Detect and contain cyber threats in minutes , not days.
ONE PLATFORM,ALL OUT PROTECTION
Be the Hunter, Not the Prey.
The nature of threats and approaches used by adversaries have changed radically, but the solutions used by enterprises have not. Stop fixating on the perimeter and start looking at your network more like an obstacle course where hackers could be deceived, worn down, paralyzed and ultimately thwarted. You protect what matters; they go away empty handed. This is about changing the economics of hacking. Make the cost of the hack impossible for the hackers to justify and you win. Shift your security mindset from "incident response" to "continuous response.” You start by assuming systems are already compromised and require continuous monitoring and remediation.

XDR
Unify-native endpoint, network, mobile, cloud, intelligence, deceptions and identity telemetry with any open, third party data from your security ecosystem into one powerful platform.

MDR
Enlists our in-house experts to validate, investigate, contain & remediate every XDR-identified threat that puts your network and reputation at risk, so you can refocus attention and resources on the strategy behind your program.

SOCaaS
TRUSTED BY CUSTOMERS AROUND THE WORLD



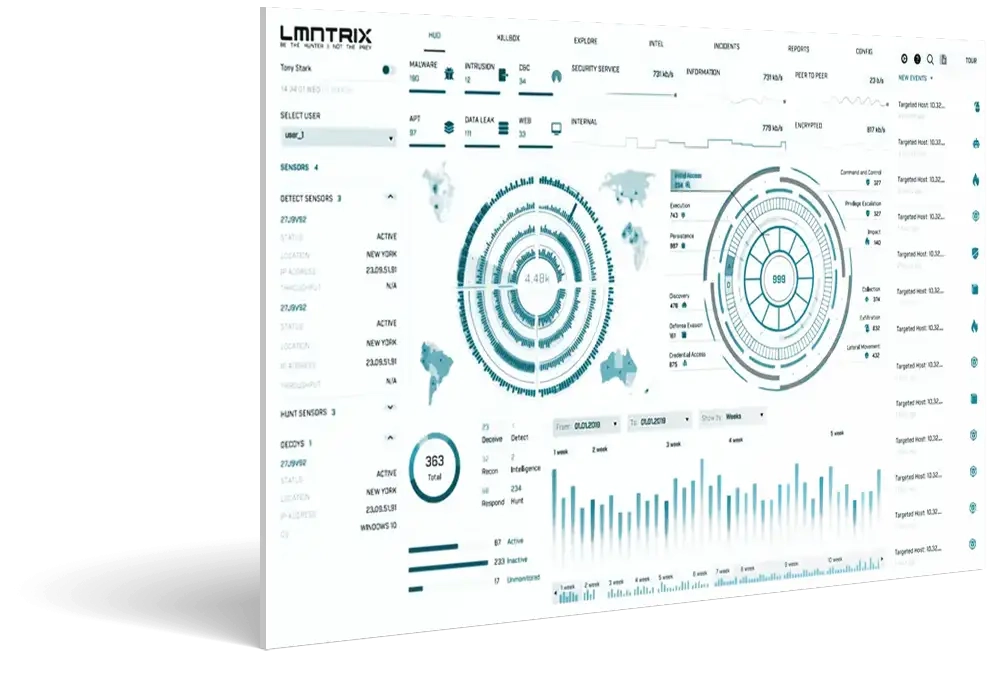
The Next Frontier for Detection and Response
XDR unlike any other
Fortify. Automate. Supercharge. Extend protection from the endpoint to the cloud with complete visibility, military-grade protection, and automated response. Discover the power of hyper-converged LMNTRIX XDR.
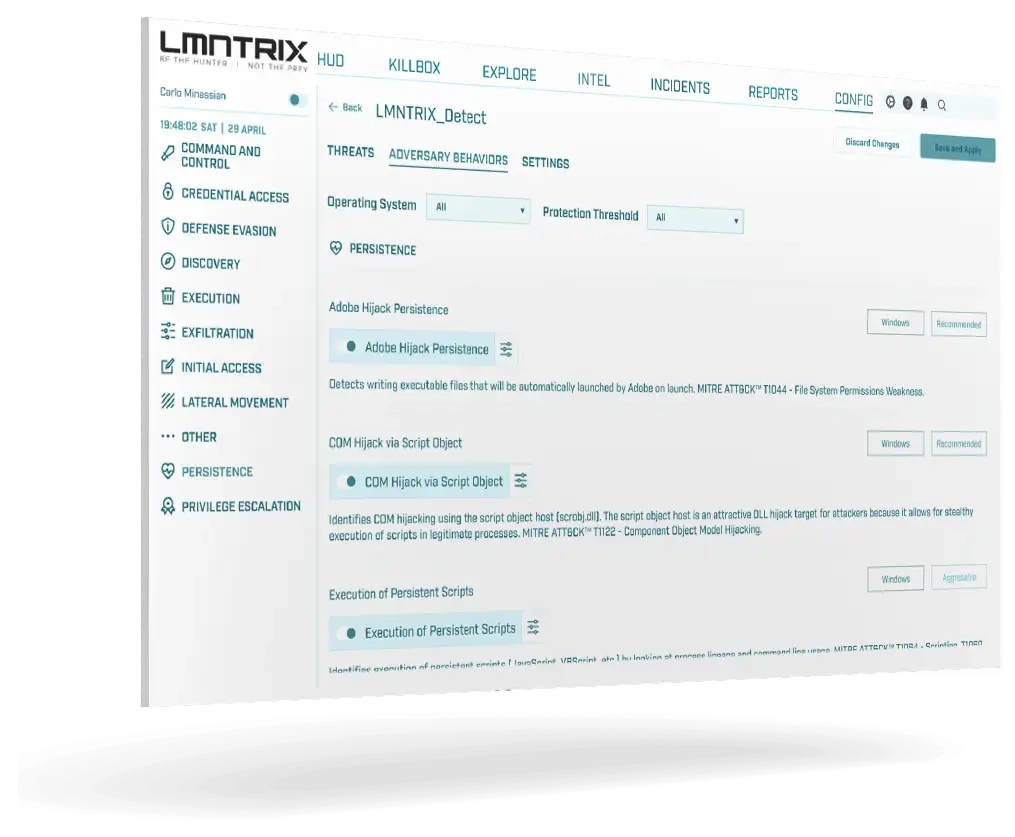

