Frequently Asked Questions
Everything You Need to Know About LMNTRIX
About LMNTRIX
What is LMNTRIX?
LMNTRIX is a cybersecurity company that specializes in advanced threat detection and response services, offering solutions to help organizations protect against cyber threats. The company is known for its Managed Extended Detection and Response (MXDR) platform, which integrates various security functions, threat intelligence, and human expertise to provide comprehensive protection across an organization’s network.
LMNTRIX’s approach combines Active Defense strategies, which include proactive threat hunting, adversarial exposure validation, and incident response, to detect and neutralize cyber threats that traditional security controls miss. Unlike many of its competitors, LMNTRIX operates independently without venture capital backing, allowing it to focus on innovation and tailor its solutions to customer needs without the external pressures of investors.
The company’s solutions are designed to be deployed quickly, with minimal disruption, and are aimed at enterprises looking for a robust cybersecurity posture without the complexity and overhead associated with traditional security operations centers (SOCs).
Who owns LMNTRIX?
LMNTRIX is owned by Carlo Minassian, who is the founder and CEO of the company. Carlo Minassian established LMNTRIX as a private cybersecurity firm that operates independently, without venture capital backing or public listing, allowing the company to maintain control over its strategic direction and innovation pace. Minassian’s approach focuses on building and developing LMNTRIX’s technology and business without external pressures from investors or a board, which aligns with his philosophy of focusing on long-term growth and enjoying the process of building a business.
When was LMNTRIX founded?
LMNTRX was founded in 2015.
What is the history and background of LMNTRIX?
LMNTRIX is a cybersecurity company specializing in advanced threat detection and response solutions. Founded by Carlo Minassian in 2015, the company aims to help organizations protect themselves against sophisticated cyber threats that traditional security measures overlook.
Founding and Early History
- Carlo Minassian’s Background: Before establishing LMNTRIX, Carlo Minassian was a well-known figure in the cybersecurity industry. He founded earthwave, an Australian managed security services provider (MSSP), which was acquired by Dimension Data (now part of NTT Ltd.) in 2013. His experience with earthwave provided him with valuable insights into the limitations of existing log/SIEM based SOC solutions.
- Establishment of LMNTRIX (2015): Recognizing the evolving landscape of cyber threats and the need for more advanced detection capabilities, Minassian founded LMNTRIX. The company’s mission was to develop a platform that could automatically detect, investigate, and respond to advanced persistent threats (APTs) and sophisticated cyber-attacks that are routinely missed by existing security controls
Mission and Vision
- Mission: To empower organizations with the tools and expertise necessary to detect and respond to advanced cyber threats in real-time, minimizing potential damage and ensuring business continuity.
- Vision: To redefine cybersecurity by providing a unified, adaptive security architecture that evolves with emerging threats and integrates seamlessly with existing infrastructures.
Technological Innovations
- LMNTRIX XDR Platform:
- Multi-Layered Defense: The XDR platform combines multiple security technologies and methodologies to provide comprehensive protection from endpoint to the cloud. It natively integrates network traffic analysis, endpoint detection and response, deception technologies, cloud and mobile security together with threat intelligence.
- Advanced Analytics: Utilizes machine learning and behavioral analytics to identify anomalous activities and potential threats that traditional signature-based systems might miss.
- Unified Visibility: Offers a centralized dashboard for monitoring and managing security events across the entire IT environment.
- Managed Detection and Response (MDR):
- Provides 24/7 monitoring and threat detection services.
- Employs skilled security analysts for proactive threat hunting and rapid incident response.
- Managed Extended Detection and Response (MXDR):
- Extends detection and response capabilities across endpoints, networks, mobile, cloud services, and applications.
- Enhances visibility and control over a broader range of assets and potential attack vectors.
Growth and Expansion
- Client Base: Since its inception, LMNTRIX has expanded its services globally, catering to organizations of various sizes across multiple industries, including finance, healthcare, government, and retail.
- Global Presence: Headquartered in California, USA, LMNTRIX has established offices and operations in regions such as North America, Europe, India, the Middle East, and the Asia-Pacific.
- Partnerships and Collaborations:
- Collaborates with other technology vendors and cybersecurity firms to enhance its service offerings.
- Engages in information sharing with industry groups to stay ahead of emerging threats.
Industry Recognition
- Thought Leadership:
- LMNTRIX frequently publishes research papers, blogs, and reports on cybersecurity trends and threats.
- The company’s experts are often invited to speak at industry conferences and events.
- Certifications and Compliance:
- Complies with international security standards and regulations, such as SOC2, PCI DSS, ISO 27001 and GDPR.
- Assists clients in meeting their regulatory compliance requirements through detailed reporting and audit support.
Commitment to Innovation
- Research and Development:
- Continuously invests in R&D to enhance its platforms and services.
- Focuses on integrating artificial intelligence and machine learning to improve threat detection accuracy and reduce false positives.
- Adaptive Security Architecture:
- The LMNTRIX XDR platform is designed to be adaptive, meaning it evolves with the threat landscape.
- Regular updates and improvements ensure that clients are protected against the latest cyber threats.
Community and Social Responsibility
- Education and Training:
- Provides training and resources to clients to improve their internal security awareness and capabilities.
- Supports initiatives to educate the broader community about cybersecurity best practices.
- Workforce Diversity:
- Promotes diversity and inclusion within the company, recognizing that a variety of perspectives strengthens their ability to innovate and solve complex problems.
LMNTRIX has established itself as a significant player in the cybersecurity industry by focusing on advanced threat detection and response. With a strong foundation built on the expertise of its founder, Carlo Minassian, the company addresses the challenges posed by sophisticated cyber threats through innovative technologies and services. LMNTRIX continues to evolve its offerings to meet the changing needs of organizations worldwide, helping them safeguard their critical assets and maintain operational resilience.
What are the core values and mission of LMNTRIX?
LMNTRIX is a trailblazing company in the field of autonomous cybersecurity, dedicated to protecting organizations from sophisticated and constantly evolving cyber threats. Our mission is to defeat every cyber attack, every second of every day, recognizing that the digital landscape is perpetually changing and that adversaries are increasingly leveraging automation and advanced technologies.
Mission
At the core of LMNTRIX’s mission is a commitment to proactive innovation rather than passive reaction. They understand that traditional security measures are no longer sufficient against modern cyber threats. By continuously evolving our technology and expertise, LMNTRIX aims to stay several steps ahead of attackers. Our goal is to provide organizations with instant and effective defense mechanisms that operate at unparalleled speed, scale, and accuracy.
XDR Platform
One of the key innovations from LMNTRIX is the XDR Platform. This state-of-the-art solution is designed to:
- Instantly Defend Against Cyberattacks: Offering real-time protection that can outpace human capabilities.
- Operate at Unmatched Speed and Scale: Capable of handling vast amounts of data and complex threats more efficiently than traditional methods.
- Deliver Higher Accuracy: Reducing false positives and ensuring that genuine threats are identified and addressed promptly.
The XDR Platform embodies LMNTRIX’s forward-thinking approach, leveraging technologies that seem futuristic because we designed it to combat the threats of tomorrow as well as today.
Core Values
LMNTRIX’s operations are guided by a set of core values that reflect their commitment to excellence and ethical practices:
- Dependability: Being a reliable partner for our clients, consistently delivering on promises.
- Integrity: Upholding the highest ethical standards in all interactions and decisions.
- Passion for Team Success: Fostering a collaborative environment where collective achievements are celebrated.
- Unwavering Purpose: Maintaining a steadfast focus on our mission to protect against cyber threats.
- Determination: Persistently pursuing innovation and excellence despite challenges.
- Kindness: Treating colleagues, clients, and the broader community with respect and consideration.
These values underscore LMNTRIX’s belief in teamwork and the importance of considering the impact of our actions on others. Our passion for cybersecurity drives us to push technological boundaries and deliver exceptional solutions.
Dedication to Protecting Critical Infrastructure
LMNTRIX is committed to securing the essential elements of modern infrastructure:
- Data: Safeguarding sensitive information from unauthorized access and breaches.
- Systems: Protecting the platforms that store, process, and share data to ensure operational continuity.
We serve a diverse clientele, including major corporations, government agencies, healthcare providers, and educational institutions. By offering solutions that enhance defenses while simplifying complexity, LMNTRIX helps these organizations navigate the challenging cybersecurity landscape with confidence.
Not Just a Cybersecurity Company
In essence, LMNTRIX is more than a traditional cybersecurity firm. We are a team of innovators and problem-solvers who are deeply committed to:
- Staying Ahead of Evolving Threats: Continuously updating our technologies to counter new forms of cyber attacks.
- Empowering Organizations: Providing tools and expertise that enable clients to operate securely in an increasingly digital world.
- Advancing the Field of Cybersecurity: Contributing to the broader community through thought leadership and collaboration.
Our dedication goes beyond merely offering services; we strive to make a meaningful impact by enhancing the overall security posture of the organizations we work with.
LMNTRIX’s mission and core values reflect a profound commitment to protecting the digital assets of organizations worldwide. By combining cutting-edge technology with a passionate team and a clear set of guiding principles, we aim to provide unparalleled cybersecurity solutions. Our approach is characterized by proactive innovation, ethical practices, and a deep understanding of the evolving nature of cyber threats. Through our work, LMNTRIX seeks to ensure that businesses, governments, and institutions can focus on their objectives without compromising on security.
Who are LMNTRIX’s competitors?
SentinelOne and CrowdStrike are widely recognized as leading solutions in the Endpoint Detection and Response (EDR) and Endpoint Protection Platform (EPP) market. However, LMNTRIX offers a compelling alternative with its advanced cybersecurity platform that has demonstrated exceptional performance in client proof-of-concept (POC) and proof-of-value (POV) engagements. Organizations looking for robust security solutions may find LMNTRIX to be a superior option in several key areas.
LMNTRIX’s Competitive Advantages
- Autonomous Single-Agent XDR Platform:
- Comprehensive Security Functions: LMNTRIX provides an Extended Detection and Response (XDR) platform that integrates 12 security functions into a single agent. This unified approach simplifies deployment and management while enhancing overall security coverage.
- Best-in-Industry OS Coverage: The platform supports Linux, macOS, Windows, iOS, Android and Chromebook operating systems, ensuring consistent protection across diverse IT environments.
- Cost-Effective MDR Services Included:
- Managed Detection and Response (MDR) at No Additional Cost: Unlike some competitors, LMNTRIX includes MDR services without extra fees, often at a price point lower than the licensing costs of other vendors. This makes advanced cybersecurity more accessible and budget-friendly. All subscriptions come standard with unlimited Digital Forensics and Incident Response (DFIR), containment, remediation, and threat hunting. This comprehensive coverage eliminates the need for third-party incident response retainer services that often remain unused.
- Value Proposition: Organizations receive both the software and expert monitoring services bundled together, maximizing return on investment.
- Autonomous Detection Without Reliance on Cloud or Human Analysts:
- Active EDR Agent: LMNTRIX’s solution operates effectively without constant cloud connectivity or dependence on human analysts for threat detection and response.
- On-Device and Network Analysis: The platform performs pre-execution and on-execution analysis directly on devices and networks, enabling real-time protection against known and unknown threats.
- Third-Party Security Integrations: Seamlessly integrates with existing security controls, enhancing the overall security posture without overhauling current systems.
- Proven Threat Detection Efficacy:
- Superior Performance in POCs/POVs: In active client evaluations, LMNTRIX has consistently detected threats that some other leading vendors have missed. This track record highlights the platform’s advanced threat detection capabilities.
LMNTRIX MXDR offers a robust and cost-effective cybersecurity solution that stands out in the market due to its autonomous, single-agent XDR platform and inclusive MDR services. Its ability to detect threats without relying on cloud connectivity or human analysts provides a significant advantage, especially for organizations operating in environments with limited internet access or those seeking to reduce dependency on external analysis.
While SentinelOne and CrowdStrike are established leaders in the EDR/EPP space, LMNTRIX has demonstrated superior performance in certain client engagements by consistently identifying threats that others have missed. Organizations seeking to enhance their cybersecurity posture may benefit from considering LMNTRIX as a viable alternative.
Next Steps
- Request a Demo or POC: Engage with LMNTRIX to experience the platform’s capabilities firsthand.
- Compare Solutions: Conduct a thorough evaluation comparing LMNTRIX with other vendors to determine the best fit for your organization’s needs.
- Assess Total Cost of Ownership: Consider both licensing fees and additional services like MDR when calculating overall costs.
Managed Extended Detection & Response (MXDR)
What is LMNTRIX MDR?
LMNTRIX MDR stands for LMNTRIX Managed Detection and Response, a comprehensive cybersecurity service offered by LMNTRIX. This service is designed to help organizations detect, investigate, and respond to cyber threats that traditional security measures might miss.
Key Features of LMNTRIX MDR:
- Advanced Threat Detection: Utilizes a combination of machine learning, behavioral analytics, and threat intelligence to identify both known and unknown threats across your network, endpoints, and cloud environments.
- 24/7 Monitoring: Provides continuous, around-the-clock monitoring of your IT infrastructure to quickly identify suspicious activities and potential security incidents in real-time.
- Threat Hunting: Employs skilled security analysts who proactively search for hidden threats and adversaries within your systems that automated tools may overlook.
- Rapid Incident Response: Offers immediate action to contain and remediate threats, minimizing potential damage and downtime.
- Security Analytics and Reporting: Delivers detailed analytics and customizable reports that provide insights into your security posture, compliance status, and areas for improvement.
- Integration with Existing Systems: Seamlessly integrates with your current security tools and technologies to enhance overall effectiveness without requiring a complete overhaul.
Benefits of Using LMNTRIX MDR:
- Enhanced Security Posture: Improves your organization’s ability to detect and respond to sophisticated cyber threats.
- Cost-Effective: Reduces the need for significant in-house security investments by leveraging LMNTRIX’s expertise and resources.
- Scalable Solutions: Adapts to the size and needs of your organization, whether you’re a small business or a large enterprise.
- Expert Support: Gains access to a team of cybersecurity professionals with specialized knowledge and experience.
LMNTRIX MDR is particularly valuable for organizations that may lack extensive in-house cybersecurity capabilities but recognize the need for robust threat detection and response mechanisms. By outsourcing these critical functions to LMNTRIX, organizations can focus on their core business activities while maintaining a strong security posture against evolving cyber threats.
For more detailed information or to explore how LMNTRIX MDR can benefit your organization, you may visit the LMNTRIX official website or contact their sales team directly.
What is LMNTRIX MXDR?
LMNTRIX MXDR stands for Managed Extended Detection and Response, a comprehensive cybersecurity service offered by LMNTRIX. It builds upon traditional Managed Detection and Response (MDR) by extending capabilities across multiple security layers, providing a more holistic approach to threat detection and response.
Key Features of LMNTRIX MXDR:
- Unified Security Platform: Integrates data from endpoints, networks, cloud services, and applications to offer a centralized view of your security posture.
- Advanced Threat Detection: Employs machine learning, behavioral analytics, and threat intelligence to identify sophisticated cyber threats, including zero-day attacks and advanced persistent threats (APTs).
- Proactive Threat Hunting: Security experts actively search for hidden threats and vulnerabilities within your environment that automated systems might miss.
- Automated Response and Remediation: Utilizes automation to quickly contain and neutralize threats, reducing the time attackers have to cause damage.
- Continuous Monitoring: Offers 24/7 surveillance of your IT infrastructure to detect anomalies in real-time.
- Scalable and Flexible Solutions: Adapts to the specific needs and size of your organization, whether on-premises, in the cloud, or hybrid environments.
Benefits of Using LMNTRIX MXDR:
- Comprehensive Security Coverage: Extends beyond endpoints to include networks, cloud services, and applications, providing a more complete defense strategy.
- Reduced Complexity: Simplifies security management by consolidating multiple tools and services into a single, cohesive platform.
- Faster Incident Response: Minimizes response times through automation and expert intervention, limiting potential damage.
- Expert Support: Gains access to a team of seasoned cybersecurity professionals for analysis, support, and guidance.
- Regulatory Compliance: Assists in meeting various compliance standards by maintaining detailed logs and reports of security activities.
Why Choose LMNTRIX MXDR?
In today’s complex cyber landscape, threats can come from anywhere and target any part of your IT environment. LMNTRIX MXDR is designed to address these challenges by providing:
- Extended Visibility: Monitors a wide array of data sources to ensure no threat goes unnoticed.
- Adaptive Security Measures: Continuously updates its threat detection algorithms to adapt to emerging cyber threats.
- Cost Efficiency: Eliminates the need for multiple security vendors and tools, potentially lowering overall security expenditures.
For organizations seeking a robust and adaptive security solution, LMNTRIX MXDR offers the tools and expertise necessary to protect against advanced cyber threats effectively.
To learn more about how LMNTRIX MXDR can enhance your organization’s cybersecurity posture, visit the LMNTRIX official website or reach out to their sales team for a personalized consultation.
What is Active Defense?
Reinventing Cyber Defense with First Principles Thinking
At LMNTRIX, we’ve revolutionized cyber defense by embracing a First Principles Thinking approach. By deconstructing the complexities of cybersecurity to their most fundamental truths, we’ve crafted a solution built from the ground up—free from outdated assumptions. Instead of relying on traditional log or SIEM-based methods to build a SOC, we asked ourselves:
“What are the undeniable facts we know to be true?”
From these core truths, we engineered an innovative solution that challenges conventional norms.
Assuming Breaches to Stay Ahead
A fundamental principle of LMNTRIX Active Defense is the assumption that existing security controls can be easily bypassed. We don’t rely on them for threat detection. Instead, any logs collected from your current security measures are used solely for Digital Forensics and Incident Response (DFIR).
Detecting the Undetectable Across All Vectors
We deploy advanced techniques to identify threats that routinely evade traditional security controls across multiple threat vectors—including APT, email, web, network, endpoint, cloud, mobile, and encrypted attacks. Our exclusive focus is on threats that penetrate your defenses, not those that are blocked. Without collecting any logs from your environment, we layer in our own detections. This empowers our platform and team to validate and investigate every single threat that slips past your existing security controls.
LMNTRIX Active Defense is based on multiple Detective, Responsive, and Predictive capabilities that integrate and share information to build a security protection system that is more adaptive and intelligent than any one element. The constant exchange of intelligence between the XDR components and the broader cybersecurity community enables LMNTRIX to keep abreast of the tactics, techniques, and procedures (TTPs) of the most persistent, well-resourced, and skilled attack groups.
Automated Incident Response Lifecycle
We handle the entire Incident Response (IR) lifecycle for you, much of which is automated. Every threat is validated, investigated, contained, and remediated swiftly and effectively.
Exceptional Results You Can Trust
- 95% Reduction in False Positives: Focus on real threats without the noise.
- Rapid Detection and Containment: Over 90% of incidents are detected in under 1 minute and contained within 30 minutes.
Measurable Risk Reduction
What does this mean for you? A significant decrease in risk. On average, we detect 30-60 threats per client each month that go completely unnoticed by existing log or SIEM-based SOCs and MSSPs.
How good is LMNTRIX?
LMNTRIX is regularly apprised by industry-leading analyst firms and independent 3rd party testing such as:
- In 2024, recognised as a MDR Leader by IDC.
- In 2023, covered in 8 Gartner research reports and one of 20 vendors globally recognised in the Gartner MDR market guide.
- In 2022, covered in Forrester Landscape Reports for MSSP and NAV
- In 2023, ranked #19 on MSSP Alert from global Top 250 MSSPs
LMNTRIX is highly regarded for its MXDR services, receiving excellent reviews for its proactive threat detection and response capabilities. It is praised for cutting out the inefficiencies of traditional SIEM systems, minimizing false positives, and focusing on a proactive, adversarial approach. LMNTRIX Active Defense has an average rating of 5 out of 5 on Gartner Peer Reviews and 9.8 out of 10 on PeerSpot and is favored by enterprises for its effectiveness in monitoring and validating threats before alerts are generated, reducing alert fatigue and improving response times.
The company is particularly noted for its high level of customer satisfaction, with many users recommending it for its robust security insights and fast incident response capabilities.
Analysts are drowning in data and simply aren’t able to keep up with sophisticated attack vectors. LMNTRIX helps turn data into validated incidents, so analysts can focus on the alerts that matter most.
What is LMNTRIX used for?
LMNTRIX is a cybersecurity company that specializes in advanced threat detection and response solutions. Organizations use LMNTRIX to enhance their cybersecurity posture by effectively identifying, investigating, and responding to sophisticated cyber threats that traditional security measures might miss.
Primary Uses of LMNTRIX:
- Advanced Threat Detection and Response:
Both of these capabilities can either replace or complement existing SOC investments.
- Managed Detection and Response (MDR): LMNTRIX offers MDR services that provide 24/7 monitoring of an organization’s IT environment. This service detects real-time threats and responds swiftly to security incidents.
- Managed Extended Detection and Response (MXDR): Building upon MDR, MXDR extends capabilities across multiple security layers—endpoints, networks, cloud services, and applications—for a more comprehensive defense strategy.
- Proactive Threat Hunting:
- Security experts at LMNTRIX actively search for hidden threats and vulnerabilities within your systems that automated tools might overlook. This proactive approach helps in early detection and mitigation of potential risks.
- Incident Response and Remediation:
- Offers rapid containment and remediation services to minimize damage and downtime in the event of a security breach. This includes isolating affected systems, eliminating threats, and restoring normal operations.
- Security Analytics and Reporting:
- Provides detailed analytics, dashboards, and customizable reports that offer insights into your security posture, compliance status, and areas for improvement. This helps organizations make informed decisions about their cybersecurity strategies.
- Integration with Existing Security Infrastructure:
- LMNTRIX solutions are designed to integrate seamlessly with your current security tools and technologies, enhancing overall effectiveness without the need for a complete system overhaul.
- Regulatory Compliance Support:
- Assists organizations in meeting various regulatory compliance requirements by maintaining detailed logs and reports of security activities, which are essential for audits and assessments.
Benefits of Using LMNTRIX:
- Enhanced Security Posture: Improves your organization’s ability to detect and respond to advanced cyber threats, including zero-day exploits and advanced persistent threats (APTs).
- Expertise Access: Provides access to a team of seasoned cybersecurity professionals with specialized knowledge and experience.
- Cost Efficiency: Reduces the need for substantial in-house security investments by leveraging LMNTRIX’s resources and expertise.
- Scalability: Offers solutions that adapt to the size and specific needs of your organization, suitable for both small businesses and large enterprises.
- Operational Focus: Allows your internal teams to focus on core business activities while LMNTRIX manages the complexities of cybersecurity.
In Summary:
Organizations use LMNTRIX to strengthen their defenses against a wide array of cyber threats. By leveraging advanced technologies like machine learning and behavioral analytics, along with expert human analysis, LMNTRIX helps organizations:
- Detect threats that traditional security measures miss.
- Respond swiftly and effectively to security incidents.
- Gain comprehensive visibility into their security environment.
- Meet regulatory and compliance requirements.
- Optimize their cybersecurity investments.
By partnering with LMNTRIX, organizations aim to reduce their risk of cyber attacks, protect sensitive data, and ensure business continuity in an increasingly complex threat landscape.
For more information on how LMNTRIX can benefit your organization, you may visit the LMNTRIX official website or contact their team for a personalized consultation.
Can LMNTRIX's solutions protect against zero-day attacks and advanced persistent threats (APTs)?
Yes, LMNTRIX’s cybersecurity solutions are designed to protect against zero-day attacks and advanced persistent threats (APTs) by leveraging a combination of advanced technologies and proactive strategies. Here’s how LMNTRIX achieves this level of protection:
- Artificial Intelligence and Machine Learning
- Behavioral Analysis:
- Anomaly Detection: LMNTRIX employs AI-driven behavioral analytics to establish a baseline of normal user and system behavior. By continuously monitoring for deviations from this baseline, the system can detect anomalies that may indicate zero-day exploits or APT activities.
- Predictive Modeling: Machine learning algorithms analyze vast amounts of data to identify patterns and predict potential threats before they materialize, enhancing early detection capabilities.
- Real-Time Threat Intelligence
- Continuous Updates:
- Global Threat Feeds: LMNTRIX integrates real-time threat intelligence from multiple global sources, ensuring the most up-to-date information on emerging threats and vulnerabilities.
- Threat Sharing Communities: Participation in cybersecurity communities enhances the platform’s ability to anticipate and recognize new attack vectors.
- Advanced Endpoint Detection and Response (EDR)
- Active EDR Agent:
- Pre-Execution Analysis: The agent analyzes files and code before execution to prevent malicious activities from initiating.
- On-Execution Monitoring: Continuous monitoring during execution allows for immediate detection and interruption of suspicious processes.
- Autonomous Operation:
- No Reliance on Cloud Connectivity: The EDR agent operates effectively without constant internet access, making real-time decisions on the device itself.
- Minimal Human Intervention: Advanced automation reduces the need for human analysts to be involved in the initial detection and response phases.
- Network Traffic Analysis
- Deep Packet Inspection:
- Identifying Malicious Traffic: By inspecting network packets, LMNTRIX can detect hidden threats attempting to communicate with external servers or move laterally within the network.
- Deception Technologies:
- Honeypots and Decoys: Implementing decoy systems lures attackers away from critical assets and exposes their tactics, techniques, and procedures (TTPs).
- Proactive Threat Hunting
- Expert Cybersecurity Analysts:
- Continuous Monitoring: A team of seasoned professionals actively searches for hidden threats that automated systems might miss.
- Unlimited Threat Hunting: Included in all subscriptions, this service ensures that organizations have ongoing expert support without additional costs.
- Automated Tools:
- IoC and TTP Identification: Automated systems scan for indicators of compromise and known attacker methodologies to flag potential threats promptly.
- Adaptive Security Architecture
- Unified Visibility:
- Centralized Dashboard: LMNTRIX provides a holistic view of the organization’s security posture across all endpoints, networks, cloud services, and applications.
- Scalability and Flexibility:
- Customizable Solutions: The platform adapts to the unique needs of each organization, ensuring optimal protection regardless of size or industry.
- Rapid Incident Response and Remediation
- Automated Response Mechanisms:
- Immediate Containment: Upon detecting a threat, the system can automatically isolate affected endpoints to prevent spread.
- Remediation Actions: The platform can terminate malicious processes and remove threats without waiting for manual intervention.
- Unlimited DFIR Services:
- Digital Forensics and Incident Response: Included as a standard part of all subscriptions, LMNTRIX offers unlimited incident response support, eliminating the need for third-party retainers.
- Compliance and Reporting
- Detailed Analytics:
- Regulatory Compliance: The platform assists in meeting compliance requirements by maintaining detailed logs and reports of all security incidents and responses.
- Audit Support:
- Comprehensive Reporting: Provides the necessary documentation for audits, demonstrating the organization’s commitment to robust cybersecurity practices.
LMNTRIX’s solutions are well-equipped to protect against zero-day attacks and advanced persistent threats by combining AI-driven technologies with proactive threat hunting and comprehensive incident response services. Their multi-layered approach ensures that both known and unknown threats are detected and neutralized promptly.
What compliance standards do you adhere to?
LMNTRIX is certified to SOC2, ISO27001 and PCI DSS.
Can you provide details on your response time to threats?
Detection Time: Nearly real-time or within minutes.
Investigation Time: From a few minutes to a few hours.
Containment Time: Within minutes after detection.
Remediation Time: From hours to days, depending on the severity and complexity of the breach.
Notification Time: Immediate to within an hour.
What kind of reporting and visibility will we have?
LMNTRIX XDR provides real-time visibility to all alerts. LMNTRIX MDR provides detailed incident reports, monthly technical reports and quarterly business review reports that are available via the XDR.
What is your process for incident response and remediation?
Our process is integrated with our broader security operations and uses forensic techniques and includes the following phases: Preparation, Identification, Containment, Eradication, Recovery, Lessons Learned, and Communication.
What industry analyst recognition do you have?
In 2024, recognised as a MDR Leader by IDC.
In 2023, covered in 8 Gartner research reports and recognised in the MDR market guide.
In 2022, covered in Forrester Landscape Reports for MSSP and NAV
In 2023, ranked #19 on MSSP Alert from global Top 250 MSSPs
What is expected from my team?
Your team will be required to assist during service onboarding as well as active engagement to add more context during the incident response process and to assist our team in threat validation and incident closure for more complex incidents.
Who is responsible for containment?
LMNTRIX. You also have the option of initiating containment for malicious indicators we detect using our XDR interface.
What is the extent of containment?
Containment is limited to hosts, network and cloud firewalls, cloud email and web security solutions.
How does your XDR platform integrate with existing security tools and infrastructure?
Our XDR tech stack is deployed using an agent on your hosts; a network sensor using SPAN/TAP; an API for cloud security; an App for mobile security, and standard log collection for analytics/SIEM.
How does containment work?
During service onboarding we integrate our XDR platform with your security controls. Using a combination of pull, push, and API’s we add malicious indicators to your tech stack so they are automatically blocked.
Containment vs. Remediation?
An example of containment is the blocking of a malicious IP across your security controls.
An example of remediation is the process of terminating a malicious process on a machine or deleting malicious malware.
What is the extent of containment and remediation?
LMNTRIX provides unlimited containment & remediation support at no extra cost.
Does LMNTRIX XDR integrate with my current SIEM?
LMNTRIX XDR for SIEM provides native next generation SIEM capability, however if you wish to retain your SIEM, we can forward our XDR alerts to your SIEM or we can consume logs from your SIEM.
Do I need to retain my SIEM?
You would need to retain your SIEM if your enterprise is large enough to warrant one. Usually, compliance obligations, reporting and post breach forensics and IR are the drivers for procuring SIEM solutions. Alternatively, you could use LMNTRIX XDR for SIEM and possibly save on your current SIEM licensing costs.
What types of threats can your XDR solution detect and respond to?
LMNTRIX XDR has 12 detection modules, each designed to detect different threat vectors including threats across endpoint, network, cloud, mobile, identity, lateral movement, behaviour, anomalies, retrospection, encrypted attacks, darknet, OT and more.
Can my existing AV/EDR run in parallel?
Yes, our agent can run alongside your existing agent given we whitelist one another. Most clients replace their existing agent within a few months or when the incumbents license expires as they witness firsthand how much the incumbent is missing.
How do you integrate with our service desk?
We provide native integration for ServiceNow and provide an API for all other service desk solutions.
What is the level of automation in your XDR solution?
Native Automated SecOps capability can be found across our XDR. This extends to automating threat detection, alert validation, incident creation and client communication process. Our threat intelligence process is also completely automated.
How does your XDR solution handle false positives and false negatives?
We achieve a 5% or less false positive rate through automated alert validation and supervised ML before alerts are turned into incidents.
How long is the onboarding process?
It depends on each module. EDR agent and network sensors typically take 2 weeks to deploy while log collection or deceptions take longer and, in many cases, rely on client IT availability and speed of execution.
What are the deployment options for your XDR platform?
LMNTRIX XDR is a cloud-based solution with a tech stack that is deployed inside the enterprise network.
How is data privacy handled in your XDR solution?
The LMNTRIX XDR and MDR are SOC2, PCI DSS and ISO27001 certified and extensive security measures are in place to protect client data.
What support and training do you offer for your XDR solution?
Following the onboarding process a 2-hour training session is scheduled for each client followed by on-demand training as required post deployment.
What specific services are included in your MDR offering?
24/7 monitoring, threat detection, incident response, proactive threat hunting and unlimited DFIR together with containment and remediation are standard services.
What is Threat Hunting?
Traditional defenses can’t keep up with new attacker techniques, leaving companies vulnerable to hacks. Even if the good guys could match their adversaries’ offensive measures, there would still be times when their defenses would fail. Inevitably, an employee will click on malicious link in an email or visit a dicey website or a firewall will be improperly installed. Unlike traditional, reactive approaches to detection, hunting is proactive. With hunting, security professionals don’t wait to take action until they’ve received a security alert or, even worse, suffer a data breach. Instead, hunting entails looking for opponents who are already in your environment. Hunting leads to discovering undesirable activity in your environment and using this information to improve your security posture. These discoveries happen on the security team’s terms, not the attacker’s. Rather than launching an investigation after receiving an alert, security teams can hunt for threats when their environment is calm instead of in the midst of the chaos that follows after a breach is detected.
How does the LMNTRIX XDR Platform compare to other "next-generation" endpoint protection solutions? What makes it unique?
The LMNTRIX XDR Platform distinguishes itself from other next-generation endpoint protection solutions through its innovative and unified approach to cybersecurity. Here’s what sets it apart:
- Unified Data Lake Architecture: LMNTRIX Grid acts as an industry-first data lake that seamlessly integrates various security layers—including Endpoint Protection (EPP), Endpoint Detection and Response (EDR), Network Detection & Response (NDR), Network Forensics (Packets), Deceptions, Mobile Threat Defense (MTD), Identity, Internet of Things (IoT) security, and Cloud Workload Protection Platform (CWPP)—into a single, centralized platform. This consolidation allows organizations to access and analyze backend data across their entire network through one cohesive solution.
- Real-Time Autonomous Security: The platform introduces a real-time, autonomous security layer that spans all enterprise assets, whether they are on-premises or in the cloud. This means threats are detected and mitigated instantly without manual intervention, enhancing the organization’s ability to respond swiftly to emerging threats.
- Single Codebase and Deployment Model: LMNTRIX XDR is built on a single codebase and employs a consistent deployment model across all components. This uniformity simplifies management and reduces complexity, ensuring seamless integration and operation of all security functions within the platform.
- First to Integrate NDR, Packets, Identity, SIEM, Attack Validation, OT/IoT and CWPP into XDR: Unlike other solutions, LMNTRIX is the first to expand from a cloud-native, autonomous protection system to a comprehensive cybersecurity platform that incorporates IoT security and cloud workload protection within an Extended Detection and Response (XDR) framework. This integration provides broader visibility and control over a wide array of devices and workloads that are often overlooked by other security solutions.
- Advanced AI-Powered Threat Hunting: Powered by artificial intelligence, the platform offers advanced threat hunting capabilities that provide complete visibility across every device—virtual or physical. This AI-driven approach enables the detection of sophisticated threats that might evade traditional security measures, allowing organizations to uncover and address vulnerabilities they were previously unaware of.
- Ease of Management and Control: LMNTRIX XDR is designed for user-friendly operation, allowing security teams to prevent, detect, respond to, and hunt threats effectively across all enterprise assets. Its centralized management console provides administrators with comprehensive tools to monitor and control their security environment efficiently.
In essence, the LMNTRIX XDR Platform’s uniqueness lies in its ability to unify diverse security functions into a single, AI-enhanced platform that delivers comprehensive protection and unparalleled visibility. It empowers organizations to see and control aspects of their network that were previously hidden or difficult to manage, thereby elevating their overall security posture beyond what other next-generation endpoint protection solutions offer.
Can I use LMNTRIX for Incident Response?
Yes, LMNTRIX is highly effective for incident response and offers specialized features designed to streamline and enhance the process of managing security incidents. Here’s how LMNTRIX supports incident response efforts:
- Active Endpoint Detection and Response (ActiveEDR): The platform’s ActiveEDR technology continuously tracks and monitors all processes that load into memory, organizing them into contextual “stories” that represent their behavior over time. This detailed tracking enables the system to understand the relationships between processes and the changes they make to the system.
- Network Detection & Response (NDR, Packets): Using a combination of techniques such as machine learning, behavioral analytics, and anomaly detection, our NDR and Packets sensors can identify unusual patterns or deviations from normal network behavior that may indicate cyber threats such as malware infections, lateral movement, or data exfiltration. You can deploy our sensors on enterprise networks, data centres or cloud environments.
- Cloud Detection & Response (CDR): Easily extend your incident response efforts across major cloud platforms using our CDR function.
- Contextual Awareness for Accurate Detection: By maintaining a historical context of process activities, LMNTRIX can identify when a legitimate process begins to exhibit malicious behavior. This contextual awareness allows the platform to make informed decisions about which actions to take, reducing false positives and enhancing detection accuracy.
- Automated and Manual Remediation Options: LMNTRIX allows organizations to set policies that dictate how the platform should respond to detected threats. If automatic remediation is enabled, the system will autonomously neutralize the threat and clean the system. Alternatively, administrators have the option to manually trigger remediation actions when needed.
- Reverse Execution to Remove Threats: When remediation is initiated, the LMNTRIX agent uses the stored historical context to “play back” the sequence of events leading up to the attack. This enables the agent to systematically undo the malicious changes, remove unwanted code artifacts, and restore system integrity.
- Integration with Management Policies: The platform seamlessly integrates with an organization’s security policies, ensuring that incident response actions align with compliance requirements and operational protocols. This integration provides a consistent and controlled approach to managing security incidents.
- Preservation of System Functionality: Throughout the incident response process, LMNTRIX ensures that system functionality is preserved as much as possible. By targeting only the malicious elements and unauthorized changes, the platform minimizes disruption to normal operations.
By incorporating these advanced incident response features, LMNTRIX not only enhances an organization’s ability to detect and prevent threats but also provides powerful tools to respond effectively when incidents occur. Its comprehensive approach to incident response makes it a valuable asset for organizations seeking to strengthen their cybersecurity defenses and reduce the impact of security breaches.
Endpoint Security
What is endpoint security software?
Endpoint security software consists of applications or tools installed on endpoint devices such as laptops, desktops, and servers to protect them from a wide array of cyber threats. These threats include malware, ransomware, exploits, live attacks, and malicious scripts that aim to steal data, cause financial loss, or disrupt systems and operations. By securing each individual device connected to a network, endpoint security software plays a crucial role in an organization’s overall cybersecurity strategy, preventing attackers from infiltrating the network through vulnerable endpoints.
What is considered an endpoint?
An endpoint refers to any device that serves as a point of entry or exit within a network, where communications originate or are received. Unlike network devices that merely relay or route data (like routers or switches), endpoints are the devices that actively participate in network communications. Examples include desktops, laptops, smartphones, tablets, servers, and Internet of Things (IoT) devices. In essence, an endpoint is any device that can connect to a network and is capable of sending or receiving data.
