
Despite the creator of NanoCore RAT being sentenced to 33 months jail last year, his creation lives on. LMNTRIX Cyber Defense Centre analysts recently discovered the malware was being offered for free on the Dark Web. The below thread, posted on April 8 this year and written in German, lists a number of RATs available for free download. As well as NanoCore, the author provides links to several other malware variants including Babylon RAT and Echo RAT:
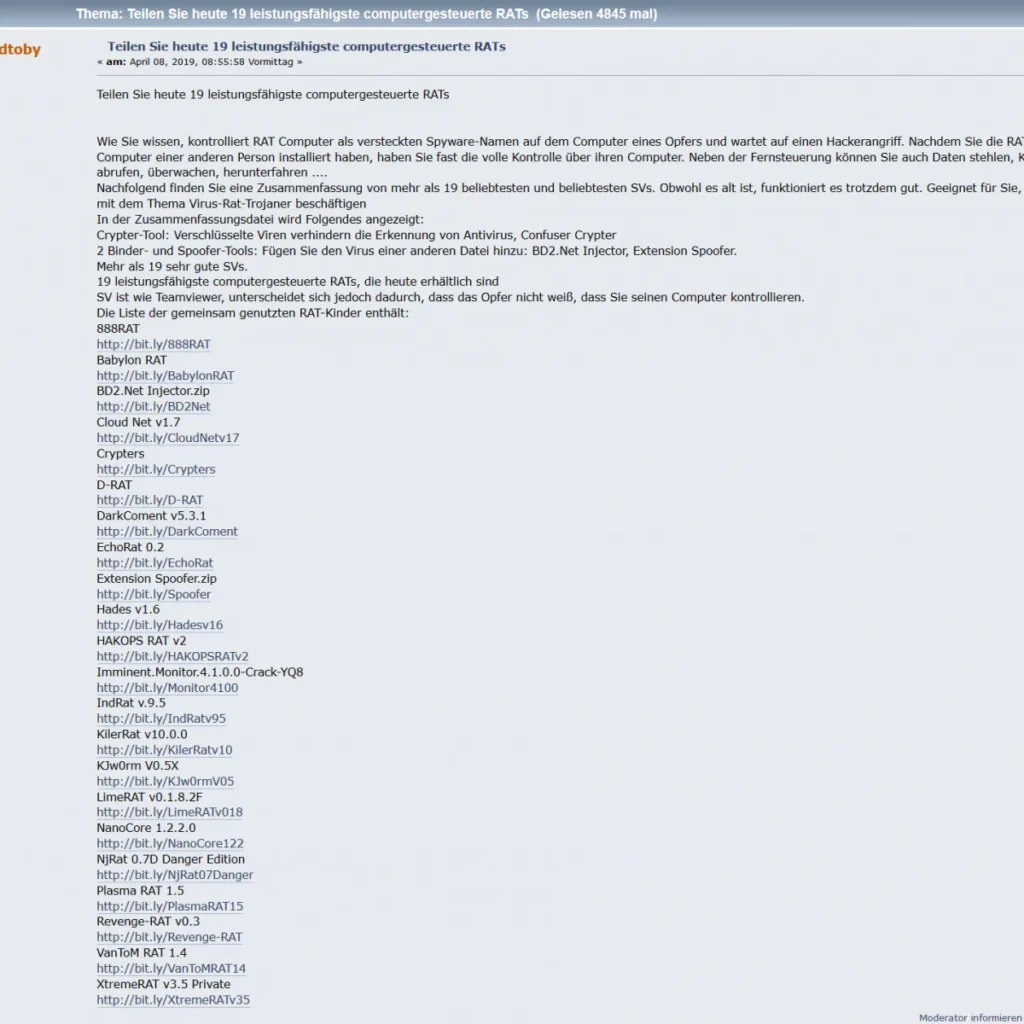
Figure 1: Deep Web Forum containing download links to RATs
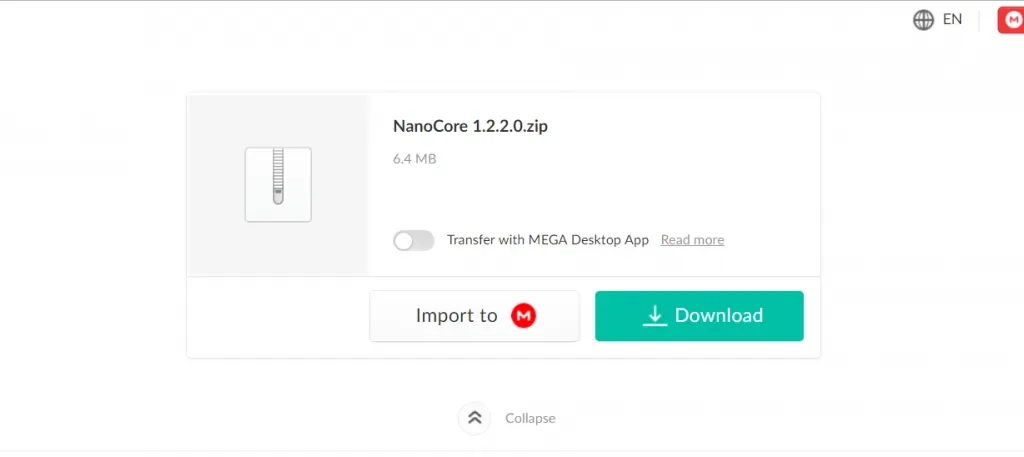