Extended
Natively unify Machine and Underground Intelligence, NGAV, EDR, NDR, Network Forensics, Cloud Security, Mobile Threat Defense, Security Analytics, Identity protection, with Deceptions Everywhere.
Detection
Detect threats missed by existing security controls, and turn previously siloed data into high-fidelity, cross-domain attack indicators, insights and alerts to surface the most sophisticated threats.
Response
Turn XDR incidents into action. Automate integrated response actions across the LMNTRIX XDR platform and 3rd party security products to shutdown the most advanced attacks from endpoint to cloud - all from a single console.
Forensics
Identify the root cause of threats to prevent future incidents.
Superior Detection - Unmatched Response - Open Without Compromise
Under the hood of yourManaged XDR

NGAV+EDR
Endpoint technology that focuses on detecting and responding to security threats on devices such as desktops, laptops and servers. Uses advanced analytics and machine learning algorithms to analyze endpoint device activity and identify potential security threats.

NDR
Advanced analytics and machine learning algorithms to analyze network traffic and identify abnormal behavior or patterns that may indicate a security threat.
Cloud

Deceptions
Also known as Moving Target Defense, it involves continuously changing or randomizing the system or network's attack surface, such as by changing IP addresses, ports, software configurations, or other system parameters with the use of decoys, breadcrumbs and traps.