Are servers considered endpoints?
Yes, servers are considered endpoints within a network infrastructure. They play a vital role by hosting applications, storing data, and providing services to other devices. Servers, often running operating systems like Linux, are just as susceptible to cyber threats as other endpoints. Therefore, it’s essential to deploy robust security solutions on servers to ensure they are protected against malware, unauthorized access, and other cyber attacks, just like any other endpoint device.
What is next-gen endpoint protection?
Next-generation endpoint protection refers to advanced security solutions that proactively predict, prevent, and respond to cyber threats using cutting-edge technologies. Unlike traditional antivirus software that relies on signature-based detection, next-gen solutions employ machine learning, artificial intelligence, and behavioral analysis to monitor all activities within a network—including system kernel and user space operations. By evaluating patterns and identifying anomalies in real-time, these tools can detect and neutralize threats early, even those that have not been previously identified. This proactive approach enhances the ability to catch sophisticated attacks like zero-day exploits, fileless malware, and advanced persistent threats (APTs) before they can cause significant harm.
What is an endpoint protection platform?
An Endpoint Protection Platform (EPP) is an integrated security solution that combines multiple protective technologies into a single, unified agent deployed on endpoint devices. Its primary functions include preventing, detecting, and responding to threats across various attack vectors. Powered by machine learning and automation, an EPP offers real-time threat prevention and detection, swiftly eliminates identified threats through automated, policy-driven responses, and provides comprehensive visibility into endpoint activities. This includes full-context, real-time forensics that help security teams understand the nature and progression of attacks, enabling them to respond more effectively.
What is endpoint management software?
Endpoint management software refers to tools that enable organizations to centrally manage, monitor, and secure all endpoint devices within their network. By deploying agents on each device, administrators can use a management console to oversee various aspects such as software updates, security policy enforcement, threat monitoring, and response actions. This centralized approach eliminates the need for multiple disparate tools and add-ons, streamlining administrative tasks and ensuring consistent security measures are applied across all endpoints.
What is the best endpoint protection?
The most effective endpoint protection combines advanced technologies within a single, autonomous agent to defend against a broad spectrum of cyber threats. This includes integrating both static analysis (examining code before execution) and behavioral AI (monitoring actions during execution) to protect against file-based malware, fileless attacks, malicious scripts, and memory exploits. Such solutions operate continuously, whether the endpoint is online or offline, ensuring constant protection. Evaluations by independent organizations, like the MITRE ATT&CK framework, can help identify leading solutions by assessing factors such as detection rates, response capabilities, and reliance on automation versus human analysis. The best endpoint protection systems minimize missed detections, maximize high-quality threat identifications, and automate responses to neutralize threats swiftly and effectively.
What is EDR?
Endpoint Detection and Response (EDR) is a cybersecurity solution that focuses on monitoring endpoint devices to detect suspicious activities and potential threats in real time. EDR tools collect and analyze data on every activity and event occurring on endpoints, such as process executions, network connections, and file modifications. By correlating this information, EDR provides critical context that helps identify advanced threats that may bypass traditional security measures. Upon detecting a threat, EDR solutions can automate response actions like isolating the infected device from the network, stopping malicious processes, or alerting security personnel, thereby containing the threat swiftly.
What is Active EDR?
Active Endpoint Detection and Response (Active EDR) enhances traditional EDR by adding real-time context and automated response capabilities without requiring constant human oversight. Active EDR solutions continuously track and contextualize all activities on a device, enabling them to identify malicious actions as they happen. By understanding the relationships between processes and events, Active EDR can automate the necessary responses to neutralize threats immediately. This technology also facilitates efficient threat hunting by allowing security analysts to search using a single Indicator of Compromise (IOC), streamlining the investigation process.
What is XDR?
Extended Detection and Response (XDR) is an evolution of EDR that expands threat detection and response capabilities beyond endpoints to include multiple native security layers such as networks, cloud workloads, servers, and more. XDR also aggregates and correlates data from various 3rd party sources, providing a unified view of threats across the entire IT ecosystem through a single interface. This comprehensive visibility enhances the ability to detect complex, multi-vector attacks and accelerates triage, investigation, and remediation efforts. By automating data collection and analysis across multiple security domains, XDR helps security analysts respond to threats more quickly and effectively before they can escalate.
How is XDR different from SOAR?
Security Orchestration, Automation, and Response (SOAR) platforms are designed for mature security operations centers (SOCs) to create and execute complex, multi-step workflows (playbooks) that automate responses across an integrated ecosystem of security tools via APIs. SOAR solutions are typically complex, requiring significant resources to implement and maintain.
In contrast, XDR offers a more streamlined, user-friendly approach, often described as “SOAR-lite.” XDR platforms provide out-of-the-box integrations and automate simpler response actions without the need for extensive coding or playbook development. While SOAR focuses on deep customization and orchestration across many tools, XDR emphasizes ease of use and quick deployment, offering automated threat detection and response capabilities that are accessible to organizations without a highly mature SOC.
What is the LMNTRIX EDR agent?
The LMNTRIX EDR agent is a lightweight software component installed on endpoint devices—including desktops, laptops, servers, and virtual environments—that provides autonomous protection against cyber threats. Operating at the kernel level of the operating system, the agent monitors all processes and activities in real time. Utilizing technologies like Dynamic Behavioral Tracking, it observes and records detailed information about each event, including the origin of processes, file and registry changes, network connections, and other forensic data. This comprehensive monitoring enables the agent to detect and respond to threats autonomously, even without an active internet connection, providing continuous protection for the endpoint.
How do you implement endpoint security?
Implementing endpoint security involves deploying security agents or software across all endpoint devices within an organization. This process includes installing the endpoint protection solution on each device, ensuring proper configuration, and aligning it with the organization’s security policies. Once deployed, security teams can use centralized management tools to monitor alerts, perform threat hunting, and apply both local and global security policies. Regular updates, ongoing monitoring, and periodic assessments are essential to maintain the effectiveness of the endpoint security measures and adapt to new and emerging threats.
Is endpoint security an antivirus?
While antivirus software is a component of endpoint security, modern endpoint protection encompasses a much broader range of security measures. Traditional antivirus solutions primarily rely on signature-based detection to identify known malware, which can be insufficient against new or sophisticated threats. Endpoint security solutions offer advanced capabilities such as behavioral analysis, machine learning, and real-time threat detection and response. They protect against a wide variety of threats, including malware, ransomware, zero-day exploits, and fileless attacks. Therefore, while antivirus is part of endpoint security, comprehensive endpoint protection provides a more robust defense by addressing the limitations of traditional antivirus software.
What is considered an endpoint in endpoint security?
An endpoint in endpoint security is any device that connects to a network and can send or receive data, serving as a point of entry or exit for network communications. Examples of endpoints include:
- Desktops and Laptops: Commonly used computing devices in workplaces.
- Mobile Devices: Smartphones and tablets used for both personal and business purposes.
- Wearables: Smartwatches and other connected wearable technology.
- Internet of Things (IoT) Devices: Smart devices like sensors, cameras, and appliances.
- Point-of-Sale (POS) Systems: Devices used in retail for processing transactions.
- Medical Devices: Connected equipment used in healthcare settings.
- Printers and Multifunction Devices: Networked office equipment.
- Servers and Virtual Machines: Physical and virtual systems providing services and resources.
As technology evolves, the number and variety of endpoints continue to grow, increasing the potential attack surface for cyber threats. This expansion makes securing endpoints more critical than ever, as they often represent the frontline defense against unauthorized access and data breaches. Modern endpoint security must address the unique challenges posed by diverse devices, including mobile and IoT devices, to ensure comprehensive protection.
What are the primary benefits of using LMNTRIX for cloud security and protecting cloud workloads?
LMNTRIX provides robust cloud security solutions that offer several key benefits for protecting cloud workloads:
- Comprehensive Protection: Safeguards cloud assets against a wide range of threats, including malware, zero-day exploits, and advanced persistent threats.
- Real-Time Visibility: Offers continuous monitoring and real-time insights into cloud workloads, enabling proactive threat detection.
- Automated Threat Detection and Response: Utilizes AI and machine learning to identify and respond to threats autonomously, reducing the time to mitigate risks.
- Seamless Integration: Easily integrates with major cloud service providers like AWS, Azure, and Google Cloud, ensuring consistent security across multi-cloud environments.
- Operational Efficiency: Simplifies security management with centralized control and automated processes, freeing up resources for other strategic initiatives.
By leveraging these capabilities, organizations can enhance their cloud security posture, protect sensitive data, and maintain compliance with regulatory requirements.
What is the role of AI and machine learning in LMNTRIX's cybersecurity solutions?
Artificial intelligence (AI) and machine learning (ML) are foundational to LMNTRIX’s cybersecurity solutions, enabling advanced threat detection, prevention, and response capabilities. Here’s how they contribute:
- Automated Threat Detection: AI and ML algorithms analyze vast amounts of data to identify patterns and anomalies indicative of cyber threats, including previously unknown or zero-day attacks.
- Adaptive Defense: The systems continuously learn from new data, adapting to evolving threat landscapes without requiring manual updates or intervention.
- Reduced False Positives: Intelligent analysis helps distinguish between legitimate activities and malicious behavior, minimizing false alarms and allowing security teams to focus on genuine threats.
- Real-Time Response: AI-powered automation enables immediate action against detected threats, such as isolating affected devices or terminating malicious processes, thereby limiting potential damage.
- Scalability: Machine learning models can handle the increasing volume and complexity of data as organizations grow, ensuring consistent security coverage.
Overall, AI and machine learning enhance the effectiveness and efficiency of cybersecurity measures, providing robust protection against sophisticated cyber threats.
Are Norton and Symantec the same?
Norton and Symantec are brands associated with traditional antivirus solutions that have been widely used for endpoint protection. Historically, these products have relied on signature-based detection methods, where known malware signatures are used to identify and block threats. While they have been effective against known threats, this approach has limitations in detecting new or rapidly evolving malware.
In contrast, modern cybersecurity solutions like LMNTRIX have moved beyond signature-based detection. LMNTRIX employs advanced technologies such as static machine learning analysis and dynamic behavioral analysis to protect against a broader spectrum of threats. By evaluating files and processes in real time—both before execution and during runtime—without relying on signature databases, LMNTRIX can detect and neutralize zero-day exploits and fileless attacks that traditional antivirus products might miss.
Additionally, LMNTRIX ‘s approach reduces the need for frequent updates and system scans that can consume network bandwidth and impact system performance. This results in more efficient and effective endpoint protection, better suited to address the complexities of today’s cyber threat landscape.
How does LMNTRIX Endpoint Security work?
How does LMNTRIX work?
LMNTRIX operates by leveraging patented technology designed to safeguard enterprises against a wide spectrum of cyber threats. It employs a multi-vector approach that integrates both pre-execution and on-execution artificial intelligence (AI) technologies.
- Pre-Execution Static AI: Before any file or application is executed, LMNTRIX uses Static AI to analyze it for malicious characteristics. This proactive analysis effectively replaces traditional antivirus applications by detecting and blocking threats before they can initiate any harmful actions.
- On-Execution Behavioral AI: While applications are running, LMNTRIX monitors real-time behaviors using Behavioral AI. This allows the system to detect and respond to anomalous activities associated with sophisticated threats such as fileless attacks, exploits, malicious macros, harmful scripts, cryptominers, ransomware, and other advanced cyber attacks.
One of the standout features of LMNTRIX is its ability to respond to threats within milliseconds, significantly reducing the dwell time of attacks to nearly zero. The platform offers a comprehensive set of response capabilities, including:
- Alerting: Generating immediate notifications to inform security teams of detected threats.
- Process Termination: Stopping malicious processes before they can cause further damage.
- Quarantining: Isolating infected files to prevent the spread of malware.
- Remediation: Reversing unauthorized changes made by malicious activities.
- Network Isolation: Disconnecting affected devices from the network to contain threats.
- Remote Shell Access: Providing secure remote access for deeper investigation and remediation.
By combining these advanced technologies and rapid response features, LMNTRIX delivers comprehensive protection that adapts to the evolving cyber threat landscape.
What are the top features of the LMNTRIX platform?
The LMNTRIX XDR (Extended Detection and Response) platform offers a suite of advanced features designed to provide robust and comprehensive cybersecurity solutions:
- Advanced Threat Hunting: Utilizing tools like Killbox, LMNTRIX automates the correlation of security events, enabling analysts to quickly identify the root causes of incidents. This reduces investigation times and enhances the efficiency of threat hunting operations.
- Automated and Rapid Response: The platform is engineered to minimize the time an attacker can remain undetected. Automated response capabilities include real-time alerting, process termination, file quarantine, and system rollback to restore compromised data.
- Unified Integration: LMNTRIX consolidates multiple security functions into a single, cohesive platform. This integration provides a future-proof solution that surpasses traditional antivirus software by addressing a broader range of threats across various environments.
- Behavioral AI Technology: Pioneering the use of behavioral AI since 2015, LMNTRIX employs machine learning algorithms to analyze behaviors and detect anomalies in real-time. This enhances the detection of sophisticated threats that may evade signature-based detection methods.
- Scalability and Ease of Use: The platform offers global scalability and user-friendly interfaces, ensuring that organizations can effectively manage security across large and diverse environments without compromising performance.
- Real-Time Cyber Defense: Operating at speeds and scales beyond human capability, LMNTRIX provides instantaneous defense against cyberattacks with higher accuracy than manual efforts.
- Compliance Support: LMNTRIX assists organizations in meeting industry standards and regulatory requirements by supporting various compliance frameworks and providing detailed security documentation.
- Comprehensive Cloud Security: Extending protection to cloud environments, the platform offers endpoint protection, incident response tools, identity detection and response, insider threat detection, attack surface management, and advanced security analytics.
By integrating these features, LMNTRIX delivers a holistic cybersecurity solution capable of addressing modern threats across diverse infrastructures.
Does LMNTRIX protect me while I am disconnected from the internet (such as during traveling)?
Yes, LMNTRIX continues to protect your device even when it is offline or disconnected from the internet. The LMNTRIX agent installed on your endpoint operates independently, utilizing locally stored AI models and analysis techniques to detect and prevent malware threats in real-time without requiring an active internet connection.
However, while the agent maintains protection on the device, the central management console’s ability to monitor and manage that specific endpoint is limited during the period of disconnection. Administrative visibility and certain remote functionalities will resume once the device reconnects to the internet, at which point the agent will synchronize updates and logs with the console.
Is LMNTRIX an antivirus?
LMNTRIX functions as more than a traditional antivirus solution. It is an autonomous cybersecurity platform designed to protect against a comprehensive range of attacks, from common malware to advanced persistent threats (APTs), whether your device is online or offline.
While it fulfills and exceeds the requirements typically associated with enterprise antivirus solutions—validated by industry authorities like MITRE, Gartner, and Forrester—LMNTRIX extends its capabilities beyond basic antivirus functions. It serves as a complete replacement for legacy antivirus, next-generation antivirus (NGAV), and Endpoint Detection and Response (EDR) tools. Additionally, it offers extensive protection across various environments, including endpoints, cloud services, containers, mobile devices, IoT devices, and data assets.
LMNTRIX can operate alongside other security tools if desired, providing flexibility in your security infrastructure while delivering comprehensive prevention, detection, and response capabilities that surpass traditional antivirus software.
How does LMNTRIX differ from other antivirus software?
LMNTRIX distinguishes itself from traditional antivirus software through several key innovations:
- AI-Driven Detection: Unlike traditional antivirus solutions that rely on signature-based detection, LMNTRIX employs advanced artificial intelligence and machine learning algorithms. This enables real-time detection and neutralization of threats, including zero-day exploits and sophisticated malware that signature-based methods may miss.
- Multi-Vector Security: LMNTRIX provides holistic protection across multiple vectors, not just endpoints. It secures cloud workloads, containers, mobile devices, and IoT devices within a unified platform, addressing diverse enterprise security needs.
- Automated Rapid Response: The platform is designed to minimize attack dwell time through automated response features. These include instant alerting, process termination, file quarantine, and system rollback, allowing for immediate remediation without manual intervention.
- Alignment with Industry Frameworks: By mapping its detection and response capabilities to the MITRE ATT&CK® framework, LMNTRIX ensures its strategies align with recognized industry standards, enhancing the effectiveness of threat detection and response.
- Advanced Threat Hunting: Tools like Killbox automate complex tasks such as event correlation and root cause analysis, improving the efficiency and speed of threat investigations.
- Proven Effectiveness: Positive user reviews and industry accolades validate LMNTRIX’s superior performance compared to traditional antivirus solutions, demonstrating its ability to address modern cyber threats effectively.
By integrating these advanced features into a single platform, LMNTRIX offers a comprehensive and future-proof cybersecurity solution that significantly outperforms traditional antivirus software.
Can I use the LMNTRIX platform to replace my current AV solution?
Yes, you can use LMNTRIX to replace your current antivirus solution. It is designed to serve as a complete replacement for traditional antivirus software, offering advanced protection that covers and exceeds the capabilities of legacy systems. If preferred, LMNTRIX can also operate alongside existing security tools, such as Microsoft Defender, providing flexibility during transition periods or in environments where layered security is desired.
Which products can LMNTRIX help me replace?
LMNTRIX XDR can replace several types of security products within your organization’s cybersecurity infrastructure:
- Traditional Antivirus Solutions: LMNTRIX EDR serves as a full replacement for legacy antivirus software with advanced AI-driven protection.
- Next-Generation Antivirus (NGAV) and EDR Tools: LMNTRIX EDR’s integrated detection and response capabilities eliminate the need for separate NGAV and Endpoint Detection and Response tools.
- Network Traffic Analysis (NTA) Tools: LMNTRIX Packets can replace traditional NTA products by providing comprehensive network traffic visibility and analysis.
- Network Visibility Appliances: LMNTRIX Packets can replace devices like Forescout by offering integrated network visibility and device management.
- Network Detection & Response (NDR): LMNTRIX NDR can replace devices such as Fire Eye Network & Email Security appliances, Cisco IDS and Threat Grid and Cisco Umbrella combined, Darktrace, Extrahop or VectraAI.
- Network Forensic Tools: LMNTRIX Packets can replace solutions such as FireEye Network Forensics, RSA Netwitness Packets, and EnCase
- Threat Intelligence Platform (TIP): LMNTRIX Intelligence eliminates the need for FireEye Mandiant Advantage Security Operations, Threat Intelligence, Anomaly, ThreatQuotient and Recorded Future.
- Deception Technology: LMNTRIX Deceive replaces vendors such as Attivo, TrapX, and Illusive Networks.
- Deep & Darknet Intelligence: LMNTRIX Recon offers similar capability to Digital Shadows, SixGill, Intsights, FireEye Mandiant Advantage Security Operations, and Recorded Future.
- Security Information & Event Management (SIEM): LMNTRIX SIEM delivers SIEM, UEBA and Analytics functions in a single platform and is a direct replacement for vendors such as Splunk, FireEye Helix, Exabeam and Securonix.
- Managed Detection & Response: LMNTRIX MDR is far superior to log based for MDR vendors such as FireEye Mandiant Managed Defense, Cisco MDR, Expel, Proficio, ArcticWolf, Rapid7, Sophos and others listed in the Gartner MDR Market Guide.
- Extended Detection & Response: LMNTRIX XDR with 12 native security functions is far superior to EDR and log based XDR vendors such as Microsoft, SentinalOne, CrowdStrike, Sophos, and TrendMicro.
- Dedicated Threat Hunting Platforms: With advanced threat hunting capabilities, it eliminates the need for standalone threat hunting solutions.
By consolidating these functions, LMNTRIX simplifies your security stack, reduces complexity, and enhances overall protection.
Can LMNTRIX protect endpoints if they are not connected to the cloud?
Yes, LMNTRIX is designed to protect endpoints even when they are not connected to the cloud or the internet. The LMNTRIX agent performs both static and dynamic behavioral analyses locally on the endpoint, enabling it to detect and prevent threats without relying on cloud connectivity. When the endpoint reconnects to the internet, the agent synchronizes with the LMNTRIX cloud for updates and to upload logs and events to the central management console.
What detection capabilities does LMNTRIX EDR have?
LMNTRIX EDR employs a multi-layered detection strategy utilizing several advanced engines:
- Reputation Engine: Assesses the trustworthiness of files and processes based on known threat intelligence.
- Static AI Engine: Analyzes files before execution to detect malicious characteristics.
- Behavioral AI Engine: Monitors real-time behaviors of running processes to identify anomalies and malicious activities.
- Active Endpoint Detection and Response (ActiveEDR): Continuously records endpoint activities to detect sophisticated threats through context-aware analysis.
These cascading engines work together to detect and prevent various types of attacks at different stages, providing comprehensive security coverage.
Does LMNTRIX provide malware prevention?
Yes, LMNTRIX offers robust malware prevention. Its Endpoint Protection Platform (EPP) uses Static AI to analyze executable files before they run, replacing the need for traditional, easily bypassed signature-based methods. The platform also examines files like PDFs and Microsoft Office documents for embedded malicious code. By employing on-agent machine learning models, LMNTRIX effectively detects both common and novel malware without relying on large signature databases.
Is LMNTRIX's machine learning feature configurable?
Yes, the machine learning algorithms used by LMNTRIX are directly configurable by customers using 3 available models. The AI models are developed and trained by LMNTRIX’s data science team to ensure optimal performance across all environments. Updates to these models are periodically deployed through agent software updates, eliminating the need for customers to train or customize the AI within their own environments.
Can LMNTRIX detect in-memory attacks?
Yes, LMNTRIX can detect in-memory attacks. By integrating with hardware-based technologies like Intel® Threat Detection Technology (Intel TDT), LMNTRIX gains accelerated memory scanning capabilities. This allows the platform to efficiently identify and respond to malicious activities that occur directly in system memory, which are often missed by traditional security solutions.
Is LMNTRIX a HIDS/HIPS product/solution?
LMNTRIX functions as both a Host-based Intrusion Detection System (HIDS) and a Host-based Intrusion Prevention System (HIPS) by monitoring and protecting individual hosts from malicious activities. Additionally, it extends beyond traditional HIDS/HIPS capabilities by offering Endpoint Detection and Response (EDR), threat hunting, asset inventory, device hygiene monitoring, and other advanced security features, providing a comprehensive security solution.
Is LMNTRIX cloud-based or on-premises?
LMNTRIX XDR is a Cloud-Based (SaaS) solution hosted in the cloud, such as on Amazon AWS.
Does LMNTRIX offer solutions for mobile devices?
Yes, LMNTRIX provides security solutions for mobile devices through the LMNTRIX Mobile agent, which extends advanced threat detection and prevention to iOS, Android and Chromebook devices. Features include Mobile Threat Defense, integration with Mobile Device Management (MDM) solutions, easy deployment, and compatibility with various mobile operating systems. The Mobile Agent complements existing MDM solutions by adding robust security capabilities without replacing current device management tools.
Can LMNTRIX help with securing remote work environments?
Absolutely, LMNTRIX is well-suited for securing remote work environments. The platform offers:
- Remote Shell Access: Secure remote access to endpoints for troubleshooting and management without physical contact.
- Automated Threat Response: Rapid detection and remediation of threats without the need for on-site intervention.
- Centralized Management: Unified policy enforcement and visibility across all remote devices.
- Advanced Threat Detection: AI-driven technologies to protect remote workers from sophisticated attacks.
These features enable organizations to maintain strong security across diverse and dispersed remote workforces.
Does LMNTRIX offer protection against insider threats?
Yes, LMNTRIX provides protection against insider threats through:
- Behavioral Analytics: Monitoring user activities for anomalies and suspicious behaviors.
- Real-Time Alerts: Immediate notification of potential insider threat activities.
- Integration and Automation: Enhanced SOAR capabilities and threat prioritization through integrations.
- Best Practices: Recommendations for robust access control policies, employee training, and fostering a culture of security awareness.
This comprehensive approach helps detect, prevent, and respond to insider threats effectively.
How does LMNTRIX ensure the security of IoT devices?
LMNTRIX secures IoT devices by:
- Continuous Monitoring: Using its NDR, Packets, Deceptions and Endpoint Protection Platform to detect and respond to threats targeting IoT devices.
- XDR Platform Coverage: Extending protection to IoT devices through behavioral AI and unified security management.
- Network Quarantine: Utilizing network containment features to quarantine and prevent communication with unmanaged or unsecured devices.
This multi-faceted approach addresses the unique challenges of securing IoT devices within an enterprise environment.
What kind of reporting features does LMNTRIX offer?
LMNTRIX provides a variety of reporting features, including:
- Monthly Reports: Detailed insights into threats, unmitigated issues, and new agent installations.
- On-demand Reports: Tailored reports based on specific data fields, OS versions, and applications.
- Annual Business Review Meetings: Reports are delivered during annual business review meetings that are designed for executives and stakeholders.
Availability of specific features may depend on your LMNTRIX plan and configuration.
Does LMNTRIX offer any forensics capabilities?
Yes, LMNTRIX offers unlimited DFIR capabilities through our CDC at no extra cost, which allows:
- Automated and Manual Data Collection: Gathering forensic artifacts across the network.
- Auto-Parsing of Artifacts: Extracting meaningful information for analysis.
- Integration with Real-Time Telemetry: Combining forensic data with live telemetry for comprehensive incident understanding.
- Scalability: Conducting DFIR activities efficiently across large environments.
DFIR capabilities are limited to your subscription levels. For example, without LMNTRIX Packets, our network forensics capability will be very limited.
How does LMNTRIX handle false positives?
LMNTRIX manages false positives by:
- Behavioral Analysis: Utilizing AI to accurately distinguish between legitimate and malicious activities.
- Detailed Incident Information: Providing insights into detections to aid in assessment.
- Exclusion Management: Allowing careful creation of exclusions with guidance from LMNTRIX Support.
- False Positive Submission: Enabling customers to submit suspected false positives for review.
- Security Solution Tuning: Offering recommendations to align detection engines with organizational needs.
Consulting LMNTRIX Support is advised for uncertainties or assistance in managing false positives.
Can LMNTRIX detect and prevent supply chain attacks?
Yes, LMNTRIX can detect and prevent supply chain attacks through:
- Advanced AI Detection: Real-time identification of malicious activities stemming from compromised third-party components.
- Automated Response: Immediate actions like quarantining and blocking threats.
- Real-World Effectiveness: Proven ability to thwart supply chain attacks, such as blocking trojanized installers from known software providers.
- Industry Alignment: Mapping to the MITRE ATT&CK® framework to stay ahead of emerging tactics.
- Underground Monitoring: LMNTRIX Recon monitors your supply chains and alerts you of possible breaches that could directly impact your business.
Additionally, LMNTRIX emphasizes best practices like supplier due diligence and robust security controls to mitigate supply chain risks.
How does LMNTRIX protect against malware and ransomware attacks?
LMNTRIX protects against malware and ransomware through:
- Advanced Detection Techniques: Using AI and machine learning to identify both known and unknown threats.
- Auto-Scanning of Removable Media: Scanning external devices to prevent malware introduction.
- Rapid Response: Mandating swift remediation actions to contain threats.
Continuous updates and enhancements ensure LMNTRIX stays ahead of evolving malware and ransomware threats.
How does LMNTRIX's AI technology adapt to new, emerging threats?
LMNTRIX adapts to emerging threats by:
- Continuous Learning: Updating AI and machine learning models to recognize new threat patterns.
- Multi-Vector Approach: Securing various environments to detect threats across different vectors.
- Industry Framework Alignment: Staying aligned with the MITRE ATT&CK® framework for updated tactics and techniques.
- Countering AI-Powered Threats: Detecting sophisticated threats, including those leveraging AI, by identifying unique indicators.
- Innovation and Updates: Investing in research and regularly enhancing the platform’s capabilities.
This dynamic approach ensures LMNTRIX remains effective against the constantly evolving threat landscape.
Does LMNTRIX offer any kind of firewall protection?
No, LMNTRIX relies on the built in Windows firewall protection that allows administrators to:
- Manage Endpoint Firewall Settings: Control network traffic to and from endpoints via the management console.
- Define Rules and Policies: Create and apply firewall rules using tags that represent policies.
While there are current limitations on FQDN rules and category-based blocking, LMNTRIX continues to enhance firewall capabilities to meet diverse security needs.
Does LMNTRIX EDR offer any kind of File Integrity Monitoring or DLP protection?
No, LMNTRIX relies on 3rd party solutions for FIM and DLP features. LMNTRIX EDR is exclusively focused on NGAV and EDR functions.
LMNTRIX EDR - Specifications, Performance, Installation
Which Operating Systems can run LMNTRIX EDR agent?
LMNTRIX offers clients for Windows, macOS, and Linux. For none vendor supported OSs such as Windows XP, LMNTRIX recommends the use of open source Cisco ClamAV solution. LMNTRIX XDR also offers OT/IoT security, mobile (iOS/Android/Chromebook) as well as cloud security.
What are the system requirements for installing LMNTRIX EDR agent?
LMNTRIX is designed to be compatible with a wide range of enterprise devices, making it a versatile solution for your organization’s security needs. Here’s a brief overview of the system requirements:
Windows OS Support
- Windows Server2008R2, 2012R2, 2016, 2019, 2022
- Windows 7 SP1
- Windows 8.1
- Windows 10
- Windows 10 Anniversary
- Windows 11
Linux OS Support
- CentOS / Red Hat Linux 6.5, 7.x and 8.
- Ubuntu 16.04, 18.04 and 22.04 (64-bit)
- SLES 15
- Debian 9, 10, 11
- Oracle Linux 8 and 9
- Alma Linux 9
- Rocky Linux 9
- Amazon Linux 2
- Google Container
optimized OS
Mac OS Support
- MacOS 10.13, 10.14, 10.15
- MacOS 11, ,12 ,13, 14
- MacOS 10.12
- MacOS 10.13
General Requirements: LMNTRIX can be managed through the LMNTRX XDR Cloud-Based Console hosted on AWS. The LMNTRIX EDR agent connects to the LMNTRIX XDR using TLS from anywhere. Unlike several competitors, there is no need for a VPN for home users that are not on the corporate network.
Can I install LMNTRIX on workstations, servers, and in VDI environments?
LMNTRIX can be installed on all workstations and supported environments.
Do I need to uninstall my old antivirus program?
LMNTRIX works as a complete replacement for traditional anti-malware solutions or in conjunction with them. You can uninstall the legacy AV or keep it. The choice is yours. If choosing to keep the legacy solution, we recommend whitelisting our agent and visa-versa.
Will LMNTRIX agent slow down my endpoints?
The LMNTRIX agent does not slow down the endpoint on which it is installed. Our agent is designed to have as little impact on the end user as possible while still providing effective protection both online and offline.
In contrast to other anti-malware products that require either constant cloud connectivity or constant “.dat” file signature updates and daily disk scans, our agent instead uses static file AI and behavioral AI which saves on CPU, memory and disk I/O. End users have better computer performance as a result. System resource consumption will vary depending on system workload.
LMNTRIX EDR agent is a lightweight dissolvable agent. Deploys in minutes with no end user impact or reboot required:
- Average CPU Usage: <2%
- Memory Utilization: 250MB-300MB
- Disk Usage: <500MB
- Optional Event Storage: 500MB
Does LMNTRIX EDR provide proxy support?
For enterprise networks that do now allow direct Internet access, the LMNTRIX EDR service provides support for enterprise proxies.
The LMNTRIX XDR IP address will be supplied to you by the CDC.
Client needs to provide their proxy information in the form:
IP and Port
10.1.1.2:3128
URL
http://proxy.domain.local
https://proxy2.domain.local
Proxy-aware agent pack will install sensor agents which will use direct path as well as proxy path to connect back to the LMNTRIX XDR.
Important notes about the Proxy aware sensor pack –
- SSL Inspection is not supported and must be bypassed for all EDR traffic.
- Only unauthenticated proxies are supported.
- In case of authenticated proxy being present –
- Configure the proxy and add a rule to allow traffic to the LMNTRIX XDR IP
- Use a different proxy policy that allows for unauthenticated proxy access to the LMNTRIX XDR IP
Can LMNTRIX scale to protect large environments with 100,000-plus endpoints?
LMNTRIX can scale to protect large environments. Some of our clients have more than 200,000 endpoints in their environments.
How do I turn off LMNTRIX?
To turn off LMNTRIX, use the Management console. Agent functions can be modified remotely in multiple ways including starting and stopping the agent, as well as initiating a full uninstall if needed.
How do I uninstall LMNTRIX?
The Management console is used to manage all the agents. Agent functions can be modified remotely in multiple ways including starting and stopping the agent, as well as initiating a full uninstall if needed. You may also uninstall our agent locally using an Admin account and a command issued at command prompt. Contact the LMNTRIX CDC for uninstall command instructions if you wish to uninstall it locally.
Do I need a large staff to install and maintain my LMNTRIX product?
You do not need a large security staff to install and maintain LMNTRIX as it’s completely managed for you by LMNTRIX MDR who accelerate the detection, prioritization, and response to threats.
If you choose to operate the solution yourself, our customers typically dedicate one full-time equivalent person for every 100,000 nodes under management. This may vary depending on the requirements of the organization. This estimate may also increase or decrease depending on the quantity of security alerts within the environment.
What are the best practices for deploying LMNTRIX in an enterprise environment?
Deploying LMNTRIX in an enterprise environment involves several best practices, as outlined in the documents found:
- Multi-Vector Approach: LMNTRIX provides a holistic security solution that extends beyond just endpoints. It covers containers, cloud workloads, IoT devices, and mobile offering a unified platform for diverse enterprise needs.
- Compatibility: LMNTRIX is designed to be compatible with a wide range of enterprise devices, making it a versatile solution for your organization’s security needs.
- Securing Remote Work Environments: The LMNTRIX XDR platform provides a comprehensive security solution that extends beyond just endpoints. This is particularly beneficial for remote work environments where diverse devices and platforms are often in use.
- Deployment Stages: The main stages are onboarding, deployment, and ongoing post-deployment. Onboarding can be done in one call, or more than one call, or in an on-site workshop. A deployment can be two to eight weeks (depends on sizing and IT availability) and includes a gradual Agent deployment.
- Guided Onboarding: The LMNTRIX Guided Onboarding (GO) service is a consultative and advisory service designed to maximize your success with the LMNTRIX portfolio of products and services.
- Project Planning: The LMNTRIX project team will collaborate with your resources to develop an overall project plan, schedule, deployment plan, and success criteria in alignment with established best practices and lessons learned over years of deploying LMNTRIX solutions.
Remember, each deployment is unique and should be adapted to your specific needs. It’s always best to consult with LMNTRIX Support for assistance during the deployment process.
What are the steps to troubleshoot common issues in LMNTRIX EDR agent?
Troubleshooting common issues in LMNTRIX can vary depending on the specific problem you’re encountering. However, here are some general steps you can follow based on the documents found:
- Identify the Issue: The first step in troubleshooting is to clearly identify the problem. Are you having trouble with installation, detection, or something else? Understanding the issue will help you find the right solution.
- Check the Documentation: We provide extensive documentation. This can be a great resource for finding solutions to common problems.
- Contact Support: If you can’t find the solution in the documentation, the next step is to contact LMNTRIX’s support team. They can provide expert assistance and guide you through the troubleshooting process.
- Use the LMNTRIX Console: The LMNTRIX console provides a wealth of information about your system’s status and any threats it has detected. This can be a valuable tool for troubleshooting.
- Update Your Software: If you’re having trouble with LMNTRIX, it’s possible that you’re using an outdated version of the software. Check to see if there are any updates available and install them if necessary.
- Reinstall the Software: If all else fails, you may need to uninstall and then reinstall LMNTRIX. This can resolve issues caused by corrupted files or incorrect settings.
For more specific issues, you can reach out to support.
Remember, it’s important to keep detailed notes of any issues you encounter, as well as the steps you take to resolve them. This can be helpful if you need to contact support or if you encounter the same issue in the future.
LMNTRIX Network Detection & Response (NDR)
What is LMNTRIX NDR?
LMNTRIX NDR is a subscription feature of LMNTRIX XDR. LMNTRIX NDR uses a proprietary multi-vector threat detection sensor (NDR network sensor) to detect suspicious ingress and egress communications 24 hours a day, 7 days a week, and 365 days a year. With the application of context provided by the NDR Sensor, the service provides detection of zero-day attacks, known threats, data leakage detection, post-infection detection of bots on hosts & pre-infection detection of malware that have evaded the customer’s preventive security controls.
The LMNTRIX NDR also relies on advanced analytics and machine learning algorithms to analyze network traffic within traditional perimeter controls to identify abnormal behaviors and patterns indicative of a security threat.
- It is deployed as a virtual or physical appliance to network choke points with high-value digital assets/servers
- Scales to support small through to enterprise networks
- Continuous network monitoring and management by our Cyber Defense Center (CDC)
- Integrates with the LMNTRIX Intelligence real-time TIP solution
- Automatic incident creation in the event of a confirmed validated breach. Incidents are contained automatically or where system is unsure, incidents are confirmed by our Intrusion Analysts firsts before containment and remediation actions take place or escalated to the client/partner.
- Includes optional monitoring for OT networks where applicable
Does LMNTRIX NDR support advanced malware detection?
LMNTRIX NDR provides the following advanced malware detection capabilities:
- Detection and alerting on inbound malware targeting Customer’s network through e-mail attachments and web traffic.
- Detection against inbound malware in unencrypted and a subset of encrypted e-mail attachments. Attachments are executed and inspected for maliciousness and, if necessary, alerted on.
- Detection and alerting on existing malware infections that have evaded preventative security controls.
- Detection and alerting on malware in unencrypted web content. Web content is inspected in real time, observed for malicious behaviour and, if necessary alerted on.
What is best practice deployment architecture for the LMNTRIX NDR sensor?
The LMNTRIX NDR sensor appliance is deployed on customer’s premises in SPAN or TAP mode after the customer’s perimeter security controls (Firewalls, IPSs, WAF, DDoS, SWG, SMG, etc). It needs to at minimum monitor the internal interface of the perimeter firewall and optionally for east-west threat detection monitor the server VLAN/segment. Once deployed, the NDR Sensor is tuned to automatically connect to the LMNTRIX XDR where it’s managed and monitored by the LMNTRIX CDC. Connectivity between the LMNTRIX XDR and the NDR sensor is secured using high security industry standard encryption. All ten (10) threat detection engines constantly monitor traffic flow to detect pre-infection of malware, post-infection of bots on hosts, data leakage and alert the CDC of potential breaches.

