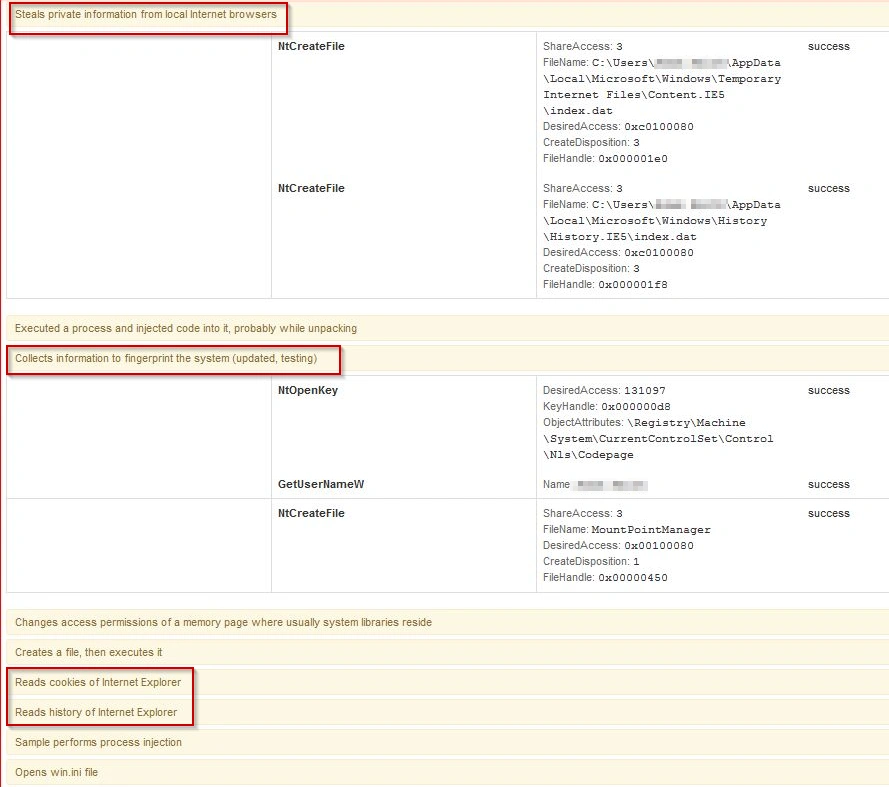
Image: Fareit Behavior – Cuckoo analysis
This show us the full functionality: it steals private information from local Internet browsers and collects information to fingerprint the system and read cookies/browser history.
Network Activities
Like any malware, a connection must be established in order to receive further instructions and configuration. In this case, it is trying to connect to the CnC server:
hxxp://alliedharvast.com/ramos/panelnew/gate.php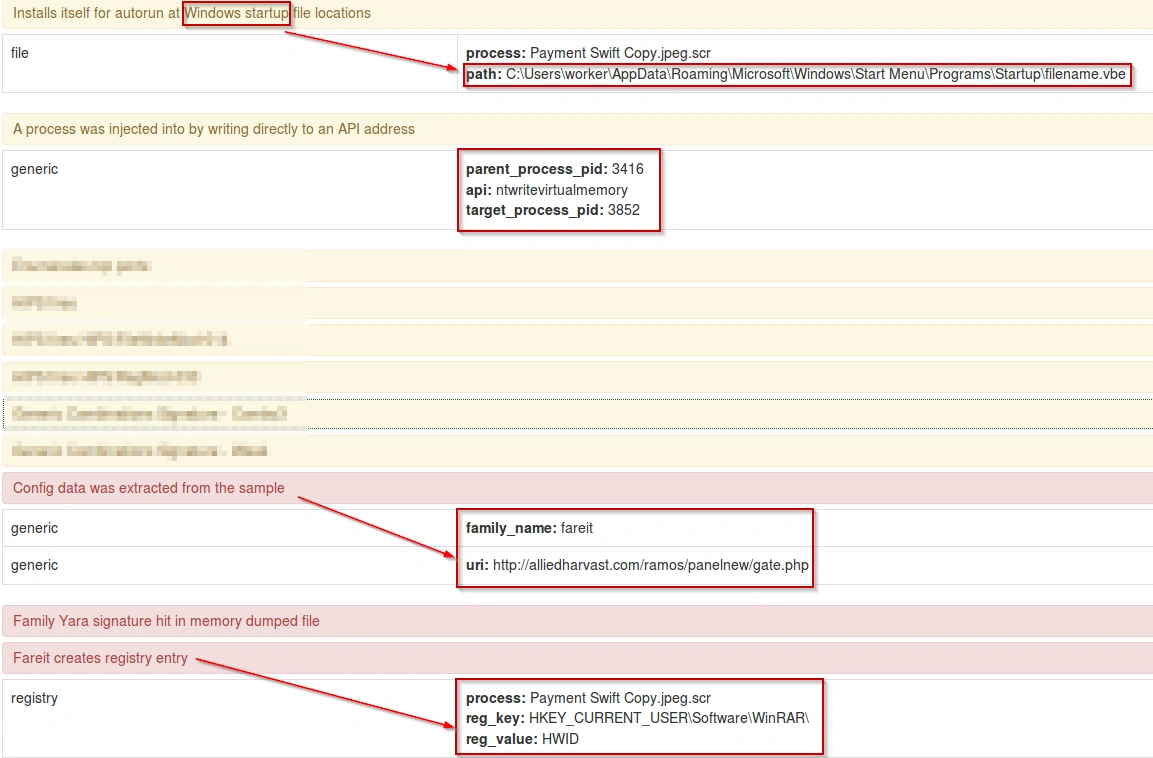
Image: Fareit Behavior and CnC connection seen during Cuckoo analysis
Finally, it also calls out to:
hxxp://pornhouse.mobi/main.php?dir=//Virgin%20Babes%20First%20Sex&start=1&sort=1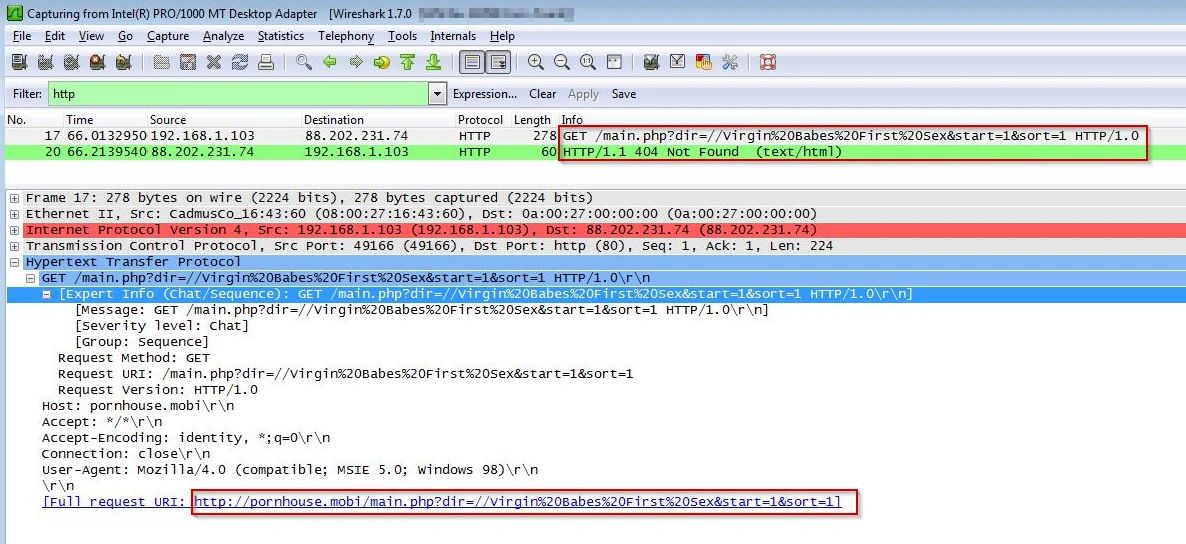
Image: Network Activity via Wireshark
Conclusion
At a passing glance, these emails can look legitimate. Before opening them, however, take a minute to verify the sender’s address. Also, most banks these days will never ask you to send them details via email and, finally, if in doubt you can always call the institution and check.
A few minutes diligence can save you from having your personal details fall in the hands of attackers who won’t hesitate to milk you dry.
Another good tip is to configure your email server to block or remove emails that contains file attachments and/or URLs commonly used to spread threats such as .vbs, .bat, .exe, .pif and .scr files.