Intelligence

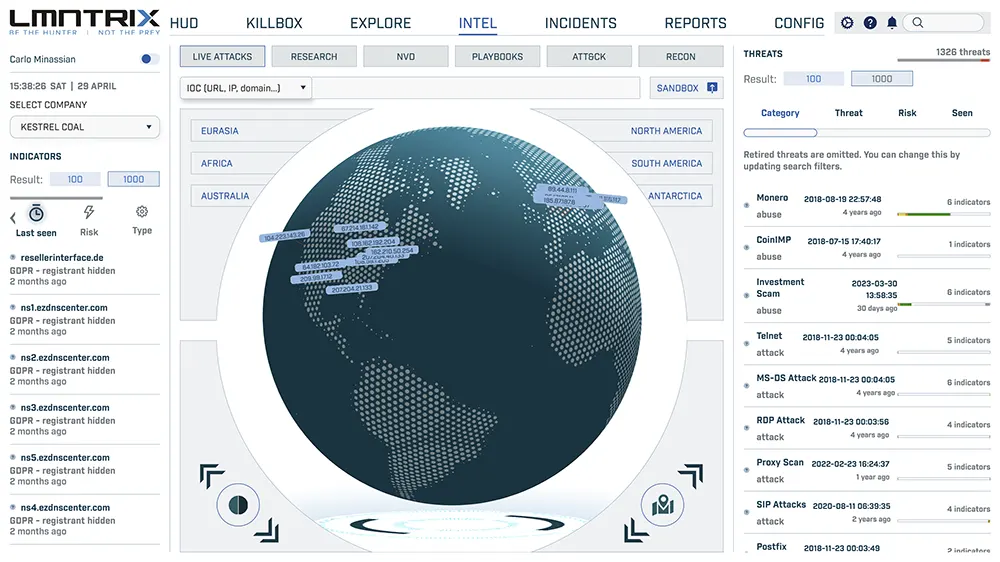
SIEM

Recon
Managed Detection and Response (MDR)
Stop attacks 24/7 with continuous monitoring, proactive threat hunting, alert triage, investigation and response built on LMNTRIX XDR.
24/7 Monitoring and Response
Surgical Remediation
Unlimited DFIR
Proactive Threat Hunting
Leverage our proprietary Hunt Cycle - Survey, Secure, Detect, Respond to shine a light into the darkest corners, leaving adversaries with nowhere to hide.
Reduce TCO with Instant ROI
5 x Faster MTTD & MTTR
1
Detect < 1 Min
5
Investigate < 5 mins
30
Remediate<30 Mins
Every Second Counts
Reverse the adversary advantage with laser-accurate detection and lightning-fast investigation and response
- 1
Deploy
- 2
Detect
- 3
Investigate
- 4
Remediate
- 5
Report
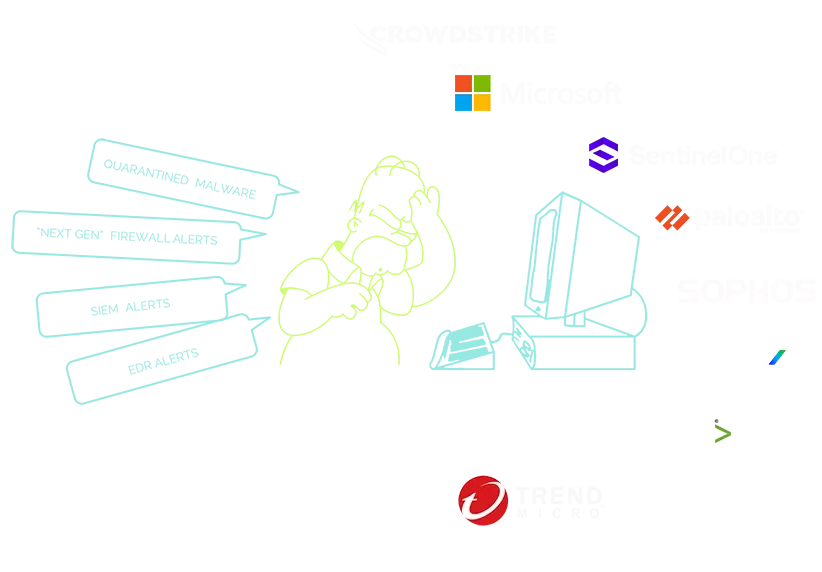
SIEM just doesn’t cut it anymore.
Here’sWhy...
Let’s talk about the elephant in the room. Raise your hand if you’ve been let down by your SIEM. Wow. That’s a lot of hands.