What are the best placement strategies for the LMNTRIX NDR?
The most important decision when deploying NDR sensors is locating strategic areas for capturing network traffic. Once key network segments are identified, the NDR sensors can be deployed and optimized to meet security and administrative needs.
One more important thing to consider while deploying NDR sensors is that it should be placed after the Customer’s network perimeter controls (Firewalls, IPSs, email and web security solutions) to ensure the data is cleansed before reaching the NDR sensor.
The NDR sensor requires a SPAN/Mirror/Tap connection to passively capture packets as the data traverses your network. It is important to capture network traffic at key network segments to fully benefit from the threat detection capabilities of the NDR sensor.
The most obvious network segment to cover is the Internet Egress Gateway. The sensor can be deployed almost anywhere in your network, but most common deployments include:
- Monitoring egress traffic as it leaves the network at the perimeter/firewall.
- Internal core to monitor communication of internal traffic flows to/from servers.
- In the DMZ to capture inbound traffic to servers
- Within the corporate cloud (Amazon Web Services for example) to monitor inbound/outbound traffic flows from a corporate cloud.

What are the NDR sensor deployment requirements?
The NDR sensor is pre-configured and shipped as an appliance, VMWare, Hyper-V or KVM based on the client requirement.
Once the network segments have been identified for monitoring, the next step is to deploy the NDR sensor. The NDR sensors are typically deployed with one management interface with bi-directional access to the LMNTRIX XDR via a VPN and one or more capture interfaces. The management interface needs to be assigned a private IP to ensure it is accessible from the LMNTRIX XDR to allow for remote management.
The capture interfaces monitor traffic coming from a mirror, SPAN, or tap interface on the network infrastructure. An NDR sensor can have one or more capture interfaces depending on your architecture. Where VPN is not available, then direct Internet access is supported by opening ports to the NDR sensor from the LMNTRIX XDR.
What are the NDR sensor hardware requirements?
LMNTRIX NDR relies on the customer to provision a SPAN, mirrored or physical tap on their internal switch that will provide bi-directional flow traffic and that is configured to capture traffic from one or more monitored ports, and copy this traffic to the interface on the NDR sensor. Tap must support bidirectional copy to a single interface.
The number of NICs required depends on the network segments to be monitored. The NDR sensor must have a minimum of 2 NICs, one of which is used for establishing management connectivity to the LMNTRIX XDR and for integrating the NDR sensor with the customer’s AD server. The other NIC is used to connect to the SPAN/mirrored port on the switch. A NDR sensor can have 2 or more NICs where multiple segments need to be monitored.
The NDR sensor hardware requirements are based on the throughput requirements of your SPAN/TAP port. Below table lists the minimum hardware configuration requirements based on various throughputs. We would recommend scoping more than the minimum requirements to allow for growth.
No. CPU Cores | SPAN/TAP (Mbps) |
2 core | 200 Mbps |
4 cores | 300 Mbps |
8 cores | 600 Mbps |
12 cores | 800 Mbps |
16 cores | 1 Gbps |
20 cores | 1.2 Gbps |
24 cores | 1.4 Gbps |
CPU / SPAN Throughout Guide
The server hardware we used in our testing was as follows:
- 12 GB RAM – 5 million concurrent connections
- 2 GB RAM – 1 million concurrent connections
- VMWare ESXi 5.5 with dedicated virtual cores
- Intel E5-2637
- NICs – vmxnet3
The memory amount is based on the number of connections it needs to inspect.
The performance increase it is not linear and this may vary depending on the virtual CPU cores allocated, CPU type, RAM, traffic blend as well as hypervisor release and configuration. We believe that the most efficient performance is achieved at 8 virtual cores.
What are the NDR sensor network access requirements?
The NDR sensor needs bi-directional communication with the LMNTRIX XDR. Connectivity between the LMNTRIX XDR and the NDR sensor is secured using industry standard high security encryption and digital certificates. The NDR sensor does not support SSL decryption of the management traffic.
The NDR sensor also requires access to our XDR via the Internet to receive updates.
Two (2) forms of access are supported between the NDR sensor and the LMNTRIX XDR:
- IPSec VPN: We establish a VPN between the LMNTRIX XDR and the client’s Internet perimeter (VPN termination point) or optionally we establish a VPN directly to the NDR sensor.
- The below ACL needs to be created to enable internet access for the LMNTRIX NDR sensor.
Direction | Source | Destination | Service/Port | Remarks |
Outbound | NDR sensor IP address | Any | http(80), https(443) | To enable the internet access for NDR sensor |
- The below ACLs need to be created to allow bi-directional communication between the LMNTRIX XDR and the LMNTRIX NDR sensor. These rules are used for updating the multiple engines and remote sensor management by the LMNTRIX CDC.
Direction | Source IP | Destination IP | Port | Remarks |
Inbound | xxx.xxx.xxx.xxx/22 | NDR sensor IP address | TCP/22 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx/22 | NDR sensor IP address | TCP/256 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx/22 | NDR sensor IP address | TCP/443 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx/22 | NDR sensor IP address | TCP/3978 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx/22 | NDR sensor IP address | TCP/4488 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx/22 | NDR sensor IP address | TCP/8305 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx/22 | NDR sensor IP address | TCP/18191 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx/22 | NDR sensor IP address | TCP/18192 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx/22 | NDR sensor IP address | TCP/18208 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx/22 | NDR sensor IP address | TCP/18209 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx/22 | NDR sensor IP address | TCP/18211 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx/22 | NDR sensor IP address | TCP/28443 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx/22 | NDR sensor IP address | ICMP | To access NDR sensor from LMNTRIX XDR |
Outbound | NDR sensor IP address | xxx.xxx.xxx.xxx/22 | TCP/257 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | xxx.xxx.xxx.xxx/22 | TCP/389 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | xxx.xxx.xxx.xxx/22 | TCP/443 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | xxx.xxx.xxx.xxx/22 | TCP/3978 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | xxx.xxx.xxx.xxx/22 | TCP/8081 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | xxx.xxx.xxx.xxx/22 | TCP/8305 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | xxx.xxx.xxx.xxx/22 | TCP/8446 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | xxx.xxx.xxx.xxx/22 | TCP/9090 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | xxx.xxx.xxx.xxx/22 | TCP/18191 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | xxx.xxx.xxx.xxx/22 | TCP/18210 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | xxx.xxx.xxx.xxx/22 | TCP/18264 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | xxx.xxx.xxx.xxx/22 | ICMP | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | xxx.xxx.xxx.xxx/32 | TCP/5000 | To access LMNTRIX XDR from NDR sensor |
Note: xxx.xxx.xxx.xxx: request IP from LMNTRIX
- Direct Internet Access: With this option communication to the LMNTRIX NDR sensor is established through the Internet without the use of a VPN, although all of the communication between the sensor and the LMNTRIX Platform is encrypted by default. An unused and routable Internet IP address is required to be setup with one to one NAT.
Below are the pre-requisites for establishing communication between LMNTRIX XDR and the LMNTRIX NDR sensor without VPN:
- Bi-direction static NAT of NDR sensor with Public IP address.
- Below ACL needs to be created to enable internet access from the NDR sensor.
Direction | Source | Destination | Service/Port | Remarks |
Outbound | NDR sensor IP address | Any | http(80), https(443) | To enable the internet access for NDR sensor |
- The below ACLs need to be created to allow bi-directional communication between the LMNTRIX XDR and the LMNTRIX NDR sensor. These rules are used for updating the multiple engines and remote sensor management by the LMNTRIX CDC.
Direction | Source IP | Destination IP | Port | Remarks |
Inbound | xxx.xxx.xxx.xxx | NDR sensor Public IP address | TCP/22 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx | NDR sensor Public IP address | TCP/256 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx | NDR sensor Public IP address | TCP/443 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx | NDR sensor Public IP address | TCP/3978 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx | NDR sensor Public IP address | TCP/4488 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx | NDR sensor Public IP address | TCP/8305 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx | NDR sensor Public IP address | TCP/18191 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx | NDR sensor Public IP address | TCP/18192 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx | NDR sensor Public IP address | TCP/18208 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx | NDR sensor Public IP address | TCP/18209 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx | NDR sensor Public IP address | TCP/18211 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx | NDR sensor Public IP address | TCP/28443 | To access NDR sensor from LMNTRIX XDR |
Inbound | xxx.xxx.xxx.xxx | NDR sensor Public IP address | ICMP | To access NDR sensor from LMNTRIX XDR |
Outbound | NDR sensor IP address | 35.175.38.253 | TCP/257 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | 35.175.38.253 | TCP/389 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | 35.175.38.253 | TCP/443 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | 35.175.38.253 | TCP/3978 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | 35.175.38.253 | TCP/8081 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | 35.175.38.253 | TCP/8305 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | 35.175.38.253 | TCP/8446 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | 35.175.38.253 | TCP/9090 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | 35.175.38.253 | TCP/18191 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | 35.175.38.253 | TCP/18210 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | 35.175.38.253 | TCP/18264 | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | 35.175.38.253 | ICMP | To access LMNTRIX XDR from NDR sensor |
Outbound | NDR sensor IP address | 34.192.245.94 | TCP/5000 | To access LMNTRIX XDR from NDR sensor |
Note: xxx.xxx.xxx.xxx: request IP from LMNTRIX
What is the NDR sensor performance impact on our network?
All events generated by the ten (10) NDR engines are sent to the LMNTRIX XDR using an API where they are automatically validated and turned into incidents where applicable.
There is no concept of packet capture or connection log in the NDR sensor. All events are exclusively threat related and they are meta data only (like an IDS alert). As such the volume of threat data passed from the sensor to the XDR platform is minimal and has inconsequential impact on the Customer(s) Internet connection.
The LMNTRIX NDR service does not retain any events or logs. The LMNTRIX XDR receives meta data from the sensors which are automatically validated by the XDR and if deemed a threat they are contained. If unsure, alerts are converted into incidents where an intrusion analyst conducts further investigation including endpoint analysis before containment and remediation actions take place.
LMNTRIX NDR is not a log management nor a compliance solution as we do not collect or retain any logs.
How does the NDR sensor detect encrypted attacks
The use of Secure Sockets Layer (SSL) or Transport Layer Security (TLS) encryption for Internet and enterprise traffic is growing steadily. Modern applications that use SSL communications by default – such as SharePoint, Exchange, WebEx, Salesforce.com and Google Apps – are commonplace and rapidly growing. Even hosted and mobile email applications such as Gmail, Yahoo and Zimbra utilize SSL encryption by default in today’s workplace environments.
LMNTRIX highly recommends clients to complete their visibility into the encrypted SSL-based traffic with the use of either dedicated appliances or by turning on the SSL Inspection feature of their existing Firewalls.
A holistic encrypted traffic management strategy that considers the various division needs, policies to be established, regulatory compliance requirements, and data privacy mandates is essential for all clients.
The NDR sensor cannot natively detect threats within encrypted traffic and instead it relies on external solutions to deliver decrypted content of SSL flows. This enables LMNTRIX to deliver the necessary visibility into both SSL and non-SSL network traffic.
Supported 3rd party SSL decryption solutions to manage encrypted traffic include those from Garland Technology, Blue Coat (SSL Visibility Appliance and ProxySG solution), Radware (Content Inspection Director (CID) and AppXcel), A10 Networks (Thunder SSLi) and Gagamon (GigaSMART).
Some NetGen Firewall vendors such as Palo Alto Networks support SSL inspection and the ability forward on the clear SSL flows off box to a 3rd party solution such as the LMNTRIX NDR sensor.
What are the LMNTRIX responsibilities as it relates to the operation of the LMNTRIX NDR?
The following provides a list of LMNTRIX responsibilities:
- Provide a license to use the LMNTRIX NDR service consistent with the parameters of your purchase.
- If applicable, LMNTRIX authorized partner will provide some of the hardware components required to implement the service.
- Configuration of the NDR sensor ready for deployment by LMNTRIX authorized channel partner or Customer
- Provide remote assistance for implementing the Service. Implementations will need to be scheduled through an assigned project manager.
- Establishing management connectivity between the NDR sensor and the LMNTRIX XDR.
- Fine Tuning the policies of various Engines to reduce false positives.
- Perform all the required maintenance of the software running on the NDR sensor.
- Perform remote health monitoring of Service components that are deployed in your environment.
- Provide 24-hour access to our Cyber Defense Center (“CDC”) so that you may ask questions related to the Service. While LMNTRIX will do our best to answer your questions immediately, some inquiries will result in a ticket for the Senior Intrusion Analyst Team which will be addressed during LMNTRIX’ normal business hours, Monday through Friday, 8:00-5:00 U.S. Eastern Standard Time excluding U.S. holidays (“Normal Business Hours”).
What are client responsibilities as it relates to the operation of the LMNTRIX NDR?
The following provides a list of Client responsibilities:
- Providing an installation environment as required for the Customer-controlled components of the Service. This may include, but is not necessarily limited to, one or more of the following: rack space, power, cooling, network connectivity, a provisioned cloud environment, virtual machine licenses, and hardware to support a virtual sensor.
- Procurement of sensor hardware as per throughput requirements and number of network segments to be mirrored. (Hardware specifications need to be validated by LMNTRIX).
- Locating strategic areas for capturing network traffic to deploy the sensor(s).
- Allotment of private IP address for the NDR sensor management interface for bi-directional communication with the LMNTRIX XDR and LMNTRIX specified 3rd party vendor threat update clouds. Provide default gateway details for the NDR sensor to connect to the LMNTRIX XDR, the Internet and for AD integration.
- Create an access rule on Perimeter firewall(s) for allowing bi-directional access to sensor private IP address.
- Identifying the specific systems or Internet Protocol (“IP”) address ranges that are to be monitored, and providing updates to LMNTRIX when changes to systems that are to be monitored occur.
- Configuring SPAN port or TAP where SPAN is not available.
- Ensuring that the NDR subscription covers the corresponding network throughput.
What are the NDR sensor threat detection engines?
The NDR sensor employs ten (10) threat detection engines. These are:

What is the LMNTRIX NDR Context Awareness Engine?
Context awareness engine removes the traffic origin anonymity by mapping the IP addresses to user’s identities. This helps deliver context to the CDC based on identity instead of only IP addresses. When the Context Awareness Engine identifies a source and destination, it shows the IP address of the user or machine with a name.
Context Awareness Engine gets identity data seamlessly from Microsoft Active Directory using AD Query. It works based on querying the Active Directory Security Event logs and extracting the user and machine mapping to the network address from them.
The NDR sensor can be integrated with AD server using either AD administrator or non-AD administrator credentials.
Below procedure describes on how to integrate AD Using Context Awareness AD Query without Active Directory Administrator privileges on Windows Server 2008 and above
AD Query uses Windows Management Instrumentation (WMI) to query Active Directory Domain Controllers for the Security Event logs. To handle the remote calls to the Domain Controllers, AD Query uses Distributed COM (DCOM) technology. In order to connect to a remote computer using WMI, WMI permissions should be granted, and DCOM settings and WMI namespace security settings should enable the connection. After a user/group can connect to the Domain Controller using WMI, it should have the permissions to read the Security Event logs.
There are four main stages:
- Creating a user/group and granting it DCOM permissions.
- Giving the user/group WMI permissions.
- Adding read permissions to the Security Event logs.
- Create a user with Distributed COM and Event reading permissions
- Create a domain user (or use an existing one).
- Add this user to the built-in domain groups: Distributed COM Users, Event Log Readers, and Server Operators.
- Make sure that DCOM remote launch activation permissions and remote access permissions are granted for the Distributed COM Users group (as described in Securing a Remote WMI Connection)):

- Make sure the user is a member of the following groups:
- Distributed COM Users
- Domain Users
- Event Log Readers
- Server Operators
- Grant the user WMI permissions
Note: This step should be performed on each Domain Controller.
- Run Windows Management Instrumentation (WMI) console:
Go to Start menu – click on Run… – type wmimgmt.msc – click on OK/press Enter.
A.Right-click on WMI Control – click on Properties.

B. Go to the Security tab – expand Root.
C. Select CIMV2 – click on Security button.

D. Add the domain user that you have created to work with AD Query.
Grant him the Remote Enable permission.

E. Click on Advanced button.
F. Make sure that the permissions for the domain user apply to This namespace and subnamespaces.

G. Click on OK and close the dialogs.
4. Restart WMI service
Note: This step should be performed on each Domain Controller.
Run the Windows Services Manager:
Go to Start menu – click on Run… – type services.msc – click on OK/press Enter.
- Locate the Windows Management Instrumentation service and restart (right-click on the service – click on Restart).

