
Overview
Since its discovery in 2007, the Ursnif banking trojan has made a name for itself as one of the most widely used banking malware variants (second only to Zeus). It is known for stealing bank account details, credit card data, and, in recent years, various other login credentials. Ursnif, which is also known as ‘Gozi’, can spread via infected USB flash drives, though its most recent campaigns have relied on more traditional malspam techniques.
In one such campaign, our researchers discovered Ursnif hidden in a malicious .zip file attachment. The phishing email’s subject line was “AA Insurance Invoice” and the attachment was embedded with a .LNK file which acted as a downloader for actual malware. All these details are available in the IOC section further below.
Additionally, recent threat intelligence evidence suggests some Ursnif campaigns are employing FastFlux techniques in order to evade detection. This technique involves using an ever-changing network of compromised machines to act as proxy servers. By rapidly swapping the CnC IP address, rules-based detection technologies may struggle to keep up with the update cycle. The below screenshot shows the multiple IP addresses believed to be associated with the Fast Flux technique:

Figure 1
Ursnif is a global malware in the truest sense of the word. Recent campaigns have targeted Japanese and Australian users, though it has been used extensively in the past to target European and US victims. Its C&C servers are similarly widespread. Below, we see the location of its servers in the US, South America, Northern Africa, the Middle East and throughout Europe. It is also known to have servers in South East Asia.
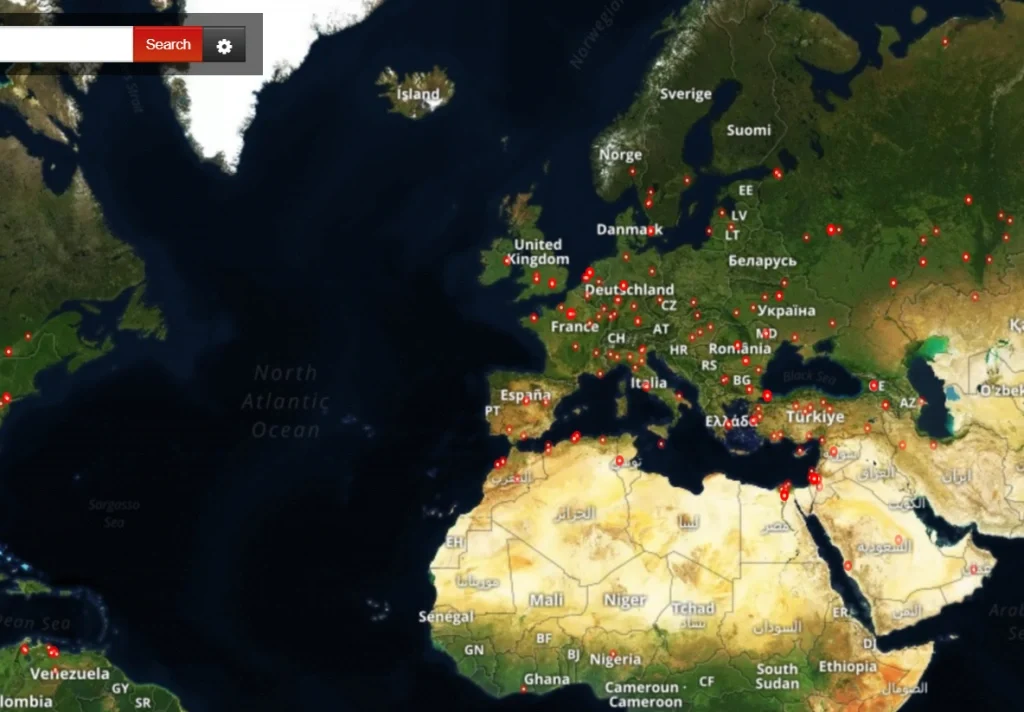
Figure 2
Static Analysis:
File type: PE (Exe file)
Hash (SHA-256): 3c7aa81d3bb71a7dce4cb2cad5c04e511a7210dcb435e03b118f6e7774822718
Size: 563712 bytes
File description: Vertex Cleaning Agency
AV detection:
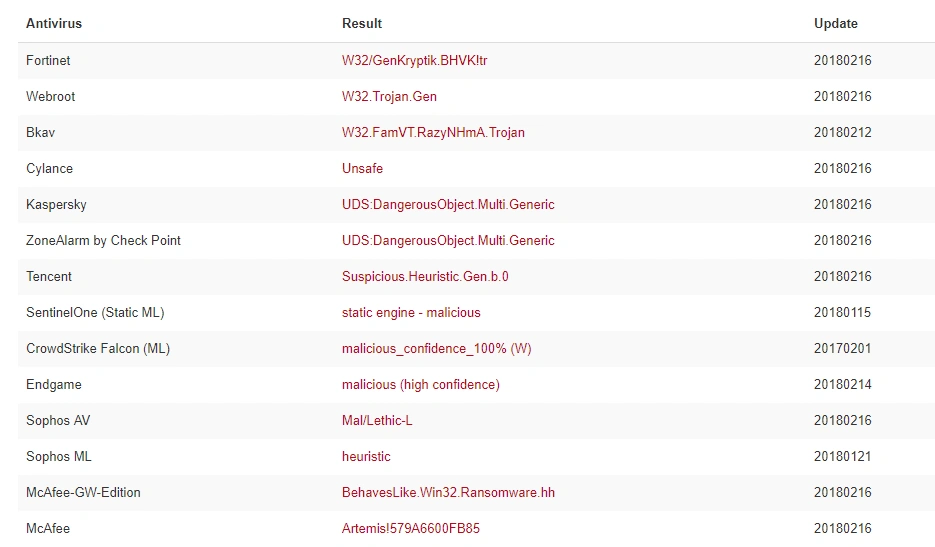
Figure 3 Latest detection for this sample
We first tested to see how successful AV vendors were in detecting this sample. While it was picked up by most vendors, it was not identified as Ursnif which would suggest the detections are based on heuristic signatures.