LMNTRIX has reimagined cybersecurity, turning the tables in favor of the defenders once again. We have cut out the bloat of Stupidly Irrelevant Electronic Messaging (SIEM) alerts and log analysis, creating new methods for confounding even the most advanced attackers.
Endless False Positives
Endless Alert Fatigue
Endless Cost
The Game Changer
You’re ready for advanced protection
and that means XDR
- Endpoint Security (LMNTRIX EDR)
- Network Security (LMNTRIX NDR)
- Mobile Security (LMNTRIX MOBILE)
- IoT & OT Security (LMNTRIX OT)
- Identity Protection (LMNTRIX IDENTITY)
- Network Forensics (LMNTRIX PACKETS)
- Moving Target Defense (LMNTRIX DECEIVE)
- Underground Intelligence (LMNTRIX RECON)
- SIEM & Security Analytics (LMNTRIX SIEM)
- SIEM Rules
- Incident Management
- ML-Driven Threat Detection
- Proactive Threat Hunting
- Automated Root Cause Analysis
- Flexible Response
- Integrated Threat Intelligence
- Integrated Policy Management
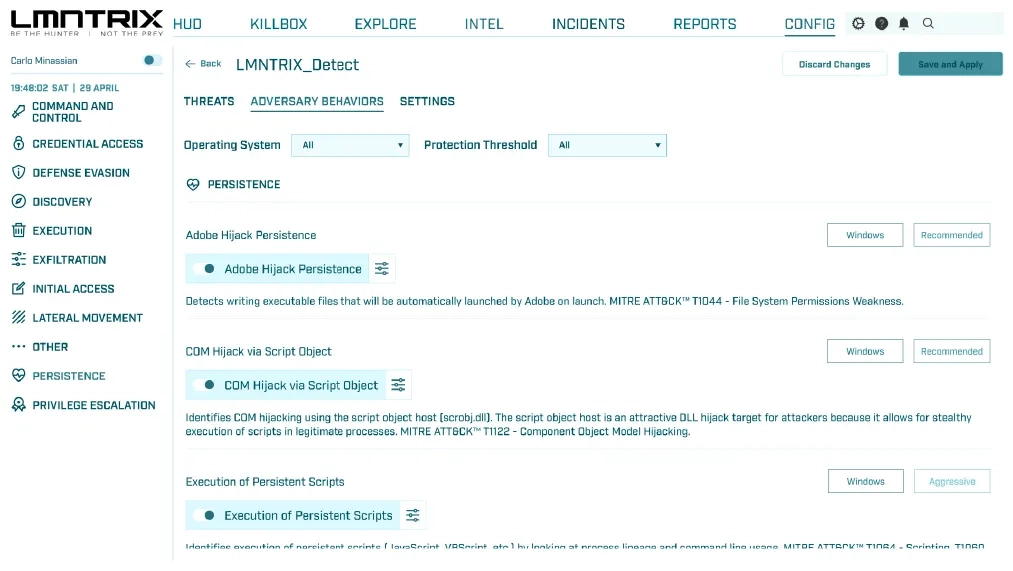
Endpoint Security (LMNTRIX EDR)
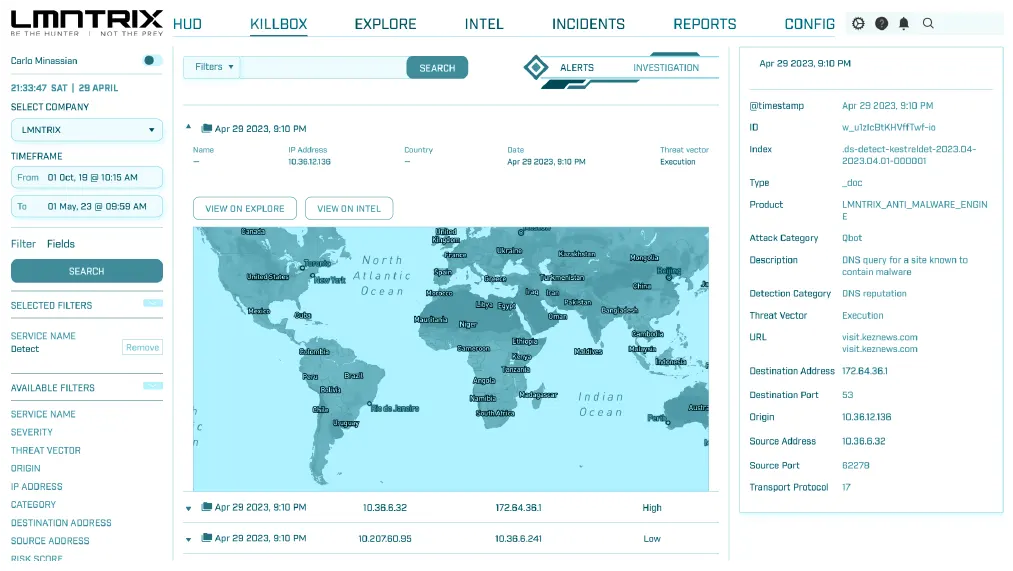
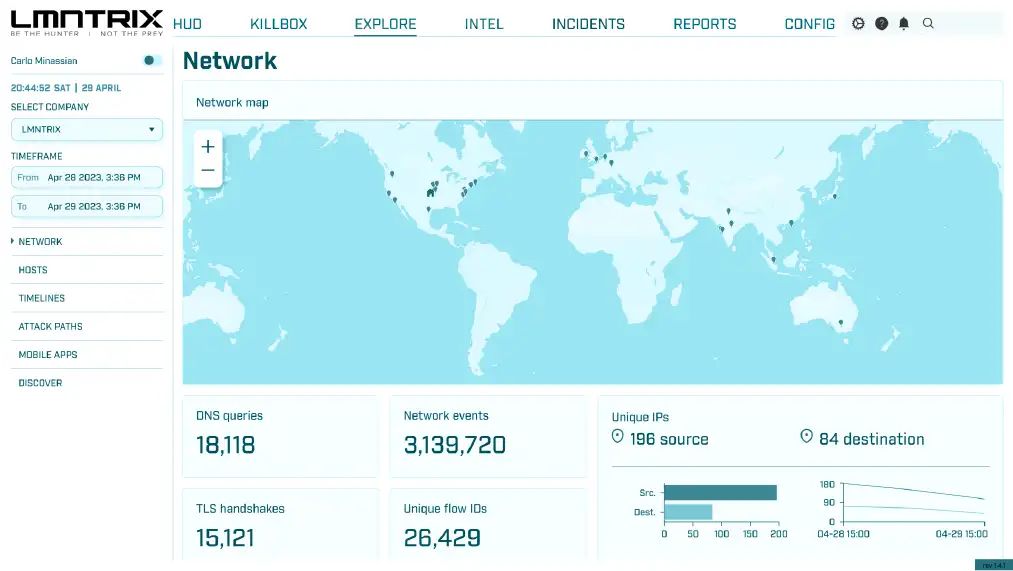
Network Security (LMNTRIX NDR)
Our NDR technology combines machine learning and behavioral analytics to identify and respond to even the most elusive threats in real-time. With comprehensive visibility into network traffic, you can proactively detect and stop attacks before they cause damage, ensuring the security and continuity of your business operations.
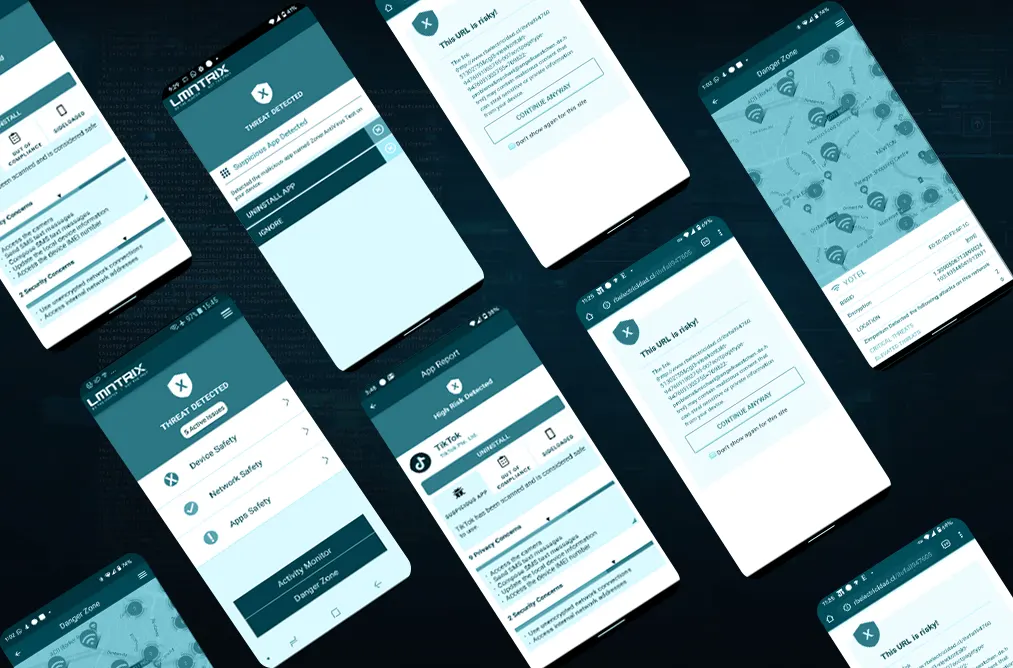
Mobile Security (LMNTRIX MOBILE)
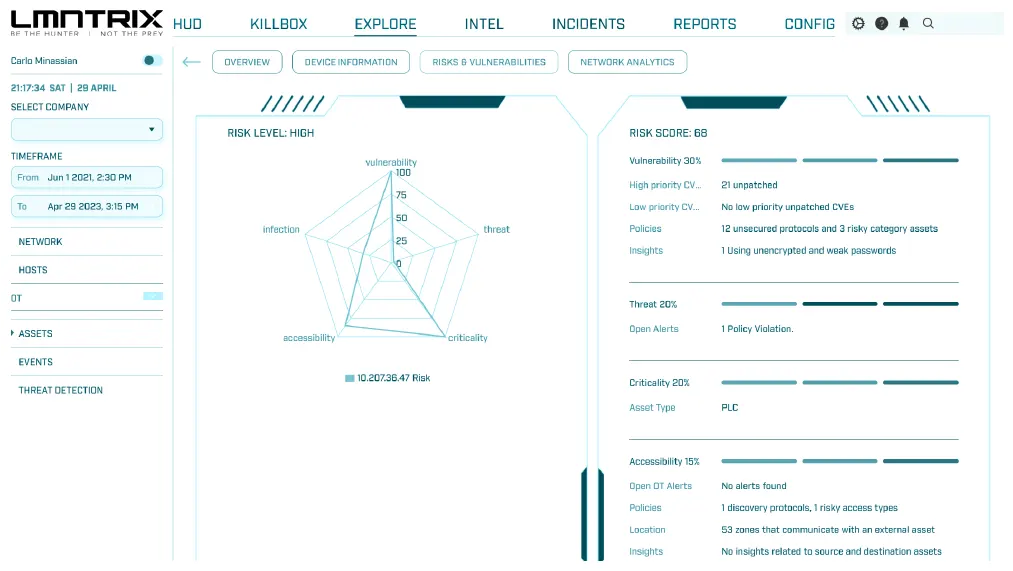
IoT and OT Security (LMNTRIX OT)
Identity Protection (LMNTRIX IDENTITY)
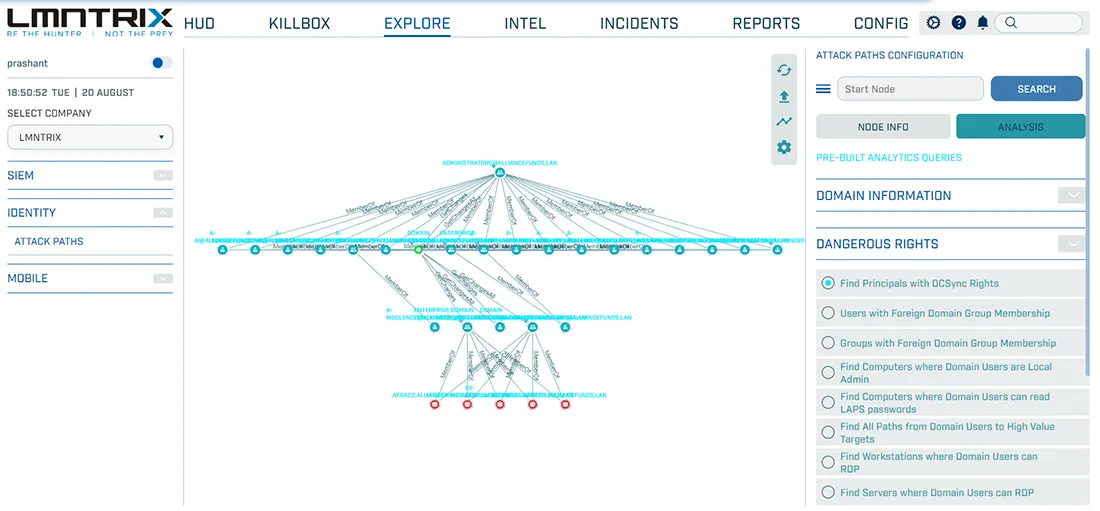
Network Forensics (LMNTRIX PACKETS)
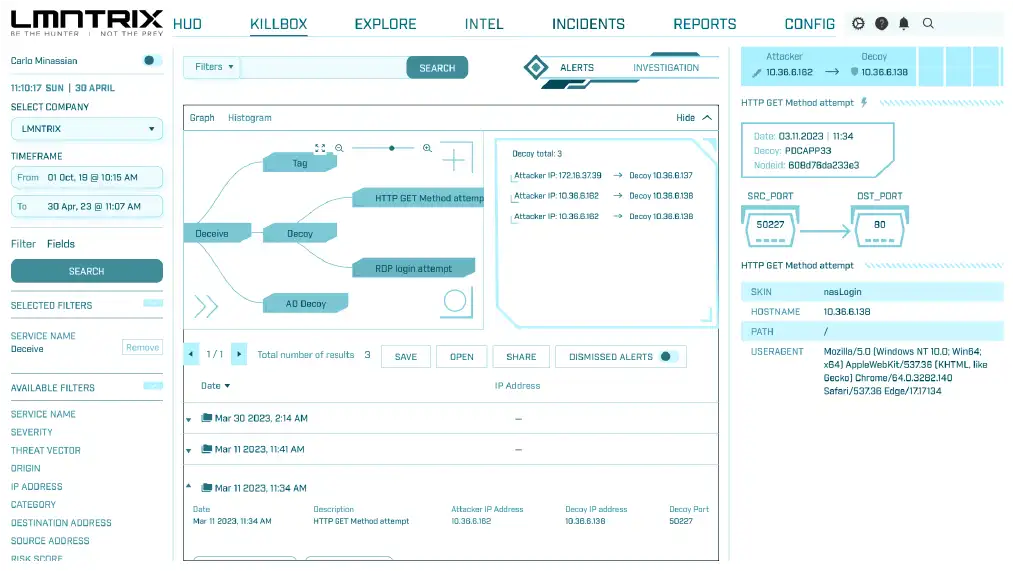
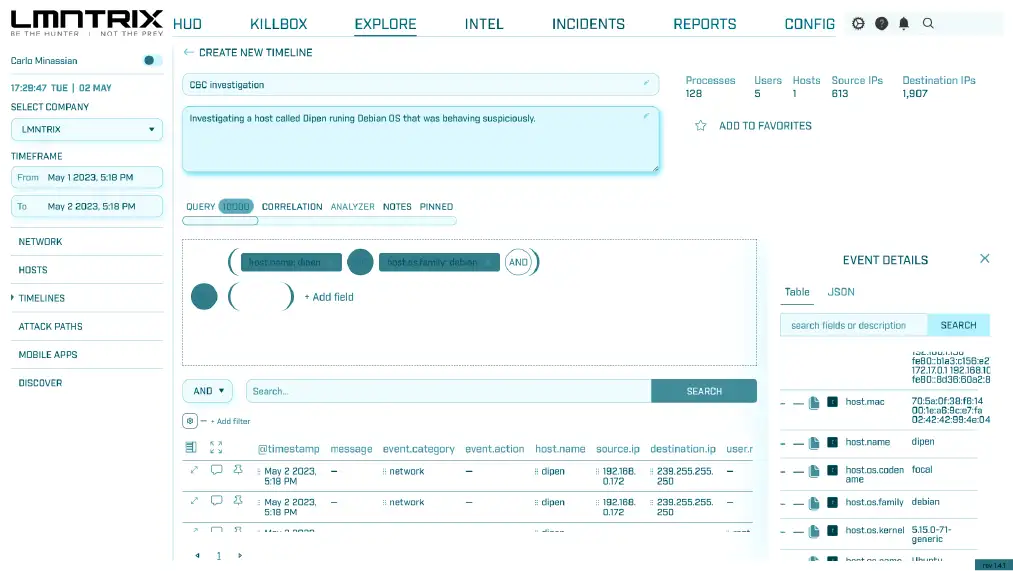
Moving Target Defense (LMNTRIX DECEIVE)