Client Responsibilities:
- Enable the Network connectivity between NDR sensor and AD Server.
- Providing AD service account details for NDR sensor integration with AD server.
What is the LMNTRIX NDR Data Leakage Detection Engine?
The Data Leakage Detection Engine identifies, monitors and detects data transfer through deep content inspection and analysis of transaction parameters such as source, destination, data object and protocol. The intent of the Data Leakage Detection Engine is to detect the unauthorized transmission of confidential information to and from the client network(s).
The Data Leakage Detection Engine captures original data that caused a rule match, including the body of the transmission and attached files. The policy is defined by LMNTRIX to match the data that should be detected from transmission, based on customer’s data policy. A set of defined data types recognizes sensitive forms, templates, and data to be detected. The policy is fine-tuned continuously by LMNTRIX to convert the confidentiality and integrity guidelines of the customer’s organization into automated rules. New data types are created to match the customer specific data monitoring requirements.
Even without any data leakage policies defined by the client, the Data Leakage Detection Engine by default uses pre-defined Data Types and rules developed by LMNTRIX to provide advanced Data Leakage Detection capability. The NDR sensor monitors all the traffic containing data and being sent through supported protocols. This includes users sending data via a HTTP proxy or a mail server, the Data Leakage Engine monitors the data before it leaves the organization. The Data Leakage Engine scans the traffic, including email attachments, for data that should be protected from being sent outside the organization. This data is recognized by protocol, source, destination, and complex Data Type representations.
The Data Leakage Detection Engine captures traffic and scans it against the Data Leakage Detection policy. If the data in the traffic matches a rule in the policy, an incident is logged and a ticket automatically generated on the LMNTRIX XDR.
LMNTRIX Responsibilities:
- CDC to configure and fine tune the Data Leakage Detection Policy.
Client Responsibilities:
- Specify any key words and Data types to monitor for data leak detection.
- Provide Email address domains list.
- Provide list of internal networks or hosts.
What is the LMNTRIX NDR Web Security Engine?
Today, the businesses struggle to keep up with the security challenges because of the wide adoption of social media and web applications by the people. The usage of internet applications creates a new set of challenges such as Malware threats, Bandwidth hogging and a Loss of Productivity. As with internet applications, access to the non-work related website browsing can open networks to a variety of security threats and have a negative effect on employee productivity.
Web Security Engine provides detection capabilities by using the Granular Application Control, Largest Application Library, by detecting the employee’s internet access to inappropriate and illicit websites, by detecting bandwidth issues and it also helps in decreasing the legal liability and improves organizational security.
The LMNTRIX CDC constantly fine tunes the Web Security policy to match the customer’s environment. Traffic that matches the active pre-defined policy creates an event which further creates an incident on the LMNTRIX XDR.
LMNTRIX Responsibilities:
- CDC to configure and fine tune the Web Security Engine Policy.
Client Responsibilities:
- Specify any custom URL and application categories to monitor.
What is the LMNTRIX NDR Intrusion & Web Application Detection Engines?
The Intrusion & Web Application Detection Engines analyse traffic contents to find potential risks to the customer’s network. This engine provides, detection of specific known exploits; detection of vulnerabilities including both known and unknown exploit tools; detection of protocol misuse which in many cases indicates malicious activity or potential threat; detection of outbound malware communications, detection of tunneling attempts; detection of applications which are bandwidth consuming or may cause security threats to the network such as peer to peer and Instant Messaging applications.
The Intrusion & Web Application Detection Engines constantly update the library of detections to stay ahead of emerging threats. During service inception, detections are activated as per Intrusion & Web Application Detection policy to allow processes to focus on handling the most important traffic and to report on only the most concerning threats. The LMNTRIX CDC constantly fine tunes the policies which activate only the detections that are tuned to match the customer asset type on each segment. For example, a segment of Windows machines do not require monitoring for Mac or Unix based threats. This ensures that we detect only the attacks that most threaten the customer’s network and help reduce false positives. Furthermore, Intrusion & Web Application Detection profiles enable LMNTRIX to configure a set of detections per NDR sensor. Detections are activated with Medium or Higher severity level, Medium or lower performance impact and Medium or higher confidence level.
Exceptions are configured on the NDR sensor for all the traffic monitored by the sensor or at a specific detection level, to detect certain traffic from being identified by the Intrusion & Web Application Detection policies or specific detection. Intrusion & Web Application Detection signatures are updated hourly using an automated schedule. Traffic that matches the active pre-defined signatures creates an event which further creates an incident on the LMNTRIX XDR.
LMNTRIX Responsibilities:
- CDC to configure and fine tune the Intrusion & Web Application Detection Engine Policies.
Client Responsibilities:
- Specify internally hosted applications.
- Specify the DNS servers, SNMP server, NIS servers, LDAP Servers, HTTP Proxy servers, Anti-Virus definition servers, Mail relay server IP addresses and Vulnerability scanner IP addresses.
What is the LMNTRIX NDR Emulation Engine (sandbox)?
The Emulation Engine provides the NDR sensor with pre-infection defense approach. It detects unknown malware, targeted attacks and zero-day attacks. Cyber-threats continue to increase and now it is easier for criminals to create new malware that can easily bypass existing protections. Cyber criminals can change the malware signature and make it virtually impossible for signature based products to protect networks against infection. Emulation Engine can detect new malware and zero-day vulnerabilities and targeted attacks.
Emulation Engine gives networks the necessary detection capabilities against unknown threats in files that are downloaded from the internet or attached to emails. Emulation is being performed by opening files on more than one virtual computer with different operating system environments. The virtual computers are closely monitored for unusual and malicious behavior, such as an attempt to change registry keys or run unauthorized process. Emulation can be conducted on the LMNTRIX Cloud or on the NDR sensor. However, when conducted on the cloud, CPU level emulation (not available on the on-premise sensor) is able to detect far many more advanced threats not possible by the standalone NDR sensor. Furthermore, if on premise emulation is necessary then LMNTRIX highly recommends the use of a dedicated appliance for the Emulation Engine, to help minimize the performance impact on the NDR sensor.
When the analysis is conducted on the LMNTRIX Cloud, all the communication between the NDR sensor and the LMNTRIX Cloud is secured using SSL encryption.
What is the LMNTRIX NDR Anti-Malware Engine?
The Anti-Malware Engine provides the NDR sensor with pre-infection defense approach where it helps in detecting known viruses and file transfers. Malware is a major threat to network operations that has become increasingly dangerous and sophisticated. The Anti-Malware Engine scans incoming and outgoing files to detect threats such as worms and Trojans. It also delivers pre-infection detection capability from malware contained within files.
The Anti-Malware Engine detects infections from incoming malicious file types such as Word, Power Point, Excel and Adobe). Incoming files are classified on the NDR sensor and compared against the known malicious files. The Anti-Malware Engine also detects malware downloaded from the internet by monitoring access to the sites that are known to be connected to malware. Accessed URLs are checked by the NDR sensor caching mechanisms or sent to the cloud repository to determine if they are permissible or not.
Detections are activated with Medium or Higher severity level, Medium or lower performance impact and Medium or higher confidence level. The traffic which matches the pre-defined Anti-Malware criteria is immediately logged and incidents generated in the CDC ticketing system.
What is the LMNTRIX NDR Bot Detection Engine?
The Bot Detection Engine provides the NDR sensor with post-infection bot detection approach. A Bot is a malicious software that can invade the endpoint machine. There are many infection methods such as opening attachments that exploit a vulnerability and accessing a web site that results in a malicious download.
When a bot infects a computer, it takes control over the computer and neutralizes its Anti-Virus defenses. Bots are difficult to detect since they hide within the computer and change the way they appear to Anti-Virus software. It then connects to a Command and control (C&C) center for instructions from cyber criminals. The cyber criminals or bot herders, can remotely control it and instruct it to execute illegal activities without the owner’s knowledge. A single bot can create multiple threats. Bots are often used as tools in attacks known as Advanced Persistent Threats (APT) where cyber criminals pinpoint individuals or Organizations for attack. A botnet is a collection of compromised computers.
The Bot Detection Engine identifies infected machines in the organization by analyzing the network traffic using the inbuilt threat engine. It uses the cloud repository to receive updates and queries it for classification of unidentified IPs and URLs. It detects bot communication to C&C sites and alerts if the sensitive information is stolen or sent out of the organization.
The Bot Detection Engine identifies bot infected computers by correlating multiple detection methods such as by identifying the command and control addresses used by criminals to control bots, by identifying the communication patterns used by each botnet family, by identifying bot behavior such as detecting attack types, such as Spam (leveraging outbound mail analysis) and Click fraud, as well as anomalies (irregular ports, protocols).
Following the discovery of a bot infected machine, the Bot Detection Engine logs the event and an incident is automatically generated on the LMNTRIX XDR for further analysis by the CDC.
What is the LMNTRIX NDR Email Security Engine?
Email Security Engine detects wide variety of virus and malware threats delivered through mail. It offers antivirus detection with both zero-hour and signature based detection. It also offers Email IDS detection against Denial of Service (DoS) and buffer over-flow attacks.
Mail anti-malware detects against a wide range of viruses and malware and includes scans of message content and attachments. Email Security Engine includes a highly-rated anti-malware engine that scans POP3 and SMTP mail protocols. This layer of detection detects a wide range of known virus and malware attacks, and is at the core of the anti-malware defense. The Email Security Engine utilizes Email IDS to effectively detect attacks targeting the messaging infrastructure. Such attacks aim to gain access to the protected network, bring down a piece of the messaging infrastructure, or utilize the messaging infrastructure as a resource for launching new attacks.
What is the LMNTRIX NDR Anti-Spam Engine?
The relentless and unprecedented growth in unwanted email poses an unexpected security threat to the network. As the amount of resources allocated to handling unsolicited emails increases from year to year, employees waste more and more time sorting through unsolicited bulk email commonly known as spam. The Anti-Spam Engine allows LMNTRIX to detect spam that was missed by the clients Mail Security Gateway solution and has now reached the customer’s network.
Anti-Spam Engine identifies spam by analyzing known and emerging distribution patterns. It’s strength lies within its ability to avoid searching for key words and phrases that might classify a legitimate email as spam and instead of focusing on other message characteristics, this method offers high spam detection rate with a low number of false positives. To preserve the personal privacy and business confidentiality, only selected characteristics are extracted from the message envelope, headers and body. Hashed values of these message characteristics are sent to a Detection center cloud for pattern analysis. The Detection center cloud identifies spam outbreaks in any language, message format, or encoding type.
The Anti-Spam Engine performs detection based on features such as Content based Anti-Spam, Mail Anti-Virus, IP reputation Anti-Spam, Block List anti-spam, Zero-hour malware protection and IDS.
Once identified the network spam generating machine, events are logged and followed by the automatic creation of an incident ticket on the LMNTRIX XDR.
What is the LMNTRIX NDR Threat Intelligence Engine?
The NDR sensor Threat Intelligence Engine integrates the LMNTRIX Threat Intelligence Platform (TIP) feed. This feed is updated hourly from the LMNTRIX XDR.
LMNTRIX Intelligence is the LMNTRIX initiative for crowd-sourcing threat intelligence. It is a community based immunity system that aggregates over 300 threat feeds into a single feed and correlates it against all incoming and outgoing communication from a Client’s network seen by the NDR sensor.
Any positive hits on the Indicators of Compromise (IOCs) from the TIP automatically create an incident ticket on the LMNTRIX XDR. The ticket is validated for any false positives by the CDC before escalating to the client.
LMNTRIX Cloud
What is LMNTRIX Cloud?
LMNTRIX Cloud provides customers with an end-to-end solution for securing public cloud workloads across AWS, Azure and GCP. It functions via APIs and does not require the installation of any agent. The service is designed to offer complete protection for AWS, Azure and GCP workloads. It provides a variety of protective layers to secure application infrastructure and workloads that are hosted in public cloud environments, preventing unauthorized access, misconfigurations, and malicious activity. LMNTRIX Cloud contextualizes the cloud, application, and user behavior in your environment and creates an attack storyline to identify actual threats. By focusing on actual threats in the runtime, LMNTRIX improves productivity and morale of the SOC and reduces business risk.
The service includes Cloud Security Posture Management (CSPM) and Identity Threat Detection and Response (ITDR) services. A runtime Cloud Threat Detection and Response (CDR) service monitors and analyzes all threat vectors of identity, permissions, exposed assets, and unauthorized access to identify real-time risk.

Does LMNTRIX Cloud provide multi-cloud support?
LMNTRIX Cloud provides centralized visibility into the current security risks identified across multiple accounts, regions, and cloud platforms. It helps drive corrective actions according to the severity and urgency of the risks for the organization. Alerts are published to the LMNTRIX XDR KILLBOX in the same way as all other service elements, providing unrivalled visibility across your environment. As with all other service elements, alerts are fully validated by CDC analysts prior to the creation of an incident.
Does LMNTRIX Cloud provide compliance assurance and reporting?
LMNTRIX Cloud continuously monitors the configuration of your cloud and alerts you to risky misconfigurations, as well as on violations of security best practices and industry standards. LMNTRIX Cloud offers comprehensive reporting of your cloud inventory, exposure, and misconfigurations. It can generate on-the-fly compliance reports against many standards including SOC2, PCI DSS, NIST CSF, Azure & AWS CIS, ISO27001, HIPAA and GDPR. This level of monitoring shows the SOC how misconfigurations are being used to penetrate your environment. This is especially helpful with misconfigurations that cannot be addressed or take time to be addressed. This level of monitoring reduces the risk of misconfigurations that your business must tolerate.
Does LMNTRIX Cloud offer excessive permissions hardening?
LMNTRIX Cloud continuously monitors all Identity and Access Management (IAM) user and role activity in the cloud and tracks how different IAM entities utilize the access permissions they have been granted. By comparing granted permissions to what has actually been used over time, LMNTRIX Cloud identifies excessive access permissions and provides actionable recommendations on how to reduce them- delivered regularly as incidents via the XDR portal.
How does LMNTRIX Cloud deliver threat detection?
LMNTRIX Cloud utilizes dozens of algorithms, including machine learning and deep learning-based, to detect suspicious activity and anomalous behavior across multiple layers of the cloud environment, from user and role activity to east-west and south-north network communications to host activity. LMNTRIX leverages malicious behavior indicators to create an attack sequence. Malicious behavior indicators (MBIs) are behaviors and activities that we flag over time and build into a sequence based on the metadata and logs we are collecting from the cloud. An MBI alone is not usually indicative of an attack, but it is indicative of an interesting activity. A string of MBIs creates an attack sequence and once the overall score of a sequence reaches a specific threshold it is determined to be an alert.
The Detection Process

By using cloud logs, enriching them with status information gained from our API based posture management, applying our ML detections and historical knowledge we create high alerting and validated incidents for your cloud environment.
Attack Stories
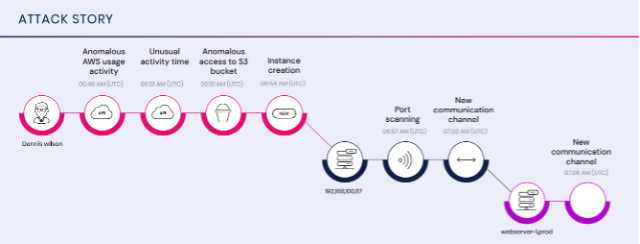
Leveraging the full platform logging and visibility, combined with the high-fidelity alerting, we are able to create timelines that represent an adversaries use of tactics, techniques and procedures in your environment.
What telemetry is collected from Azure cloud and what permissions are required ?
Integration of your cloud environment with LMNTRIX cloud security is simple and can be performed within the space of an hour. Separate integration guides have been prepared for each public cloud provider. Our service requires no agents or appliances, making use of built-in API and application functionality.
LMNTRIX Cloud collects and processes the following Azure telemetry:
- Subscription-level telemetry:
- Configuration metadata describing the cloud resources including VMs, databases, and network security groups
- Subscription Activity logs
- Network Flow logs
- Tenant-level telemetry includes:
- Configuration metadata describing users and roles
- LMNTRIX cloud makes use of the following read only permissions:
- Read. All (required)
- A tenant-level read-only permission allowing LMNTRIX cloud security to access information related to Identity and Access Management (IAM).
- Reader (required):
- A subscription-level read-only permission allowing LMNTRIX cloud security to access configuration metadata in your Azure subscriptions.
- Storage Blob Data Reader (optional):
- A storage account-level permission allowing LMNTRIX cloud security to access Activity and Network Flow logs in a specified storage account.
- Read. All (required)
What telemetry is collected from AWS cloud and what permissions are required?
Integration of your cloud environment with LMNTRIX cloud security is simple and can be performed within the space of an hour. Separate integration guides have been prepared for each public cloud provider. Our service requires no agents or appliances, making use of built-in API and application functionality.
LMNTRIX Cloud collects and processes the following AWS telemetry:
- Configuration metadata describing the account settings and its deployed cloud resources, including EC2 instances, databases, security groups, and users.
- CloudTrail logs providing event history of your AWS account activity, including actions taken through the AWS Management Console, AWS SDKs, command line tools, and other AWS service account activity related to actions across your AWS infrastructure.
- Note: CloudTrail logs are collected by LMNTRIX cloud Security from S3 buckets.
- VPC Flow logs capture information about the network traffic going to and from network interfaces in your VPCs.
- CloudTrail S3 Data event logs capture data events for objects stored in an S3 bucket. Once enabled, these S3 data events are delivered by AWS as part of the regular CloudTrail logs. LMNTRIX recommends that you enable CloudTrail S3 Data event logs for those S3 buckets that hold information critical for your business. For more information, see: https://docs.aws.amazon.com/AmazonS3/latest/userguide/enable-cloudtrail-logging-fors3.html
LMNTRIX cloud makes use of the following read only permissions (granted to LMNTRIX cloud by assigning IAM permission policies to a cross-account role created for LMNTRIX cloud security in the customer’s AWS account.):
- Security Audit policy—An AWS-managed policy provided out-of-the-box. This policy grants access to read security configuration metadata, such as information about the configuration of users, servers, databases, and more.
- AWSWAFReadOnlyAccess policy—An AWS-managed policy provided out-of-the-box. This policy provides read-only access to AWS WAF configuration metadata.
- Read-access permissions to the S3 buckets in the AWS account(s) storing the CloudTrail and VPC Flow logs:
- s3:ListBucket
- s3:Get*
- In addition, you need to set up SNS notifications in your AWS account. https://docs.aws.amazon.com/AmazonCloudWatch/latest/monitoring/US_SetupSNS.html
What are LMNTRIX responsibilities during LMNTRIX Cloud onboarding?
- Provide a license to use the LMNTRIX Cloud service consistent with the parameters of your purchase.
- Provide the customer or partner with the required information to complete the integration of their public clouds with LMNTRIX Cloud.
- Assist with configuration of cloud policy & response.
- Provide 24-hour access to our Cyber Defense Center (“CDC”) so that you may ask questions related to the Service. While LMNTRIX will do our best to answer your questions immediately, some inquiries will result in a ticket for the Senior Intrusion Analyst Team which will be addressed during LMNTRIX’ normal business hours, Monday through Friday, 8:00-5:00 U.S. Eastern Standard Time excluding U.S. holidays (“Normal Business Hours”).
What are Client responsibilities during LMNTRIX Cloud onboarding?
- Complete the LMNTRIX Cloud section of the starter pack.
- Integration of their cloud environment with us per the relevant integration guide.
- Providing LMNTRIX with the required permissions and information to establish the service.
- Configure logging as appropriate to make use of threat detection service.
- Maintain awareness of all public cloud vendor fees, especially as related to logging.
LMNTRIX Mobile
What is LMNTRIX Mobile?
LMNTRIX Mobile is a subscription feature of LMNTRIX XDR. LMNTRIX Mobile is a Mobile Threat Defense (MTD) privacy-first application that provides comprehensive mobile security for enterprises. LMNTRIX Mobile is designed to protect an employee’s corporate-owned or BYO device from advanced persistent threats without sacrificing privacy or personal data.
Once deployed on a mobile device, LMNTRIX Mobile begins protecting the device against all primary attack vectors, even when the device is not connected to a network. LMNTRIX reduces risk by analyzing risky apps and jailbreaks on the device before giving access to corporate email and apps.
- Detects threats from device compromises, network attacks, phishing and content, and malicious apps
- Integrates with LMNTRIX XDR to provide CDC visibility of mobile threats and risks
- Offers unmatched forensics capabilities for devices, network connections, and malicious applications

How does LMNTRIX Mobile work?
LMNTRIX Mobile employs a robust defense strategy against threats targeting mobile devices by using machine learning. This engine operates directly on mobile devices and conducts a meticulous analysis of device behavior across various dimensions, including device activities, network interactions, phishing attempts, and application behavior. The machine learning engine has the ability to identify both familiar and previously unknown malware threats, including zero-day exploits. Its threat detection capabilities encompass a wide range of malicious software, such as ransomware, spyware, adware, trojans, and keyloggers, among others. A notable feature of machine learning engine is its self-sufficiency, as it does not rely on traditional security methods like signatures, cloud connectivity, or periodic updates to detect threats. It operates seamlessly in real-time and even offline, ensuring uninterrupted protection for mobile devices.
LMNTRIX Mobile protects users and their devices from many types of threats. These threats are broadly categorized into Network, Device and Malware threats.

What type of network threats does LMNTRIX Mobile support?
Network threats encompass attacks that take advantage of vulnerabilities within the networks utilized by mobile devices, including Wi-Fi, cellular, or Bluetooth. Several examples of network threats are as follows:
- Rogue Access Points (RAPs): These are deceptive or malicious Wi-Fi hotspots designed to deceive users into connecting to them, subsequently intercepting their data or delivering malware.
- Man-in-the-Middle (MITM) Attacks: These attacks involve an adversary intercepting and altering communication between two parties, such as a user and a website, without their awareness.
- SSL Stripping: This represents a form of MITM attack that degrades the security of a website from HTTPS to HTTP, facilitating the theft of sensitive information or the injection of malicious content.
- DNS Hijacking: This type of attack redirects users to fraudulent websites by modifying the DNS settings of the device or the network.
LMNTRIX Mobile detects network threats by analyzing both device behavior and network traffic. It has the capability to recognize anomalous or malicious network activities, including RAPs, MITM attacks, SSL stripping, DNS hijacking, and more. Additionally, it promptly notifies users and implements predefined remediation actions based on established rules.
What type of device level threats does LMNTRIX Mobile support?
The Device threat vector is one of the categories of threats that LMNTRIX Mobile identifies and mitigates. This category pertains to attacks that exploit vulnerabilities within the device’s operating system, kernel, or configuration. Examples of device threats include:
- OS/kernel exploits.
- Modifications to profile configuration.
- System tampering.
- Exploits targeting physical USB or SD card interfaces.
- Tracking using smart tags.
- Unpatched mobile operating systems.
- Vulnerable mobile operating systems.
LMNTRIX Mobile leverages machine learning to analyze the device’s behavior, allowing it to detect any deviations from the normal state. This proactive approach enables LMNTRIX Mobile to identify and respond to device threats effectively, enhancing the security and integrity of the device and its data.
Can LMNTRIX Mobile detect provide protection against malware?
Malware threats refer to malicious applications that can inflict harm on mobile devices by stealing data, spying on users, or engaging in undesirable activities. LMNTRIX Mobile, a mobile threat defense solution, is equipped to detect and thwart these malware threats effectively. LMNTRIX Mobile harnesses advanced machine learning algorithms to scrutinize the behavior of both the device and its applications, thereby enabling it to identify known as well as previously unknown malware threats. Several examples of malware threats that LMNTRIX Mobile can detect include:
- Spyware: This category encompasses malware that operates covertly to monitor the user’s activities, such as phone calls, messages, location data, or browsing history. It then surreptitiously transmits this information to a remote server.
- Ransomware: Ransomware is a malicious software that encrypts the user’s data or locks the device, typically demanding a ransom for the restoration of access.
- Banking Trojans: Banking trojans are malware designed to target financial or banking applications, with the goal of pilfering the user’s credentials, account information, or financial resources.
- Rootkits: Rootkits are a class of malware that acquire root or administrative privileges on the device, effectively concealing their presence from detection and removal tools.
To safeguard mobile devices from these malware threats, LMNTRIX Mobile employs a multi-faceted approach. It promptly notifies the user of any detected threats and takes predefined remedial actions.
Does LMNTRIX Mobile provide policy enforcement?
LMNTRIX Mobile allows for highly customizable policy enforcement across user defined device groups. Customizable policy sets exist for:
- Privacy
- Control access to device location, network information, application details, browser and device information.
- Threats
- Control on device alerting, automated response and notifications for more than one hundred different types of device-based threats.
- Phishing
- Control protection for phishing links received on the device, including custom filtering and web category handling.
- App settings
- Control ML malware detection and the availability of other features through the LMNTRIX Mobile application.
- App Policy
- Control alerting based on application IDs, versions, developer signatures, etc.
- Network Policy
- Control access to specific WiFi networks, SSL Certificates & sinkhole network access ot specific IP addresses, Domains, or Countries.
- Device Inactivity
- Control alerting based on device and application inactivity.
- OS Risk
Control alerting based on device OS being out of compliance.
How is LMNTRIX Mobile deployed?
Deployment of LMNTRIX Mobile is accomplished in one of two different ways:
- For managed devices, LMNTRIX Mobile can be integrated with a mobile device management (MDM) or enterprise mobility management (EMM) solution, such as VMware Workspace ONE, Microsoft Intune, IBM MaaS360, or MobileIron to allow for zero touch provisioning.
LMNTRIX Cloud collects and processes the following AWS telemetry:
- Configuration metadata describing the account settings and its deployed cloud resources, including EC2 instances, databases, security groups, and users.
- CloudTrail logs providing event history of your AWS account activity, including actions taken through the AWS Management Console, AWS SDKs, command line tools, and other AWS service account activity related to actions across your AWS infrastructure.
- Note: CloudTrail logs are collected by LMNTRIX cloud Security from S3 buckets.
- VPC Flow logs capture information about the network traffic going to and from network interfaces in your VPCs.
- CloudTrail S3 Data event logs capture data events for objects stored in an S3 bucket. Once enabled, these S3 data events are delivered by AWS as part of the regular CloudTrail logs. LMNTRIX recommends that you enable CloudTrail S3 Data event logs for those S3 buckets that hold information critical for your business. For more information, see: https://docs.aws.amazon.com/AmazonS3/latest/userguide/enable-cloudtrail-logging-fors3.html
LMNTRIX cloud makes use of the following read only permissions (granted to LMNTRIX cloud by assigning IAM permission policies to a cross-account role created for LMNTRIX cloud security in the customer’s AWS account.):
- Security Audit policy—An AWS-managed policy provided out-of-the-box. This policy grants access to read security configuration metadata, such as information about the configuration of users, servers, databases, and more.
- AWSWAFReadOnlyAccess policy—An AWS-managed policy provided out-of-the-box. This policy provides read-only access to AWS WAF configuration metadata.
- Read-access permissions to the S3 buckets in the AWS account(s) storing the CloudTrail and VPC Flow logs:
- s3:ListBucket
- s3:Get*
- In addition, you need to set up SNS notifications in your AWS account. https://docs.aws.amazon.com/AmazonCloudWatch/latest/monitoring/US_SetupSNS.html

- For unmanaged devices, users simply download the LMNTRIX Mobile application & scan a provided QR code to enrol their devices.
What are LMNTRIX responsibilities during the LMNTRIX Mobile onboarding process?
- Provide a license to use the LMNTRIX Mobile service consistent with the parameters of your purchase.
- Provide the customer or partner with the required information to complete the enrolment of their devices with LMNTRIX Mobile.
- Provide assistance with configuration of mobile security policy & MDM integration.
- Provide 24-hour access to our Cyber Defense Center (“CDC”) so that you may ask questions related to the Service. While LMNTRIX will do our best to answer your questions immediately, some inquiries will result in a ticket for the Senior Intrusion Analyst Team which will be addressed during LMNTRIX’ normal business hours, Monday through Friday, 8:00-5:00 U.S. Eastern Standard Time excluding U.S. holidays (“Normal Business Hours”).
What are Client responsibilities during the LMNTRIX Mobile onboarding process?
- Complete the LMNTRIX Mobile section of the starter pack.
- Supply all requested details of mobile endpoints & users.
- Integrate LMNTRIX Mobile with MDM solution where applicable.
- Enrol devices in LMNTRIX Mobile.
LMNTRIX Deceive
What is LMNTRIX Deceive?
LMNTRIX Deceive is a subscription feature of LMNTRIX XDR and an integral part of our Active Defense architecture. Our approach weaves a deceptive layer over your entire network – every endpoint, server and network component is coated with deceptions. The moment an attacker penetrates your network, they are in an illusive world where all the data is unreliable. If attackers cannot collect reliable data, they cannot make decisions. And if they cannot make decisions, the attack is paralysed. This approach provides the following benefits:
- No false positives – every alert is treated as a major incident and escalated to you
- Turn the tables on the bad guys!
- Change the economics of cyber defence by shifting the cost to the attacker
The intent of the service is to address insider threats and advanced human adversaries that are now on your network moving laterally stealing data and actively working to elevate their privileges. Existing solutions such as SIEM, IPS, EDR, Sandboxes, NextGen Firewalls, Web and Email Gateways are defenseless against this threat vector. By deploying deceptions everywhere, we are able to address this difficult threat vector.
LMNTRIX Deceive changes the asymmetry of cyber warfare, by focusing on the weakest link in a targeted attack – the human team behind it. Targeted attacks are orchestrated by human teams. And humans are always vulnerable. Advanced attackers rely on one simple fact – that what they see is real and that the data they collect is reliable. Firewall, Anti-virus, EDR, Sandbox, IDS, and intelligence feed technologies generate so much data that the signal is lost.
Attackers prowling a target network look for juicy content. They browse Active Directory for file servers and explore file shares looking for documents, try default passwords against network devices and web services, and scan for open services across the network.
LMNTRIX Deceive is a cloud-based service running off the LMNTRIX XDR where deceptions are deployed from, alerts reviewed, notifications configured and devices managed from.
LMNTRIX Deceive incorporates 4 types of deceptions. These are Decoys, Breadcrumbs, Tags, and Personas. Each is designed to address a different insider threat and human adversary threat type and together they form a powerful defense.

What is a Decoy?
Decoys are appliances that can represent one or more servers/services. These include operating systems, file servers, web servers, routers, switches, file shares with files, applications (NAS, FTP, SSH, etc). Decoys are available in appliance, VM or docker formats.
They are pre-configured and shipped to Customer’s to deploy on their networks. We recommend one per segment and one per 100 endpoints where budget permits. Each decoy communicates with the LMNTRIX Cloud for management and alerting.
Each Decoy is configured to match your existing network segment profile. For example, if you have a segment of Windows 7 desktops then we would deploy a Windows 7 Decoy amongst your existing fleet.
The deception capability offered by Decoys is to detect less sophisticated external adversaries and insider threats that are randomly conducting network reconnaissance and trying to gain access to customer’s network and data.
Whenever a Decoy is accessed (such as a network scan, ssh, ftp, file access, share access), an alert is captured by the LMNTRIX XDR and an incident created and investigated by the LMNTRIX CDC. Legitimate company employees should never have any reason to access a Decoy, as such every alert generated by a Decoy is treated as a high severity alert by the LMNTRIX CDC.
What services are supported by Decoys?
Each Decoy ships with 10 or more different types of detection modules. The Customer is responsible for selecting one or more detection modules within the Service Starter pack.
- Host port scan: Detects whether the Decoys were subjected to a port scan from a single originator. This feature can be disabled or enabled in the portal.
- Network port scan: Detects when an attacker scans across your network for a particular port. This requires multiple Decoys on your network
- FTP: Provides an authentication-only FTP daemon. All login attempts are recorded
LMNTRIX Mobile protects users and their devices from many types of threats. These threats are broadly categorized into Network, Device and Malware threats.

- SSH: Provides an authentication-only SSH daemon. All login attempts are recorded. A fake SSH session is presented to attacker.

- Telnet: Provides an authentication-only Telnet daemon. All login attempts are recorded. A fake Telnet session is presented to attacker

- HTTP brute-force: Exposes a web-based login page, and reports when login attempts are made. The HTTP module reports login attempts on a website hosted by the device. To make the login appear legitimate, we let you pick from a range of fake websites that might be found on internal networks. The skin only holds the login page. The device can be deployed as an endpoint running Apache services running on port 80.

- Windows shared files: Provides a fully functional Windows file share complete with actual files like PDFs, word files etc named by you. Alerts whenever someone tries to open the files. Includes the ability to join Active Directories.
Example: The device can be deployed as an endpoint running SAMBA services
When an attacker gains access to the database and attempts to click on a file he will be prompted to put in the password for the file and the alert gets triggered.

- Other Services: These include services like MySQL, Microsoft SQL server, HTTP proxy, SIP, SNMP, NTP, TFTP, VNC and Telnet which can be configured on the Decoys.
What is an AD Decoy?
Typically, on the top 5 list of adversary (APT or nation state) and red team techniques used once a point of breach is achieved is the enumeration of the Active Directory Radius service. The AD Decoy is a service that runs on each client AD server and alerts LMNTRIX when such activity takes place.
How does the AD Decoy work?
The AD Decoy queries the event viewer to find the logon events for normal users and Kerberos users for event IDs and shows the alerts on the LMNTRIX XDR for monitoring and response by the CDC
How is the AD Decoy deployed?
The AD Decoy deployment process is made up of the following 3 steps.
- The client AD Syd Admin needs to first manually create one or more fake users and fake SPN users on their AD server followed by the creation of fake SPN for various services that they wish to use. We recommend at least 5 fake users and SPN users.
- Next, the client needs to use the XDR (CONFIG Menu) and add all the fake user details from (1) above and save the settings to generate the AD Decoy. The fake user details are saved in an encrypted config file and added to the AD Decoy package ready for the client to download and deploy.
- The AD Decoy can now be deployed on AD server(s), and it runs as a windows service.
Please find the install/uninstall steps for this service enable in Windows AD Servers.
Pre-requisites: .Net Framework 4.0 or higher
AD server version: windows server 2012 and later.
Steps for installation :
- Extract the CheckEvents.zip
- Open the command prompt in Administrator mode and redirect to the extracted folder path.
- Execute the below command to install the service on AD Server(s). Installer will copy the required files into C:\Program Files\CheckEvents folder and create the windows service.
InstallSvc.cmd i (Refer below image)

Once the installation is completed. “Check Events” windows service automatically starts and queries the logon events from the Event Viewer (Security Log). In the config file debug value is set to True so this service will generate the log file in the service installed folder. Debug file name format : debug_DDMMYYYY.log
Steps for Uninstallation :
- Open the command prompt in Administrator mode and redirect to the installer folder path.
- Execute below command to uninstall the service on AD Server. Installer will stop the service and remove the files from C:\Program Files\CheckEvents folder and delete the folder as well.
InstallSvc.cmd u (Refer below image)

What information is captured when an AD Decoy alert is triggered?
Any enumeration of Radius or login activity related to the fake users or SPN users generates a deception threat alert on the XDR with the details below.

