
Version:1.0 StartHTML:000000276 EndHTML:000020624 StartFragment:000007074 EndFragment:000020556 StartSelection:000007074 EndSelection:000020540 SourceURL:https://www.lmntrix.com/Lab/Lab_info.php?id=85&url=ZeuS’%20grandson%20Atmos%20picks%20up%20the%20family%20trade LMNTRIX Labs LMNTRIX Labs
In the malware pantheon, one of the most highly revered strains is ZeuS – a banking trojan that was particularly virulent in the mid-to-late 2000s. The source code was being sold online for years until it was leaked in 2011 which led to ZeuS becoming the progenitor of multiple malware strains including Citadel, from which the current strain of Atmos malware is based. In a sense, ZeuS is Atmos’ grandfather.
Atmos usually targets banks and is run off the back of a huge botnet which pulls the malware’s strings from the command and control (C&C) server. While at heart a banking trojan, Atmos also has personal information in its sights.
Like ZeuS, one of Atmos’ (and Citadel’s before it) main features is Web injection which is the ability to modify banking websites and serve up rogue Web forms which asks victims for sensitive information, like credit card details. Also like Zeus, Atmos includes key logger capabilities which allows attackers to record key strokes during username and password input phases.
Atmos Infection and Sales Cycle
Atmos is initiated when a user feeds their login details to a compromised website. While the data is sent to the webserver, it is also sent to Atmos’ C&C server, giving the attacker the victim’s login details:
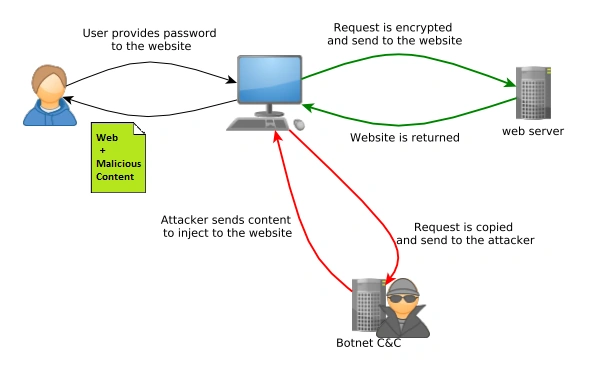
