Introduction
Disclaimer: LMNTRIX neither supports nor condones illegal acts of hacking and/or cyber war-like campaigns in any form. As a cyber defense company, we refuse to take sides with Russia or, Ukraine, LMNTRIX, and researchers in our Cyber Defense Centers strictly adhere to the morals, ethics, and true spirit of freedom, where we live and let others live in peace. These views are strictly personal, and they do NOT represent LMNTRIX as a company.
We are sure that the recent crisis in Ukraine has caught the world’s attention. What we see in war-like situations is often not the real picture. Your eyes and ears can deceive you in war. To apply a little scepticism to what you read in newspapers or watch on TV is a wise approach.
What people are seeing is the war between Russian and Ukrainian soldiers, what’s lesser-known is the scale of hybrid warfare. A term coined by NATO to describe the combination of kinetic and information warfare. The reality that is unfolding is a potent mix of kinetic attacks with arms and ammo, used in combination with cyber attacks, and disinformation campaigns. This has placed in stark relief how international relations work has changed in the past decade. Most international relations experts and diplomats agree that this revolution is an important component of this ongoing digital transformation across society, and therefore a cyber war becoming more of a reality than a theory.
From a sociological point of view, the unity of the state, society, and the economy can no longer be taken for granted, because, there are no geographic boundaries in cyber warfare. This environment is characterized by the significance assigned to information, knowledge, and ideas as resources in international relations, and by extension – information causing possible kinetic, or non-kinetic impacts in an armed conflict.
“Information warfare is real. Information operations are being conducted today. While the world has not yet witnessed nor fully comprehended the implications of a global information war, it is now enduring an ongoing information competition with sporadic conflicts in the information domain.”Source – Information Warfare (by Edward Waltz/1998)
In the past few weeks, Russia has resorted to kinetic warfare accompanied by well-orchestrated disinformation campaigns. A typical disinformation campaign can undermine the truth, confuse people from both sides and draw a false narrative, sowing the seeds of discord and distrust among the public at large. Resorting to psychological operations and/or information warfare requires the cooperation of both public and private sector entities from the Russian side to reach critical mass for the information to become a true disinformation campaign.
In the context of the Russia – Ukraine war, threat actors emerge from the dark web, trying to take financial advantage of the chaotic situation. Corporate networks and database access is being offered by threat actors in exchange for money. Further destructive Hermetic Wiper attacks were observed to be the most prevalent during the ongoing Russia Ukraine war as well as the lead-up to the kinetic war.
What is the impact of a cyber attack?
Researchers have predicted cyber-attacks as a major component in future wars. This component is said to be the fifth domain of conflict after land, air, sea, and space. The Ukrainian government has already been hit by many cyber-attacks from the Russian side, Ukraine has significantly lesser developed cyber capability and they are doing their best to defend themselves.
Some cyber-attacks are intended to wipe data from disks with no possibility of easy recovery while others tried to make Ukrainian resources unavailable by sending mass digital traffic in distributed denial of service (DDoS) attacks. Ukraine has been a testing ground for Russian cyber-attacks for so long.
Example: Sandworm – In 2015, an advanced persistent attack by Sandworm (threat actor) on Ukrainian power grids resulted in power outages for roughly 220,000 consumers in Ukraine for up to 6 hours. A foreign affairs article by Silverado Policy Accelerator founder Dmitri Alperovitch pointed out three types of cyber-attack motives in a war situation.
I) Gather Intelligence
II) Undermining military operations
III) The psychological battering of public
But researchers are not clear if cyber-attacks can have a major impact on military operations.
“A Russian cyber offensive tied to Ukraine could change all of that, showing that cyber might have far more impact on the battlefield, more coercive power, more lethal and widespread effect than many doubters would expect,” Jason Healey, a former White House official who is now a senior research scholar in cyber conflict at Columbia University
The most prominent effect of cyber operations, according to researchers will be disrupting military operations. For example, hackers can disrupt the communication channels to stop high command from sending orders to frontline troops. This will cause delayed action in a war situation. Another attack method for hackers is to spoof messages with false instructions to use the situation in their interest.