Are all Decoy alerts communicated to clients?
The LMNTRIX CDC will not alert you on every alert triggered by a Decoy. Instead, we aggregate related events to form a single incident. For example, if an attacker launches a brute-force attempt against your FTP server, you want to receive a single alert about the attack, not one per username tried.
Incidents are defined as duplicated events from the same source against the same target service within a period.
The LMNTRIX XDR records every single event generated by decoys and made available for forensic investigations irrespective of the amount of detail reported in an incident record.
What is a Breadcrumb?
A Breadcrumb refers to a small, subtle piece of false information or data that is intentionally placed within a system to lure or mislead attackers. These Breadcrumbs are part of our broader deception strategy designed to divert attackers towards a Decoy system (a honeypot) or to provide misleading intelligence.
For example, Breadcrumbs can be fake credentials, misleading file names, or false configurations that lead attackers to believe they are accessing valuable resources. When an attacker interacts with a Breadcrumb, it triggers monitoring and alerts defenders, giving them insights into the attacker’s tactics, techniques, and procedures (TTPs).
The goal is to increase the complexity of the attacker’s task while gathering intelligence without risking actual assets. This technique is often used to complement more traditional security measures, adding a layer of misdirection to protect sensitive information and infrastructure.
How are Breadcrumbs deployed?
Breadcrumbs are deployed across all Customer endpoints (servers and desktops). Each endpoint is populated with multiple interesting breadcrumbs to increase the chances of fooling attackers. Once an attacker takes a bait (breadcrumb) and tries to communicate with a breadcrumb, they are directed to the LMNTRIX XDR where they are monitored by our intrusion analysts as they communicate with our Decoy platform as we record all their actions.
Breadcrumbs rely on the integration of LMNTRIX XDR with Customer’s Active Directory for breadcrumb deployment. There are no agents or software deployed on endpoint, only interesting breadcrumbs, such as fake Admin accounts, saved Usernames/Password, and web browsing history. The breadcrumb deployment process takes less than 300 milliseconds and for windows machines which are a part of Active directory, we use legitimate API calls for breadcrumb deployment and for Linux machines which are not integrated with Active directory, we use SSH to deploy deceptions on those machines.
The process is repeated once a month to ensure breadcrumb persistence.
How do Breadcrumbs work?
During an advanced attack, an attacker gains access to an endpoint without knowing where that endpoint sits in the network structure. The attacker employs a range of tools to iteratively discover the network hierarchy from that endpoint. The collected information is analyzed to plan access attempts to lateral network locations. The goal of the attack is to locate sensitive information such as confidential company data.
The agentless solution offered by LMNTRIX presents attackers with a deceptive network view, exploiting the attacker’s belief that all received data is valid. Limitless enticing deceptions detect and divert an attack, immediately gathering information about the attacker’s ongoing activity when access is attempted, without the attacker’s awareness. Superior technology, real-time source-based forensics, and intimate knowledge of cyber-attacker psychology ensures visibility of attacks and returns information-control to the network administrators.
The following are the 3 phases on how breadcrumbs work:
- Deceive: We deploy Breadcrumbs on Client endpoints using the LMNTRIX XDR. Connectivity between the client network and LMNTRIX XDR is secured using IPSec VPN.
- Detect: Attackers take the bait (Breadcrumbs) and expose themselves.
When an attacker lands on a specific endpoint, he runs his reconnaissance tools to get a better understanding of the Clients network and gain access to such things as credentials, servers, systems and applications. However, what he ends up gaining access to are actually our Breadcrumbs including cached information that we have setup for him to interact with. During this interaction, the attacker is redirected off the Client network and onto the Decoy. The Deception is designed in such a way that the attacker thinks he’s interacting with a real server, system or application as the deception is setup to mimic an actual environment. - Defeat: Alert and investigate attack profile
LMNTRIX XDR then interacts with the attacker and the compromised endpoint machine to take snap shots from it. Complete forensic information is recorded and made available to the CDC for further analysis.

What is the impact of deploying Breadcrumbs on our network or on our machines?
Once our Breadcrumbs are deployed, they have minimal impact on your network, applications and users. The following provides the impact of breadcrumbs on your end-users, IT and attackers:
- Attackers: Our Breadcrumbs consist of data that appears to be a legitimate for the attacker, but is isolated and monitored, and that seems to contain information or a resource of value to attackers.
- End users: Our Breadcrumbs are not visible to the end users after its deployed on the endpoints and if in case the end user sees the Breadcrumb and uses it, then a false positive is triggered at out CDC. Our claim is that we have near 0 false positives.
- IT: Also, IT would not have access to view the breadcrumbs because this is not deployed on the network

What categories of Breadcrumbs do you offer?
Following is a list of Breadcrumbs that LMNTRIX takes advantage of. There are 11 categories in total and each one generates an alert to our CDC when tripped.
- Browsers: The browser’s Breadcrumbs produces deceptive information relating to the domain webhosts. Browser History deceptions masquerade as web servers that valid users have accessed in the past and this information in stored in the Google Chrome Database on the endpoint. The breadcrumbs added here tempt an attacker to access a customized webpage for Synology NAS Login. Alerts are triggered and sent to the CDC when an attempt to access a deceptive web server is made

This is a highly interactive service running on the breadcrumb server and this produces 2 alerts.
The first alert is sent when someone accesses the webpage
- Databases (Mysql and Mssql): The Database Breadcrumbs produces deceptive information relating to domain databases. Alerts are triggered when attempts to access deceptive domain databases is made.
The demo can be shown by trying to interact with the ports 3306(Mysql) and 1433(Mssql) using python.

- FTP: The FTP Breadcrumb produces deceptive information relating to domain file servers. Incident alerts are triggered by attempts to access deceptive file servers
The session is highly interactive and from the screenshot above, it clearly shows that all the commands that’s a part of the FTP protocol family.
- RDP: The RDP Breadcrumb plants deceptions that are related to local RDP files. A remote desktop protocol (RDP) file is used to access one endpoint from another. Incident alerts are triggered by attempts to use planted RDP files to access deceptive servers

- Shares: The Shares Breadcrumb produces deceptive information relating to shared folders within the domain. Incident alerts are triggered by attempts to access a deceptive shared folder.
- SSH: The SSH Breadcrumb produces deceptive information relating to domain SSH servers. Incident alerts are triggered by attempts to access a deceptive SSH server.
- Saved Sites (HTTP) in Windows Vault – Saved Site deceptions masquerade as password-protected web servers and the credentials required for authentication.

- Telnet: The SSH Breadcrumb produces deceptive information relating to domain Telnet servers. Incident alerts are triggered by attempts to access a deceptive Telnet server.

- VNC: Virtual Network Computing (VNC) is a graphical desktop sharing system that uses the Remote Frame Buffer protocol (RFB) to remotely control another computer. It transmits the keyboard and mouse events from one computer to another, relaying the graphical screen updates back in the other direction, over a network
The VNC Breadcrumb produces deceptive information relating to servers which can be accessed to the VNC service. Incident alerts are triggered by attempts to access the breadcrumb server.

What are best practices for deployment of Breadcrumbs?
On Windows desktops, we recommend the use of the following breadcrumbs:
- Saved Sites in Windows Vault: We recommend this because, this breadcrumb saves fake domain credentials in the vault of a windows machine and produces deceptive information about the Operating System.
- RDP & VNC: This is a common service/tools used by network administrators for support and as such it makes for a great trap for attackers
- Shares: Recommended on a windows machine which as it creates deceptive recently accessed file shares in the recent directory.
On Linux Servers, we recommend the use of the following breadcrumbs:
- SSH and Telnet: Since these services are active on most Linux Servers for administrative purposes, we recommend deploying these Breadcrumbs on Linux Servers.
- FTP: FTP service is common service in a Linux environment.
- Shares: If your environment uses Samba services, its highly recommended to use this service to create fake user shares.
Recommended Breadcrumbs common for both platforms
- Browser: This is recommended across both Linux and windows platforms since passwords are regularly saved by users in browsers and presenting an extra set of fake credentials to an attacker increases the probability of an attacker being lured to use the fake credentials.
- Databases: Recommended on both platforms as they can be accessed from both environments.
How do I configure users with Breadcrumbs?
To access a domain, LMNTRIX requires the details of two different users in your user directory
DIRECTORY USER: LMNTRIX uses the directory user to navigate your user directory
- To create the directory user account
- In the user directory, assign search-only permissions to a user
SERVICE USER: LMNTRIX can use the service user to deploy deceptions on network hosts
- In the user directory, create a new user.
- In the domain to be managed, make the user a local administrator on all endpoints
- Set the user attribute Account is sensitive and cannot be delegated to TRUE.
- Configure the service user to read event logs from Domain Controllers
Note: In each supported AD domain, the Local Admin AD group must be created in the domain Builtin container.
Set the user attribute Account is sensitive and cannot be delegated to TRUE
What are Tags?
Tags are unique tags that are embedded in a variety of places such as in documents, emails, Linkedin, bitcoin, images, databases, etc. that nobody should be accessing. They have the same profile and naming conventions as that used by the customer. If anyone accesses them then an alert is sent to the LMNTRIX XDR and for our intrusion analysts to investigate and escalate to the Customer if necessary. Tags can include files or emails within SaaS platforms such as Office365, Dropbox, Google Drive, HipChat, Slack, etc to monitor the vendor engineers accessing Customer files.
The use of Tags as a form of Deception deployed on real assets (workstations and servers) is aimed at detecting attackers both internal and external to the organization that have gained actual access to the Customer assets. Furthermore, Tags is one of the few methods that allows LMNTRIX to get close to confirming attack attribution. Unlike Breadcrumbs that rely on Decoys for alerting, Tags generate alerts independent of Decoys.
What types of Tags are available?
Tags are a “quick, painless way to help defenders discover they’ve been breached (by having attackers announce themselves).” To accomplish this, we create tags such as:
- A URL an adversary might visit
- A domain or hostname an adversary might resolve
- A Word or PDF document an adversary might open
When the intruder accesses or makes use of the tag, LMNTRIX will notify you via email and share a few details about the event in the form of an incident.
Web Tags
These are unique URL tags that are triggered whenever someone requests for a URL.
They are deployed in the form of an email subject line in your emails, embedded as a tag in some of your documents and as a tag in the form of a password.html files.
Best Practices:
- You could send yourself an email with the Webbug tag.
- In an email with a juicy subject line. So, if your emails are stolen, then an attacker reading them should be attracted to the mail and visit the link.
- Embedded in documents.
- Inserted into your company’s webpages that are only found through brute-force
- This URL is just an example. Apart from the hostname and the actual tag (the random string), you can change all other parts of the URL
Here is an example of a Webbug tag that we deploy for our Customer’s and the alert that we receive at the Cyber Defense center.
http://lmntrixtags.us/articles/tags/static/57wv83vsr0gskmwssixedeth7/index.html

DNS Tags
DNS Tags are unique hostnames that gets triggered whenever an attacker performs a lookup on your domain.
Best Practices:
- Create this in a .bash_history, or .ssh/config, or ~/servers.txt
- Include in a PTR entry for dark IP space of your internal network. Quick way to determine if someone is walking your internal DNS without configuring DNS logging and monitoring.
- We create an extremely simple bridge between a detection and notification action. There are many possibilities, one of them is to tail a logfile and which in turn triggers the tags when someone logs in and our CDC will receive an alert.
- Use as the domain part of an email address.
Here is an example of a DNS tag that we deploy for our Customer’s and the alert that we receive at the Cyber Defense center.
j64qemw57le0pf7s688cp547q.lmntrixtags.us

We provide SMTP tags to monitor any attacks on your databases with a unique email address
Best Practices:
- Drop this unique email address on your databases with user’s information and if an attacker tries to send an email to the email address, our CDC will receive an alert
- Here is an example of a SMTP tag that we deploy for our Customer’s and the alert that we receive at the Cyber Defense center.
- In a database with a USERS table, drop a fake record in there with this email address. If it gets triggered, you know someone has accessed your data.

We deploy unique QR codes and this is used as a tag on your containers which are left in secure locations.

As soon as the QR code is scanned, the attacker is prompted with a tag link and once he clicks on it, our CDC receives an alert and we would be able to provide our Customer with the location of these containers.
Best Practices:
- Place these QR codes on devices, computers, printers etc which are in a secure location. We will notify you through an email incase these are scanned.
- Use this QR Code to tag a physical location or object
- On your desk
Here is an alert that our analysts at the CDC receive.

MS Word and Adobe Acrobat Tags
We deploy a tag in the form of a word file or a pdf file in any of the Customer’s servers. As soon as the attacker opens this file for editing, an alert is triggered and our analysts at the CDC start investigating it before the attacker even realizes that he is being monitored.
Best Practices:
- You can add these files into the Windows directory Tags as an additional layer of deception.
- You can rename the document without affecting its operation
- These files can be saved on network shares and does not require any additional software for configuration.
- Attach to an email with a tempting Subject line
- Simply placing a tag in the document meta-data, gives us a reliable ping when the document is opened
Leave these files on a web server in an inaccessible directory, to detect webserver breaches.
Here is an example of MS word tag that we deploy for our Customer’s.
Here is an alert that our analysts at the CDC receive

Here is an example of Adobe Acrobat tag that we deploy for our Customer’s
Here is an alert that our analysts at the CDC receive.

SQL Server Tags on SELECT, UPDATE, INSERT, DELETE
Webservers often draw active content from a datastore that is usually a SQL database, and these are quite hard to protect and harden. Hence why SQL databases are likely to be exploited by SQL injection attacks.
With our SQL tags, alerts are triggered to our CDC when any one of these commands are executed on the SQL database. This adds an additional layer of security to the Customer’s databases. The next step is to copy the SQL snippet and run in your SQL Server database.
Here is an alert that our analysts at the CDC receive.

Best Practices:
- It isn’t natively possible to have MSSQL server trigger an action on a SELECT statement, but what you can do is create a custom VIEW which triggers a DNS query when a SELECT is run against the VIEW.
- Deploy a SELECT or INSERT or UPDATE or DELETE tags with a tempting VIEW name such as USER_DETAILS.
Windows Directory Browsing Tags
Our CDC gets notified whenever an attacker opens or browses a Windows directory in Explorer. It works with network shares and doesn’t require any additional software.
Additional interesting file tags are added which you think would be a risk if it falls into the wrong hands.

Best Practices:
- Windows provides an even cooler way to get notified, in the guise of the venerable old desktop.ini configuration file. Dropping a desktop.ini file in a folder allows Explorer to set a custom icon for a file.
- Since this icon can reside on a remote server (via a UNC path), using DNS we can effectively make use of a tag as our icon file.
- You can add additional files into the directory. So, you can combine other tags like MS word tag and Adobe Acrobat tag files in the directory.
Our CDC gets notified whenever an attacker has cloned your webpage.
Place this JavaScript on the page you wish to protect. When an attacker clones your site, they’ll include the JavaScript. When the JavaScript is run, it checks whether the domain is expected. If not, it fires the tag and the CDC will receive an alert.
Here is an example of a Cloned Website tag that we deploy for our Customer’s.
if (document.domain != “example.com”)
{var l = location.href;
var r = document.referrer;
var m = new Image();
m.src = “http://lmntrixtags.us/”+
“8oedbi0nvs408y049i47f3ubo.jpg?l=”+
encodeURI(l) + “&r=” + encodeURI(r);
}
Here is an alert that our analysts at the CDC receive

Best Practices
- Run the script through an obfuscator to make it harder to pick up.
- Deploy on the login pages of your sensitive sites, such as OWA or tender systems.
- This Tag does not support content delivery networks (CDN). Clients running websites behind a CDN should not use this Tag.
Our CDC gets notified whenever an attacker clones the SVN repo. Don’t forget to run “svn commit “after you’ve added the tag.
Here is an example of a SVN tag that we deploy for our Customer’s.
svn propset svn:externals “extras http://wv3c56dkki3yo27e8zhbc7n88.lmntrixtags.us” .
Here is an alert that our analysts at the CDC receive

Our CDC gets notified whenever an attacker uses this credential pair to access AWS programmatically (through the API). The key is hyper unique. i.e. There is 0 chance of somebody having guessed these credentials. If this tag fires, it is a clear indication that this set of keys has “leaked”.
Here is an example of an AWS tag that we deploy for our Customer’s.
[Default]Access key Id: AKIAIQ7YPSXLN3BH2CKQ
Secret Access Key: 0QHPJnXl1dwqUsjrh2voTOLMMLH2V8ft98iFiVoM
Here is an alert that our analysts at the CDC receive
Best Practices
- These credentials are often stored in a file called ~/.aws/credentials on linux/OSX systems. Generate a fake credential pair for your senior developers and sysadmins and keep it on their machines. If an attacker tries to access AWS with the pair you generated for Bob, chances are that Bob’s been compromised.
- Place the credentials in private code repositories. If the tag is triggered, it means that an attacker is accessing that repo without permission
The tag is like the Web tag, however, when the link is loaded the view will be immediately redirected to the specified redirect URL.
Here is an example of an Fast Redirect tag that we deploy for our Customer’s.
http://lmntrixtags.us/articles/feedback/xqmtoyuxa0vs0to66p5fofu6h/post.jsp

Best Practices
- Replace links with these to capture user information before user is redirected to where they want to go.
- Embedded in documents.
- Inserted into LMNTRIX webpages that are only found through brute-force.
- This URL is just an example. Apart from the hostname and the actual tag (the random string), you can change all other parts of the URL.
The tag is like the Fast Redirect tag, however, when the link is loaded the user’s browser / browser plugin information is captured.
Here is an example of an Slow Redirect tag that we deploy for our Customer’s.
http://lmntrixtags.us/images/uuadczrsng7apwu468df28jf1/submit.aspx

Best Practices
- Replace links with these to capture user information before user is redirected to where they want to go.
- Embedded in documents.
- Inserted into LMNTRIX webpages that are only found through brute-force.
- This URL is just an example. Apart from the hostname and the actual tag (the random string), you can change all other parts of the URL.
What geolocation information about the attacker do Tags provide?
We provide the clients with the geographical location associated with the hosting device. This varies depending on the type of tags that the attacker use.
- If the attacker uses a tag that works on DNS protocol, we provide our clients with the DNS information of the attacker.
- If the attacker uses a tag that works on HTTP protocol, we provide our clients with the Source IP information of the attacker.
- If the attacker uses a tag that works with SMTP protocol, we provide our clients with the mail servers location and other details which would include the Email address of the attacker, Email attachments etc.
- LMNTRIX Tags provides us with the Internet service provider information, Hostname, Useragent used, IP address, date and time of the attack etc, so that we can track the attacker down quickly and attribute the attack, not possible with any other solution. Furthermore, Tags notify us if the Known Exit Node was from a Tor network.

What are Personas?
Personas are unique accounts and profiles created across the Customer systems, applications and social media channels. Whenever contact is made with one of them via email, we know that an adversary has stolen or is targeting the respective data.
LMNTRIX simply guides the Customer through the process of creating Personas. It’s the Customer that creates all of the Personas across their systems as they’re the only one who has access to them.
Following provides examples of identities clients generally deploy:
- 5 Linkedin personas/fake profiles with email addresses. Social media identities are a great way to identify Customer employees are being poached or a target of a phishing/spam campaign.
- 5 different Email accounts within the Customer email/exchange directory addresses.
- 5 different Users/Email addresses created within the Customer’s “Customer Database” (E.G. salesforce.com/CRM). Any emails to these shows that the Customer’s customer DB has been stolen.
- 5 different Users/Email addresses created within the Customer HR application. Any emails to these shows that the Customer employee details have been leaked/stolen.
- 5 identity decoy phone numbers in the Customer phone directory.
- 5 Active Directory identities that can be monitored.
- 5 Customer specific application identities that can be monitored such as Marketing and Accounting systems
You must take great amount of effort to ensure that all social media decoys are realistic. For example, the following should be your approach for LinkedIn:
- Create 5 new employee profiles on LinkedIn. They must all look legitimate with proper work/company history. Their email addresses match that of other employees, such as firstname@customerdomain.com. Customer then creates aliases for these forwarding them to our CDC.
- At minimum, all employee profiles should have 10 yrs work history. You can use a new name but copy designation and employee history from other employees or competitors.
- Ensure that their location is consistent with where you operate.
- Finally, invest sometime on each profile making connections with people in your industry.
What are prerequisites & customer responsibilities for setting up LMNTRIX Deceive?
The LMNTRIX Deceive Starter Pack is required to be completed by the customer prior to service establishment.
- The Customer is responsible for the accurate completion and selection of the Starter Pack that includes each decoy profile, detection modules, decoy name and other details required for each detection module.
Note: Please choose a Decoy name such that it suits each Decoy Personality.
- The Customer is responsible for the correct deployment and network interconnectivity of each Decoy which includes updating the Starter Pack with information related to the IP address, subnet mask, VLAN, default gateway IP address etc of the decoy.
- The Customer is responsible for the accurate matching of Decoy detection modules to each network segment asset profile.
- The Customer is responsible for the correct DNS entries in their internal DNS server for each Decoy detection module to accurately resolve IPs to meaningful names, E.G. research.companyname.com
- In case of damage to the Decoy, please notify us at CDC@lmntrix.com.
- The Customer has to define the number of subnet ranges in which the Tags are deployed.
- The Customer is responsible for making sure the Tags provided are placed exactly in the same subnet as specified by them in the pre-requisites.
- A Unique Name that the customer provides us with, as per the Starter Pack must be related to the subnet in which the Tag is placed so we can identify the source of the trigger and alert you of the same.
- One comment/subnet must be specified so that we can remind you where you would have used the Tags.
- The IP ranges of the subnets must be updated in the Starter Pack.
- The OS used by the Endpoints must be specified.
- The type of Tags required must be specified by the Customer.
- If the Tags are placed in incorrect subnets, we would not be able to track the attack effectively and it would likely cause confusion.
- The Customer must create their own Tag DNS entries such that their Tags domain points to the LMNTRIX domain. This is to ensure that the attacker is never exposed to the LMNTRIX brand or domain and cause any suspicion for the attacker not to click on a tag.
Example: The customer can create a web bug http://xyzcompany.com/images/4y26grc4sx168ts7fh9zh84k0/contact.php and point it to http://lmntrixtags.us/images/4y26grc4sx168ts7fh9zh84k0/contact.php in their DNS
- Once we receive the updated Starter Pack form from the Customer, Tags are sent to the Customer through an email, so that they can be deployed in their environment.
- In case the Customer loses their Tags, they may email the CDC@lmntrix.com with their Unique name, Subnet information, and Company name, so that we can resent the Tags to them.
- If the Customer requires new Tags, they can email the CDC@lmntrix.com with an updated Starter Pack so that we can prepare and send them the new tags.
- The Customer is responsible for the accurate completion and selection of their breadcrumb profiles for every Organizational Unit (OU).
- On all Windows hosts, allow the LMNTRIX XDR to execute commands by Enabling File and Printer Sharing
- Enable LMNTRIX to test host connections by ensuring ICMP ping requests are enabled on the network.
- Customer should update the Starter Pack after creating the Directory user and Service user in their domain as mentioned in the Configuring Users section of this document.
- Enable default deployment by ensuring that the LMNTRIX XDR is a member of the network domain.
- The operating system of the workstations in each segment must be identified and updated on the Starter Pack by the Customer.
- The Customer is responsible for the selection of Breadcrumbs suitable for each segment. The Customer can refer to Best Practices for Deployment of Breadcrumbs-Recommended
- The Customer is responsible for the Breadcrumb-to-Decoy design and stories. E.G. All workstations will have a Shares Breadcrumb pointing to the research.companydomain.com, etc.
Breadcrumbs Remote operation method
By default, Breadcrumbs are deployed on hosts from the LMNTRIX XDR using the Sysinternals Deployment Tool (psexec). If your environment does not support this default configuration, you can select to run the Breadcrumbs setup tool on each host manually or deploy Breadcrumbs using a third-party remote-management tool that requires some configuration on the tool’s server (i.e. SCCM/Tanium/PatchLink/BigFix).
Note: You can select only one deployment method.
Configuring Integrated Operational Methods
The LMNTRIX remote-operation method handles Windows policy deployment and forensics collection.
The below tool can be configured to run LMNTRIX operations via the LMNTRIX’s Cloud.
- Sysinternals Deployment Tool
The Windows Sysinternals Suite is a Microsoft freeware tool that enables host management. For details, see the Sysinternals Utilities Index.
By default, the Sysinternals deployment tool runs LMNTRIX operations
External Operational Method
We can configure policy-deployment to be managed by a third-party tool directly. Windows hosts can be managed via tools such as Microsoft SCCM while Linux hosts can be handled by any external tool, such as Ansible.
- Customer is responsible for the creation of unique email accounts in their mail server and have these forwarded to the LMNTRIX CDC.
- Customer is responsible for the creation of unique personas/profiles in their applications including CRM/Salesforce, HR, Accounting, Marketing, and Active Directory environments and update that in the pre-requisites form.
- Customer’s is responsible for the creation of the LinkedIn personas and respective email and redirection to the LMNTRIX CDC.
- Customer’s need to create aliases for the above mentioned unique email addresses so that when an email is sent, it will be forwarded to alerts@lmntrix.com.
LMNTRIX Intelligence
What is LMNTRIX Intelligence?
LMNTRIX Intelligence is a subscription feature of LMNTRIX XDR.
SOC operators, CSIRT teams, and security analysts and researchers are in a race against time. The good news is that there’s an overwhelming amount of threat data available today. The challenge is rapidly converting this unstructured, disparate, and duplicative data into the contextual information to drive your security monitoring process and infrastructure.
LMNTRIX Intelligence curates and operationalize threat intelligence and accelerates incident response. It provides the essential analysis and correlation that you need to translate raw, unstructured and duplicative data into true intelligence. Reduce the noise of false positives from outdated irrelevant data in minutes. What’s left is true insight in the form of pre-built rules, reports, and dashboards that we use in LMNTRIX XDR or you can immediately apply and manage within your SIEM console.
LMNTRIX Intelligence harnesses collated intelligence into a single XDR platform to optimize collaboration and information sharing. Proprietary technology delivers earlier detection and identification of threats at every point along the attack lifecycle, making mitigating threats possible before material damage occurs.
- Threat actor communications interception identifies TTPs before they’re used in anger and proof of concept attacks before full deployment.
- Correlation of over 850 million threat indicators against real-time network data deployed deep within customer networks.
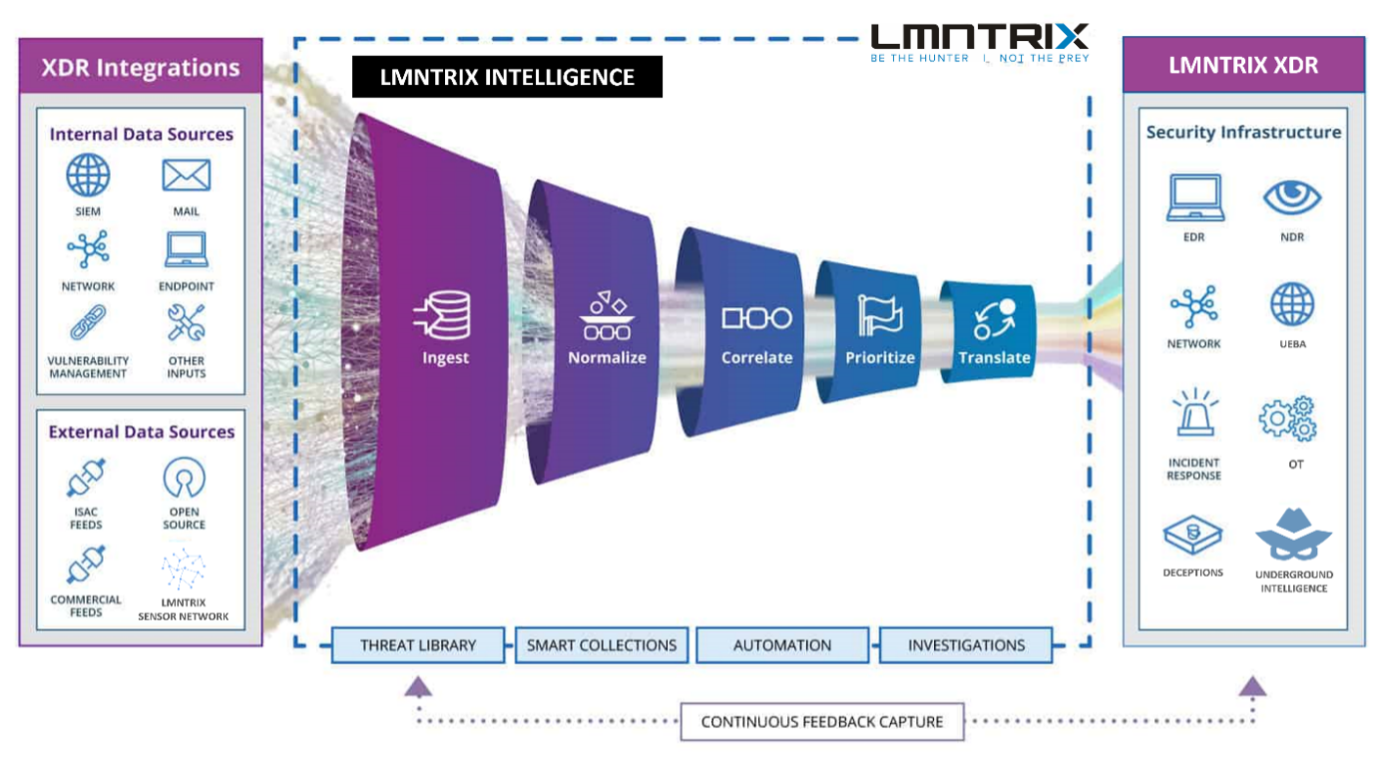
Does the LMNTRIX XDR include a Threat Intelligence Platform (TIP)?
LMNTRIX Intelligence is powered by a native TIP built within our XDR– which is a crowed-sourced threat intelligence exchange combined with our own sensor network together with over 20 commercial feeds.
We are all facing attacks, all the time and as a result we have a lot of data – why not share it?
That is the idea behind our TIP – Threat Intelligence PlLatform, that delivers a powerful community based immunity system.
Attackers are known to share methods and tactics and in order to advance the state of threat intelligence, organizations must collaborate and correlate more data, more quickly.
Today LMNTRIX TIP aggregates over 300 threat intelligence sources with the aim of aggregating more in the future to help consume, share, and act on threat intelligence.
Our TIP is:
Open
A robust platform with access to a wealth of threat intelligence data
Actionable
An integrated solution to help quickly stop threats
Social
A collaborative platform for sharing threat intelligence
How does LMNTRIX Intelligence work?
The proprietary technology behind LMNTRIX Intelligence allows us to deliver earlier detection and identification of adversaries in your organization’s network. This is achieved by making it possible to correlate tens of millions of threat indicators against real-time network logs as well as with other Active Defense service elements including:
- LMNTRIX NDR: The TIP threat feed is integrated with our NDR sensor deployed on Client’s premises. Any IOC hits on the NDR sensor are automatically validated and incidents created on the LMNTRIX XDR.
- LMNTRIX EDR: The TIP threat feed is integrated with the EDR agents deployed across Client’s endpoints. Any indicator hits on the agents are automatically validated and incident created on the LMNTRIX XDR.
- LMNTRIX Packets: The TIP threat feed is integrated with the Packets data captured on our XDR. Any indicator hits on the Packets data is automatically validated and incidents created on the LMNTRIX XDR.
- LMNTRIX SIEM: The TIP threat feed is integrated with the SIEM feature on our XDR and correlated against log data captured from our client networks. Any indicator hits on the SIEM is automatically validated and incidents created on the LMNTRIX XDR.
Our approach enables detection at every point along the attack lifecycle, making it possible to mitigate threats before material damage to your organization has occurred.
This process used by the LMNTRIX XDR includes:
- Curation & De-duplication – LMNTRIX Intelligence aggregates and de-duplicates threat data from 300+ public, private, and proprietary sources including our own HoneyNet deployed across all AWS regions.
- Machine learning – Algorithms scale to accommodate thousands of IOCs per minute across your environment
- Collaboration & Community – Securely connects security researchers within and across teams in trusted circles to cooperate on effective cyber defense strategies
- Correlate and integrate – Turns data into actionable information: XDR rules, reports, and dashboards

What type of threat indicators are captured by LMNTRIX Intelligence?
In practice, on average the LMNTRIX XDR is able to detect 20%-25% more incidents each month as a result of the threat intelligence feed than without it. It achieves this by automating detection for the following threat scenarios:
- Crimeware
- Dynamic DNS
- Phishing Attacks & URLs
- Anonymous VPN
- Hacking Tools
- Malware C&C
- APT IPs & Domains / APT IP User Agent
- Brute Force, Spammer & Bot IPs
- TOR Detection
What does a typical outcome look like when using LMNTRIX Intelligence in a SOC?
The following diagram depicts the value LMNTRIX Intelligence delivers from the time events are collected, security attacks identified and finally the attacks that are confirmed to be incidents.