Figure 1 Botnet Internal
At its peak, Citadel’s developer operated a 7,000 strong botnet primarily with Russian computers. He was arrested by the FBI in 2015. That Citadel botnet variant contained personal information including online banking credentials, credit card information, and other personally identifying data.
The below image shows the Citadel bot builder which was used to create the customized botnet sample. Later versions included the ability to avoid AV detection.
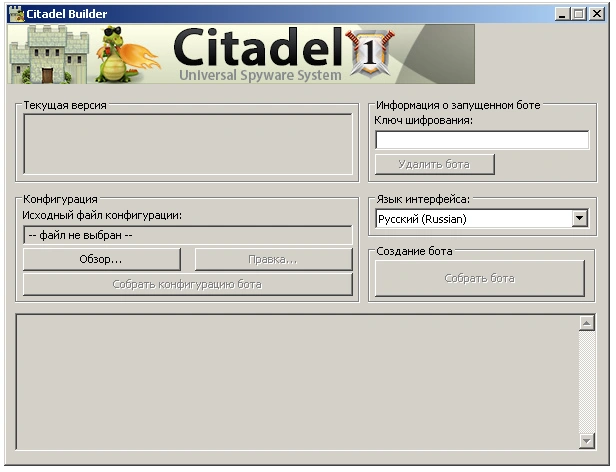
Figure 2 Citadel Bot Builder
Returning to the current Atmos strain, below is the bot builder interface:
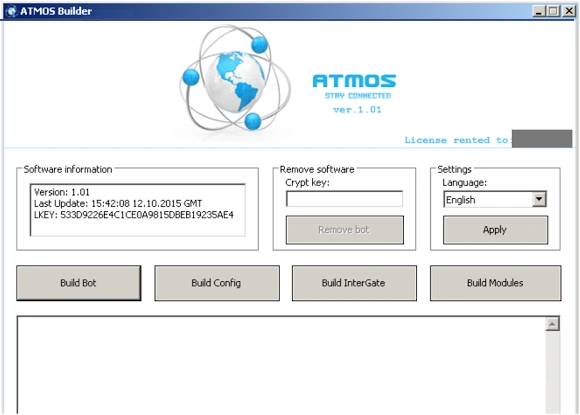
Figure 3 Atmos Builder
Below, the Atmos’ authors include the malware’s features in their sales pitch:
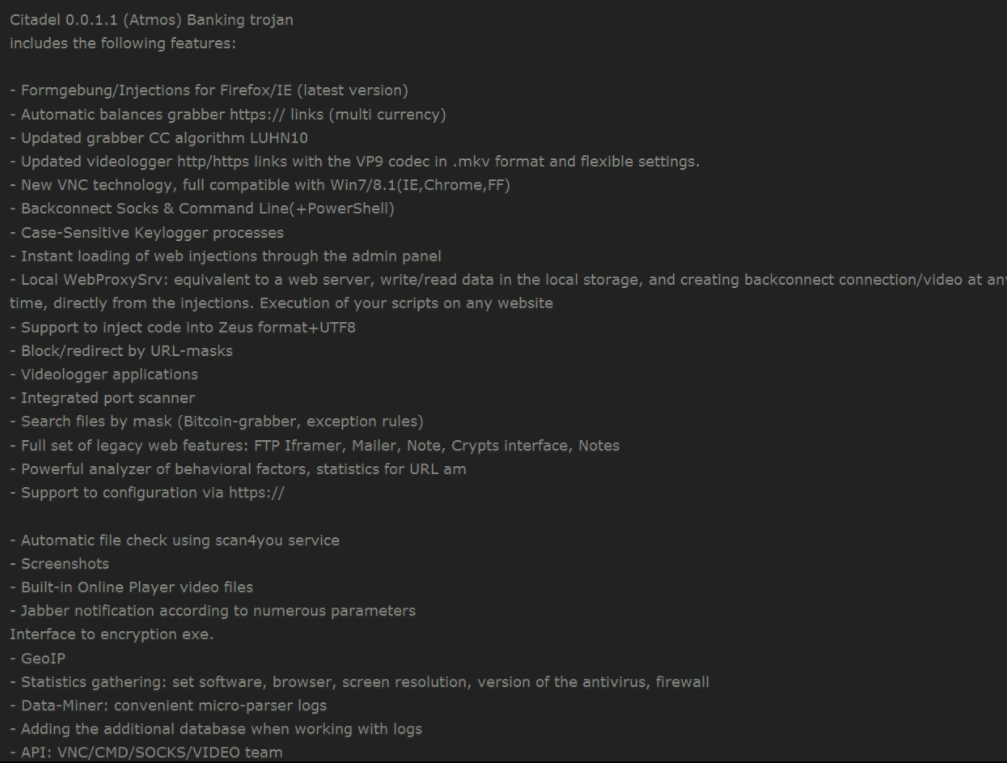
Figure 4 Citadel (Atmos) Features
While the above list, surprisingly, doesn’t include a purchase price, we saw Atmos for sale between USD$2,000 and USD$6,000 last year:
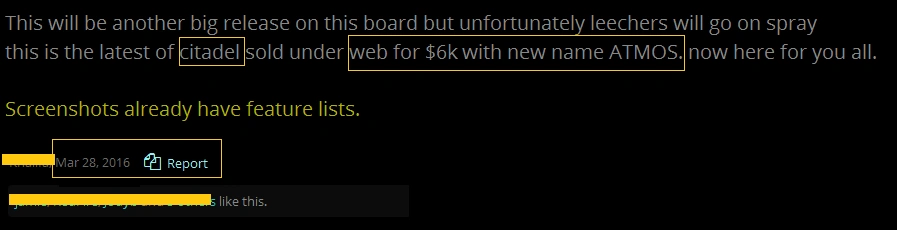
Figure 5 Price of Atmos (March 2016)
Country Stats
Atmos’ authors are indiscriminate in the countries they target. We have witnessed multiple infection methods, including spam campaigns and Web injection. The following image shows which countries make up Atmos’ botnet:
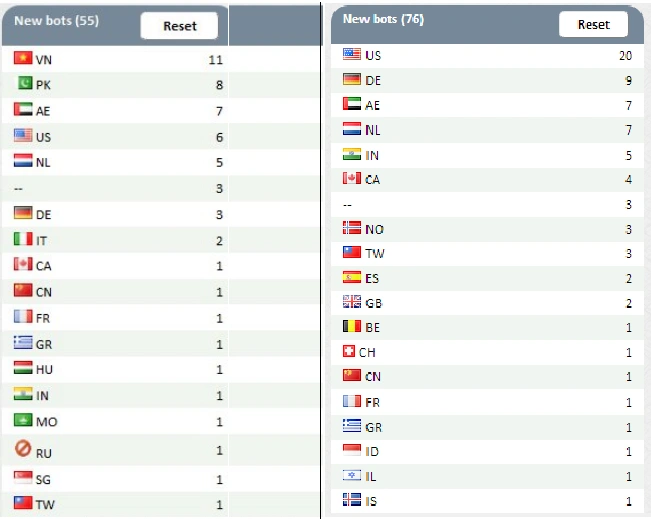
Figure 6 Atmos targeted countries
Analysis of recent Atmos sample
The sample we’ll analyse today was discovered earlier this month:
Sample detail:
MD5: 4b9660441358264519b645e91a485e0b
Size: 264 KB
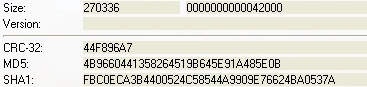
Figure 7 File detail
File Analysis