Continuously change or randomizing the system or network's attack surface, such as by changing IP addresses, ports, software configurations, or other system parameters with the use of decoys, breadcrumbs and traps.
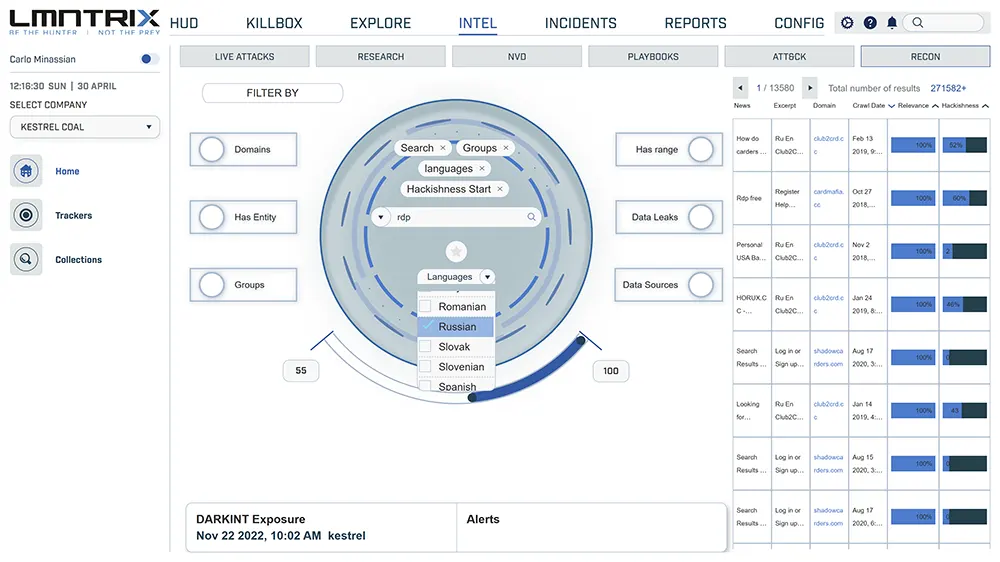
Underground Intelligence (LMNTRIX RECON)
Shine a light on the deep and dark web by using our intelligence, knowledge and proprietary techniques to your advantage.
SIEM & Security Analytics (LMNTRIX SIEM)
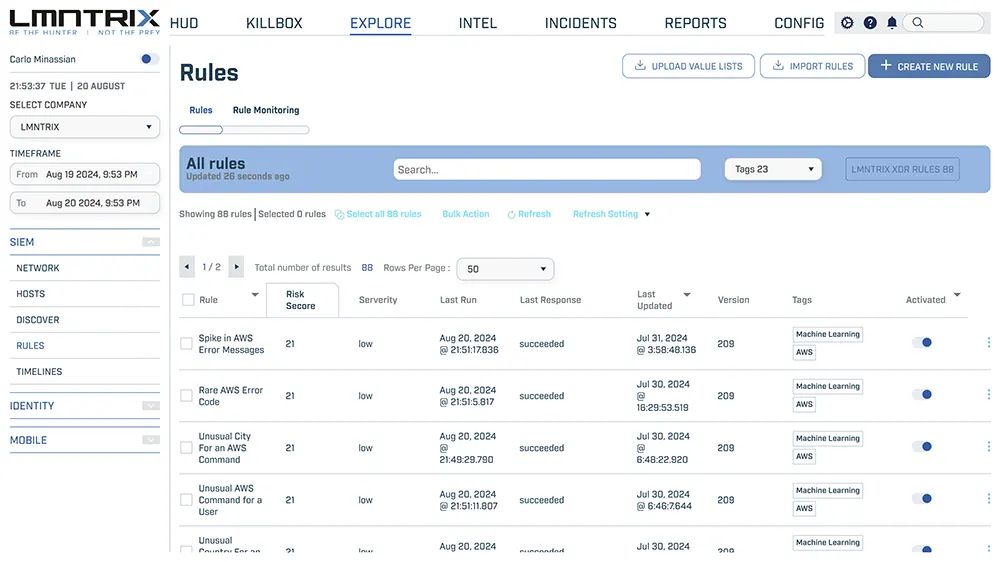
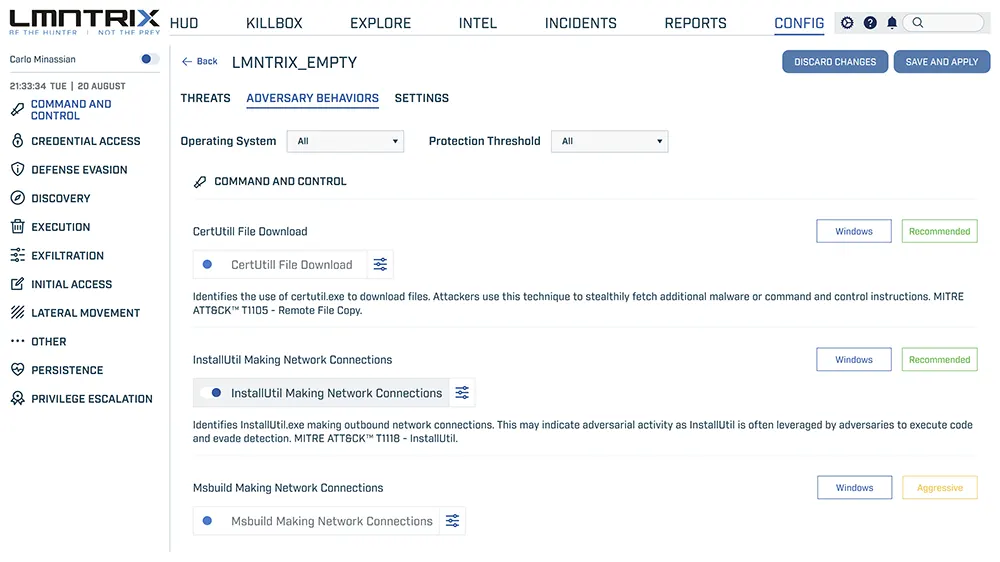
SIEM Rules
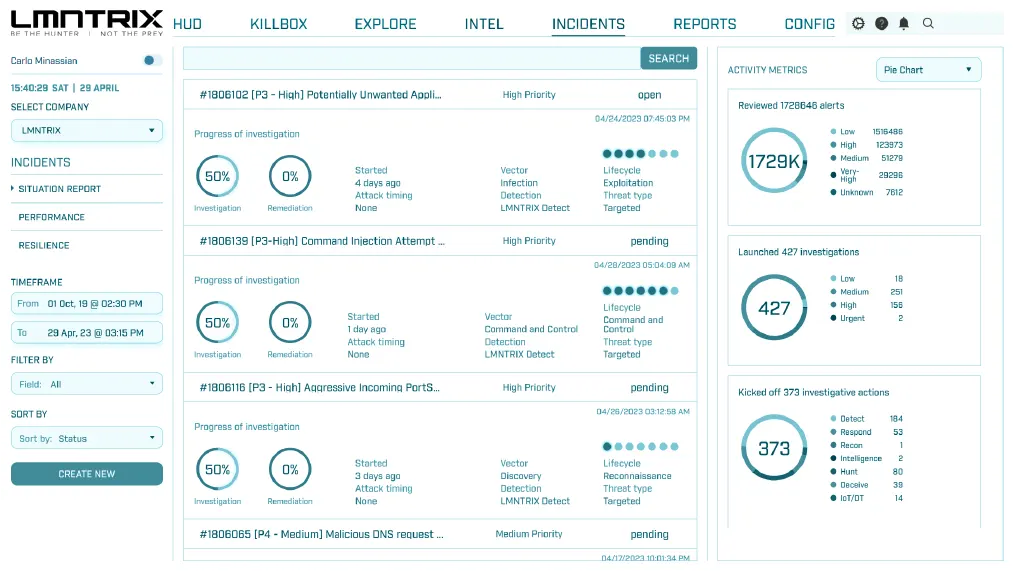
Incident Management
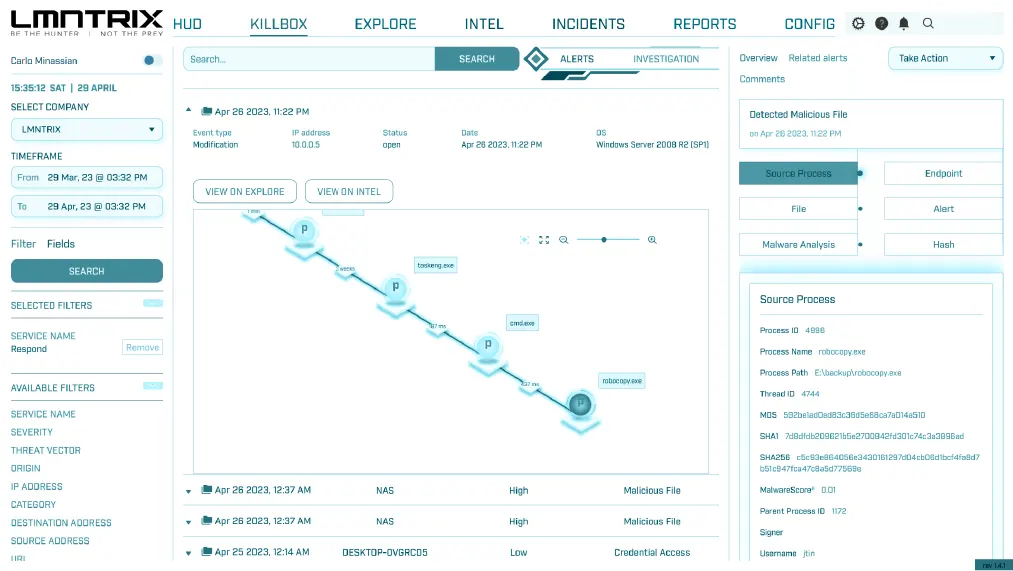
ML-Driven Threat Detection
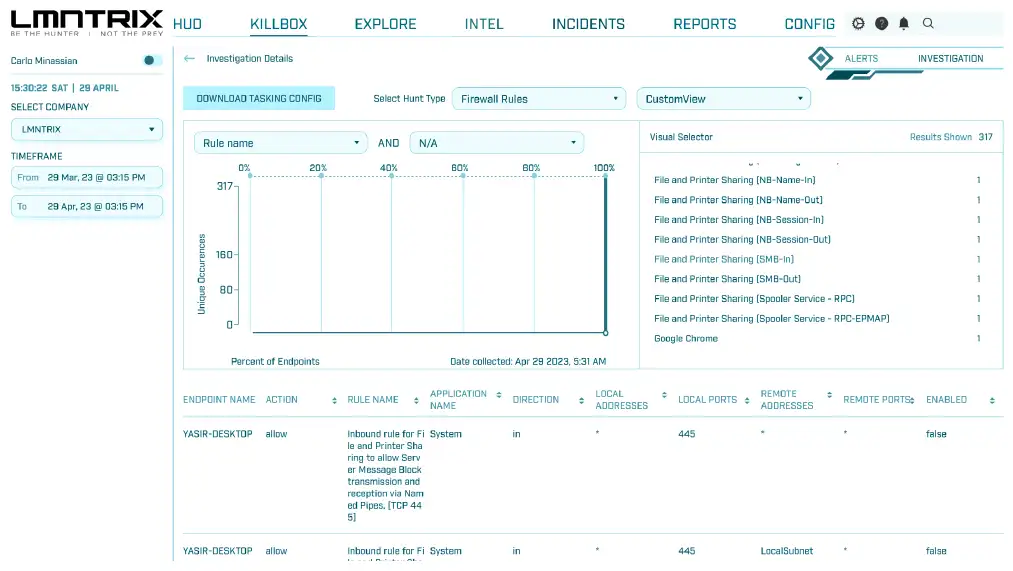
Proactive Threat Hunting
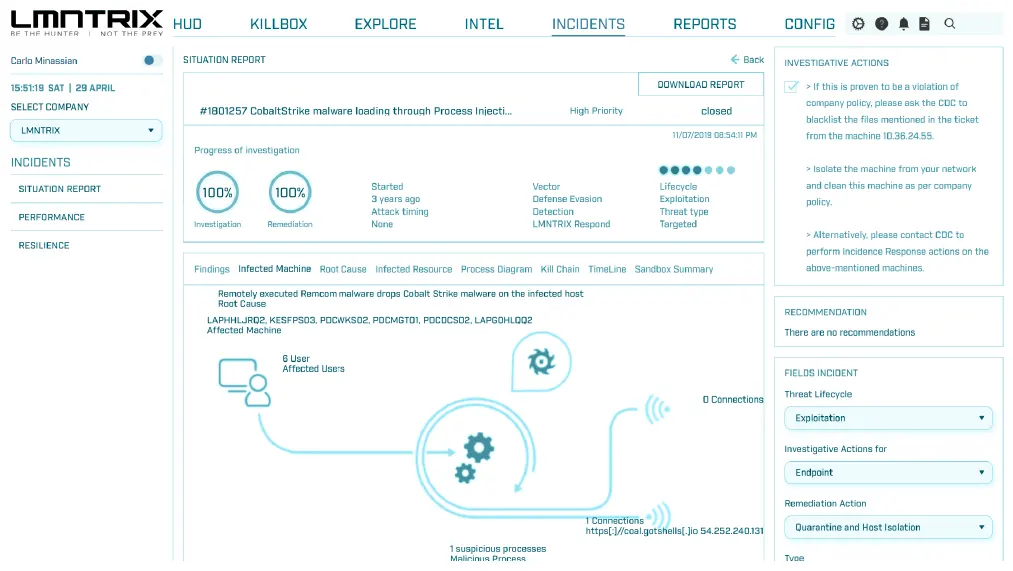
Automated Root Cause Analysis
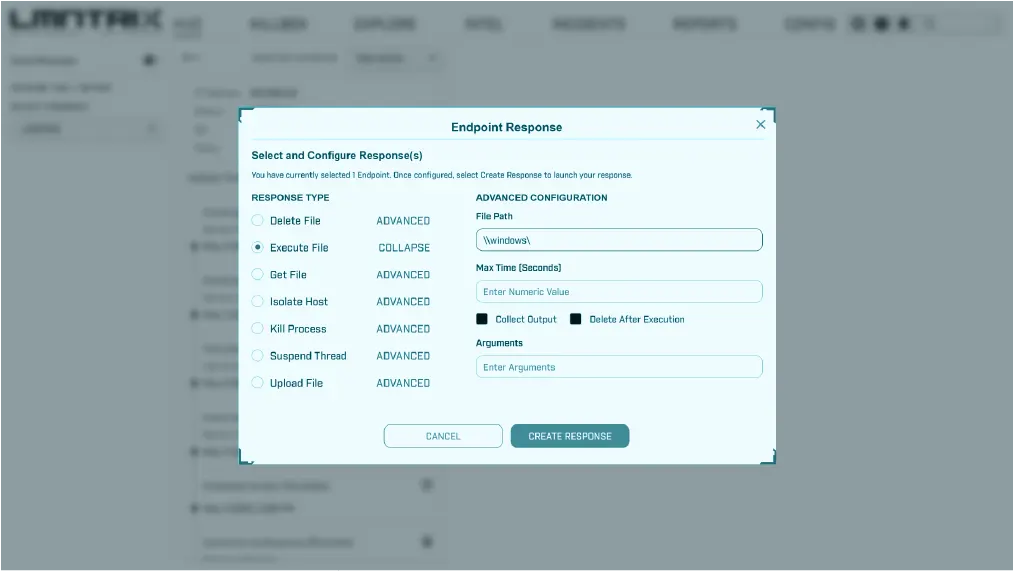
Flexible Response
Integrated Threat Intelligence (LMNTRIX INTELLIGENCE)
Integrated Policy Management
Level Up with
Layers of Expertise
CYBER DEFENCE CENTER MANAGER