Figure 2: Downloading Nanocore RAT
Taylor Huddleston was the first malware author to be prosecuted for their creation – a creation which has taken on a life of its own, spawning newer variants such as LuminosityLink RAT and Surprise Ransomware. The current version of NanoCore being offered for free online is v1.2.2, it is written in C# dot.net and has the following features:
- Remote client shutdown / restart
- Remote File Browser, Task Manager, Registry Editor, Remote Console
- Remote Mouse control
- Open webpages
- Open CD Tray
- Disable Webcam Lights
- Remote Execute
- Remote Computer Locker with custom encryption (like ransomware)
- Remote Reverse Proxy
- Remotely recover passwords
- Remote Keylogging
- Remote Video / Audio capture
Once downloaded from the Dark Web, the NanoCore RAT is controlled through a user-friendly interface. This lowers the barrier for entry and enables even the most amateur hackers to weaponise emails and kick off their own campaigns:
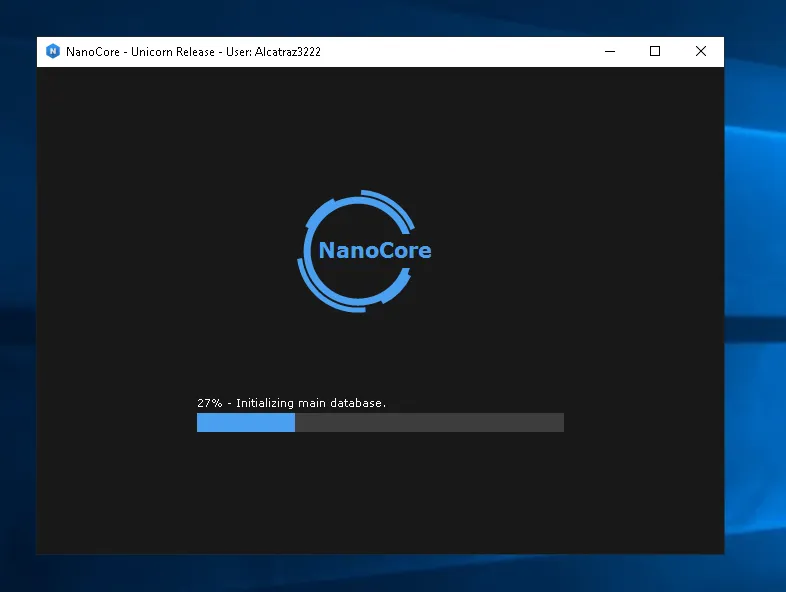
Figure 3: Nanocore RAT loading screen
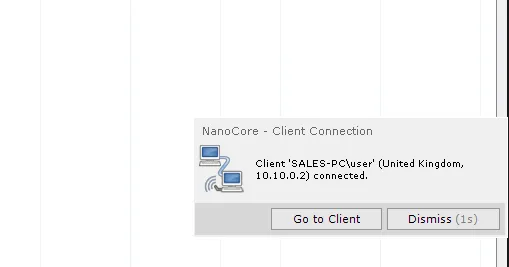
Figure 4: Nanocore client connection
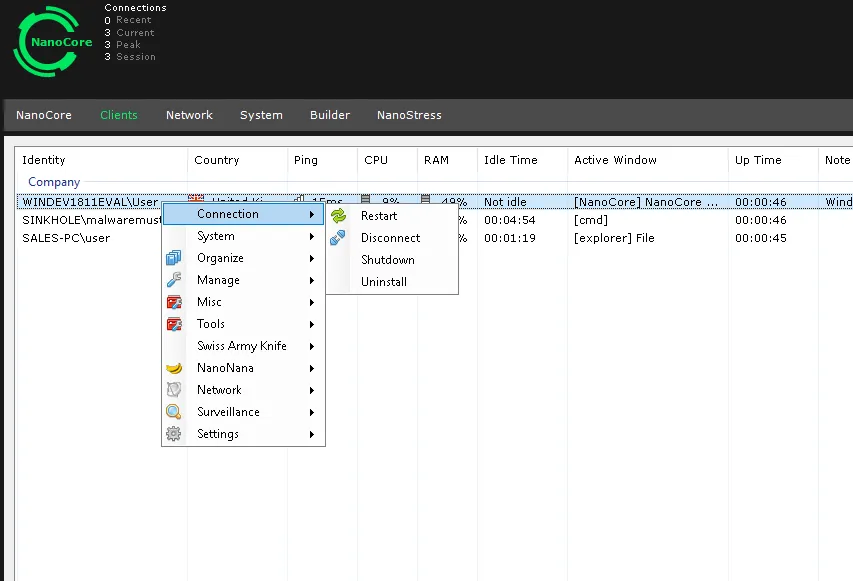