In our controlled environment, we checked the sample’s strings and found mostly junk:
• 000000019115 000000419D15 0 yGK;G
• 000000019253 000000419E53 0 GK;Y?gK
• 00000001935F 000000419F5F 0 8jG+xY
• 0000000194A3 00000041A0A3 0 GsIc9
• 000000019836 00000041A436 0 |G+xI
• 0000000198FE 00000041A4FE 0 EG(8′
• 000000019D5C 00000041A95C 0 yGK;G
We then debugged the code and started to uncover important strings:
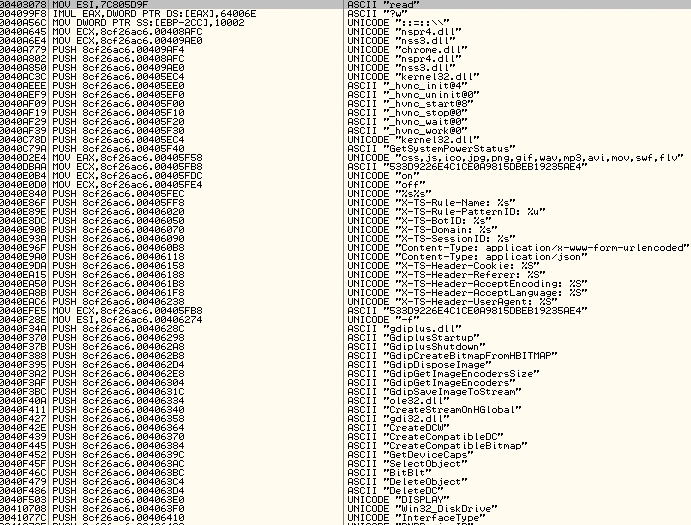
Figure 8 Strings in the memory
The above image shows important identifying strings which our researchers found were related to earlier Atmos samples for which we already had the yara signatures. Those strings are below:
• ASCII “_hvnc_init@4”
• ASCII “_hvnc_uninit@0”
• ASCII “_hvnc_start@8”
• ASCII “_hvnc_stop@0”
• ASCII “_hvnc_wait@0”
• ASCII “_hvnc_work@0”
• UNICODE “css,js,ico,jpg,png,gif,wav,mp3,avi,mov,swf,flv”
• ASCII “533D9226E4C1CE0A9815DBEB19235AE4”
In this set, we found “_hvnc_init” which is just hidden vnc routine. Below, we checked this against the earlier sample’s yara rule:
// Hidden VNC identifiers
$VNC1 = “_hvnc_init@4” wide ascii
$VNC2 = “_hvnc_uninit@0” wide ascii
$VNC3 = “_hvnc_start@8” wide ascii
$VNC4 = “_hvnc_stop@0” wide ascii
$VNC5 = “_hvnc_wait@0” wide ascii
$VNC6 = “_hvnc_work@0” wide asci
Our sample’s strings also contained browser identifiers:
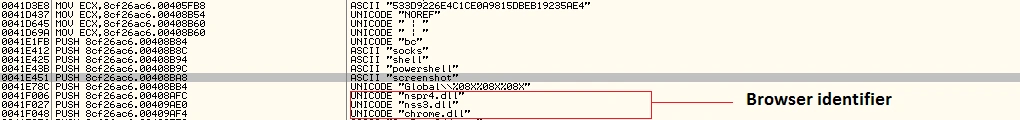
Figure 9 Browser identifiers
In addition to browser identifiers, we uncovered strings related to social networking sites Twitter, Facebook and Instagram, as well as the details of botnet domains from Russia, Ukraine, and Kazakhstan.