In this war, a cyber-attack is used to create panic and degrade the adversary’s capability to fight, information operations break the resolve to respond and push a narrative conducive to the attacking forces, even legitimizing the aggression. Kinetic operations are thus suitably aided by softening the battlefield. When NATO accuses Russia of conducting hybrid warfare, this is what they mean.
Conti Threat Actor Supporting Russia
You can read a detailed analysis of the Conti ransomware from LMNTRIX labs.
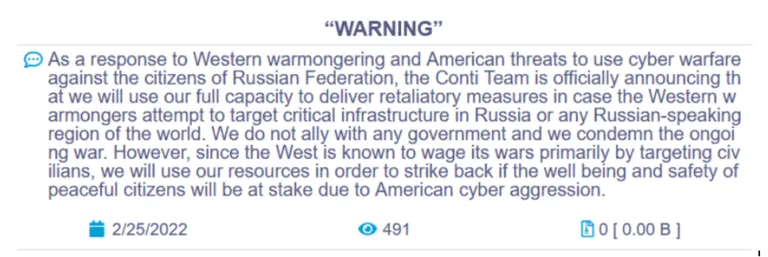
On Feb 25, 2022, the Conti ransomware group assured its full support to Russia. The message on the Conti News website leak also stated that Conti will strike back at anyone who is involved in the war against Russia.
After a very bold initial statement, the group softened their tone a bit. The reason is not very clear but some researchers said that there are chances that some sub-groups of Conti might not be in agreement with the narrative of Conti. Following are screenshots of the initial and updated messages by Conti respectively.
Initial Statement
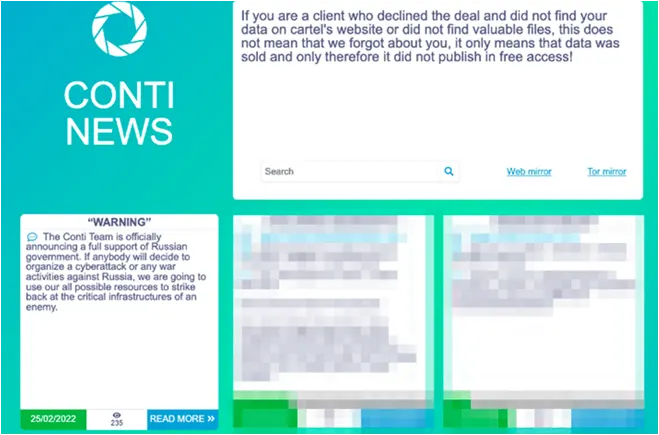
Updated statement
Hermetic Wiper
Target: Business in Ukraine
Motivation: encrypt a computer’s data in an irrecoverable fashion
Outcome: It has caused $10 billion in financial damage globally to date
Summary: The cyber-attack deploys malware that primarily wipes data was discovered just hours before Russian forces entered Ukraine, this can be regarded as the first volley of Moscow’s assault against Ukraine. The name Hermetic Wiper was given based on a stolen digital certificate from a company called Hermetic Digital Ltd. The malware fragments files on the disk and overwrites via the master boot recovery (MBR) utility to make recovery impossible. Practically the malware gains write access to low-level data structures on the disk. Due to its functional nature, it is also known as disk-wiping malware or simply referred to as a wiper.
Investigations on some initial indicators suggest that the attack has been in preparation for some time. Some evidence shows the start of malicious activities in November 2021.
After an investigation of an attack on one of Ukraine’s organizations, it appears that network access has been granted on Dec 23, 2021. The initial access was achieved via malicious SMB activity against a Microsoft Exchange server. A web shell was also installed before the wiper was deployed on Feb 23, 2022.
Based on multiple intelligence reports, the wiper-ware is preceded by exploits that aid in malware deployment or multiple distributed denial-of-service attacks to shut down protective services. LMNTRIX XDR provides detection and prevention capabilities that can help enterprise security teams to find the following indicators of compromise.