Figure 5: Nanocore Management
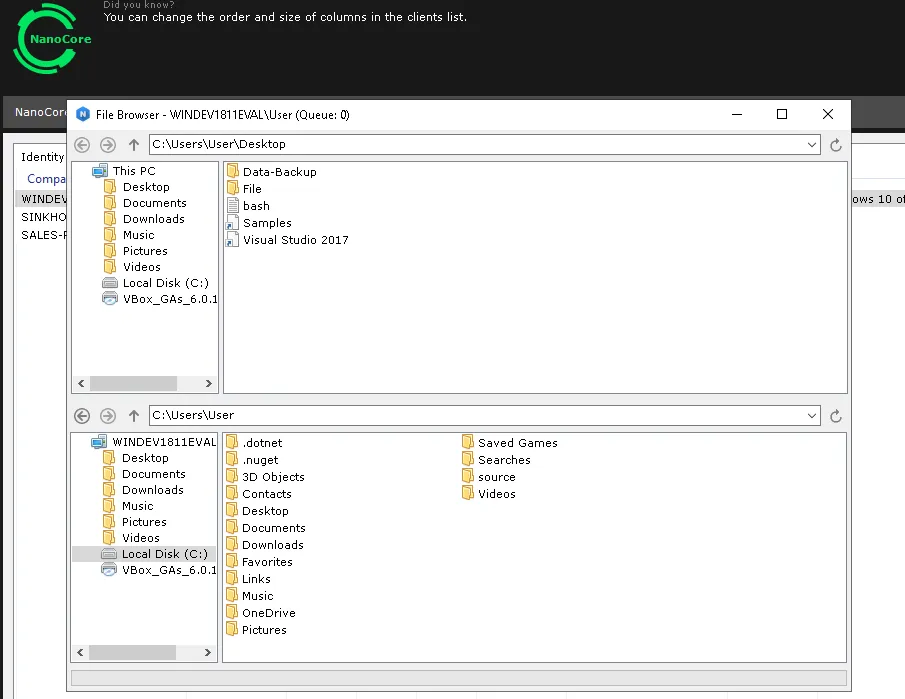
Figure 6: Nanocore Remote File Browser
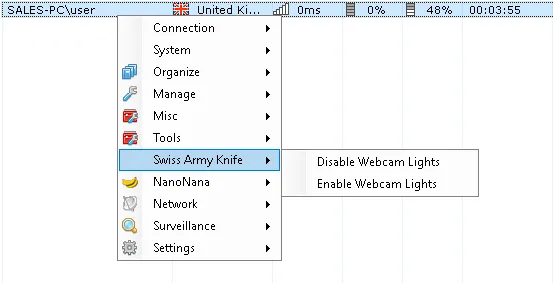
Figure 7: Nanocore Management – Turn off webcam lights
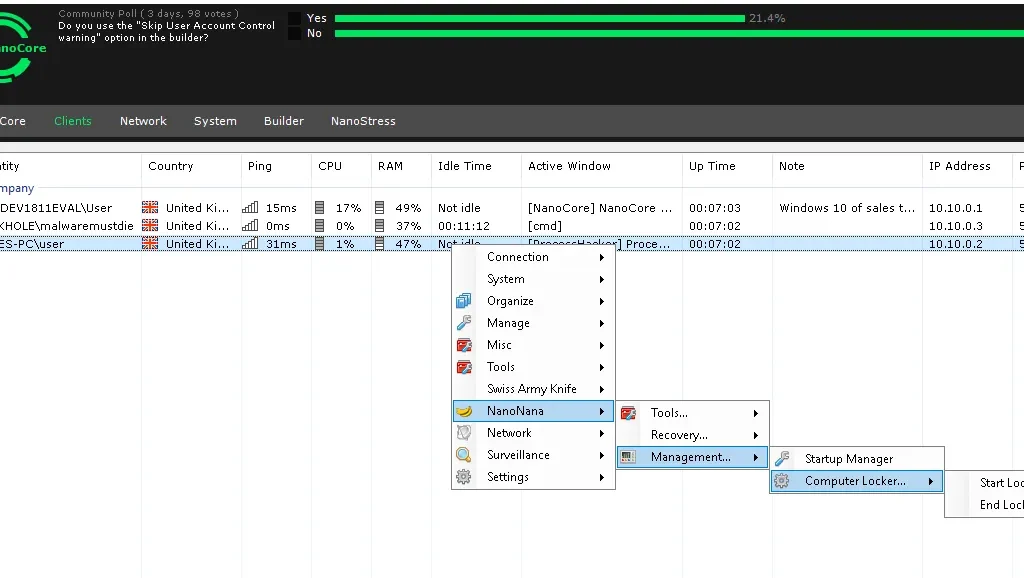
Figure 8: Nanocore Management – Ransomware Module
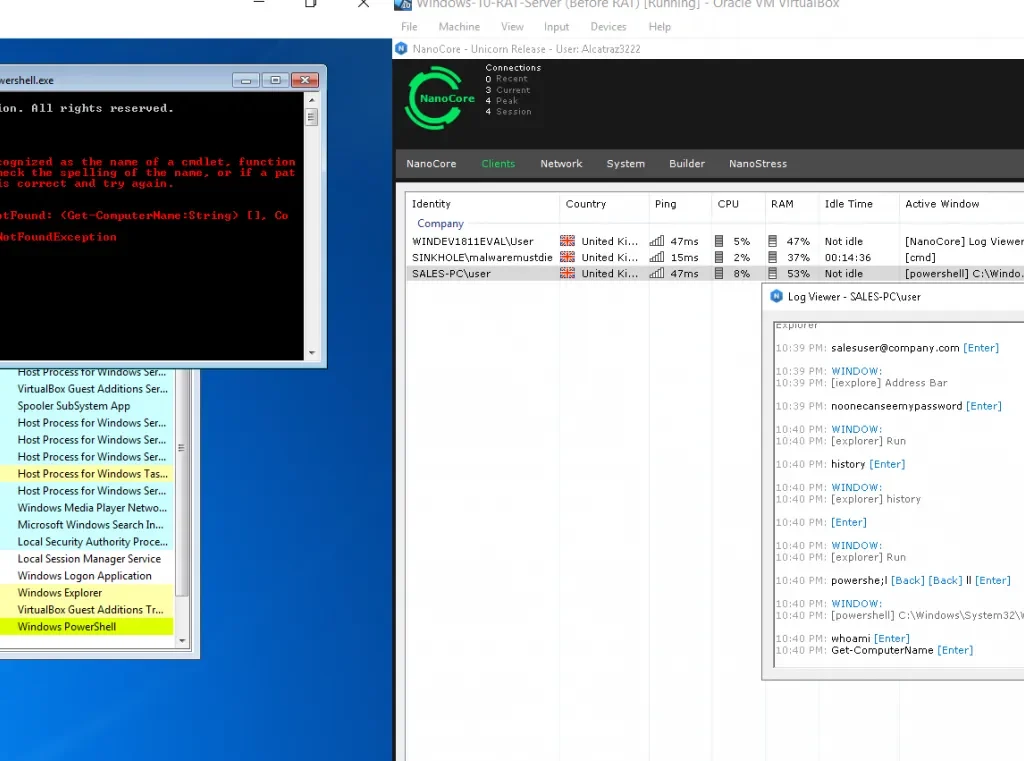
Figure 9: Nanocore Management – Keylogging Module
Anytime an exploit kit or RAT kit is made available for free, it leads to an explosion of campaigns using the malware – something we have observed since this Dark Web posting in April.