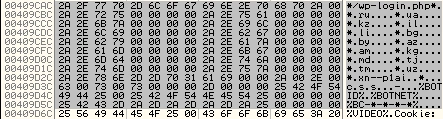
Figure 10 Botnet and Domains from Russia and its neighbouring countries
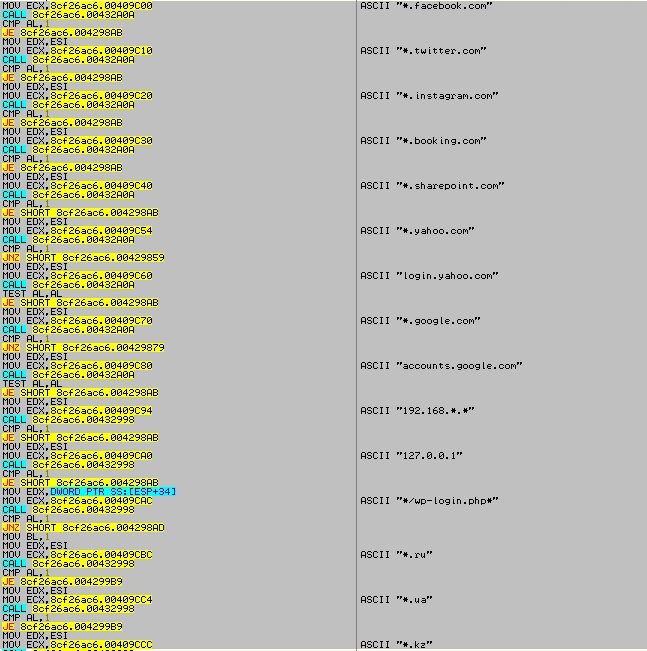
Figure 11 Sites found inside the code
The actual files created, and the domains contacted, were found inside the code itself:
• 0012F914 00 00 00 00 00 00 00 00 00 00 57 6F 63 6F 76 79 ……….Wocovy
• 0012F924 61 74 76 61 65 5C 79 7A 69 68 6D 6F 73 61 66 69 atvae\yzihmosafi
• 0012F934 2E 65 78 65 00 00 00 00 4B 69 69 78 73 79 6F 68 .exe….Kiixsyoh
• 0012F944 6D 75 6F 68 5C 79 62 68 6F 79 77 70 65 2E 79 64 muoh\ybhoywpe.yd
• 0012F954 73 00 00 00 00 00 45 66 62 6F 69 64 65 76 6B 5C s…..Efboidevk\
• 0012F964 6C 69 75 77 64 65 70 79 77 2E 67 61 74 00 00 00 liuwdepyw.gat…
• 0012F974 00 00 00 00 43 6F 70 61 61 78 75 73 00 00 00 00 ….Copaaxus….
• 0012F994 00 00 45 71 66 79 69 7A 00 00 00 00 4F 76 6F 74 …Eqfyiz….Ovot
• 0012F9A4 6D 6F 68 00 00 00 4F 6B 65 71 69 00 00 00 00 00 moh…Okeqi…..
• 0012F9B4 42 69 72 6F 78 79 62 65 00 00 5A 75 6F 6B 6F 7A Biroxybe..Zuokoz
• 0012F9C4 74 79 00 00 49 6D 76 65 63 6F 76 6F 75 00 18 F2 ty..Imvecovou.ò
• 0012F9D4 44 55 AA 54 3C 7A 13 00 B8 52 75 6E 6E 69 6E 67 DUªT<z.¸Running
• 0012FA34 74 74 70 3A 2F 2F 72 65 73 76 73 68 6F 70 2E 72 ttp://resvshop.r
• 0012FA44 75 2F 64 45 46 79 70 34 73 4A 50 5A 66 70 2F 66 u/dEFyp4sJPZfp/f
• 0012FA54 69 6C 65 2E 70 68 70 7C 66 69 00 00 00 00 73 61 ile.php|fi….sa
• 0012FA64 2E 78 6D 6C 00 .xml.