File Properties and DLL dependencies:
The sample our researchers discovered is a 32 bit PE .exe file called “vertex cleaning agency”. After reviewing the import DLLs, we spotted features including anti-debug and blacklist APIs. The below snapshot gives more information on PE file type and import DLL details:
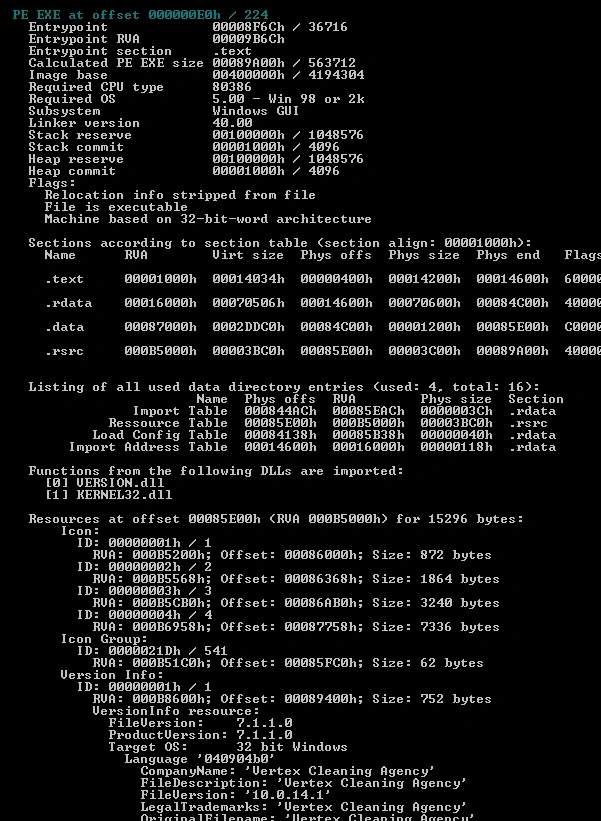
Figure 4 File properties and dll dependencies
The above snapshot shows that only two DLLs are found in the import table – Version.dll and Kernel32.dll. We’ve extrapolated further functionality below:
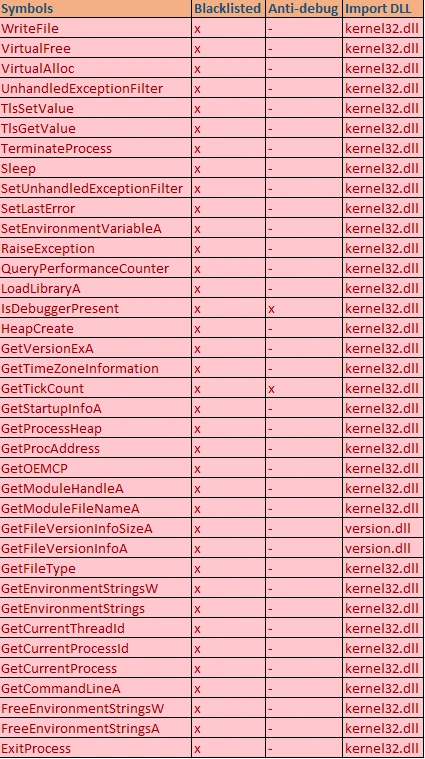
Figure 5 Blacklisted and Anti-debug API
IsDebuggerPresent, and GetTickCount are obviously anti-debug APIs which are widely used to evade detection.