Current Campaign and TTP
One of these current campaigns uses a very common TTP as it employs infection via phishing mail and macro-enabled word document. The phishing emails are targeted to the administrative mail address of an organisation and are spoofed to resemble invoices or purchase orders. The attachment names are usually “URGENT.doc” or “PO URGENT.doc”:
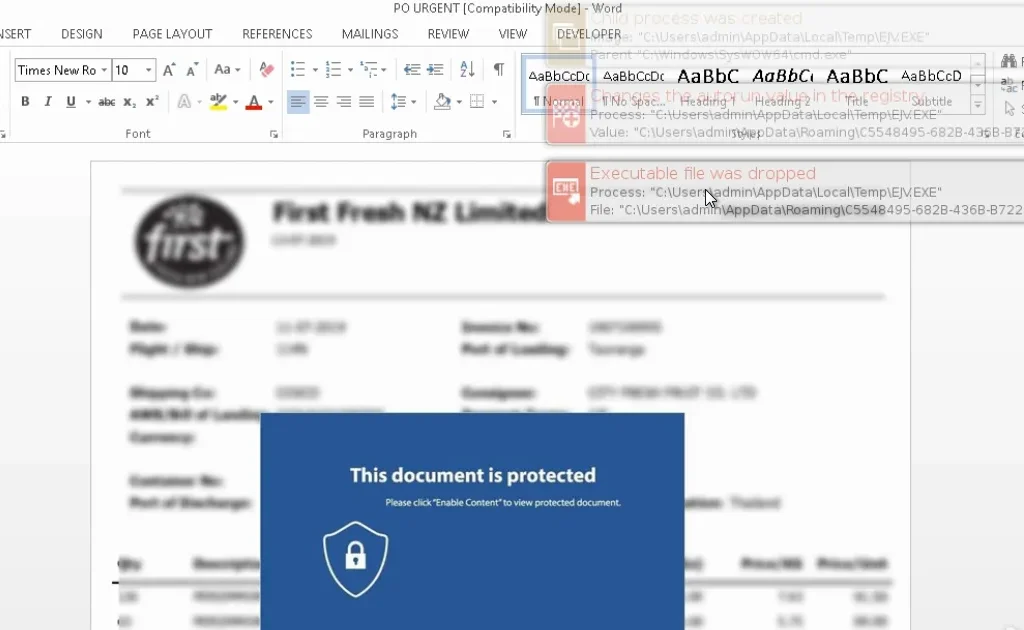
Figure 10: Malicious Word Attachment
The attachment contains a macro code, which is executed automatically when the word document is opened. The following is the behaviour of the macro code.
- A javascript file is written in the %APPDATA%\Local\Temp folder, “C:\Users\admin\AppData\Local\Temp\mczekg5e.js”, which is then executed by “wscript.exe”.
- “mczekg5e.js” writes the file “C:\Users\admin\AppData\Roaming\KQWPXSGZoR.js” and sets a custom AutoRun registry key under current user “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run” with key name “KQWPXSGZoR”. The value of the key is to execute “C:\Users\admin\AppData\Roaming\KQWPXSGZoR.js” with “wscript.exe”.
- The file “C:\Users\admin\AppData\Roaming\KQWPXSGZoR.js” is also written to Startup folder path “C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\KQWPXSGZoR.js”.
- Starts cmd.exe in %temp% folder and writes a .vbs file “C:\Users\admin\AppData\Local\Temp\B3g.vbs”. Then executes the file with “wscript.exe”. Behaviour of “B3g.vbs” is as follows –
- Writes the following files
- C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\PN6YT226\hercilio[1].exe
- C:\Users\admin\AppData\Local\Temp\EJV.EXE
- Waits for 13 seconds with timeout.exe command.
- Executes EJV.EXE, which writes the following files –
- C:\Users\admin\AppData\Roaming\C5548495-682B-436B-B722-92C4F9C95AE9\run.dat
- C:\Users\admin\AppData\Roaming\C5548495-682B-436B-B722-92C4F9C95AE9\catalog.dat
- C:\Users\admin\AppData\Roaming\C5548495-682B-436B-B722-92C4F9C95AE9\storage.dat
- C:\Users\admin\AppData\Roaming\C5548495-682B-436B-B722-92C4F9C95AE9\settings.bin
- “C:\Users\admin\AppData\Local\Temp\EJV.EXE” copies itself into the path “C:\Users\admin\AppData\Roaming\C5548495-682B-436B-B722-92C4F9C95AE9\DPI Host\dpihost.exe”
- “EJV.EXE” sets an AutoRun registry key under current user “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run” with key name “DPI Host”. The value of the key is to execute “C:\Users\admin\AppData\Roaming\C5548495-682B-436B-B722-92C4F9C95AE9\DPI Host\dpihost.exe”.