Dynamic analysis
We switched to dynamic analysis in order to observe the complete behaviour of the sample. First, we witnessed the file deleting itself after execution:
Figure 12 Duplicate file created in %appdata%
Then the following registry traces were created in the system:
• HKEY_CURRENT_USER\Software\Microsoft\Eqfyiz
• HKEY_CURRENT_USER\Software\Microsoft\Internet Account Manager\Accounts\Active Directory GC
• HKEY_CURRENT_USER\Software\Microsoft\Internet Account Manager\Accounts\Bigfoot
• HKEY_CURRENT_USER\Software\Microsoft\Internet Account Manager\Accounts\VeriSign
• HKEY_CURRENT_USER\Software\Microsoft\Internet Account Manager\Accounts\WhoWhere
Below is the sample’s auto start entry:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “Copaaxus”
Type: REG_SZ
Data: “C:\Documents and Settings\Application Data\Wocovyatvae\yzihmosafi.exe”
The physical location of the file is our original file’s duplicate MD5. This registry enables the malware to maintain persistence.
Below are the folders the malware creates:
• c:\Documents and Settings\Application Data\Efboidevk
• c:\Documents and Settings\Application Data\Kiixsyohmuoh
• c:\Documents and Settings\Application Data\Microsoft\Address Book
• c:\Documents and Settings\Application Data\Wocovyatvae
Inside the ‘Microsoft’ folder, under the newly created ‘Address Book’ folder, is an address book file %username%.wab.
IOC Details:
Based on our dynamic analysis we found the registry traces, folders and file traces created. These traces can be used to detect the malware’s presence in the host:
URLs:
• 0012FC90 68 74 74 70 3A 2F 2F 31 39 33 2E 30 2E 31 37 38 http://193.0.178
• 0012FCA0 2E 31 38 2F 64 45 46 79 70 34 73 4A 50 5A 66 70 .18/dEFyp4sJPZfp
• 0012FCB0 2F 66 69 6C 65 2E 70 68 70 7C 66 69 6C 65 3D 75 /file.php|file=u
• 0012FCC0 73 61 2E 78 6D 6C sa.xml
• 0012FA34 74 74 70 3A 2F 2F 72 65 73 76 73 68 6F 70 2E 72 ttp://resvshop.r
• 0012FA44 75 2F 64 45 46 79 70 34 73 4A 50 5A 66 70 2F 66 u/dEFyp4sJPZfp/f
• 0012FA54 69 6C 65 2E 70 68 70 7C 66 69 00 00 00 00 73 61 ile.php|fi….sa
• 0012FA64 2E 78 6D 6C 00 .xml.
• hxxp://193.0.178(.)18/dEFyp4sJPZfp/file.php|file=usa.xml
• hxxp://resvshop(.)ru/dEFyp4sJPZfp/file.php|file=usa.xml
Yara rules for detection:
$LKEY = “533D9226E4C1CE0A9815DBEB19235AE4” wide ascii
// TokenSpy identifiers
$TokenSpy1 = “X-TS-Rule-Name: %s” wide ascii
$TokenSpy2 = “X-TS-Rule-PatternID: %u” wide ascii
$TokenSpy3 = “X-TS-BotID: %s” wide ascii
$TokenSpy4 = “X-TS-Domain: %s” wide ascii
$TokenSpy5 = “X-TS-SessionID: %s” wide ascii
$TokenSpy6 = “X-TS-Header-Cookie: %S” wide ascii
$TokenSpy7 = “X-TS-Header-Referer: %S” wide ascii
$TokenSpy8 = “X-TS-Header-AcceptEncoding: %S” wide ascii
$TokenSpy9 = “X-TS-Header-AcceptLanguage: %S” wide ascii
$TokenSpy10 = “X-TS-Header-UserAgent: %S” wide ascii
// Browser identifiers
$WebBrowser1 = “nspr4.dll” wide ascii
$WebBrowser2 = “nss3.dll” wide ascii
$WebBrowser3 = “chrome.dll” wide ascii
$WebBrowser4 = “Internet Explorer” wide ascii
$WebBrowser5 = “Firefox” wide ascii
$WebBrowser6 = “Chrome” wide ascii
// Hidden VNC identifiers
$VNC1 = “_hvnc_init@4” wide ascii
$VNC2 = “_hvnc_uninit@0” wide ascii
$VNC3 = “_hvnc_start@8” wide ascii
$VNC4 = “_hvnc_stop@0” wide ascii
$VNC5 = “_hvnc_wait@0” wide ascii
$VNC6 = “_hvnc_work@0” wide asci
This set of strings can also be used to detect the malware’s presence in the host.
Conclusion
We recommend blocking the malicious domain in the proxy and firewall. The above yara rules can also be used to perform a scan on host machines.
In a SOC perspective, it is highly recommended to add the malicious domains to the threat intelligence feed so alerts can be created if any events match with the presence of those malicious domains in the network.