Behavioural and code analysis:
Our researchers analysed this malware in a controlled environment to observe its behaviour. After execution, it contacts the following Italian URL:
hxxp://mondomusicatania(.)it
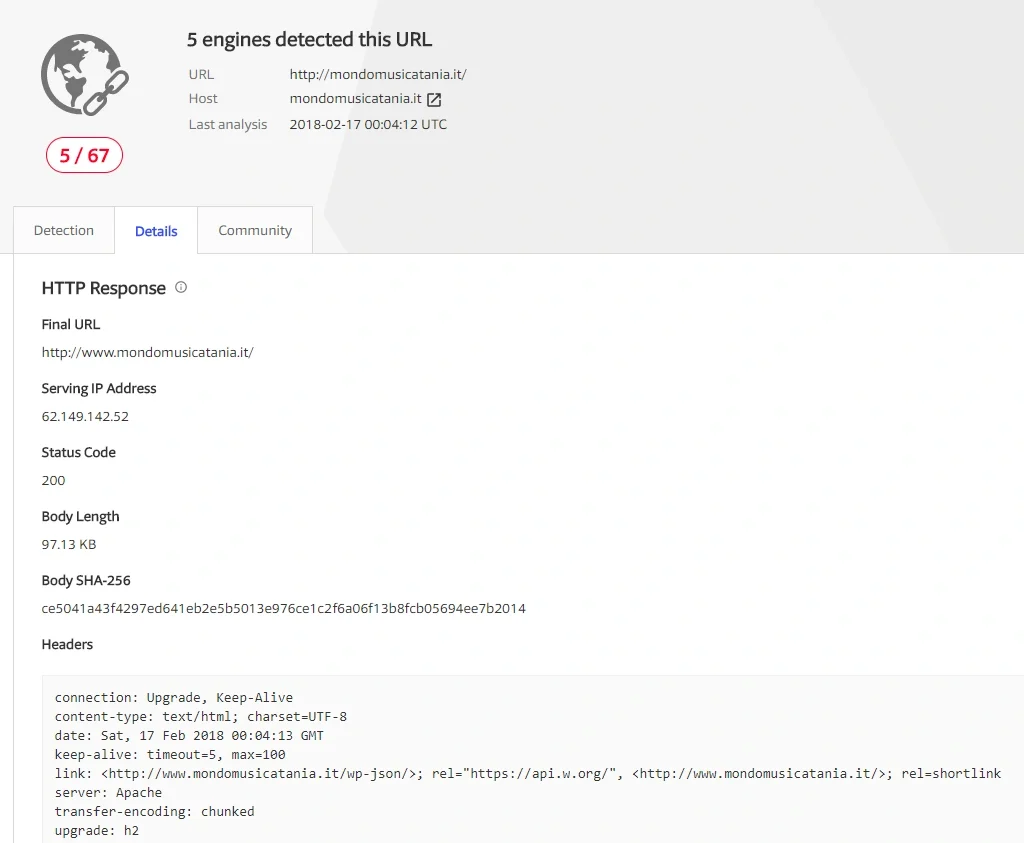
Figure 6 Details of the URL contacted

Figure 7 AV detection for the contacted URL
Multiple anti-malware solutions flagged this website.
After executing the original file, it creates a duplicate file in a folder inside %appdata% as follows:
| %appdata%\Microsoft\Capemesh\batmvmgr.exe |
The same file is then linked with the autostart registry entry in order to maintain persistence:

Figure 8 Run entry created for maintaining persistence
Ursnif then made entries related to address book and internet account managers, as follows:
| HKEY_CURRENT_USER\Software\Microsoft\Internet Account Manager HKEY_CURRENT_USER\Software\Microsoft\Internet Account Manager\Accounts HKEY_CURRENT_USER\Software\Microsoft\Internet Account Manager\Accounts\Active Directory GC HKEY_CURRENT_USER\Software\Microsoft\Internet Account Manager\Accounts\Bigfoot HKEY_CURRENT_USER\Software\Microsoft\Internet Account Manager\Accounts\VeriSign HKEY_CURRENT_USER\Software\Microsoft\Internet Account Manager\Accounts\WhoWhere HKEY_CURRENT_USER\Software\Microsoft\WAB HKEY_CURRENT_USER\Software\Microsoft\WAB\WAB4 HKEY_CURRENT_USER\Software\Microsoft\WAB\WAB4\Wab File Name |
Finally, a WAB file is created in the location: Microsoft\AddressBook\(username).wab
IOC details:
Hash: 3c7aa81d3bb71a7dce4cb2cad5c04e511a7210dcb435e03b118f6e7774822718
Malicious URL contacted: hxxp://mondomusicatania(.)it
Malicious IP address: 62.149.142(.)52
Registry entry:
Key: “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run”
Value: “comssapi”
Data or Physical location: “%Appdata%\Microsoft\Capemesh\batmvmgr.exe
Infection URL: hxxp://nth-gen.co.uk/AA%20Insurance%20Invoice.zip
Infection URL Domain: nth-gen[.]co[.]uk
Infection URL IP: 46.249.205.43
IOC for Insurance Campaign Malicious File (mentioned in introduction):
File name: AA Insurance Invoice.zip
MD5: b85fddb1c4b9035138cd30d31c180faf
SHA256: ed4007797c15d89bca7fe4ad0411807fb1d075917f01f410f8a78648bf1a04f9
Conclusion
By using the above IOCs, in particularl blacklisting the malicious URL and IP addresses, organisations can limit their exposure to the latest Ursnif campaign. While we’ve seen no evidence in this campaign of the use of infected USB devices, its authors have been known to use this tactic in the past. As such administrators need to a keep strict policy on the usage of unauthorised USB and storage devices inside the network (this should be a no-brainer, but it never hurts to double check).