- Writes the following files
Persistence Techniques
The macro code drops a Stage One payload, which is a javascript file “C:\Users\admin\AppData\Roaming\KQWPXSGZoR.js”. Persistence during this stage is achieved by the following two methods:
Setting an AutoRun registry key “KQWPXSGZoR” under “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run” to execute “C:\Users\admin\AppData\Roaming\KQWPXSGZoR.js”.
- Writing the stage 1 payload into startup folder path “C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\KQWPXSGZoR.js”.The Stage Two payload is dropped by execution of “B3g.vbs” into “C:\Users\admin\AppData\Local\Temp\EJV.EXE”. It is also observed in the INetCache path “C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\PN6YT226\hercilio[1].exe”. This is the NanoCore RAT client. Persistence on Stage 2 is achieved by the following method:
- Setting an AutoRun registry key “DPI Host” under “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run” to execute “C:\Users\admin\AppData\Roaming\C5548495-682B-436B-B722-92C4F9C95AE9\DPI Host\dpihost.exe”.
Detection
The attack cycle outlined above can be detected based on the techniques attackers employ. Using MITRE’s ATT&CK Framework, we can break down the attacker techniques as follows.
- T1064 – Scripting: As scripting is commonly used by system administrators to perform routine tasks, any anomalous execution of legitimate scripting programs, such as PowerShell or Wscript, can signal suspicious behaviour. Checking office files for macro code can also help identify scripting used by attackers. Office processes, such as winword.exe spawning instances of cmd.exe, or script applications like wscript.exe and powershell.exe, may indicate malicious activity.
- T1060 – Registry Run Keys / Startup Folder: Monitoring Registry for changes to run keys that do not correlate with known software or patch cycles, and monitoring the start folder for additions or changes, can help detect malware. Suspicious programs executing at start-up may show up as outlier processes that have not been seen before when compared against historical data. Solutions like LMNTRIX Respond, which monitors these important locations and raises alerts for any suspicious change or addition, can help detect these behaviours.
- T1193 – Spearphishing Attachment: Network Intrusion Detection systems, such as LMNTRIX Detect, can be used to detect spearphishing with malicious attachments in transit. In LMNTRIX Detect’s case, in-built detonation chambers can detect malicious attachments based on behaviour, rather than signatures. This is critical as signature-based detection often fails to protect against attackers that frequently change and update their payloads.
Indicator of Compromise
The table below lists the Indicators of Compromise which can further help security professionals identify NanoCore activity.
| INFO | VALUE | TYPE |
|---|---|---|
| Malicious Attachment | P.O. URGENT.doc | Word Document Name |
| Malicious Attachment | 70f3125dcf765f405abea4ae1126e98b | MD5 |
| Stage 1 payload | f10b1fb2fc5f69ccc148053f930d4c66 | MD5 |
| Stage 2 payload | e2b951058ababdb4cb738342b67d0c83 | MD5 |
| Attacker Domain | kcexports.me | Domain |
| RAT Sinkhole | clinton2.duckdns.org | Domain |
| RAT Domain | pluginsrv.duckdns.org | Domain |
| RAT Domain | clintonlog.hopto.org | Domain |
| RAT Domain | prod-tp.sumo.mozit.cloud | Domain |
| RAT IP | 67.207.93.17 | IP Address |
| RAT IP | 192.169.69.25 | IP Address |
| RAT IP | 185.244.31.111 | IP Address |
Recommendations
The strategies outlined in the ‘Detection’ section above, coupled with the list of IoCs, can help security personnel identify the presence of NanoCore RAT in their networks.
LMNTRIX’s Adaptative Threat Response solution also provides complete endpoint security with detection techniques mapped to the “MITRE ATT&CK” framework. With advanced analytics, LMNTRIX XDR brings light to threats that otherwise go undetected, along with detailed analysis to provide attack attribution and mitigation. The LMNTRIX solution includes an inbuilt offline capability which uses machine learning models to classify malicious files and quickly isolates the location and determines the extent of the executable.
LMNTRIX Detect is a part of the Active Defense solution and focuses on Network Intrusion Detection. It receives numerous proprietary and open source feeds for classification of IP and domain names, and contains a detonation chamber/sandbox environment that allows for quick assessment of suspicious files entering the perimeter via network.
On 2019-08-22



[…] NanoCore RAT ofrecido gratuitamente en foros de la Dark Web (abril 2024) […]