Comprehensive Threat
Prevention, Detection and Response
LMNTRIX XDR
Block endpoint, network, cloud and mobile attacks with a proven, lightweight next-gen agent, network sensors and APIs
NGAV, EDR, Mobile Threat Defense, Identity
NDR + Network Forensics + SIEM
Machine & Underground Intelligence
Full Visibility & ML-Driven Detection
Find stealthy threats with the solution that achieved the best combined MITRE ATT&CK detection & protection scores
Machine Learning and Analytics
Rogue Device Discovery & Asset Management
Vulnerability Assessment
Accelerated Investigations
Quickly analyze attacks by grouping alerts into incidents and viewing rich investigate context
Incident Management
Root Cause Analysis & Cross-Data Insights
Live Terminal for Direct Endpoint Access
Active Threat Hunting
Swiftly contain fast moving threats across key enforcement points
Search and Destroy
Script Execution
File Block, Quarantine, Removal, Device Isolation
Automatic Containment Across Network & Cloud
LMNTRIX is compatible with
The cybersecurity tools you already have
We detect far more threat vectors because we cover more tech. LMNTRIX is compatible with a growing list of security telemetry providers such as those below, and many others. We can provide the technology you need from our award-winning portfolio, or our XDR can leverage your existing cybersecurity technologies to detect and respond to threats. Telemetry is automatically consolidated, correlated, and prioritized with insights from the LMNTRIX tech stack and the LMNTRIX Threat Intelligence.