What are the deployment options for LMNTRIX Intelligence?
The LMNTRIX Intelligence (TIP) platform is a native feature of LMNTRIX XDR and hosted on AWS, where it curates and de-duplicates data. The primary method of consumption of the service is by other XDR service elements such as the NDR, EDR, Packets and SIEM. Optionally, Clients can also consume the threat feed using standard protocols into their existing security infrastructure including SIEM, EDR or NextGen Firewalls.
For whole of governments or industry sectors who wish to deploy the platform internally, LMNTRIX makes the platform available as a private TIP.
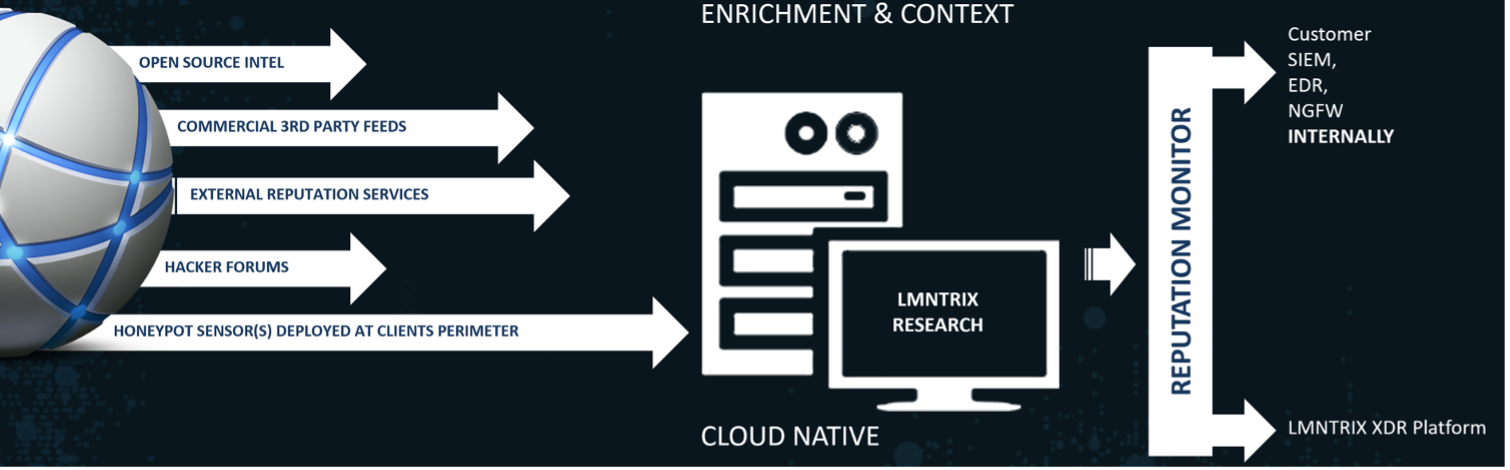
What are the service deliverables from LMNTRIX Intelligence?
LMNTRIX Intelligence provides the LMNTRIX XDR and our threat analysts with the edge they need to analyze, discover, share and integrate threat data into security team processes for business risk reduction. The service deliverables include:
- Analyzes and pinpoint IOCs allowing you to quickly search for a specific indicator type over any time range, and drill-down into details.
- Eliminates unnecessary, duplicative and irrelevant indicators – before they enter your infrastructure.
- Integrates with the LMNTRIX XDR and your SIEM and other parts of your security architecture for automated threat detection and response.
- Real-time Risk Analysis – Ranks each individual IOC based on severity, relevance, and contextual variables.
- Easy-to-use interface – to view threat information received through STIX/TAXII feeds.
LMNTRIX Recon
What is LMNTRIX Recon?
LMNTRIX Recon is a subscription feature of LMNTRIX XDR that delivers powerful early warnings of hacking and fraud attacks via a sophisticated cyber intelligence platform. Scanning a wide range of sources (e.g. deep and dark web, cyber-crime forums, IRC channels, social media, app stores, paste sites), it provides near-real-time alerts about cyber-threats.
By converting security intelligence into actionable data, the LMNTRIX Recon enables our Customer’s to detect unknown threats and minimize their dangerous exposure.
LMNTRIX Recon also provides an option for an upfront 2-day Quick Scan or a thorough 15-day Exposure Analysis to help baseline the Client’s threat exposure to the deep and dark web prior to initiating the monitoring service.
We identify your data as it accesses criminal command-and-control servers from multiple geographies that national IP addresses cannot access
What outcome does a subscription to LMNTRIX Recon provide?
- Deep and Dark Web Threat Alerting: Proactive and automated monitoring for your organizations stolen or compromised data and alerting you when data is
- Compromised Data Tracking, Incident Response & Reporting: Track and triage incidents and better manage risk.
- Holistic Threat Intelligence Program Development.
- Compromised Data Trending & Peer/Industry Benchmarking: Gain insight into your organization’s current threat posture while benchmarking it against your peers and the industries that you serve.
- HR and Policy Enforcement – Cyber Education & Awareness.
- Targeted Individual and Repeat Offender Monitoring.
What are the subscription levels to LMNTRIX Recon?
LMNTRIX Recon offers two subscription levels:
1- Basic: Provides monitoring for credentials exposure only. I.E. usernames and passwords
2- Premium: Provides monitoring for all data types in multiple languages including HUMINT. This includes the following exposure types:
i. Credentials
ii. Personas
iii. Breaches
iv. Physical
v. Source Code
vi. Hacktivism
vii. Botnets
viii. Vulnerabilities
b. Legal & Compliance
i. Mobile Apps
ii. Employees
iii. Data Loss
iv. Publicly Identifiable Information (PII)
c. Reputation & Revenue Loss
i. Product Information
ii. Contracts
iii. Brand Abuse
iv. Brand
v. Executive Profiles
The LMNTRIX Recon Premium subscription level offers six (6) service levels to select from:
| Service Level | Total Number of Keywords | Total Number of Queries per Month |
| Basic | 5 | Up to 10 |
| Basic+ | 20 | Up to 40 |
| Bronze | 50 | Up to 100 |
| Silver | 150 | Up to 300 |
| Gold | 250 | Up to 500 |
| Platinum | Unlimited | Unlimited |
What are the use cases or actionable intelligence delivered by LMNTRIX Recon?
The following are the uses cases for LMNTRIX Recon:
Internal Operations & Management
- Holistic Threat Intelligence Program Development
- Proactive & Automated Security Management
- High Value Target (HVT) Monitoring
- Targeted Individual and Repeat Offender Monitoring
- Reduce Incident Response Times
- Policy Enforcement
- Cyber Education & Awareness
- Identify trends and potential exposure points within your supply chain
- Share threat intelligence and support corporate supply chain management and security policies
- Understand how your organization’s threat posture compares to your industry peers and competitors
- Demonstrate a comprehensive approach to loss prevention and educate through the deployment of external security monitoring services
How does LMNTRIX Recon work?
We monitor the following 24/7, 365 days a year:
- Hidden Criminal Chat Rooms (280 forums)
- Private Websites
- Peer-to-Peer Networks
- IRC (Internet Relay Chat) Channels
- Social Media Platforms
- Black Market Sites
- 640,000+ botnets
On average, we identify and report on more than 1 million compromised IP addresses and more than 80,000 compromised emails every day.
- Detect – LMNTRIX Recon constantly scans a wide range of sources for threat intelligence across the deep, and dark web. It also uses existing search engines to gather additional valuable information (“piggybacking”). All this data is gathered by a proprietary browsing solution that overcomes obstacles in the dark web i.e. anti-bot technologies and stores it on the LMNTRIX XDR.
- Analyze – LMNTRIX Recon analyzes, categorizes, and prioritizes cyber threats in real time using proprietary, patent-pending data mining algorithms and unique machine learning capabilities to focus intelligence on what is important to you.
- Respond – After ensuring relevancy and existence of a cyber threat, the information goes through a false positive assessment and classification process by our intrusion analysts before an incident ticket is created and escalated to the Client.
Note: LMNTRIX Recon does not provide any remediation services, as we only provide monitoring for the deep & dark web (not clear web).
What type of threats or incidents does LMNTRIX Recon produce?
LMNTRIX Recon delivers the following types of incidents:
- Attack indications – Hackers use websites, forums, and social media to plan and coordinate attacks. Our system detects and alerts you of these plans that are found through the cyber-space, e.g. the company name in target lists, or a bid for attacking the company in hackers’ forums.
- Data Leakage – Secret data often leaks from the organization. Leaks can happen from hackers who penetrated the organization, or even frustrated or careless employees. Even the most advanced DLP can’t provide 100% certainty about data safety. Our system finds your leaked secret data and lets you know, giving you a chance to protect yourself from it being used in future attacks, e.g. credentials that might be used for logging in to your employees’ accounts, secret documents about the company’s projects, information about the company’s internal network.
- Brand Security – Social media has become an important arena for branding, marketing and communicating with Customer’s. Many hackers create and manage fake accounts and applications to seduce innocent Customer’s and steal their personal data and even hurt your company’s reputation. Our system detects and alerts you about imitating fake pages, profiles, applications, and even posts aimed at hurting your reputation.
- Phishing – One of the most common social-engineering attacks is phishing, done by spear-phishing e-mails or phishing sites. In order to execute this attack, the hacker must first open a fake domain to host the phishing site or send the spear phishing e-mail. Our system offers early detection for potential phishing domains soon after registration, and allows you the time to prepare and prevent the attack.
- Exploitable Data – Our unique methodology allows us to detect and report about information indexed by search engines that is exploitable by hackers. High-level hackers find this information and use it to piece together sophisticated cyber-attacks. Examples include published web vulnerabilities, information about your internal confidential network, databases, and software used –including exact version numbers.
- VIP Protection – Your company’s VIPs are some of your most important assets. Holding the most valuable experience and sensitive data about the company, their protection is high priority. Our system detects and alerts you about potential attacks on your VIPs, secret data that leaked from a VIP (e.g. secret documents, passwords), and fake VIP profiles in social media and other websites.
What are client responsibilities for onboarding LMNTRIX Recon?
Customer is responsible for completing the data collection sheet with accurate information about their business and respected keywords that are to be used during the deep & dark web monitoring service.
These include: products, assets, supply chain, company name(s), domain name(s), IP ranges, executive profiles, publicly identifiable information, source code, etc that they would like monitored.
LMNTRIX Packets
What is LMNTRIX Packets?
LMNTRIX Packets is a subscription feature of LMNTRIX XDR. It provides time machine or DVR like capability for your network by recording everything using our XDR platform. LMNTRIX Packets combines unlimited visibility and the detection of slow and complex threats that develop over time, giving the LMNTRIX team the strategic advantage to hunt and investigate threats through every stage of an attack. By harnessing the power of the cloud, LMNTRIX has the unique ability to create an unlimited retention window with full-fidelity forensics, automated retrospection and advanced visualization—all with the ease and cost-savings of an on-demand deployment model.
How does LMNTRIX Packets work?
The four (4) distinct capabilities by LMNTRIX Packets are:
1) Post Breach Forensics: LMNTRIX Packets is like memory for your network. With full fidelity packet capture, optimized and stored for up to a year, you will know with absolute confidence whether or not events have impacted your environment. Our packet capture capability is offered with either full packet capture or meta data only. The service helps answer questions such as: How did they get in? What did they do and how did they get around while on our network? What Tactics, Techniques and Procedures (TTP’s) did they use? What did they access?
2) Anomaly Detection: LMNTRIX Packets is built on a foundation of deep network analysis from Packet sensors that span the ”new network”—including the data center, perimeter, core, IoT and operational technology networks as well as cloud workload networks and SaaS applications. Unlike other network traffic analysis (NTA) solutions, LMNTRIX Packets parses over four thousand protocols and processes layer 2 through layer 7 data, including performing encrypted traffic analysis with integration with our dedicated virtual TLS decryption appliance. LMNTRIX Packets uses this information to autonomously profile entities such as devices, users and applications, while also preserving these communications for historical forensics.
Extracted activity data feeds into the LMNTRIX XDR which uses a combination of detection models to uncover malicious intent. An ensemble of machine learning approaches avoid reliance on simplistic and noisy anomaly detection and unsupervised learning. LMNTRIX’s Adversarial Modelling capability enables the uncovering of even the most complex attacker tactics, techniques, and procedures (TTPs), by connecting dots across entities, time, protocols and attack stage. Finally, the platform also ingests threat intelligence indicators of compromise to detect known malware.
LMNTRIX Packets is the world’s first security expert system that can perform autonomous threat hunting and incident triage. Using a combination of artificial intelligence, open-source intelligence, and LMNTRIX’s own human expertise, LMNTRIX Packets autonomously connects the dots across the dimensions of time, entities, and protocols, enabling the solution to present end-to-end situations to our analysts rather than atomic alerts. Analysts thus see the entire scope of an attack as well as investigation and remediation options on a single screen rather than having to piece it together painstakingly themselves. Importantly, federated machine learning allows LMNTRIX customers to see these benefits while keeping their private data firmly within their infrastructure.
3) Retrospection: LMNTRIX Packets detects threats in real time and automatically replays stored packets to discover previously unknown threats. Correlates intelligence from proprietary research, machine learning and flow-based traffic algorithms as well as multiple third-party threat intelligence feeds. Real-time intelligence triggers the retrospection and continuous rescoring of historical traffic. The service help answer the question: Were we breached in the past and we didn’t know about it?
4) Proactive Threat Hunting: Our Threat Hunting service involves the proactive, stealthy, and methodical pursuit and eviction of adversaries inside your network without relying on IOCs.
Hunting within the LMNTRIX hunting platform dataset is accomplished by analyzing intrusions, reverse engineering malware, analyzing traffic generated by malware and other attacks, then selecting metadata generated by the LMNTRIX Packets based on this type of behavior. The LMNTRIX team has conducted many investigations and has created content, tactics and automation for the platform that allow an analyst to quickly navigate the dataset by combining many aspects of behavior into a single piece of metadata. This cuts down on the number of drills needed to find the sessions with the desired behavior, enhancing performance of the platform and reducing the effort needed to find malicious behavior. This has allowed LMNTRIX to discover incidents without any prior knowledge or notification that the organization was under a targeted attack. LMNTRIX has also used these methodologies and content to discovery many incidents where the attacker wasn’t even using malware, but authenticated access, also called Living off the “LANd”.
The unprecedented view into network traffic provided by LMNTRIX Packets is most effective for Incident Response capabilities but can also be used to validate the appropriate enforcement of your security policies and/or uncover areas where these policies and procedures may require improvement. LMNTRIX Packets is intended for organizations who want to uncover new malicious activity and not simply react to alerts based on known threats.
LMNTRIX Packets is not a typical network traffic based sensor, it is not an IDS/IPS or Netflow device, although some of its more basic capabilities could provide some overlap. Metadata is generated to describe a technical aspect or behavior within a network session. A session is defined as one or two related stream(s) of traffic with a requestor and, usually, a responder. These sessions are ordered by capture time and as such time is the first WHERE clause applied to the database when beginning an investigation. Knowing how the data is collected and ordered is integral to understanding how to hunt in LMNTRIX Packets.
Metadata in LMNTRIX Packets is considered indicators of an activity, not signatures like those used by traditional IDS/IPS and as such is handled differently. The logic contained in the LMNTRIX Packets parsers is far more versatile than your typical regex based signatures. The parsers, feeds and application rules that process traffic generate metadata about the structure of the data and extract values from the individual sessions that can be searched for efficiently. This differs from traditional IDS/IPS solutions in that it is possible to find new unknown malicious activity compared to only finding previously identified malicious activity. Signature-like parsers are also used, but because the parser engine is using a common scripting language, more complex logic can be used to determine a match, giving a far lower false-positive rate when used in this manner.
What are the consumption options for LMNTRIX Packets?
There are three (3) options to consider when subscribing to LMNTRIX Packets. These are:
- Packet Capture Option:
- Full Packet Capture – captures packets off the wire in their entirety. Ideal for 100% of investigations. This is a very expensive option and ideal for Enterprise clients.
- Meta Data Capture – captures only Meta data about the packets. Ideal for up to 80% of investigations. This is the most commonly used option.
- Capture Throughput:
This is the total throughout of all packets collected across the Customer’s network as seen on the LMNTRIX XDR. It includes the total throughout captured across all sensors deployed across a Customer network. We offer subscription options starting from 100Mbps to 10Gbps+.
- Data Retention Period:
- LMNTRIX XDR: Data or packets can be retained on the LMNTRIX XDR for 1, 2 or 3 months. Additional data retention is available for up to 12 months at request.
- On-Premise: Optionally, data or packets can be retained on the Customer premises for extended period, based on disk space provisioned by Customer.
What is the LMNTRIX Packets sensor deployment architecture?
The LMNTRIX Packets sensor(s) is deployed on customer’s premises in SPAN or TAP mode after the customer’s perimeter security controls (Firewalls, IPSs, WAF, DDoS, SWG, SMG, etc). Given enough processing capacity, the LMNTRIX Packets sensor can also be deployed on the same LMNTRIX NDR appliance/VM. Once deployed, the sensor is tuned to automatically connect to the LMNTRIX Cloud where it’s managed and monitored by the LMNTRIX CDC.

Are there any best practice LMNTRIX Packets sensor placement strategies?
The most important decision when deploying Sensors is locating strategic areas for capturing network traffic. Once key network segments are identified, the Sensors can be deployed and optimized to meet security and administrative needs.
One more important thing to consider while deploying Sensors is, it should be placed after the Customer’s Perimeter firewalls/Gateways, IPS’s, Email and Web security solutions (Mail Relay servers and Web Proxies) so that the Sensor can analyse traffic after it has been cleansed.
Customer’s can deploy as many sensors as they wish to help meet their segmentation and architecture requirements. For Packets, LMNTRIX does not charge based on the number of sensors deployed, but on the aggregate total throughout across all sensors.
The Sensor requires a SPAN/Mirror/Tap connection to passively capture packets as they traverse your network. It is important to capture network traffic at key network segments to fully benefit from the threat detection capabilities of the sensor.
The most obvious network segment to cover is the Internet Egress Gateway. The Sensor can be deployed almost anywhere in your network but most common deployments include:
- Monitoring egress traffic as it leaves the network at the perimeter/Firewall.
- Internal core to monitor communication of internal traffic flows to/from servers.
- In the DMZ to capture inbound traffic to servers
Within the corporate cloud (Amazon Web Services for example) to monitor inbound/outbound traffic flows from a corporate cloud.
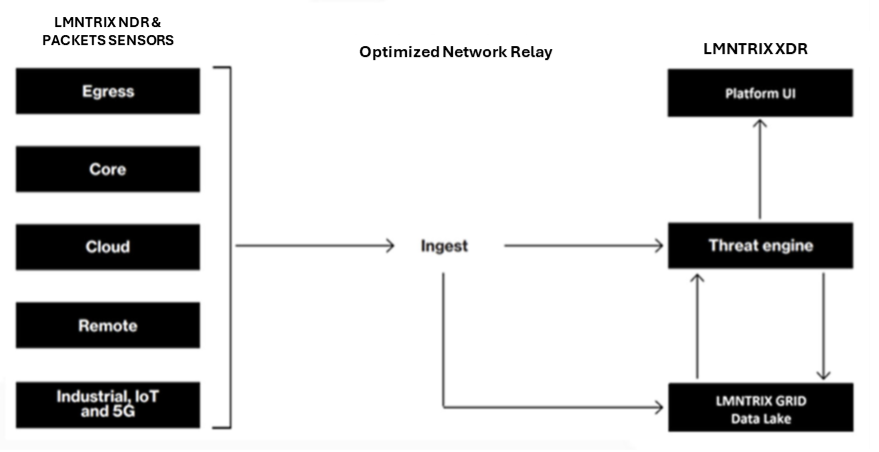
What are the LMNTRIX Packets sensor hardware requirements?
The minimum requirements for a sensor deployment are listed below:
VMware vSphere 5.1 or above
If you have a VMware virtualized environment, LMNTRIX will provide you an Open Virtualization Format (OVF) package that contains a deployable LMNTRIX virtual machine
Or
A physical server with CentOS Linux version 6.x. installed and patched.
NOTE: CentOS 6.x is required. No other version should be considered. A physical server must be dedicated for each sensor deployed.
RAM and CPU Cores
Each sensor requires resources based on the network traffic ingest rate on the configured network interface. The below chart is a guide to be used when configuring a sensor VM or physical server.
I/F Load (Mbps) | No. Cores | RAM (GB) |
160 | 4 | 12 |
240 | 6 | 18 |
320 | 8 | 24 |
400 | 8 | 30 |
480 | 10 | 36 |
560 | 12 | 42 |
640 | 12 | 48 |
720 | 14 | 54 |
800 | 16 | 60 |
880 | 16 | 66 |
960 | 18 | 72 |
1000 | 20 | 78 |
2000 | 36 | 150 |
CPU Core and RAM requirements
Disk Space
A sensor must have a local disk store for files that are extracted from network streams. These files are always stored on the sensor and stay in the local network. The sensor will delete extracted files, oldest first, when disk space is running low. The amount of disk space required is directly proportionate to the volume (Mbps) of traffic the sensor handles and the number and types of files in the network stream.
As a general rule, you should allocate as much disk space for local storage as you can. It is ideal if extracted files are stored for a five (5) day period. The below chart is a guide to be used when configuring the disk space requirements for a sensor VM or physical server.
I/F Load (Mbps) | Disk Space |
160 | 1 TB |
240 | 2 TB |
320 | 4 TB |
400 | 6 TB |
480 | 8 TB |
560 | 10 TB |
640 | N/A |
720 | N/A |
800 | N/A |
880 | N/A |
960 | N/A |
1000 | N/A |
2000 | N/A |
Sensor disk space requirements
Network Interfaces
A sensor must be configured with two (2) network interfaces (I/F). One is a management I/F used to configure, manage, and troubleshoot the sensor. The second I/F is used to capture network traffic. For a physical server sensor, this I/F is connected to a SPAN/TAP. In a VMware infrastructure, this I/F is connected to a VMware virtual switch or a SPAN/TAP. If a SPAN/TAP is used, then a port on the physical hypervisor network I/F must be available for the sensor. The network traffic capture I/F is not configured for an IP address.
The management I/F should be configured with a static IP address if possible. If this is not possible, then DHCP addressing will work, although this will require some work to “find” the host when the IP address is not known. If DHCP is configured, then it is recommended that an IP address be reserved for the I/F on the DHCP server.
SPAN / TAP
The network monitoring I/F of a sensor must be provided an access point to provide network visibility. This is most often done with a Switch Port Analyzer (SPAN) or a Test Access Port (TAP). Regardless of which technology is used, it is critically important that the device be configured properly. If not, then the sensor may “see” a large volume of redundant traffic, or it my only see half of a network conversation.
The most common network access method use is a SPAN port from a switch. The switch is configured to mirror the network traffic from one or more ports to a single port. This allows great flexibility in configuring what network traffic (vlans) are visible to the SPAN port. The network monitoring I/F on the sensor is connected to the configured SPAN port.
A network TAP is a standalone network capture device that is connected inline in a network segment to be monitored. The network monitoring port of the sensor is connected to a port on the TAP. Network TAP’s are the preferred way to connect a sensor to a network since they have greater throughput and are less complicated. The drawback is that they are expensive and you must be inline to work correctly.
LMNTRIX will help you determine the most appropriate method to connect the sensor to a SPAN or TAP depending on your network infrastructure.
How does a LMNTRIX Packets sensor communicate with LMNTRIX XDR?
In order for a sensor to communicate with the LMNTRIX XDR and access other services, firewall rules must be configured to allow the required communication. This communication will only occur from the sensor management I/F only.
The below chart lists the required ports that need to be allowed through an Internet facing firewall and web proxy server if applicable.
TCP Port | Purpose / IP Address* |
22 (SSH) | Cloud aggregator (Outbound) |
80 / 443 (HTTP / HTTPS) | Intel Feeds (Outbound) |
443 (TCP) | XDR forwarder (Outbound) |
53 (UDP/TCP) | DNS service (Internal or Outbound) |
443(HTTPS) | rabbitmq.com (Updates – Outbound) |
123 (UDP) | NTP time service (Outbound) |
3128 (TCP) | Python Pip repositories (Outbound) |
22 (SSH) | System management (Internal) |
9093 | LMNTRIX XDR |
* LMNTRIX IP addresses will be provided at provisioning time. * LMNTRIX IP addresses will be provided at provisioning time. | |
How are encrypted threats detected with LMNTRIX Packets?
The use of Secure Sockets Layer (SSL) or Transport Layer Security (TLS) encryption for Internet and enterprise traffic is growing steadily. Modern applications that use SSL communications by default – such as SharePoint, Exchange, WebEx, Salesforce.com and Google Apps – are commonplace and rapidly growing. Even hosted and mobile email applications such as Gmail, Yahoo and Zimbra utilize SSL encryption by default in today’s workplace environments.
LMNTRIX highly recommends clients to complete their visibility into the encrypted SSL-based traffic with the use of dedicated appliances or switches.
A holistic encrypted traffic management strategy that considers the various division needs, policies to be established, regulatory compliance requirements, and data privacy mandates is essential for all clients.
The LMNTRIX Packets sensor cannot natively detect threats within encrypted traffic and instead it relies on external solutions to deliver decrypted content of SSL flows. This enables LMNTRIX to deliver the necessary visibility into both SSL and non-SSL network traffic.
Supported solutions to manage encrypted traffic include those from Mira Security, Blue Coat (SSL Visibility Appliance and ProxySG solution), Radware (Content Inspection Director (CID) and AppXcel), A10 Networks (Thunder SSLi) and Gagamon (GigaSMART).
What are LMNTRIX responsibilities during Packets onboarding?
The following provides a list of LMNTRIX responsibilities:
- Provide a license to use the LMNTRIX Packets service consistent with the parameters of your purchase.
- If applicable, LMNTRIX authorized partner will provide some of the hardware components required to implement the service.
- Configuration of the sensor ready for deployment by LMNTRIX authorized channel partner or Customer
- Provide remote assistance for implementing the Service. Implementations will need to be scheduled through an assigned project manager.
- Perform remote health monitoring of Service components that are deployed in your environment.
- Provide 24-hour access to our Cyber Defense Center (“CDC”) so that you may ask questions related to the Service. While LMNTRIX will do our best to answer your questions immediately, some inquiries will result in a ticket for the Senior Intrusion Analyst Team which will be addressed during LMNTRIX’ normal business hours, Monday through Friday, 8:00-5:00 U.S. Eastern Standard Time excluding U.S. holidays (“Normal Business Hours”).
What are Client responsibilities during Packets onboarding?
The following provides a list of Client responsibilities:
- Providing an installation environment as required for the Customer-controlled components of the Service. This may include, but is not necessarily limited to, one or more of the following: rack space, power, cooling, network connectivity, a provisioned cloud environment, virtual machine licenses, and hardware to support a virtual sensor.
- Procurement of sensor hardware as per throughput requirements and number of network segments to be mirrored. (Hardware specifications need to be validated by LMNTRIX).
- Locating strategic areas for capturing network traffic to deploy the sensor(s).
- Allotment of private IP address to sensor management interface for bi-directional communication with the LMNTRIX XDR. Provide default gateway details for the sensor to connect to the LMNTRIX XDR.
- Create an access rule on Perimeter firewall(s) for allowing bi-directional access to sensor private IP address.
- Identifying the specific systems or Internet Protocol (“IP”) address ranges that are to be monitored, and providing updates to LMNTRIX when changes to systems that are to be monitored occur
- Addressing any issues associated with sensor credentials.
- Ensuring that their subscription covers their corresponding network throughput.
LMNTRIX Identity
What is LMNTRIX Identity?
LMNTRIX Identity is a subscription feature of LMNTRIX XDR. The Identity enables hyper-accurate detection of identity-based threats, extends MITRE ATT&CK® coverage, and halts novel attacks using multiple advanced techniques.
Comprised of five key service elements that provides a comprehensive intelligence-led identity threat identification, management, and response solution that halts novel identity-based attacks using multiple advanced techniques:
- AD Audit: Applies Active Directory audits with deep visibility across user accounts, access levels, and activities.
- IATDR: Identity and access threat detection & response.
- Attack Paths: Detects chains of abusable privileges and user behaviors, creating direct and indirect connections between computers and users.
- AD Decoy: Uses decoy credentials and services for the detection of attack reconnaissance activity.
- Identity Recon: Employs Darknet Credential Breach Monitoring.
What is the LMNTRIX Identity “Identity and Access Threat Detection & Response (IATDR)” service?
Identity and Access Threat Detection & Response (IATDR) service is designed to protect organizations from attacks that target user identities and access privileges, by using our Identity detection rules and advanced machine learning jobs to identify suspicious activity related to user accounts, and taking swift action against suspicious behavior.
Key features of IATDR include:
- Data Collection: IATDR collects Identity & Access data from you environments, such as Azure EntraID ,Microsoft 365, AD, AWS, Okta, GCP and Google Workspace.
- Identity Detection Rules: Over 125 identity detection rules are continuously monitoring Identity & Access threats across multiple platforms, assessing various factors to ensure comprehensive protection, including:
- User Activity (e.g. Failed login attempts exceeding a certain threshold within a timeframe, Accessing resources outside of normal business hours or location…)
- User Attributes (e.g. High-privilege accounts attempting to access low-privilege resources, Users with recent password resets trying to access sensitive data…)
- Device Characteristics: (e.g. Login attempts from unknown or unauthorized devices)
- Machine Learning Jobs: Identity machine learning (ML) adds another layer of sophistication to Identity threat detection, our Identity Machine learning analyses Users Behavior, Automates the Anomaly Detection, and Reduces False Positives.
- Fine-tuning: Regularly review and adjust rules to ensure optimal balance between identifying real threats and avoiding false positives.
What are the use cases for LMNTRIX Identity IATDR?
- Compromised Account Detection: IATDR detects the login attempt as a deviation from the user’s baseline behavior and triggers an alert
- Privilege Escalation and Lateral Movement Attempts
- Insider Threats: detect unusual data access patterns, such as downloading large amounts of data outside of work hours
- Brute-Force Login Attempts: pre-defined rules can detect these brute-force attempts and automatically lock down the account after exceeding a certain number of failed attempts
- Zero-Day Attacks: machine learning algorithms can identify anomalous user behavior that deviates from established patterns, even if it doesn’t match a pre-defined rule
How do I configure AWS identity data for LMNTRIX Identity IATDR?
Collect AWS CloudTrail data, this data contain account activity across your AWS infrastructure.
Setup
- Create S3 bucket.
- Create an SQS queue in the same AWS Region using Amazon SQS console.
- Replace the access policy attached to the queue with the following queue policy
{
“Version”: “2008-10-17”,
“Id”: “cloudtrail_ID”,
“Statement”: [
{
“Sid”: “__owner_statement”,
“Effect”: “Allow”,
“Principal”: {
“Service”: “s3.amazonaws.com”
},
“Action”: “SQS:*”,
“Resource”: “arn:aws:sqs:us-east-1:227915451108:<queue-name>”,
“Condition”: {
“StringEquals”: {
“aws:SourceAccount”: “<account-id>”
},
“ArnLike”: {
“aws:SourceArn”: “arn:aws:s3:::<bucket-name>”
}
}
}
]
}
Make sure to change the <sqs-queue-arn> and <bucket-name> to match your SQS queue Amazon Resource Name (ARN) and S3 bucket name.
- Configure S3 Bucket
We’ll need to ensure our bucket is configured correctly by modifying the event notification properties. To do this, we’ll navigate to Amazon S3 -> $BucketName -> Properties -> Event notifications -> Create event notification:

Under Event Types, we can select the type of events for which we would like to receive notifications to our SQS queue:

We’ll also need to select the queue where events will be published:

- Configure CloudTrail Logs to S3 Bucket
- Create an IAM user account for LMNTRIX-SIEM and have sufficient access to Amazon S3 and Amazon SQS:
{
“Version”: “2012-10-17”,
“Statement”: [
{
“Sid”: “cloudtrialpolicy”,
“Effect”: “Allow”,
“Action”: [
“sqs:DeleteMessage”,
“s3:GetObject”,
“sqs:ChangeMessageVisibility”,
“sqs:ReceiveMessage”,
“sqs:SendMessage”,
“s3:ListBucket”,
“s3:GetBucketLocation”
],
“Resource”: [
“arn:aws:s3:::*/*”,
“arn:aws:s3:::<bucket-name>”,
“arn:aws:sqs:<region>:<owner-account-id>:<queue-name>”
]
}
]
}
- Share the following with LMNTRIX
- [S3] Bucket ARN
- Region Name
- [SQS] Queue URL
- SQS ARN
- Access Key ID
How do I configure Azure identity data for LMNTRIX Identity IATDR?
Microsoft Office 365:
Collect data from Office 365 and Azure AD activity logs exposed by the Office 365 Management Activity API.
Setup
enable Audit Log and register an application in Microsoft Entra ID (formerly known as Azure Active Directory, once the application is registered:
- Note Application (client) ID and the Directory (tenant) ID in the registered application’s Overview page.
- Create a new secret to configure the authentication of your application:
- Navigate to Certificates & Secrets
- Click New client secret and provide some description to create new secret.
- Note the Value.
- Add permissions to your registered application. Please check O365 Management API permissions for more details.
- Navigate to API permissions page and click Add a permission
- Select Office 365 Management APIs tile from the listed tiles.
- Click Application permissions.
- Under ActivityFeed, select Read permission. This is minimum required permissions to read audit logs of your organization as provided in the documentation. Optionally, select ActivityFeed.ReadDlp to read DLP policy events.
- Click Add permissions.
- If Read permission under Microsoft.Graph tile is not added by default, add this permission.
- After the permissions are added, the admin has to grant consent for these permissions.
Microsoft Entra ID:
Collect data from
- Sign-in logs: Information about sign-ins and how your users use your resources.
- Identity Protection logs: Information about user risk status and the events that change it.
- Provisioning logs: Information about users and group synchronization to and from external enterprise applications.
- Audit logs: Information about changes to your tenant, such as users and group management, or updates to your tenant’s resources.
Setup Microsoft EntaID:
- Diagnostic setting to export logs from Microsoft EntaID to Event Hubs
- Event Hub to store in-flight logs exported by Microsoft EntaID
- Storage Account Container to store information about logs consuming
How do I configure GCP identity data for LMNTRIX Identity IATDR?
Collect audit logs of administrative activities and accesses within your Google Cloud resources
Setup: set up a Service Account with a Role and a Service Account Key to access data on your GCP project
- Service Account: create a Service Account. A Service Account (SA) is a particular type of Google account intended to represent a non-human user who needs to access the GCP resources
- Role privileges:
- metricDescriptors.list
- timeSeries.list
- subscriptions.consume
- subscriptions.create *
- subscriptions.get
- topics.attachSubscription *
- Service Account Keys
Now, with your brand new Service Account (SA) with access to Google Cloud Platform (GCP) resources, you need some credentials to associate with it: a Service Account Key.
From the list of SA:
- Click the one you just created to open the detailed view.
- From the Keys section, click “Add key” > “Create new key” and select JSON as the type.
- Download and store the generated private key securely (remember, the private key can’t be recovered from GCP if lost).
- The Project Id : the Google Cloud project ID where your resources exist.
- Credentials File: Save the JSON file with the private key in a secure location of the file system.
- Share the following with LMNTRIX
- Project Id
- Credentials File
- Subscription Name: the short subscription name here, not the full-blown path with the project ID. You can find it as “Subscription ID” on the Google Cloud Console
- Topic: Name of the topic where the logs are written to.
Google Workspace:
Collect data from the different Google Workspace audit reports APIs.
Setup
- In order to Collect data from the Google Reports API you must:
- Have an administrator account.
- Set up a ServiceAccount using the administrator account. https://support.google.com/workspacemigrate/answer/9222993?hl=en
- Set up access to the Admin SDK API for the ServiceAccount. https://support.google.com/workspacemigrate/answer/9222865?hl=en
- Enable Domain-Wide Delegation for your ServiceAccount. https://developers.google.com/admin-sdk/reports/v1/guides/delegation
- This integration will make use of the following oauth2 scope:
- https://www.googleapis.com/auth/admin.reports.audit.readonly
- download your service account credentials as a JSON file and share with LMNTRIX
- Click the Advanced option of Google Workspace Audit Reports. The default value of “API Host” is https://www.googleapis.com. The API Host will be used for collecting admin, drive, groups, login, saml, and user accounts logs.
How do I configure Okta identity data for LMNTRIX Identity IATDR?
Collects events from the Okta API, specifically reading from the Okta System Log API.
Types Of Authentications
- API Key: In this type of authentication, we only require an API Key for authenticating the client and polling for Okta System Logs.
- Oauth2: In this type of authentication, we require the following information:
- Your Okta domain URL. [ Example: https://dev-123456.okta.com ]
- Your Okta service app Client ID.
- Your Okta service app JWK Private Key
- The Okta scope that is required for OAuth2. [ By default this is set to okta.logs.read which should suffice for most use cases ]
Steps to acquire Okta Oauth2 credentials:
- Acquire an Okta dev or user account with privileges to mint tokens with the * scopes.
- Log into your Okta account, navigate to Applications on the left-hand side, click on the Create App Integration button and create an API Services application.
- Click on the created app, note down the Client ID and select the option for Public key/Private key.
- Generate your own Private/Public key pair in the JWK format (PEM is not supported at the moment) and save it in a credentials JSON file or copy it to use directly in the config.
How do I configure On-premise AD identity data for LMNTRIX Identity IATDR?
Collects Identity events from your Active Directory by deploying LMNTRIX-Identity-Agent on each Active directory server.
What is the LMNTRIX Identity “Attack Paths”?
The Attack Paths module is designed to assess and analyze the security posture of Active Directory (AD) environments. By mapping out relationships and permissions within AD, Attack Paths enables security professionals to identify and visualize potential attack paths, privilege escalation vectors, and lateral movement opportunities.

Key features Attack Paths include:
- Attack Path Mapping: Attack Paths identifies and maps out potential attack paths within AD environments, helping users understand how attackers could compromise their network.
- Relationship Analysis: Attack Paths analyzes relationships between users, groups, computers, and other objects in AD to uncover security vulnerabilities and misconfigurations.
- Visualization: Attack Paths provides a graphical interface for visualizing the complex relationships and attack paths discovered during analysis, enhancing understanding and decision-making.
- Data Collection: Attack Paths collects data from AD environments using Attack Path sensor, a stealthy data collection tool designed to minimize its footprint and avoid detection by security monitoring tools.
- Custom Querying: Users can perform custom queries and analyses within Attack Paths to investigate specific aspects of their AD environment and identify security risks.
What are the use cases for LMNTRIX Identity “Attack Paths”?
- Security Assessment: Attack Paths is used to assess the security posture of AD environments, identifying vulnerabilities and weaknesses that could be exploited by attackers.
- Penetration Testing: Penetration testers leverage Attack Paths to simulate real-world attack scenarios, uncovering security flaws and evaluating the effectiveness of security controls.
- Red Teaming: Red Teamers use Attack Paths to perform comprehensive security assessments, testing the organization’s defenses and incident response procedures.
- Vulnerability Management: Attack Paths helps prioritize remediation efforts by identifying and prioritizing security vulnerabilities, misconfigurations, and excessive permissions within AD environments.
How do I deploy LMNTRIX Identity “Attack Paths”?
Attack Paths relies on a sensor for data collection from AD environments. Attack Paths sensor collects various types of data from AD environments, including information about users, groups, computers, permissions, and group memberships.
Pre-requisites:
- .Net Framework 4.0 or higher
- Need to run it on AD server.
- Open secure.lmntrix.com via 443 on firewall.
Installation Steps:
- Extract the AttackerPathsSensor.zip
- Open the command prompt in Administrator mode and redirect to the extracted folder path.
- Execute the command below to install the service on Windows Server. The installer will copy the required files in to into C:\Program Files\AttackerPathsSensor folder and create the windows service.
InstallSvc.cmd i (Refer below image)

Once the installation is completed. “AttackerPathsSensorSvc” windows service automatically starts.
Uninstallation Steps:
- Open the command prompt in Administrator mode and redirect to the installer folder path.
- Execute the command below to uninstall the service on windows server. Installer will stop the service and remove the files from c:\Program Files\AttackerPathsSensor folder and delete the folder as well.
InstallSvc.cmd u (Refer below image)

Automated Attack Validation (AAV)
What is network penetration testing?
Network penetration testing is a security test where experts try to hack into an organization’s computer network to find vulnerabilities and weaknesses. It’s like a “mock” hack to see if a hacker could get in and cause damage. The goal is to identify any problems and fix them before a real hacker can take advantage. It’s basically a way to check the security of an organization’s network.
What is LMNTRIX AAV?
LMNTRIX AAV is a subscription feature of LMNTRIX XDR. LMNTRIX AAV is a scripted network penetration testing platform that runs the exact same steps and processes performed by a security consultant doing a live pentest. This includes technical tasks such as host discovery, service enumeration, vulnerability analysis, exploitation, post-exploitation, privilege escalation and lateral movement, as well as documentation and reporting.
LMNTRIX AAV combines the knowledge of multiple highly skilled penetration testers along with numerous tools and techniques used in the industry by penetration testers with over a decade of experience and certifications.
How does LMNTRIX AAV differ from a vulnerability assessment?
A vulnerability assessment simply informs an organization about the vulnerabilities that are present within its environment. However, a vulnerability assessment does not attempt to exploit those vulnerabilities to determine the potential impact of successfully exploiting those vulnerabilities. This is not a flaw with vulnerability scanners; they just simply aren’t designed to do this.
LMNTRIX AAV differs in that it is able to perform exploitation and post-exploitation techniques to demonstrate to customers how successfully exploiting a vulnerability could potentially lead to further access to systems and/or confidential data leakage within their environment.
What is the biggest difference between LMNTRIX AAV compared to a traditional network penetration test?
Traditional penetration tests are extremely time-consuming, whereas LMNTRIX AAV can run numerous tools simultaneously, wait for them to complete, automatically analyze the results, and determine its next move. This saves a significant amount of time from simply running one command at a time. Furthermore, LMNTRIX AAV reduces the time spent reporting from 6 hours (average between reporting, QA, etc.) to less than a minute. That’s a 29,900% speed increase per assessment that it saves.
What is involved in a network penetration test?
In network penetration tests, several attempts are made to exploit security vulnerabilities with the ultimate goal of gaining access to data and systems. These exploit attempts include targeting patching deficiencies, authentication weaknesses, misconfigurations, and even users (via man-in-the-middle attacks). After an initial compromise, post-exploitation activities occur, which typically include privilege escalation, lateral movement, and enumeration of accessible resources to find sensitive data.
What are the benefits of network penetration testing for an organization?
Some of the benefits of network penetration testing include the following:
- Prioritizing the remediation of critical security weaknesses
- Understanding how an attacker could gain access to sensitive data or systems
- Meeting compliance and regulatory requirements
- Testing and improving incident response procedures
- Validating the effectiveness of security controls
What kind of reports and deliverables can be expected from a network penetration test?
It is common to expect an executive summary, technical report, and a vulnerability report (or spreadsheet) as part of the final deliverables for a network penetration test. These reports are specifically tailored toward executive and technical audiences to help understand the risks that the environment poses to the organization
Does LMNTRIX AAV cover MITRE ATT&CK types?
The platform does indeed actually replicate some of the attacks documented in the MITRE ATT&CK framework, and the reporting structure includes references to the framework at the moment.
Are automated penetration testing tools as effective as manual penetration testing?
While automated tools provide faster and more consistent results, manual testing may uncover complex vulnerabilities that automated tools might miss. A combined approach often provides the best results specially where web application or API testing is required.
How often should automated penetration testing be performed?
Automated penetration testing can be conducted on a continuous or periodic basis. Many organizations choose to run tests weekly or monthly to maintain up-to-date vulnerability assessments.
How is LMNTRIX AAV priced?
LMNTRIX AAV is priced according to the total number of internal and external IPs to be tested at any one time. IPs reset each month until the end of the subscription. Unused IPs do not roll over to the following month or subscription. Clients can upgrade to the next IP block during the first 10 months of their subscription and only pay the difference. Each assessment consumes IPs and will automatically deduct from the allocated monthly IP count until the reset date.
Can LMNTRIX AAV integrate with other security tools?
Yes, LMNTRIX AAV offers integration with popular SIEMs, ticketing systems, and other security tools to streamline workflows.
Does LMNTRIX AAV support internal and external network testing?
Yes, LMNTRIX AAV can test both internal and external networks, allowing organizations to identify vulnerabilities from both an insider and outsider perspective.
What is the reporting process like for LMNTRIX AAV?
LMNTRIX AAV provides comprehensive reports that include vulnerability details, impact assessment, and remediation suggestions. Reports are generated in various formats for easy sharing and compliance.
Can LMNTRIX AAV perform post-exploitation activities?
Yes, LMNTRIX AAV includes post-exploitation capabilities, which allow it to simulate data exfiltration, privilege escalation, and lateral movement to understand the potential impact of vulnerabilities.
How does LMNTRIX AAV ensure that automated testing doesn’t disrupt normal business operations?
LMNTRIX AAV uses safe testing methods and configurable settings to minimize the risk of disruption, allowing organizations to control the intensity and scope of tests.
Is it possible to customize attack scenarios in LMNTRIX AAV?
Yes, LMNTRIX AAV allows users to customize attack scenarios and adjust the scope of the testing to focus on specific environments or assets.
What are the key requirements for deploying LMNTRIX AAV in an organization?
LMNTRIX AAV requires minimal setup, typically involving a virtual appliance or cloud-based deployment, and access permissions to relevant network segments.
Does LMNTRIX AAV support cloud environment testing?
Yes, LMNTRIX AAV can perform penetration testing across cloud environments, identifying vulnerabilities in services such as AWS, Azure, and Google Cloud Platform.
How does LMNTRIX AAV prioritize vulnerabilities?
LMNTRIX AAV uses risk scoring based on factors such as exploitability, impact, and severity to prioritize vulnerabilities in its reports.
Can LMNTRIX AAV conduct automated social engineering attacks?
No. LMNTRIX AAV focuses primarily on technical vulnerabilities, it cannot simulate social engineering as part of its broader attack scenarios.
How does automated penetration testing help with regulatory compliance?
Automated testing can help organizations meet compliance requirements by providing consistent vulnerability assessments and detailed reports for standards like PCI-DSS, HIPAA, and GDPR.
Is it safe to use automated penetration testing in a live production environment?
While automated tools aim to be non-disruptive, it’s recommended to perform tests during low-traffic periods or in a staging environment when possible to minimize risks.
Can automated penetration testing tools identify zero-day vulnerabilities?
Automated tools are generally effective at detecting known vulnerabilities; however, they may not be able to identify unknown (zero-day) vulnerabilities without updated exploit libraries.
Does LMNTRIX AAV offer role-based access control (RBAC)?
Yes, LMNTRIX AAV includes RBAC features to ensure that only authorized personnel can access sensitive test results and configuration settings.
Can automated penetration testing tools replace vulnerability scanners?
Automated penetration testing tools offer more comprehensive assessments by simulating actual attacks, while vulnerability scanners typically identify vulnerabilities without attempting exploitation. Both tools complement each other.
How does LMNTRIX AAV handle sensitive data encountered during testing?
LMNTRIX AAV adheres to data protection best practices, ensuring that sensitive information is handled securely and that test data is stored and encrypted according to industry standards.
Is it possible to schedule recurring tests with LMNTRIX AAV?
Yes, LMNTRIX AAV supports scheduled testing, allowing organizations to run penetration tests on a recurring basis, such as weekly, monthly, or quarterly.
What steps should organizations take after receiving an automated penetration testing report?
After a test, organizations should review the findings, prioritize remediation based on risk, and apply recommended fixes. Retesting can be performed to verify that vulnerabilities are resolved.
How do automated penetration testing tools compare to red teaming exercises?
Automated tools focus on finding technical vulnerabilities, while red teaming includes social engineering and operational tactics. Red teaming services such as the LMNTRIX Red Teaming involves more comprehensive and creative attack simulations.
What training is needed to use automated penetration testing tools like LMNTRIX AAV?
These tools are designed to be user-friendly, with intuitive interfaces and detailed documentation. Basic cybersecurity knowledge is helpful, but extensive training is usually not required for standard operation.
LMNTRIX Security Information and Event Management (SIEM)
What is LMNTRIX SIEM?
LMNTRIX SIEM is a subscription feature of LMNTRIX XDR that provides a security solution for monitoring, detecting, and responding to security threats. It’s built on LMNTRIX XDR and integrates data from various sources for comprehensive threat detection and response.
How does LMNTRIX SIEM work?
LMNTRIX SIEM works by collecting, storing, and analyzing security data from logs, events, and metrics across multiple sources in your network. It uses LMNTRIX XDR for indexing, searching visualization and analysis of data. Users can write custom detection rules, use machine learning for anomaly detection, and build dashboards to monitor security events in real-time.
What data sources can LMNTRIX SIEM ingest?
LMNTRIX SIEM can ingest a wide variety of data sources, including logs from network devices, endpoint agents, cloud services, operating systems, and application logs. Commonly used integrations include AWS CloudTrail, Azure, Google Cloud, Zeek, and Sysmon.
How does LMNTRIX SIEM compare to other SIEM solutions?
Yes, LMNTRIX SIEM supports real-time detection. It allows users to configure real-time alerts by writing detection rules and leverages machine learning models to detect anomalies in real-time. This is useful for identifying suspicious activities as they happen and responding swiftly.
Does LMNTRIX SIEM support real-time detection?
In network penetration tests, several attempts are made to exploit security vulnerabilities with the ultimate goal of gaining access to data and systems. These exploit attempts include targeting patching deficiencies, authentication weaknesses, misconfigurations, and even users (via man-in-the-middle attacks). After an initial compromise, post-exploitation activities occur, which typically include privilege escalation, lateral movement, and enumeration of accessible resources to find sensitive data.
How is LMNTRIX SIEM priced?
LMNTRIX SIEM follows a tiered pricing model based on daily data ingestion capacity. Costs are primarily associated with the underlying LMNTRIX XDR (storage and compute resources) as well as any additional premium services such as 24/7 monitoring and incident response. Subscription options can start at 1GB/day to 100+GB/day ingestion.
Can LMNTRIX SIEM handle cloud environments?
Yes, LMNTRIX SIEM is designed to handle multi-cloud environments. It supports ingestion of cloud logs from major providers like AWS, Microsoft Azure, and Google Cloud. Additionally, it provides cloud-native monitoring and security tools to protect cloud workloads.
How customizable is LMNTRIX SIEM?
LMNTRIX SIEM is highly customizable. Users can create custom dashboards, detection rules, and data visualizations to meet specific security monitoring needs. Its open architecture also allows integration with other tools and data sources, making it adaptable for different environments.
What are the key features of LMNTRIX SIEM?
LMNTRIX SIEM offers features such as centralized log management, threat detection and analysis, visualizations, customizable dashboards, pre-built and custom detection rules, and machine learning for anomaly detection. These features make it a comprehensive tool for monitoring security data in real-time and responding to threats.
How does LMNTRIX SIEM leverage machine learning for threat detection?
LMNTRIX SIEM uses machine learning to detect anomalies by establishing baselines for normal behavior across data sources. It can then flag deviations from this baseline as potential threats. For example, it might detect unusual login patterns or data exfiltration attempts. These models can be customized or used out-of-the-box and are continuously updated to adapt to new patterns.
What is the LMNTRIX Common Schema (LCS), and how does it benefit LMNTRIX SIEM?
The LMNTRIX Common Schema (LCS) is a data model that standardizes the way security data is ingested and organized within LMNTRIX XDR and SIEM. LCS makes it easier to correlate data across different sources, providing a unified view of events. This schema ensures consistent field names, which simplifies analysis and allows for more effective searches and visualizations.
How does LMNTRIX SIEM support event sources not supported out of the box?
LMNTRIX offers parser development at no extra cost for all LMNTRIX SIEM clients. Parser development can take anywhere from few days to few weeks to complete depending on the complexity of the event source.
How does LMNTRIX SIEM handle data storage and scalability?
LMNTRIX SIEM is built on the LMNTRIX XDR platform, which is designed for scalability. It handles large volumes of data by distributing it across clusters. This makes it suitable for organizations of various sizes, from small businesses to large enterprises. LMNTRIX’s architecture allows for horizontal scaling, which means adding more nodes to increase capacity.
What are the deployment options for LMNTRIX SIEM?
LMNTRIX SIEM is offered as a cloud-based SaaS subscription inclusive of platform operations and maintenance. Optional SIEM alert monitoring and incident response is available from LMNTRIX or one of our certified partners.
How long does LMNTRIX SIEM retain our data?
The standard configuration of LMNTRIX SIEM retains data online for 90 days and archived for 9 months. This gives clients access to a total of one year data. Additional online and archive capacity is available on request.
How does LMNTRIX SIEM integrate with other LMNTRIX XDR tools?
LMNTRIX SIEM is fully integrated with the LMNTRIX XDR, including for search and storage, visualization, containment, incident management and for data ingestion. This integration allows users to build a seamless workflow for collecting, processing, storing, and analyzing security data in one unified platform.
Does LMNTRIX SIEM provide alerting capabilities?
Yes, LMNTRIX SIEM offers alerting features through LMNTRIX XDR, allowing users to set up alerts based on custom rules. These alerts can be sent to various channels, such as email, Slack, or custom webhooks. Additionally, alerting rules can be configured to trigger responses based on specific threat indicators, enabling faster remediation.
What types of organizations benefit most from using LMNTRIX SIEM?
LMNTRIX SIEM is particularly beneficial for medium to large enterprises with complex IT infrastructures and multiple data sources. It is also suitable for organizations that need a scalable, flexible, and customizable security solution that can aid in compliance reporting and post breach forensics and incident response.
How can LMNTRIX SIEM assist with compliance requirements?
LMNTRIX SIEM provides auditing capabilities and data retention options that help organizations meet compliance requirements for standards like GDPR, HIPAA, and PCI DSS. Its ability to store and analyze logs, along with its alerting and reporting functions, can support compliance audits and investigations by tracking and documenting security events.
What support options are available for LMNTRIX SIEM?
The standard subscription to LMNTRIX SIEM includes 24/7 support. This provides clients 24/7 access to LMNTRIX’s cyber defense centre, security updates, and guidance for deployment, configuration, and optimization.
How does LMNTRIX SIEM handle threat intelligence?
LMNTRIX SIEM standard configuration includes integration with LMNTRIX Intelligence which is made up of over 300 threat feeds from open source, commercial and our own sensor network. LMNTRIX SIEM can also integrate with threat intelligence feeds, such as open-source feeds or commercial threat intelligence platforms. Users can ingest threat data to enrich their security logs with additional context, such as IP reputation, and correlate events against known threat indicators for enhanced detection capabilities.
Does LMNTRIX SIEM support multi-tenancy for MSSPs?
Yes, LMNTRIX SIEM supports multi-tenancy features, making it suitable for Managed Security Service Providers (MSSPs). MSSPs can manage multiple client environments within a single LMNTRIX deployment while maintaining data segregation and security.
What are LMNTRIX SIEM’s capabilities for endpoint security?
LMNTRIX SIEM can collect events from any 3rd party endpoint security solution and it integrates with the LMNTRIX EDR, which provides endpoint detection and response (EDR) capabilities. This agent enables real-time monitoring of endpoint activities, such as process creation, file access, and network connections. LMNTRIX SIEM can use this data to detect malicious behaviors and respond to endpoint threats.
How does LMNTRIX SIEM handle data ingestion and parsing?
Data ingestion in LMNTRIX SIEM is facilitated by LMNTRIX Data Shippers (LDS), which collect and parse data from various sources. LDS are lightweight data shippers for specific log types, which also offers advanced filtering and transformation. LDS allow LMNTRIX to standardize data formats and enrich logs before storing them in LMNTRIX XDR.
What are some common use cases for LMNTRIX SIEM?
LMNTRIX SIEM is used for various security purposes, including network monitoring, threat hunting, insider threat detection, anomaly detection, and compliance monitoring. It is also useful for centralized log management, where it collects logs from multiple sources for unified analysis and rapid incident response.
How customizable are the detection rules in LMNTRIX SIEM?
Detection rules in LMNTRIX SIEM are highly customizable. Users can build custom rules based on their unique security needs and specific environments. LMNTRIX provides a detection rule builder that allows analysts to specify conditions, thresholds, and alerting actions, which enables tailored detection capabilities.
Does LMNTRIX SIEM support automated response actions?
Yes, LMNTRIX SIEM can trigger automated response actions through integrations with SOAR platforms or by using custom webhooks to initiate responses. For example, it can send an alert to an orchestration tool that automates actions like blocking an IP, disabling a user account, or isolating a compromised endpoint.
What are some limitations of LMNTRIX SIEM?
While LMNTRIX SIEM is powerful and flexible, some limitations include:
- Steep Learning Curve: It may require a solid understanding of the LMNTRIX XDR to set up and maintain effectively.
- Custom Configuration: Out-of-the-box functionality may not be sufficient for some users, necessitating significant customization.
- Data Volume Costs: High data ingestion volumes can lead to increased costs due to storage and compute requirements, especially in large environments.
LMNTRIX Email
What is LMNTRIX Email?
LMNTRIX Email is a subscription feature of LMNTRIX XDR that provides an email security solution for detecting and responding to email borne security threats that routinely bypass existing perimeter email security solutions such as Exchange Online, Mimecast and Proofpoint. LMNTRIX Email is a post-breach email security solution that uses Microsoft graph and Gmail APIs to identify threats in user mailboxes after they have bypassed traditional email security layers like Microsoft Defender for Office 365, Mimecast and Proofpoint.
How does LMNTRIX differ from traditional email security solutions?
Unlike traditional solutions that focus on blocking threats at the perimeter, LMNTRIX is designed to detect threats that have already reached the inbox, offering an additional layer of security by identifying malicious emails that bypass other filters.
What type of threats does LMNTRIX Email detect?
LMNTRIX detects threats such as phishing attacks, malicious attachments, suspicious links, and other harmful content that existing security layers might have missed.
Why is LMNTRIX considered a post-breach solution?
It operates within the mailbox after initial security layers have allowed emails through, focusing on threats that have bypassed frontline defenses like Microsoft Defender for Office 365, Mimecast or Proofpoint.
What email platforms does LMNTRIX support?
The solution currently supports Microsoft Exchange Online (part of Office 365) and Gmail through their respective APIs.
How does LMNTRIX use the Exchange Online and Gmail APIs?
LMNTRIX integrates with these APIs to analyze email content, attachments, and links directly within user mailboxes, detecting suspicious activities and providing detailed threat intelligence.
Does LMNTRIX quarantine or delete malicious emails?
Yes, LMNTRIX can automatically quarantine or delete malicious emails once identified, based on predefined security policies.
How does LMNTRIX identify threats missed by other security solutions?
LMNTRIX uses a combination of threat intelligence, sandboxing, AI-driven threat analysis, behavioral analysis, and anomaly detection to uncover hidden threats that have evaded perimeter defenses.
Can LMNTRIX scan historical emails, or is it only for new emails?
LMNTRIX can only scan new emails within the mailbox.
What types of email attachments does LMNTRIX scan?
LMNTRIX scans all common attachment types, including PDFs, Word documents, Excel files, and compressed files, for embedded malware or malicious links.
How is LMNTRIX deployed in an organization’s environment?
LMNTRIX is deployed as a cloud-based solution that integrates with Office 365 and Google Workspace through their APIs, requiring minimal setup and no on-premises hardware.
Does LMNTRIX require administrative access to user mailboxes?
Yes, LMNTRIX needs API-level access to user mailboxes for scanning and threat detection but follows strict data privacy protocols to ensure security.
Can LMNTRIX integrate with existing SIEM or SOAR platforms?
Yes, LMNTRIX supports integration with SIEM and SOAR platforms, allowing organizations to correlate email threats with other security events for a holistic view of their security posture.
What are the system requirements for implementing LMNTRIX?
Since LMNTRIX is a cloud-based solution, there are minimal on-premises requirements. Organizations only need compatible Office 365 or Google Workspace accounts with API access enabled.
How long does it take to implement LMNTRIX Email?
It takes less than 30 minutes to configure the service. Clients are supplied with detailed instructions on how to configure their O365 and Gmail environments to give LMNTRIX Email the necessary API access.
How much does LMNTRIX Email cost, and how is it priced?
LMNTRIX Email costs less than a cup of coffee per month for each mailbox. Pricing is based on the number of mailboxes in your organization, making it affordable and scalable as your needs grow.
Is LMNTRIX compatible with mobile email clients?
Yes, LMNTRIX monitors emails regardless of the client used to access them, as the solution integrates directly with Exchange and Gmail at the server level.
How does LMNTRIX ensure user data privacy?
LMNTRIX follows strict data privacy standards, limiting access to only relevant email data and using encryption protocols to protect sensitive information. Furthermore, LMNTRIX is certified to ISO27001, SOC2 and PCI DSS security standards.
Can users review flagged emails before LMNTRIX takes action?
No, LMNTRIX cannot be configured to notify users or administrators of flagged emails, allowing them to review potential threats before action is taken.
Does LMNTRIX provide reports on detected threats?
Yes, LMNTRIX generates detailed reports on detected threats, including information on email origins, type of threat, and suggested remediation steps.
What data does LMNTRIX retain for analysis and reporting?
LMNTRIX retains only necessary data for threat analysis and reporting, following industry standards for data retention and privacy compliance.
How quickly can LMNTRIX detect threats within user mailboxes?
LMNTRIX operates in near real-time, scanning emails and identifying threats within minutes after they enter a mailbox.
Can LMNTRIX automatically block malicious links within emails?
Yes, LMNTRIX can neutralize malicious links by altering them or notifying users not to click on them, depending on the configuration.
How does LMNTRIX handle email phishing attacks?
LMNTRIX identifies phishing emails by analyzing email headers, sender reputation, and suspicious patterns, flagging and isolating such emails from users.
Does LMNTRIX support multi-factor authentication for secure access?
Yes, LMNTRIX supports multi-factor authentication (MFA) for administrators to ensure secure access to the LMNTRIX XDR platform and email data.
What types of analysis does LMNTRIX perform on email attachments?
LMNTRIX uses sandboxing and static and dynamic analysis to inspect attachments for embedded malware, malicious macros, and other exploitative content.
Does LMNTRIX replace existing email security solutions?
No, LMNTRIX is a complementary post-breach solution that works alongside Microsoft Defender for O365, Mimecast, Proofpoint, and other email security solutions to catch threats that bypass initial defenses.
Can LMNTRIX send alerts to IT teams via ticketing systems?
Yes, LMNTRIX integrates with popular ticketing systems such as Jira and ServiceNow, enabling automated alerting and incident tracking for IT and security teams.
What remediation options does LMNTRIX offer?
LMNTRIX provides automated remediation, including quarantining, deleting, and blocking emails or attachments, as well as options for manual review.
How does LMNTRIX help organizations respond to email threats more effectively?
By providing detailed threat insights and automated remediation options, LMNTRIX allows organizations to respond quickly to email threats, reducing potential risks.
Can LMNTRIX help prevent similar threats in the future?
Yes, LMNTRIX learns from past incidents and adjusts its detection algorithms to improve future threat detection, helping to prevent similar attacks from succeeding.
LMNTRIX OT
What is LMNTRIX OT?
LMNTRIX OT is a subscription feature of LMNTRIX XDR that provides OT and IoT security capability designed to enhance visibility, security, and monitoring of industrial control systems (ICS) and critical infrastructure.
What industries does LMNTRIX OT serve?
LMNTRIX OT serves industries such as energy, manufacturing, utilities, transportation, oil and gas, and healthcare, focusing on environments with critical infrastructure.
What is the primary function of LMNTRIX OT?
The primary function is to provide real-time visibility, threat detection, and anomaly detection for OT and IoT environments, helping organizations monitor and protect their industrial networks.
How does LMNTRIX OT support industrial cybersecurity?
LMNTRIX OT uses network detection & response (NDR), network traffic monitoring, behavioral analytics, machine learning, endpoint detection & response, threat intelligence and deceptions to detect threats and anomalies in industrial control systems, helping prevent cyber incidents and operational disruptions.
What are the key components of LMNTRIX OT' solution?
Key components include LMNTRIX NDR for OT, LMNTRIX Packets for OT, LMNTRIX EDR for OT, LMNTRIX Deceive for OT and LMNTRIX Intelligence for OT.
Where on a typical OT network are LMNTRIX OT components deployed?
Using the Purdue model below we can see where each of the LMNTRIX OT security functions are deployed:
LMNTRIX NDR and Packets for OT are deployed on a SPAN or TAP port at level 3.5 and inspects traffic from all lower levels. Both NDR and Packets sensors can be deployed on the same machine as depicted in the below architecture or on separate machines.
LMNTRIX EDR for OT can be seen deployed on all workstations and servers including the SCADA servers, Historian, DNS, Patching servers, and Jump box.
Finally, Decoys from LMNTRIX Deceive for OT can be seen deployed at Levels 2, 3 and 3.5 using a variety of protocols including Modbus, S7comm, Bacnet, IPMI, ENIP, Guardian AST, Kamstrup, and Hart-ip.