Hermetic Wiper IOC’s
Following are some of the IOCs observed in victim’s environment by LMNTRIX CDC,
- 1bc44eef75779e3ca1eefb8ff5a64807dbc942b1e4a2672d77b9f6928d292591
- 0385eeab00e946a302b24a91dea4187c1210597b8e17cd9e2230450f5ece21da
- A64c3e0522fad787b95bfb6a30c3aed1b5786e69e88e023c062ec7e5cebf4d3e
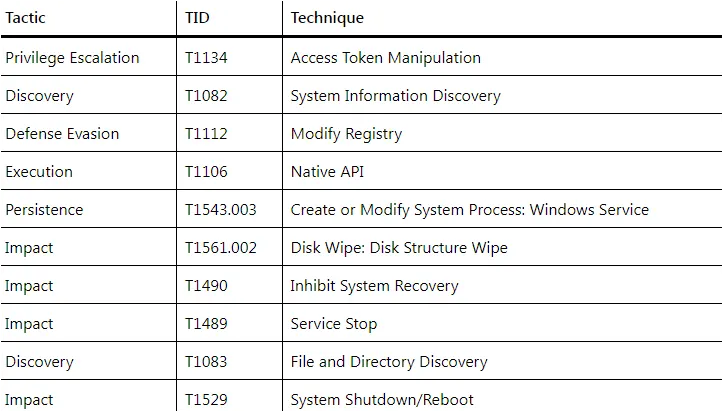
MITRE ATT&CK Mapping for Hermetic Wiper
Yara Signatures for Hermetic Wiper
https://github.com/Neo23x0/signature-base/blob/master/yara/apt_ua_hermetic_wiper.yar
SaintBot
Target: Ukrainian Organizations
Motivation: Politically Motivated
Outcome: Not Clear
Summary: Several Phishing emails are observed targeting Ukrainian organizations Containing attached documents and two shortcut files. One shortcut file downloads and executes Outsteel malware using PowerShell which further downloads and executes SaintBot malware.
Several emails were reported disguised as messages from Ukrainian police. The SaintBot malware is designed to be inactive when the Language Code Identifier (LCID) of the infected device is in Russia, Ukraine, Belarus, Armenia, Kazakhstan, or Moldova. One unique feature observed by LMNTRIX CDC is the malware design. The design allows utilizing the distributing mechanism to further spread any kind of malware.
The malware works by exploiting Fodhelper available in Windows 10, by attempting to bypass user account control. The SaintBot is able to execute with administrative privileges by adding registry entry.
Saintbot collects information from infected hosts and sends that information to Command and Control Server. Following command and control servers are observed so far.
- hxxp://8003659902[.]space/wp-adm/gate.php
- hxxp://smm2021[.]net/wp-adm/gate.php
- hxxp://8003659902[.]site/wp-adm/gate.php
SaintBot IOCs
- D01b6d2461b4616969a7e688acf91fdc20ae37b51c0b67fed700e0a42365ccda
- Filename : SecuriteInfo.com.Variant.Graftor.941749.26444.23114
- Filesize : 220’160 bytes
- Origin Country : US
Anonymous Group’s attacks against Russia
Target: Russian Government, Corporate & Media Websites
Motivation: Politically Motivated
Outcome: Hacktivists protesting the war and its aggressor
Summary: How the Anonymous group’s story begins in the online message forums of 4chan, the anonymous social community website founded in 2003, and how it has morphed today reads like folklore. Today Anonymous has morphed into a decentralized movement of like-minded online users who would communicate in encrypted chat rooms to plan online attacks and disruptions. This group has evolved to bigger and better things like attacking a nation-state like Russia with politically motivated messages or defacement of government-linked websites. After declaring cyberwar against the Russian government, Anonymous has managed to get unauthorized access to IT infrastructure to orchestrate full defacements of government, corporate, and media websites. One account from a news publication CNBC cites a live news feed on Russian TV displaying a “pro Ukrainian” message in the Russian language.
Appendix: Timeline of Events
January 15, 2022: The WhisperGate malware was first observed by Microsoft Threat Intelligence Centre. The malware was found to target Ukrainian Organizations.
February 23, 2022: Another malware known as HermeticWiper was being observed by SentinelLab researchers in Ukrainian organizations. The malware results in boot failure of the device.
February, 24, 2022 – Russians start the initial armed conflict on Eastern European borders with Ukraine
February 24, 2022: IsaacWiper Malware observed in Ukrainian organization has been reported by ESET.
March 7, 2022: Ukraine’s Computer Emergency Response Team (CERT-UA) confirmed use of Micro Backdoor against Ukrainian Organizations.
March 14, 2022: A destructive wiper known as CaddyWiper was also observed by ESET researchers