How We Protect
small and large enterprises
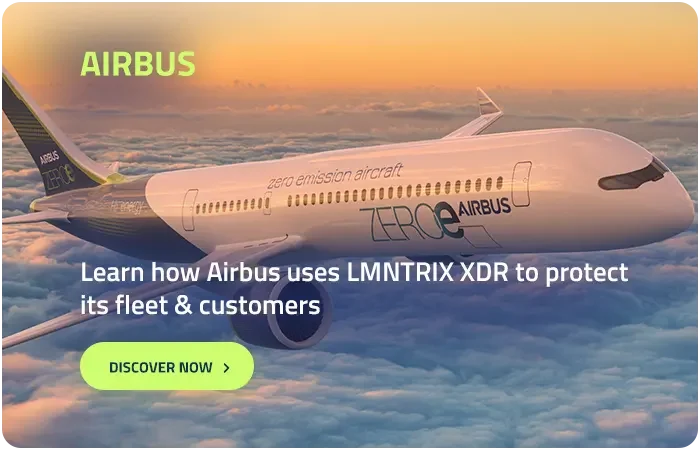
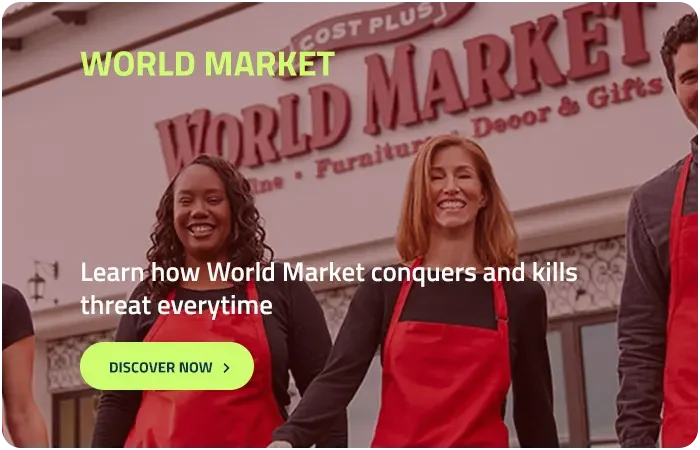
Why clients love working with LMNTRIX
You’re ready for advanced protection
and that means XDR







Don't just take our word for it...

Leader

Leader

Open Source Excellence

Top 250 MSSP Companies In The World

Users Choice Award
Top Rated Security