Is LMNTRIX OT superior to other OT security solutions?
Yes, LMNTRIX OT is considered far superior to point product OT security solutions as it supports both IT and OT environments using the same solution while providing protection against multiple threat vectors (endpoint, network, lateral movement, encrypted attacks) and is completely operationalised and delivered with LMNTRIX MDR as standard capability.
Unlike other vendor OT security solutions, the LMNTRIX architecture and technology stack provides complete support for ICS/SCADA environments.
The LMNTRIX multi-vector and holistic architecture detects any threat to the SCADA application, process or network, providing granular visibility of SCADA traffic and facilitating attack forensics:
- We monitor and record all SCADA activity out-of-band and independent of the ability of SCADA devices to send logs
- We baseline normal behavior and alert on deviations from the baseline to prevent undesired network operations based upon policy
- With our integrated network and endpoint threat forensics together with deceptions everywhere we reveal the entire sequence of an attack event
- All security and events related to our architecture are centrally managed, providing a complete view across your enterprise and control networks
- We support the industry’s most extensive support of ICS/SCADA-specific protocols including BACNet, DNP3, IEC-60870-5-104, IEC 60870-6 (ICCP), IEC 61850, MMS, Modbus, OPC, Profinet, S7 (Siemens) and many others
- We detect and prevent exploits of ICS vulnerabilities with SCADA IDS signatures and on the endpoint using exploit prevention using hardware assisted control flow integrity (HA-CFI), closing the window of exposure between vulnerable and patched systems.
- We detect lateral movement using SCADA specific deceptions
- We recommend LMNTRIX EDR to be installed on all Corporate endpoints in Prevention Mode. However, LMNTRIX EDR for OT recommended deployment is on all PCN endpoints (Control/HMI Servers) in Detection Mode only – Not Prevention. It can be installed on any device permitted that supports Windows, Linux, Mac and Solaris. Recommended but not required on Control Servers and HMIs. Not recommend on any other PCS components.
- Our network sensors can utilise a full range of threat detection capabilities including deceptions, IDS, anti-malware, and sandboxing to detect inbound threats to SCADA networks
In summary our architecture provides a complete IT-OT security solution that protects the corporate network past the perimeter, the bridge between IT and OT networks and operator workstations and SCADA devices within the OT network.
What is LMNTRIX NDR for OT, and what does it do?
LMNTRIX NDR for OT is a network sensor that provides network visibility, asset inventory, vulnerability assessment, and threat detection for OT and IoT environments.
How does LMNTRIX NDR for OT detect threats?
It uses machine learning, behavioral analysis, and signature-based detection to identify unusual patterns, known vulnerabilities, and potential threats in OT and IoT networks.
What is LMNTRIX Packets for OT, and what does it do?
LMNTRIX Packets primary use case is post breach forensics as it captures and retains OT meta-data traffic for minimum 30 days and makes it available to investigators. The other use case for LMNTRIX Packets is the detection of slow and advanced attacks using a combination of retrospection, anomaly detection and threat hunting.
What is LMNTRIX Deceive for OT, and what does it do?
LMNTRIX Deceive for OT is designed to detect the presence of threat actors that have a foot hold within OT networks and are looking to move laterally.
LMNTRIX Deceive for OT weaves a deceptive layer over your entire network – every endpoint, server and network component is coated with deceptions. The moment an attacker penetrates your network, they are in an illusive world where all the data is unreliable. If attackers cannot collect reliable data, they cannot make decisions. And if they cannot make decisions, the attack is paralysed. This approach provides the following benefits:
- No false positives – every alert is treated as a major incident and escalated to you
- Turn the tables on the bad guys!
- Change the economics of cyber defence by shifting the cost to the attacker
The intent of the service is to address insider threats and advanced human adversaries that are now on your network moving laterally stealing data and actively working to elevate their privileges. Existing solutions such as SIEM, IPS, EDR, Sandboxes, NextGen Firewalls, Web and Email Gateways are defenseless against this threat vector. By deploying deceptions everywhere, we are able to address this difficult threat vector.
LMNTRIX Deceive changes the asymmetry of cyber warfare, by focusing on the weakest link in a targeted attack – the human team behind it. Targeted attacks are orchestrated by human teams. And humans are always vulnerable. Advanced attackers rely on one simple fact – that what they see is real and that the data they collect is reliable. Firewall, Anti-virus, EDR, Sandbox, IDS, and intelligence feed technologies generate so much data that the signal is lost.
Attackers prowling a target network look for juicy content. They browse Active Directory for file servers and explore file shares looking for documents, try default passwords against network devices and web services, and scan for open services across the network.
LMNTRIX Deceive is a cloud-based service running off the LMNTRIX XDR where deceptions are deployed from, alerts reviewed, notifications configured and devices managed from.
LMNTRIX Deceive incorporates 4 types of deceptions. These are Decoys, Breadcrumbs, Tags, and Personas. Each is designed to address a different insider threat and human adversary threat type and together they form a powerful defense.
What is LMNTRIX EDR for OT, and what does it do?
LMNTRIX EDR for OT is a part of LMNTRIX XDR designed to provide advanced security capabilities across an organization’s OT environment. Built on the foundation of the LMNTRIX XDR, the LMNTRIX EDR for OT focuses specifically on endpoint protection, threat detection, and incident response within OT and ICS environments. It is commonly used in cybersecurity applications to safeguard OT infrastructure, monitor for security threats, and facilitate rapid response to potential incidents.
What are the Key Functions of LMNTRIX EDR for OT?
- Endpoint Detection and Response (EDR):
- The LMNTRIX EDR for OT includes NGAV and EDR capabilities, allowing it to monitor, detect, and respond to threats on Windows and Linux endpoints in real-time. It provides visibility into endpoint activities and can detect suspicious behaviors, malicious software, and lateral movement across a network.
- EDR capabilities are bolstered by machine learning models, which can identify anomalies and detect threats like ransomware, malware, and other endpoint attacks.
- Threat Prevention:
- LMNTRIX EDR for OT uses prevention policies to block known threats before they impact systems. This includes malware prevention features that can stop malware and ransomware execution, along with behavioral detection to identify potentially harmful actions that may not be associated with known malware.
- Centralized Management and Configuration:
- The LMNTRIX EDR for OT is managed through LMNTRIX XDR, allowing centralized deployment and configuration across all OT monitored endpoints. This enables administrators to easily roll out updates, change security policies, and monitor agent health from a single interface.
- Data Collection and Analysis:
- Beyond security monitoring, the agent can also collect logs, metrics, and events from endpoints, which are then stored in LMNTRIX XDR for analysis and visualization. This comprehensive data collection supports a wide range of security analytics and observability use cases.
- Intrusion Detection:
- LMNTRIX EDR for OT can act as an intrusion detection system (IDS), monitoring network traffic and system activities for signs of unauthorized access or other indicators of compromise. This includes leveraging MITRE ATT&CK techniques to detect and map potential threats.
- Incident Response:
- The LMNTRIX EDR for OT facilitates automated and manual response actions. Security teams can isolate infected machines, terminate malicious processes, or quarantine suspicious files directly from the Elastic Security platform, helping contain threats quickly.
Does LMNTRIX EDR for OT provide proxy support?
Yes, the LMNTRIX EDR for OT supports connectivity through proxy servers. It can be configured to use proxies such as HTTP Connect (HTTP 1) and SOCKS5 proxies, which are helpful in OT environments where direct internet access is restricted. Proxy settings can be configured in various ways, depending on the deployment method.
What are the benefits of using LMNTRIX EDR for OT?
- Unified Platform: Combines data collection, analysis, and security into a single solution, which streamlines operations and simplifies security infrastructure.
- Scalability: Designed to support environments of varying sizes, from small businesses to large enterprises with distributed networks.
- Advanced Detection: Uses machine learning and behavioral analytics to identify both known and unknown threats, reducing reliance on signature-based detection alone.
- Integration with LMNTRIX XDR: Offers seamless integration with other LMNTRIX XDR components, enabling full IT and OT observability, logging, and performance monitoring alongside security functions.
What are the Use Cases for LMNTRIX EDR for OT?
- Endpoint Protection: Protects OT workstations, servers, and other endpoints from a wide range of threats.
- Security Operations: Provides OT SOC teams with tools for monitoring, investigating, and responding to security incidents.
- Compliance Monitoring: Helps meet compliance requirements by logging OT endpoint activities and storing them securely in LMNTRIX XDR for auditing.
The LMNTRIX EDR for OT offers a comprehensive security solution within the LMNTRIX XDR ecosystem, providing flexible deployment options, powerful detection capabilities, and integrated response tools to secure and monitor endpoint devices in real-time. It’s a key component of LMNTRX’s broader XDR (Extended Detection and Response) strategy.
What is the role of LMNTRIX XDR in LMNTRIX OT?
LMNTRIX XDR is a cloud-based platform that provides LMNTRIX OT with centralized management, monitoring, scalability, automation, analytics and incident management capabilities, allowing users to manage and analyze security data across multiple sites from a single interface.
How does LMNTRIX OT integrate with existing IT and OT security solutions?
LMNTRIX OT integrates with SIEMs, firewalls, ticketing systems, and network management tools to provide a seamless cybersecurity framework for both IT and OT environments.
Does LMNTRIX OT support endpoint security for OT and IoT devices?
Yes, LMNTRIX EDR for OT is focused on Nextgen Antivirus and Endpoint Detection & Response capability to provide endpoint security in OT environments.
How is LMNTRIX OT deployed in an industrial environment?
Deployment of the NDR and Packets sensors are on SPAN/TAP ports behind the OT firewall. EDR agent are deployed on all Windows and Linux machines while Deceptions are deployed on appliances or VMs within an OT environment to represent fake OT assets. All of these on premise solutions are securely managed and monitored by LMNTRIX XDR via an encrypted connection.
Does LMNTRIX OT support remote monitoring?
Yes, with LMNTRIX XDR, users can perform remote monitoring and management across multiple locations, providing real-time insights from any internet-connected device.
What kind of training is required to use LMNTRIX OT?
LMNTRIX OT is delivered with Managed Detection & Response (MDR) however LMNTRIX also offers training to help users understand platform functionalities, manage deployments, and respond to security incidents effectively.
Can LMNTRIX OT scale with my organization’s needs?
Yes, LMNTRIX OT is designed for scalability, with features like distributed architecture and cloud-based management to support organizations of varying sizes.
How does LMNTRIX OT handle firmware updates and software patches?
LMNTRIX provides regular updates for software and threat detection signatures, which can be applied manually or automatically, depending on the deployment configuration.
How does LMNTRIX OT assist with regulatory compliance?
LMNTRIX OT helps organizations meet compliance standards (e.g., NERC CIP, IEC 62443, GDPR) by providing continuous monitoring, asset management, and reporting capabilities.
Does LMNTRIX OT provide vulnerability management?
Yes, LMNTRIX OT includes vulnerability assessment tools that help identify and prioritize vulnerabilities in OT and IoT assets for remediation.
How does LMNTRIX OT protect sensitive data?
LMNTRIX OT uses encryption, role-based access control (RBAC), and secure data storage practices to protect sensitive data within the platform.
What threat intelligence capabilities does LMNTRIX OT offer?
LMNTRIX OT provides integrated threat intelligence with real-time data feeds, enabling users to stay updated on the latest OT and IoT threats and vulnerabilities.
How does LMNTRIX OT support incident response?
The platform enables rapid incident detection, alerting, and automated reporting, allowing security teams to respond swiftly to potential threats.
Can LMNTRIX OT identify and classify assets on the network?
Yes, it includes automated asset discovery and inventory, which helps organizations gain visibility into all OT and IoT devices on their network.
What are LMNTRIX OT’ visualization and reporting capabilities?
LMNTRIX OT offers customizable dashboards, reports, and visualizations to help users monitor network status, view alerts, and analyze security trends.
Does LMNTRIX OT offer API integrations?
Yes, LMNTRIX OT provides API access for integration with other security tools, enabling data sharing and streamlined workflows.
How does LMNTRIX OT handle encrypted traffic?
LMNTRIX OT can monitor encrypted traffic flows for abnormal patterns but requires integration with decryption tools for deep packet inspection.
Can LMNTRIX OT simulate attacks for testing purposes?
While LMNTRIX OT is focused on monitoring and detection, it can support integration with external tools for vulnerability testing and simulation.
Does LMNTRIX OT support predictive analytics?
Yes, it uses machine learning algorithms to identify potential risks and predict future anomalies based on historical data.
How does LMNTRIX OT handle network segmentation?
LMNTRIX OT provides network mapping and traffic analysis to help organizations design and monitor network segmentation policies for improved security.
What is the role of machine learning in LMNTRIX OT?
Machine learning is used for anomaly detection, behavioral analysis, and predictive threat detection, which enhances the platform’s ability to identify new or evolving threats.
What types of notifications or alerts can LMNTRIX OT generate?
LMNTRIX OT supports real-time alerting via email, SMS, and SIEM integrations, and alerts can be customized based on event type, severity, and frequency.
Customer Support & Services
What kind of customer support does LMNTRIX offer?
LMNTRIX provides comprehensive customer support as an integral part of its XDR (Extended Detection and Response) platform, which includes Managed Detection and Response (MDR) services at no additional cost. This ensures that clients receive 24/7 assistance in critical areas such as threat detection, continuous monitoring, incident response (DFIR), threat containment, remediation, and proactive threat hunting.
Key aspects of LMNTRIX customer support include:
- Multi-Channel Access: Support services are accessible via web, email, and phone, accommodating both Standard and Enterprise Support Plans.
- Current Version Support: Assistance is provided for the most recent version of LMNTRIX solutions and the immediately preceding version, ensuring up-to-date support.
- Expert Guidance: The support team may interact directly with a customer’s solution instance to review application data and provide tailored solutions.
- Language Support: Services are offered in English, facilitating clear communication and efficient problem-solving.
- Eligibility: Customers who have purchased LMNTRIX solutions through authorized partners are entitled to full support services, provided they are the original purchasers and have supplied accurate information.
It’s important to note that access to support services is contingent upon compliance with the LMNTRIX Terms of Service, and the support agreements are non-cancelable during the active subscription term. This commitment ensures that customers have uninterrupted support throughout their usage of LMNTRIX products.
Does LMNTRIX offer any training or educational resources?
Yes, LMNTRIX is dedicated to empowering its customers through a variety of training and educational programs designed to enhance cybersecurity knowledge and maximize the effectiveness of their solutions. Key resources include:
- Monthly Community Webinars: Hosted by industry experts, these webinars provide insights into the latest cybersecurity trends, in-depth product overviews, best practices, and live demonstrations. They are an excellent way for customers to stay informed about new features and strategies to enhance their security posture.
- LMNTRIX Training Calendar: An up-to-date schedule of upcoming training classes and workshops is available, covering a wide range of topics from introductory sessions for new users to advanced technical training for experienced administrators.
- Guided Onboarding (GO) Service: This consultative and advisory service is designed to facilitate a smooth implementation of LMNTRIX solutions. The GO service helps customers align the product capabilities with their specific security needs and operational workflows, ensuring they get the most out of their investment.
Additional resources may include detailed documentation, knowledge base articles, and personalized assistance from Technical Account Managers. Customers interested in accessing these educational materials or requiring specific training are encouraged to contact their LMNTRIX representative or visit the customer portal for more information.
How can customers report issues or bugs to LMNTRIX?
Customers experiencing issues or identifying bugs within LMNTRIX products can report them directly to the support team to facilitate prompt resolution. The recommended steps for reporting are:
- Contact Support via Email: Send a detailed description of the issue to the dedicated support email address, such as cdc@lmntrix.com. Ensure the subject line clearly indicates the nature of the problem.
- Provide Comprehensive Details:
- Description: Outline the problem, including the steps taken before the issue occurred.
- Error Messages: Include any error codes or messages that appeared.
- Screenshots and Logs: Attach relevant screenshots or log files to illustrate the issue.
- System Information: Specify details about the affected systems, such as operating system versions, LMNTRIX agent versions, and any recent changes to the environment.
- Gather Endpoint Logs: If the issue is related to a specific endpoint, collecting logs from the affected agent can greatly assist the support team in diagnosing the problem.
- Use Support Portals: If available, submit the issue through LMNTRIX’s support portal or ticketing system, which allows for tracking the progress of the reported problem.
For customers with assigned Technical Account Managers, reaching out directly can provide additional support and expedite the resolution process. In cases where the issue pertains to licensing or account management, contacting the account manager is advised.
By providing detailed and accurate information, customers enable the LMNTRIX support team to address issues more efficiently, leading to quicker resolutions and minimal disruption to their operations.
LMNTRIX Sales
Can I Get A Trial/Demo Version of LMNTRIX?
Yes, you can get a trial version of LMNTRIX.
Request a free demo through our web page: Demo
How much does LMNTRIX cost?
LMNTRIX prices vary according to the number of deployed endpoint agents and network architecture. For more details about the exact pricing, request a quote.
LMNTRIX & MITRE ATT&CK
Does LMNTRIX support the MITRE ATT&CK framework?
Yes, LMNTRIX fully supports the MITRE ATT&CK framework by integrating it into its security platform. The LMNTRIX system utilizes a Dynamic Behavioral Engine that continuously monitors and analyzes the behavior of processes on protected endpoints. This engine doesn’t just look for known threats; it observes how programs behave in real-time to identify potentially malicious activities based on their actions rather than relying solely on signature databases.
By mapping these behavioral indicators to the MITRE ATT&CK framework, LMNTRIX provides a structured and standardized way to understand and classify adversarial techniques and tactics observed within your network. The MITRE ATT&CK framework is a globally recognized knowledge base of cyber adversary behavior, reflecting the various techniques attackers use across different stages of an attack lifecycle.
Integrating this framework into LMNTRIX’s platform offers several benefits:
Enhanced Visibility: Security teams gain deeper insights into the nature of threats by understanding the specific tactics and techniques being employed against them.
Streamlined Analysis: Mapping behaviors to the MITRE framework helps analysts quickly identify and prioritize threats based on known attack patterns.
Improved Response: With clear context provided by the framework, organizations can develop more effective remediation strategies tailored to the specific threats they face.
Knowledge Sharing: Aligning with a common framework facilitates better communication within the security community, allowing organizations to share insights and strategies more effectively.
By supporting the MITRE ATT&CK framework, LMNTRIX empowers organizations to stay ahead of evolving threats through a comprehensive understanding of attacker behaviors and a more strategic approach to cybersecurity.
How can I use the MITRE ATT&CK framework for threat hunting with LMNTRIX?
Leveraging the MITRE ATT&CK framework within the LMNTRIX platform enhances your threat hunting capabilities by providing a systematic method to search for and identify malicious activities. Here’s how you can utilize this integration for effective threat hunting:
- Access Pre-Built Queries: LMNTRIX offers out-of-the-box queries that are specifically designed to detect behaviors associated with various MITRE ATT&CK techniques. These queries can save time and provide immediate insights without the need for extensive configuration.
- Create Custom Queries: If you have specific threats or techniques in mind, you can craft custom queries using elements from the MITRE ATT&CK framework. You can search across your endpoints using:
- MITRE Technique IDs: Unique identifiers assigned to each technique (e.g., T1059 for Command and Scripting Interpreter).
- Technique Names: The official names of techniques as defined in the framework.
- Descriptions and Categories: Keywords or phrases from the technique descriptions or their broader categories (e.g., “Persistence” or “Privilege Escalation”).
- Metadata: Additional information such as associated software, groups, or mitigation strategies.
- Comprehensive Endpoint Search: With these queries, you can scan your entire network of endpoints to uncover any signs of the specified techniques being employed. This is particularly useful for identifying:
- Unknown Threats: Detecting malicious activities that may not trigger traditional alerts but match known adversary behaviors.
- Advanced Persistent Threats (APTs): Uncovering sophisticated attacks that use stealthy methods documented in the MITRE ATT&CK framework.
- Policy Violations: Identifying unauthorized use of tools or commands that could indicate insider threats or policy breaches.
- Proactive Defense: By continuously hunting for behaviors outlined in the MITRE ATT&CK framework, you can proactively detect and mitigate threats before they materialize into significant security incidents.
- Incident Response Enhancement: When an alert is generated, the mapping to the MITRE ATT&CK framework provides immediate context about the potential severity and nature of the threat, allowing for a faster and more effective response.
- Reporting and Analysis: Utilize the insights gained from these queries to generate reports that inform your security posture, highlight trends, and guide future investments in cybersecurity measures.
By integrating the MITRE ATT&CK framework into your threat hunting processes with LMNTRIX, you enhance your ability to detect and respond to threats in a structured and intelligence-driven manner. This approach not only improves your current security operations but also contributes to a more resilient and informed cybersecurity strategy overall.
How Does LMNTRIX Respond to Ransomware?
How does LMNTRIX respond to ransomware?
LMNTRIX employs a comprehensive and multi-layered strategy to defend against ransomware attacks, ensuring both immediate threat neutralization and system recovery. The key response mechanisms include:
- Ransomware Reversal Sensor: Ransomware Reversal Sensor is an add-on endpoint agent that can help you recover from a ransomware attack quickly and efficiently. Our patented Session Key Intercept (SKI) technology detects ransomware encryption in real-time and immediately captures the encryption keys. The solution works against virtually all ransomware sight unseen. This allows for rapid, reliable, and economical data recovery. Our ransomware reversal sensor is sold as a separate solution ideal for risk averse enterprises with high value or critical systems.
- Automatic Termination of Malicious Processes: The platform actively monitors for suspicious activities associated with ransomware. Upon detection, it can swiftly terminate the offending processes to prevent the encryption of files and further spread of the malware.
- Quarantine of Malicious Files and Scripts: Suspected ransomware files and scripts are isolated in a secure quarantine environment. This prevents them from executing or causing harm, allowing security teams to analyze and decide on appropriate actions without risk to the network.
- Network Isolation of Compromised Devices: LMNTRIX allows for both automatic and manual isolation of infected endpoints from the network. This containment strategy halts the lateral movement of ransomware, protecting other devices within the organization. Importantly, administrators retain the ability to interact with the isolated endpoint via the management console or through LMNTRIX’s RESTful API, facilitating ongoing remediation efforts.
By integrating these response options, LMNTRIX not only stops ransomware attacks in progress but also provides tools to reverse their effects, ensuring business continuity and data integrity.
Is ransomware still a threat?
Yes, ransomware continues to be a significant and evolving threat in the cybersecurity landscape. Cybercriminals are constantly developing new ransomware variants and sophisticated delivery methods to exploit vulnerabilities. According to the 2020 Verizon Data Breach Investigations Report (DBIR), ransomware was involved in over a quarter of malware-related data breaches, highlighting its prevalence and the substantial risk it poses to organizations worldwide. The financial and operational damages caused by ransomware—including data loss, downtime, and reputational harm—underscore the necessity for robust protective measures.
Will LMNTRIX protect me against ransomware?
Absolutely. LMNTRIX is specifically engineered to safeguard enterprises against ransomware and a wide array of malware threats. The platform employs advanced behavioral analysis to detect the distinctive activities of ransomware, such as unauthorized file modifications and rapid encryption processes. By recognizing these behaviors early, LMNTRIX can intervene before the ransomware inflicts significant damage.
In scenarios where ransomware does manage to encrypt files, our Ransomware Reversal Sensor is a simple software system that, if deployed before an attack, provides an incremental protective layer.
Will I be able to restore files encrypted by ransomware?
Yes, you will. If you have deployed our Ransomware Reversal Sensor across all your endpoints. The sensor can reliably and silently intercept the cryptographic keys used at the moment of attack. With the keys available, decryption without paying ransoms is not only possible but simple and straightforward. LMNTRIX provides high-speed, enterprise-grade software decryptors that use the keys and restore the data to the moment before the attack.
Ransomware reversal is 3rd party validated and proven to work on virtually all modern ransomware, sight unseen. The solution compliments and does not overlap with existing security and backup solutions and strategies. Implementing and operating is trivial, extremely affordable, and comes with performance guarantees.
LMNTRIX Integrations
Does LMNTRIX integrate with other endpoint software?
Yes, LMNTRIX is designed to seamlessly integrate and interoperate with a variety of endpoint security solutions. Recognizing that organizations often have existing security infrastructures, LMNTRIX focuses on enhancing interoperability to complement and enhance your current setup. While LMNTRIX offers a comprehensive solution that can function as a complete antivirus (AV) replacement and combines Endpoint Protection Platform (EPP) and Endpoint Detection and Response (EDR) capabilities, it also understands the importance of flexibility in modern enterprise environments.
One of the core philosophies of LMNTRIX is to reduce complexity by minimizing the number of agents required on endpoints. Many organizations are burdened with multiple agents from different vendors, which can lead to performance issues and management challenges. LMNTRIX addresses this by providing extensive features within a single agent, allowing you to potentially phase out legacy antivirus solutions if desired. However, if you prefer to maintain certain existing tools, LMNTRIX can integrate with them to create a unified and more efficient security ecosystem.
By integrating with other endpoint software, LMNTRIX enhances your organization’s ability to detect, prevent, and respond to threats across all devices, ensuring comprehensive protection without unnecessary overhead.
Which integrations does the LMNTRIX XDR Platform offer?
The LMNTRIX Extended Detection and Response (XDR) Platform offers a wide range of integrations designed to extend its capabilities and provide a holistic security solution. These integrations enable organizations to unify prevention, detection, and response efforts across various attack surfaces and security domains.
Key integrations include:
- Security Controls: LMNTRIX XDR integrates with your existing security controls to automate the containment process. These controls include:
- NextGen firewalls such as Palo Alto Networks firewalls
- Cloud firewalls from AWS, Azure and GCP
- Web security solutions such as Zscaler
- Email security solutions such as Mimecast
- DNS security solutions such as Infoblox
- Data and Log Collection: Collect and integrate data from a myriad of sources including applications and infrastructure through our versatile tools such as LMNTRIX Agent, web crawler, and various connectors. Utilize our advanced schema, which supports flexibility in data collection, storage, and visualization, allowing for the parsing, enrichment, and safeguarding of your data to extract insights swiftly.
- OT/IoT Solutions: By seamlessly interfacing with a wide range of devices, protocols, and systems (SCADA, DCS, PLCs, Smart Sensors, Actuators, BMS), LMNTRIX XDR provides unparalleled visibility and control over complex networks, enabling proactive defense against cyber threats and enhancing operational resilience.
- Security Information and Event Management (SIEM) Systems: LMNTRIX integrates with popular SIEM platforms like Splunk, IBM Security QRadar, LMNTRIX, and others. This allows for centralized logging, correlation, and analysis of security events from multiple sources, enhancing visibility and incident response capabilities.
- Threat Intelligence Feeds: By integrating with leading threat intelligence providers, LMNTRIX enriches its detection capabilities with real-time data on emerging threats, vulnerabilities, and indicators of compromise (IOCs).
- Malware Sandboxing Solutions: LMNTRIX can work alongside sandboxing technologies to analyze suspicious files and executables in a secure environment, improving the detection of advanced malware and zero-day exploits.
- Cloud Access Security Brokers (CASBs): Integration with CASB solutions helps extend security policies to cloud services, ensuring consistent protection for cloud-based applications and data.
- Endpoint Management and IT Service Management (ITSM) Platforms: Integrations with tools like ServiceNow enable streamlined workflows, automated ticketing, and efficient incident management.
These integrations are facilitated through APIs and are often available as pre-built connectors or applications within LMNTRIX’s integration ecosystem. This ecosystem serves as a centralized hub where organizations can discover, deploy, and manage integrations to tailor the XDR platform to their specific needs.
By offering these integrations, LMNTRIX ensures that its XDR Platform can function as a central component of your security infrastructure, enhancing coordination between different tools and providing a unified approach to cybersecurity.
Visit our Integrations Page for more details: https://lmntrix.com/integration/
Does LMNTRIX integrate with my SIEM?
Yes, LMNTRIX is designed to integrate effectively with your Security Information and Event Management (SIEM) system. Integrating LMNTRIX with your SIEM enhances your organization’s ability to monitor, analyze, and respond to security events by consolidating data from multiple sources into a single platform.
Key aspects of the integration include:
- Data Feeds: LMNTRIX can send security event data to your SIEM via standard protocols such as Syslog or through APIs. This includes information on detected threats, endpoint activities, user behaviors, and more.
- Correlation and Analysis: By incorporating LMNTRIX data into your SIEM, you can leverage advanced analytics to identify patterns, correlate events across different systems, and gain deeper insights into potential security incidents.
- Customizable Dashboards and Reports: Integration enables the creation of tailored dashboards and reports within your SIEM that include LMNTRIX data, providing a comprehensive view of your security posture.
- Automated Responses: The combined capabilities allow for automated responses to certain threats, such as isolating endpoints or triggering alerts based on LMNTRIX detections.
LMNTRIX provides support and documentation for integrating with popular SIEM solutions, including but not limited to:
- Splunk
- IBM Security QRadar
- AT&T USM Anywhere
- LogRhythm
- Elastic
For detailed guidance on integrating LMNTRIX with your specific SIEM platform, you can refer to the integration resources provided by LMNTRIX or contact their support team for assistance. This integration empowers your security operations center (SOC) with enhanced visibility and efficiency in threat detection and incident response.
What is the LMNTRIX API?
The LMNTRIX Application Programming Interface (API) is a comprehensive set of tools that allows developers and security professionals to interact programmatically with the LMNTRIX platform. Embracing an “API-first” philosophy, LMNTRIX prioritizes the development of APIs to ensure that nearly all platform functionalities accessible via the user interface (UI) are also available through APIs.
Key features of the LMNTRIX API include:
- Extensive Functionality: With over 300 API functions, users can perform a wide range of actions, such as querying security events, managing endpoint policies, initiating scans, retrieving reports, and more.
- Automation and Integration: The API enables organizations to automate routine tasks, integrate LMNTRIX capabilities into existing workflows, and build custom solutions that enhance operational efficiency.
- Two-Way Communication: The API supports both retrieval of data from the LMNTRIX platform and the ability to send commands or configurations to it, facilitating seamless interaction and control.
- Well-Documented Resources: LMNTRIX provides thorough documentation, including interactive references using tools like Swagger (OpenAPI). This makes it easier for developers to understand API endpoints, parameters, and expected responses.
- Security: The API employs robust authentication and authorization mechanisms to ensure secure access and protect sensitive data.
By offering a powerful and flexible API, LMNTRIX allows organizations to tailor the platform to their specific needs, integrate with other security tools, and enhance their overall cybersecurity strategy through automation and customization.
Which type of API does LMNTRIX use?
LMNTRIX utilizes a RESTful API architecture, which is widely adopted for its simplicity, scalability, and compatibility with web technologies. RESTful APIs (Representational State Transfer) use standard HTTP methods such as GET, POST, PUT, and DELETE, making them easy to work with and integrate into various applications and systems.
Key characteristics of the LMNTRIX RESTful API include:
- Resource-Oriented Endpoints: Each API endpoint corresponds to a specific resource or action within the LMNTRIX platform, such as endpoints, alerts, policies, or reports.
- Stateless Communication: Each API call contains all the necessary information for the server to process the request, ensuring efficient and independent interactions.
- Use of Standard Data Formats: The API typically uses JSON for request and response payloads, which is easy to parse and widely supported across programming languages.
- Comprehensive Coverage: With over 300 functions, the API provides extensive coverage of the platform’s capabilities, allowing for deep integration and automation.
- Interactive Documentation: Through tools like Swagger (OpenAPI), LMNTRIX offers interactive API documentation that allows developers to test endpoints directly within the documentation interface, enhancing understanding and speeding up development.
By adopting a RESTful API, LMNTRIX ensures that its API is accessible and usable by developers with varying levels of experience, facilitating integration with a wide array of applications and systems in the cybersecurity ecosystem.


